New Version:
1. How many /30 subnets can be created from one /27 subnet
- 2
- 4
- 6
- 8
2. What information can be verified through the show ip dhcp binding command?
- that DHCPv4 discover messages are still being received by the DHCP server
- the number of IP addresses remaining in the DHCP pool
- the IPv4 addresses that are assigned to hosts by the DHCP server
- the IPv4 addresses that have been excluded from the DHCPv4 pool
3. Refer to the exhibit. A network administrator is reviewing port and VLAN assignments on switch S2 and notices that interfaces Gi0/1 and Gi0/2 are not included in the output. Why would the interfaces be missing from the output
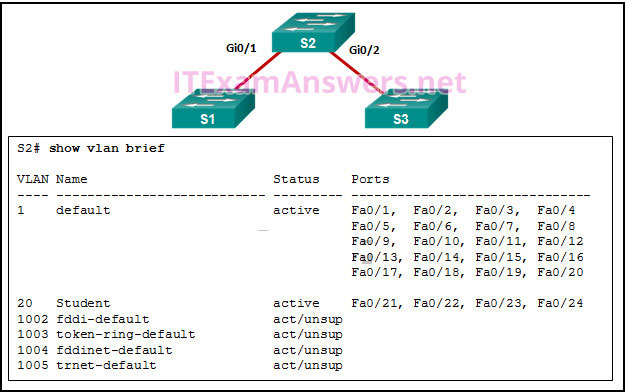
- There is a native VLAN mismatch between the switches.
- There is no media connected to the interfaces.
- They are administratively shut down.
- They are configured as trunk interfaces
4. Refer to the exhibit. A switch with a default configuration connects four hosts. The ARP table for host A is shown. What happens when host A wants to send an IP packet to host D?
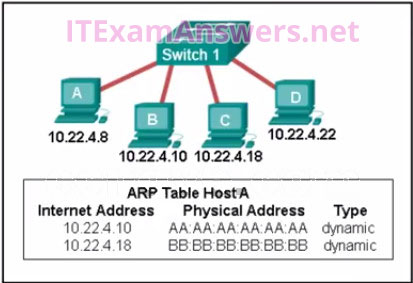
- Host A sends an ARP request to the MAC address of host D. Host D responds with its IP address.
- Host D sends an ARP request to host A. Host A responds with its MAC address.
- Host A sends out the packet to the switch. The switch adds the MAC address for host D to the frame and forwards it to the network.
- Host A sends out a broadcast of FF:FF:FF:FF:FF:FF. Every other host connected to the switch receives the broadcast and host D responds with its MAC address.
5. Refer to the exhibit. A network administrator needs to add an ACE to the TRAFFIC-CONTROL ACL that will deny IP traffic from the subnet 172.23.16.0/20. Which ACE will meet this requirement?
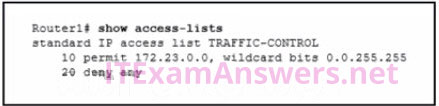
- 5 deny 172.23.16.0 0.0.15.255
- 5 deny 172.23.16.0 0.0.255.255
- 15 deny 172.23.16.0 0.0.15.255
- 30 deny 172.23.16.0 0.0.15.255
6. Which three layers of the OSI model map to the application layer of the TCP/IP model? (Choose three.)
- Application
- Data Link
- Transport
- Session
- Presentation
- Network
7. Refer to the exhibit. When a packet arrives on interface Serial0/0/0 on R1, with a destination IP address of PC1, which two events occur? (Choose two)
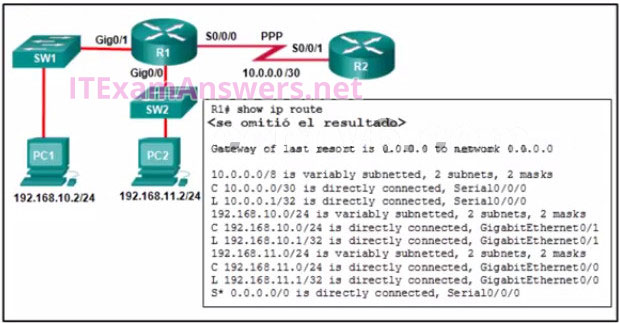
- Router R1 will de-encapsulate the packet and encapsulate it in a PPP frame.
- Router R1 will forward the packet out Gig0/1.
- Router R1 will forward the packet out Gig0/0.
- Router R1 will de-encapsulate the packet and encapsulate it in an Ethernet frame.
- Router R1 will forward the packet out S0/0/0.
8. What is the purpose of the overload keyword in the ip nat inside source list 1 pool NAT_POOL overload command?
- It allows many inside hosts to share one or a few inside global addresses.
- It allows a pool of inside global addresses to be used by internal hosts.
- It allows external hosts to initiate sessions with internal hosts.
- It allows a list of internal hosts to communicate with a specific group of external hosts.
9. What type of installation is needed to view syslog messages?
- A syslog client must be installed on a workstation.
- Because any network equipment can interpret syslog messages, nothing special is needed to view them.
- A syslog server must be installed on a router.
- A syslog server must be installed on a workstation.
10. Refer to the exhibit. A network administrator has added a new subnet to the network and needs hosts on that subnet to receive IPv4 addresses from the DHCPv4 server.
What two commands will allow hosts on the new subnet to receive addresses from the DHCP4 server? (Choose two.)
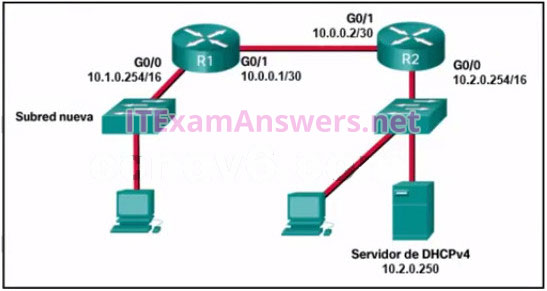
- R1(config-if)# ip helper-address 10.2.0.250
- R1(config)# interface G0/1
- R1(config)# interface G0/0
- R2(config-if)# ip helper-address 10.2.0.250
- R2(config)# interface G0/0
- R1(config-if)# ip helper-address 10.1.0.254
11. Refer to the exhibit. Static NAT is being configured to allow PC 1 access to the web server on the internal network. What two addresses are needed in place of A and B to complete the static NAT configuration? (Choose two.)
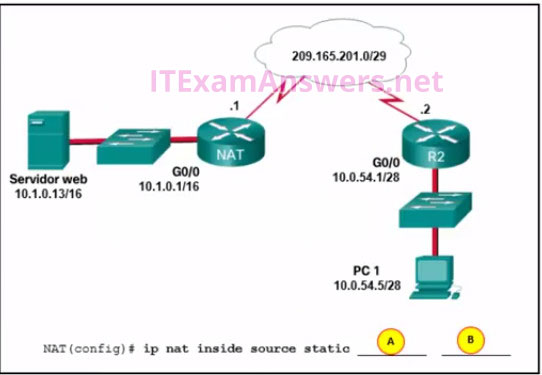
- B = 209.165.201.7
- A = 10.1.0.13
- B = 10.0.254.5
- B = 209.165.201.1
- A = 209.165.201.2
12. When creating an IPv6 static route, when must a next-hop IPv6 address and an exit interface both be specified
- when CEF is enabled
- when the static route is a default route
- when the next hop is a link-local address
- when the exit interface is a point-to-point interface
13. Which address prefix range is reserved for IPv4 multicast?
- 224.0.0.0 – 239.255.255.255
- 240.0.0.0 – 254.255.255.255
- 169.254.0.0 – 169.25.255.255
- 127.0.0.0- 127.255.255.255
14. Refer to the exhibit. What would happen after the IT administrator enters the new static route?
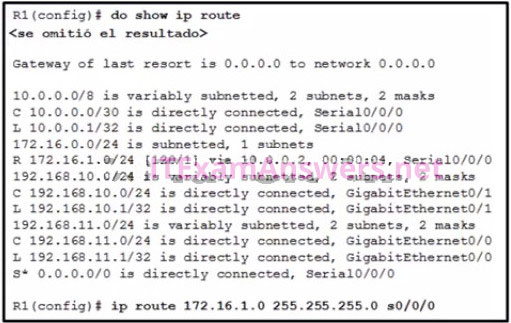
- The 172.16.1.0 route learned from RIP would be replaced with the 172.16.1.0 static route.
- The 172.16.1.0 static route is added to the existing routes in the routing table.
- The 172.16.1.0 static route would be entered into the running-config but not shown in the routing table.
- The 0.0.0.0 default route would be replaced with the 172.16.1.0 static route.
15. What effect does the default-information originate command have on a Cisco router that is configured for RIP?
- Any dynamic route that is learned from a neighboring router will propagate to other adjacent routers.
- Any default static route that is configured on the router will propagate to other adjacent routers.
- Any static route that is learned from a neighboring router will propagate to other adjacent routers.
- Any routes that are learned from a neighboring router will propagate to other adjacent routers.
16. Which type of IPv6 address refers to any unicast address that is assigned to multiple hosts?
- Single location
- Any cast
- Link-local
- Global unicast
17. An administrator wants to replace the configuration file on a Cisco router by loading a new configuration file from a TFTP server. What two things does the administrator need to know before performing this task? (Choose two.)
- TFTP server IP address
- name of the configuration file that is currently stored on the router
- router IP address
- configuration register value
- name of the configuration file that is stored on the TFTP server
- The name of the configuration file that is currently stored on the TFTP server
- The name of the configuration file that is currently stored on the router
18. Refer to the exhibit. Inter-VLAN communication between VLAN 10, VLAN 20, and VLAN 30 is not successful. What is the problem?
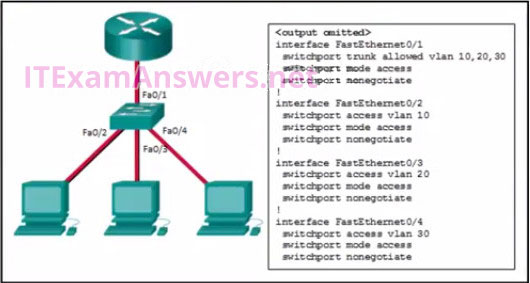
- The switch interface FastEthernet0/1 is configured to not negotiate and should be configured to negotiate.
- The access interfaces do not have IP addresses and each should be configured with an IP address.
- The switch interface FastEthernet0/1 is configured as an access interface and should be configured as a trunk interface.
- The switch interfaces FastEthernet0/2, FastEthernet0/3, and FastEthernet0/4 are configured to not negotiate and should be configured to negotiate.
19. Which statement describes the Cisco License Manager?
- It is a free, standalone software application for deploying Cisco software licenses across the network.
- It is a web-based portal for getting and registering individual software licenses.
- It is a centralized TFTP server that enables control of the number and revision level of Cisco IOS images.
- It is an organized collection of processes and components used to activate Cisco IOS software feature sets by obtaining and validating Cisco software licenses.
20. A user sends an HTTP request to a web server on a remote network. During encapsulation for this request, what information is added to the address field of a frame to indicate the destination?
- the MAC address of the default gateway
- the network domain of the destination host
- the IP address of the default gateway
- the MAC address of the destination host
21. A network administrator is designing an IPv4 addressing scheme and requires these subnets.
1 subnet of 100 hosts
2 subnets of 80 hosts
2 subnets of 30 hosts
4 subnets of 20 hosts
Which combination of subnets and masks will provide the best addressing plan for these requirements
- 9 subnets of 126 hosts with a 255.255.255.128 mask
- 3 subnets of 126 hosts with a 255.255.255.128 mask
6 subnets of 30 hosts with a 255.255.255.224 mask - 3 subnets of 126 hosts with a 255.255.255.192 mask
6 subnets of 30 hosts with a 255.255.255.240 mask - 1 subnet of 126 hosts with a 255.255.255.192 mask
2 subnets of 80 hosts with a 255.255.255.224 mask
6 subnets of 30 hosts with a 255.255.255.240 mask
22. Refer to the exhibit. How was the host route 2001:DB8:CAFE:4::1/128 installed in the routing table?
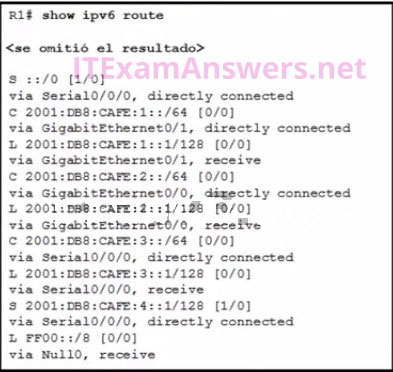
- The route was automatically installed when an IP address was configured on an active interface.
- The route was dynamically created by router R1.
- The route was manually entered by an administrator.
- The route was dynamically learned from another router.
23. What are three characteristics of the CSMA/CD process? (Choose three.)
- The device with the electronic token is the only one that can transmit after a collision.
- After detecting a collision, hosts can attempt to resume transmission after a random time delay has expired.
- All of the devices on a segment see data that passes on the network medium.
- Devices can be configured with a higher transmission priority.
- A device listens and waits until the media is not busy before transmitting.
- A jam signal indicates that the collision has cleared and the media is not busy.
24. A network engineer is troubleshooting connectivity issues among interconnected Cisco routers and switches. Which command should the engineer use to find the IP address information, host name, and IOS version of neighboring network devices?
- show ip route
- show interfaces
- show version
- show cdp neighbors detail
25. Fill in the blank
When port security is enabled, a switch port uses the default violation mode of ___shutdown ___ until specifically configured to use a different violation mode.
26. Refer to the exhibit. Which source address is being used by router R1 for packets being forwarded to the Internet?
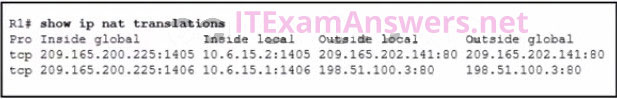
- 198.51.100.3
- 10.6.15.2
- 209.165.200.225
- 209.165.202.141
27. Which feature on a Cisco router permits the forwarding of traffic for which there is no specific route
- route source
- next-hop
- outgoing interface
- gateway of last resort
28. Which three statements characterize UDP (Choose three.)
- UDP provides sophisticated flow control mechanisms.
- UDP relies on IP for error detection and recovery.
- UDP is a low overhead protocol that does not provide sequencing or flow control mechanisms.
- UDP provides basic connectionless transport layer functions.
- UDP relies on application layer protocols for error detection.
- UDP provides connection-oriented, fast transport of data at Layer 3.
29. Refer to the exhibit. What will router R1 do with a packet that has a destination IPv6 address of 2001:db8:cafe:5::1?
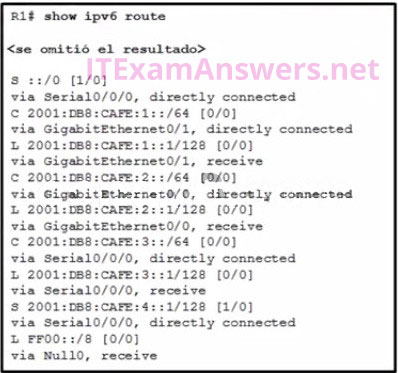
- forward the packet out GigabitEthernet0/1
- drop the packet
- forward the packet out Serial0/0/0
- forward the packet out GigabitEthernet0/0
30. How will a router handle static routing differently if Cisco Express Forwarding is disabled
- Static routes that use an exit interface will be unnecessary.
- Serial point-to-point interfaces will require fully specified static routes to avoid routing inconsistencies.
- It will not perform recursive lookups.
- Ethernet multiaccess interfaces will require fully specified static routes to avoid routing inconsistencies.
31. Refer to the exhibit. A network technician issues the command show vlan to verify the VLAN configuration. Based on the output, which port should be assigned with native VLAN?
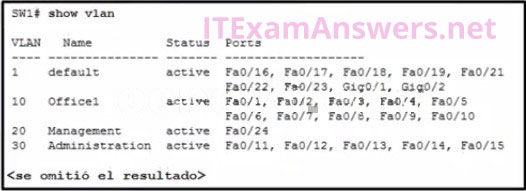
- Fa0/12
- Gig0/1
- Fa0/24
- Fa0/20
32. Which two things should a network administrator modify on a router to perform password recovery? (Choose two.)
- the configuration register value
- the NVRAM file system
- system ROM
- the system image file
- the startup configuration file
33. What are two reasons why an administrator might choose to use static routing rather than dynamic routing? (Choose two.)
- Static routing is more scalable.
- Static routing is easier to maintain in large networks.
- Static routing uses less router processing and bandwidth.
- Static routing is more secure.
- Static routing does not require complete knowledge of the whole network.
34. An administrator who is troubleshooting connectivity issues on a switch notices that a switch port configured for port security is in the err-disabled state. After verifying the cause of the violation, how should the administrator re-enable the port without disrupting network operation?
- Reboot the switch.
- Issue the no switchport port-security violation shutdown command on the interface.
- Issue the no switchport port-security command, then re-enable port security.
- Issue the shutdown command followed by the no shutdown command on the interface.
35. A network administrator has been allocated the IPv4 10.10.240.0/20 block of addresses for a LAN. Two devices on two different, but contiguous, subnets on the LAN have been assigned the addresses 10.10.247.1/21 and 10.10.248.10/24, respectively. The administrator has to create a third subnet from the remaining address range. To optimize the use of this address space, the new subnet will follow on directly from the existing subnets. What is the first available host address in the next available subnet
- 10.10.250.1
- 10.10.249.1
- 10.10.248.17
- 10.10.255.17
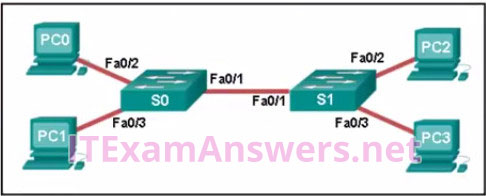
36. Refer to the exhibit. A ping to PC3 is issued from PC0, PC1, and PC2 in this exact order. Which MAC addresses will be contained in the S1 MAC address table that is associated with the Fa0/1 port?
- PC0, PC1, and PC2 MAC addresses
- just the PC1 MAC address
- just PC0 and PC1 MAC addresses
- just the PC2 MAC address
- just the PC0 MAC address
37. Refer to the exhibit. A network administrator issues the show lldp neighbors command to display information about neighboring devices. What can be determined based on the information?
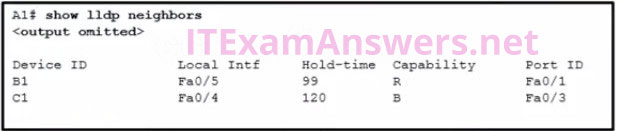
- Device C1 is a switch.
- Device A1 is connected to the port Fa0/5 on device B1.
- Device C1 is a switch.
- Device B1 is a WLAN access point.
- Device C1 is connected to device B1 through the port Fa0/3.
38. Which two devices allow hosts on different VLANs to communicate with each other (Choose two.)
- Layer 3 switch
- repeater
- router
- hub
- Layer 2 switch
39. Refer to the exhibit. Host A sends a data packet to host B. What will be the addressing information of the data packet when it reaches host B
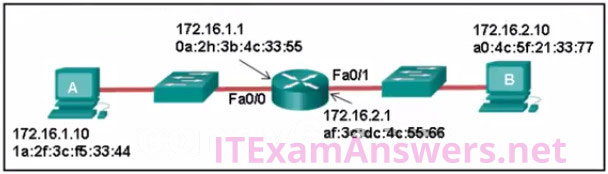
A. ![]()
B. ![]()
C. 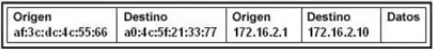
D. 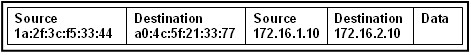
Correct Answers: A
40. Data is being sent from a source PC to a destination server. Which three statements correctly describe the function of TCP or UDP in this situation (Choose three.)
- TCP is the preferred protocol when a function requires lower network overhead.
- The source port field identifies the running application or service that will handle data returning to the PC.
- The UDP destination port number identifies the application or service on the server which will handle the data.
- The TCP process running on the PC randomly selects the destination port when establishing a session with the server.
- UDP segments are encapsulated within IP packets for transport across the network.
- The TCP source port number identifies the sending host on the network.
41. What is defined by the ip nat pool command when configuring dynamic NAT?
- the pool of global address
- the range of external IP addresses that internal hosts are permitted to access
- the pool of available NAT servers
- the range of internal IP addresses that are translated
42. Which address type is not supported by IPv6
- multicast
- private
- unicast
- broadcast
43. What is the purpose of setting the native VLAN separate from data VLANs?
- The native VLAN is for routers and switches to exchange their management information, so it should be different from data VLANs.
- A separate VLAN should be used to carry uncommon untagged frames to avoid bandwidth contention on data VLANs.
- The security of management frames that are carried in the native VLAN can be enhanced.
- The native VLAN is for carrying VLAN management traffic only.
44. Which ACE would permit traffic from hosts only on the 192.168.8.0/22 subnet?
- permit 192.168.8.0 0.0.3.255
- permit 192.168.0.0 0.0.15.255
- permit 192.168.8.0 255.255.248.0
- permit 192.168.8.0 0.0.7.255
45. Which two issues might cause excessive runt and giant frames in an Ethernet network? (Choose two.)
- damaged cable connector
- using the incorrect cable type
- native VLAN mismatch
- a malfunctioning NIC
- excessive collisions
- incorrectly configured auto-MDIX feature
46. Refer to the exhibit. Which static route would an IT technician enter to create a backup route to the 172.16.1.0 network that is only used if the primary RIP learned route fails?
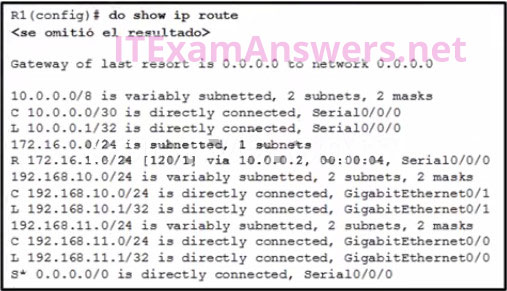
- ip route 172.16.1.0 255.255.255.0 s0/0/0
- ip route 172.16.1.0 255.255.255.0 s0/0/0 111
- ip route 172.16.1.0 255.255.255.0 s0/0/0 91
- ip route 172.16.1.0 255.255.255.0 s0/0/0 121
47. Refer to the exhibit. Which three events will occur as a result of the configuration shown on R1? (Choose three.)

- Only traffic that originates from the GigabitEthernet 0/1 interface will be monitored.
- The syslog messages will contain the IP address the GigabitEthernet 0/1 interface.
- Messages that are sent to the syslog server will be limited to levels 3 or lower.
- Messages that are sent to the syslog server will use 192.168.1.5 as the destination IP address.
- For multiple occurrences of the same error, only the first three messages will be sent to the server.
- Messages that are sent to the syslog server will be limited to levels 3 and higher.
48. Which IPv6 prefix is reserved for communication between devices on the same link?
- 2001::/32
- FC00::/7
- FDFF::/7
- FE80::/10
49. Refer to the exhibit. Packets destined to which two networks will require the router to perform a recursive lookup? (Choose two.)
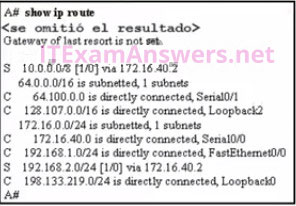
- 128.107.0.0/16
- 192.168.1.0/24
- 64.100.0.0/16
- 192.168.2.0/24
- 172.16.40.0/24
- 10.0.0.0/8
50. Refer to the exhibit. Routers R1 and R2 are connected via a serial link. One router is configured as the NTP master, and the other is an NTP client. Which two pieces of information can be obtained from the partial output of the show ntp associations detail command on R2 (Choose two.)

- Router R1 is the master, and R2 is the client.
- The IP address of R2 is 192.168.1.2.
- The IP address of R1 is 192.168.1.2.
- Both routers are configured to use NTPv2.
- Router R2 is the master, and R1 is the client.
51. A network technician is configuring port security on a LAN switch interface. The security policy requires host MAC addresses to be learned dynamically, stored in the address table, and saved to the switch running configuration. Which command does the technician need to add to the following configuration to implement this policy?
- Switch(config)# interface fa0/1
Switch(config-if)# switchport mode access
Switch(config-if)# switchport portsecurity - Switch(config-if)# switchport port-security maximum 40
- Switch(config-if)# switchport port-security macaddress
- Switch(config-if)# switchport port-security macaddress sticky
- Switch(config-if)# switchport port-security macaddress 000B.FCFF.E880
52. After a license has been purchased and installed, what is the next step that is required before it is activated?
- Copy the running configuration to flash.
- Reboot the router.
- Issue the license boot module technology-package command.
- Copy the running configuration to NVRAM.
53.Refer to the exhibit. A technician is programming switch SW3 to manage voice and data traffic through port Fa0/20. What, if anything, is wrong with the configuration?
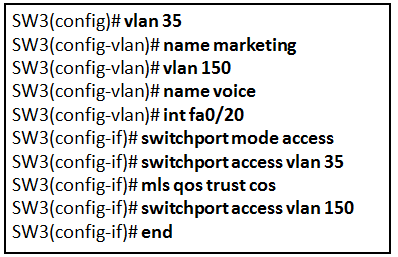
- There is nothing wrong with the configuration.
- Interface Fa0/20 can only have one VLAN assigned.
- The mls qos trust cos command should reference VLAN 35.
- The command used to assign the voice VLAN to the switch port is incorrect.
54. A network administrator is using the router-on-a-stick model to configure a switch and a router for inter-VLAN routing. What configuration should be made on the switch port that connects to the router
- CConfigure it as a trunk port and allow only untagged traffic.
- Configure the port as an access port and a member of VLAN1.
- Configure the port as an 802.1q trunk port.
- Configure the port as a trunk port and assign it to VLAN1.
55. On which switch interface would an administrator configure an IP address so that the switch can be managed remotely?
- vty 0
- FastEthernet0/1
- VLAN 1
- console 0
56.
57. The exhibit shows configuration commands from switch SW3 as follows:
SW3(config)# vlan 35 SW3(config-vlan)# name marketing SW3(config-vlan)# vlan 150 SW3(config-vlan)# name voice SW3(config-vlan)# int fa0/20 SW3(config-if)# switchport mode access SW3(config-if)# switchport access vlan 35 SW3(config-if)# mls qos trust cos SW3(config-if)# switchport access vlan 150 SW3(config-if)# end
Refer to the exhibit. A technician is programming switch SW3 to manage voice and data traffic through port Fa0/20. What, if anything, is wrong with the configuration?
- The mls qos trust cos command should reference VLAN 35.
- The command used to assign the voice VLAN to the switch port is incorrect.
- Interface Fa0/20 can only have one VLAN assigned.
- There is nothing wrong with the configuration.
58. Which address type is not supported in IPv6?
- unicast
- private
- multicast
- broadcast
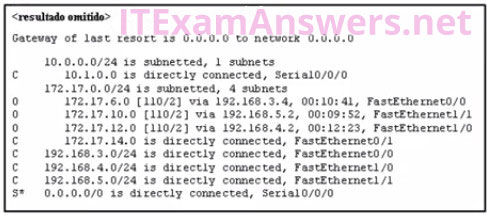
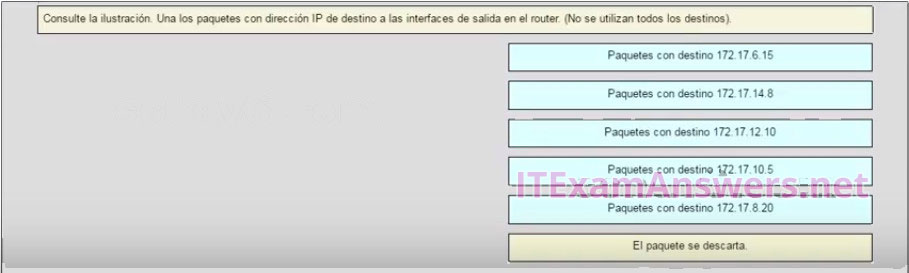
59. Refer to the exhibit. Match the packets with their destination IP address to the exiting interfaces on the router. (Not all targets are used.)
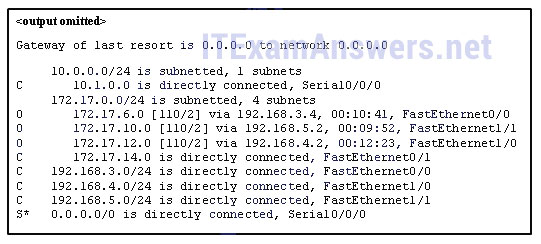
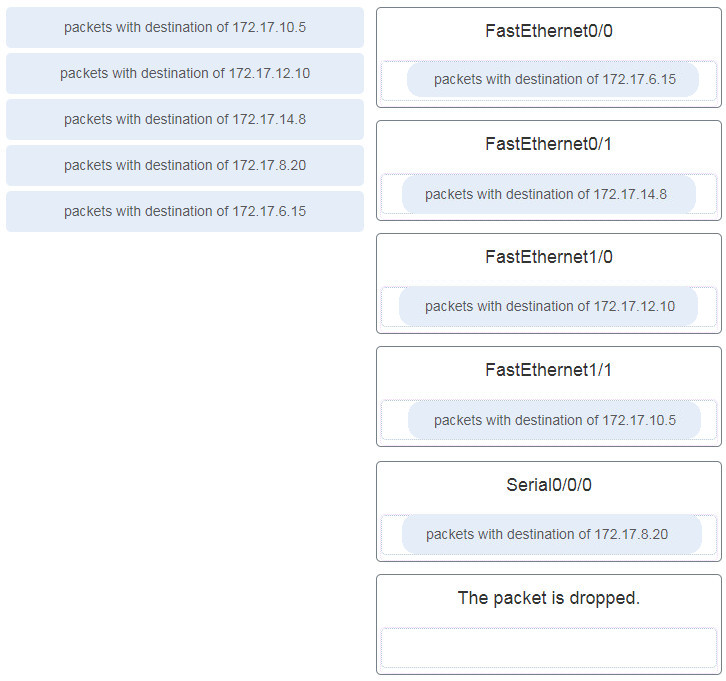

Refer to the exhibit. Match the packets with their destination IP address to the exiting interfaces on the router. (Not all targets are used.)
Hi I have the CCENT ICND1 exam in a few weeks, I would like to know if these 60 questions are enough to pass the exam? Thank you in advance for your answer.
How do you write an obsolete exam in a few weeks?
Sorry not trying to come off as a jerk, just curious as where I live that exam has been obsolete since February 2020, with no opportunity to book past Feb 20 if not passed in full, ICND1 and 2 by Feb 20 then you have to write the
entire new exam and your ICND1 score is out the window.
Whomever created this tool kudos man, I wish I found it sooner as I write the new exam in 2 weeks today.
Hi! can i have the vce file please? i appreciate your efforts!
Hi, i will have exam from CCNA 2 rse v6 this week. Can you please tell me which final exam and which PT will be here. Thank you
A network administrator is designing an IPv4 addressing scheme and requires these subnets.
1 subnet of 100 hosts
2 subnets of 80 hosts
2 subnets of 30 hosts
4 subnets of 20 hosts
Which combination of subnets and masks will provide the best addressing plan for these requirements?
Correct
Response
Your
Response
1 subnet of 126 hosts with a 255.255.255.192 mask
2 subnets of 80 hosts with a 255.255.255.224 mask
6 subnets of 30 hosts with a 255.255.255.240 mask
9 subnets of 126 hosts with a 255.255.255.128 mask
3 subnets of 126 hosts with a 255.255.255.192 mask
6 subnets of 30 hosts with a 255.255.255.240 mask
Correct Response
3 subnets of 126 hosts with a 255.255.255.128 mask
6 subnets of 30 hosts with a 255.255.255.224 mask
May I get the PDF Dumps? Taking the 100-105 – Interconnecting Cisco Networking Devices Part 1 on Thursday
I HAVE ICN1 AND 1CND2 next week , can i get the dumps
Hello , I’m going to take CCNA2 ” ‘Routing and Switching Essentials” exam on wednesday 19/02 , which questions are included please? Should I learn version 6 or 7 ?
Is OSPF on ICND1v6? I don’t remember covering it during class.
I see OSPF appear in Oficial cert guide ICND 1 100-105 (ciscopress), It is only mentioned as an overview, not as intensive as ICND2
Interesting. Besides RIP, I don’t remember covering anything beyond the admin distance of OSPF (nothing about router ID’s etc…). I’m taking the exam soon so I guess I’ll report back and post if there were any in depth OSPF questions on mine.
Is page two strictly icnd 1 or are there CCNA questions included as well?
I have ICND1 Certification Exam test next week, can you send me the vce please?
Can I get the vce dumps of ICND1 too?
I have the exam this Friday, could you pass me the vce?
The questions here are the same as in vce file
We have updated all questions/dump at this topic include: Multiple-Choice, Drag and Drop, Labs (in page 1-4).
We always appreciate all comments and suggestions :)
Hi, could you please tell me how i can the latest updated ccna dumps . Thanks
Can I get the vce dumps of ICND1 too?
i have ccna1 exam next week can you send me the vce plz?
Done, please visit
Would it be possible to get the vce dumps for the ICND1???
Can I get the vce dumps of ICND1? I am scheudled to take the test in two weeks.
Done, please visit
Can I get the vce dumps of ICND1
Can I get the vce dumps of ICND1 too? I have a exam scheduled tomorrow
Please check email , :)
can you pls send me the pdf of the latest dumps???
Can I get the vce dumps of ICND1 too?..
Can us if the CCENT (ICND1) Practice Certification Exam Answers help
Can you pajevo us if the CCENT (ICND1) Practice Certification Exam Answers help on your test tomorrow
hey guys, is this the same questions from icnd1 certification exam? I heard it’s 58 questions and so this too. please can you guys verify it cause I’m about to take the exam next week.
Yes, but I think the questions on this topic are not enough for you to pass the CCENT exam, you should read more books: CCENT ICND1 Study Guide Third Edition
So these CCENT (ICND1) Practice Certification Exam questions on are the same as the the CCENT exam
I have sent vce dump file CCENT for you, please check email :)
If I study these CCENT (ICND1) Practice Certification Exam will this help me on the real CCENT (ICND1) Certification Exam test
Yes, study the vce file and the questions on this topic, it will make up 95% of the questions in the real exam
what If I study only the CCENT (ICND1) Practice Certification Exam on your site will this help me on the real CCENT (ICND1) Certification Exam test better then the vce
Please am preparing for CCENT and am to take it next week, please i need help that goes beyond this questions on the site
We are updating, this should be completed in the next 1-2 days, we will notify you.
Hello! In a few days I have to take the ICND1/CCENT exam, can you send me vce dump file please? Thank you for the fantastic work you do on this site!
Sorry, i don’t have
hi sir, I am answering my 100-105 interconnecting cisco ND exam. could you please email me the VCE dumps pleaseeeeee.Thanks
can you send vce dump file for me please?
studying only this questions will make me pass the real ICND1?
hi there, I am answering my 100-105 interconnecting cisco ND exam. could you please email me the VCE dumps pleaseeeeee.Thanks
will this help me on the real CCENT (ICND1) Certification Exam test
snip
These same questions come in the exam?
These same questions come in the exam?
hi guy’s!!! is ccent updated ? because i’m taking the exam this Friday!!! waiting your response
Hello, I also hope to take my exam in a month, you can sell me the questions that come in your ccent, psdt: luck in your exam.
THE CCENT (ICND1) Practice Certification have These same questions come in the real CCENT CERTIFICATION EXAM QUESTIONS
HI GUY’S!!!!! MAY YOU PROVIDE CCENT CERTIFICATION EXAM QUESTIONS AND ANSWERS PLESASE
many thank to you
34. An administrator who is troubleshooting connectivity issues on a switch notices that a switch port configured for port security is in the err-disabled state. After verifying the cause of the violation, how should the administrator re-enable the port without disrupting network operation?
– Issue the shutdown command followed by the no shutdown command on the interface.
– Reboot the switch.
– Issue the no switchport port-security violation shutdown command on the interface.
– Issue the no switchport port-security command, then re-enable port security.
Shutdown followed by no shutdown
Added, thanks you!
Thanks
The answer for question number 26 is wrong , the correct answer is :209.165.200.225 Not 10.6.15.2.
Explanation: The source address for packets forwarded by the router to the Internet will be the inside global address of 209.165.200.225. This is the address that the internal addresses from the 10.6.15.0 network will be translated to by NAT.
Which WAN connectivity method would be used in a remote location where there are no service provider networks?
WiMax
cable
VPN
VSAT
Which WAN connectivity method would be used in a remote location where there are no service provider networks?
cable
VPN
VSAT*
WiMAX
https://itexamanswers.net/ccna-4-chapter-2-exam-answers-v5-0-3-v6-0-full-100.html
The exhibit shows configuration commands from switch SW3 as follows:
SW3(config)# vlan 35
SW3(config-vlan)# name marketing
SW3(config-vlan)# vlan 150
SW3(config-vlan)# name voice
SW3(config-vlan)# int fa0/20
SW3(config-if)# switchport mode access
SW3(config-if)# switchport access vlan 35
SW3(config-if)# mls qos trust cos
SW3(config-if)# switchport access vlan 150
SW3(config-if)# end
Refer to the exhibit. A technician is programming switch SW3 to manage voice and data traffic through port Fa0/20. What, if anything, is wrong with the configuration?
Correct
Response
Your
Response
The mls qos trust cos command should reference VLAN 35.
There is nothing wrong with the configuration.
The command used to assign the voice VLAN to the switch port is incorrect.
Interface Fa0/20 can only have one VLAN assigned.
The voice VLAN should be configured with the switchport voice vlan 150 command. A switch interface can be configured to support one data VLAN and one voice VLAN. The mls qos trust cos associates with the interface. Voice traffic must be trusted so that fields within the voice packet can be used to classify it for QoS.
On Question 23 the answers are:
– All of the devices on a segment see data that passes on the network medium.
– After detecting a collision, hosts can attempt to resume transmission after a random time delay has expired.
– A device listens and waits until the media is not busy before transmitting.
The Carrier Sense Multiple Access/Collision Detection (CSMA/CD) process is a contention-based media access control mechanism used on shared media access networks, such as Ethernet. When a device needs to transmit data, it listens and waits until the media is available (quiet), then it will send data. If two devices transmit at the same time, a collision will occur. Both devices will detect the collision on the network. When a device detects a collision, it will stop the data transmission process, wait for a random amount of time, then try again.
Problem 11: A = 10.1.0.13; B = 209.165.201.1