1. In addition to the criteria used by extended ACLs, what conditions are used by a classic firewall to filter traffic?
- TCP/UDP source and destination port numbers
- TCP/IP protocol numbers
- IP source and destination addresses
- application layer protocol session information
2. A router has been configured as a classic firewall and an inbound ACL applied to the external interface. Which action does the router take after inbound-to-outbound traffic is inspected and a new entry is created in the state table?
- When traffic returns from its destination, it is reinspected, and a new entry is added to the state table.
- The internal interface ACL is reconfigured to allow the host IP address access to the Internet.
- The entry remains in the state table after the session is terminated so that it can be reused by the host.
- A dynamic ACL entry is added to the external interface in the inbound direction.
3. Refer to the exhibit. If a hacker on the outside network sends an IP packet with source address 172.30.1.50, destination address 10.0.0.3, source port 23, and destination port 2447, what does the Cisco IOS firewall do with the packet?
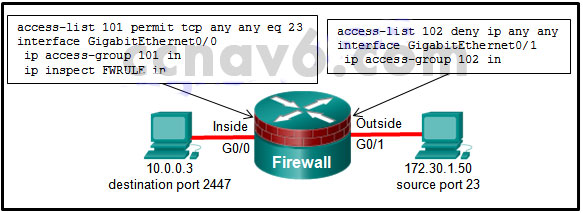
- The initial packet is dropped, but subsequent packets are forwarded.
- The packet is forwarded, and an alert is generated.
- The packet is forwarded, and no alert is generated.
- The packet is dropped.
4. What is one benefit of using a stateful firewall instead of a proxy server?
- ability to perform user authentication
- better performance
- ability to perform packet filtering
- prevention of Layer 7 attacks
5. What is one limitation of a stateful firewall?
- weak user authentication
- cannot filter unnecessary traffic
- not as effective with UDP- or ICMP-based traffic
- poor log information
6. Which statement describes a typical security policy for a DMZ firewall configuration?
- Traffic that originates from the inside interface is generally blocked entirely or very selectively permitted to the outside interface.
- Traffic that originates from the DMZ interface is selectively permitted to the outside interface.
- Traffic that originates from the outside interface is permitted to traverse the firewall to the inside interface with few or no restrictions.
- Return traffic from the inside that is associated with traffic originating from the outside is permitted to traverse from the inside interface to the outside interface.
- Return traffic from the outside that is associated with traffic originating from the inside is permitted to traverse from the outside interface to the DMZ interface.
7. Refer to the exhibit. Which statement describes the function of the ACEs?

- These ACEs allow for IPv6 neighbor discovery traffic.
- These ACEs automatically appear at the end of every IPv6 ACL to allow IPv6 routing to occur.
- These are optional ACEs that can be added to the end of an IPv6 ACL to allow ICMP messages that are defined in object groups named nd-na and nd-ns.
- These ACEs must be manually added to the end of every IPv6 ACL to allow IPv6 routing to occur.
8. When an inbound Internet-traffic ACL is being implemented, what should be included to prevent the spoofing of internal networks?
- ACEs to prevent traffic from private address spaces
- ACEs to prevent broadcast address traffic
- ACEs to prevent ICMP traffic
- ACEs to prevent HTTP traffic
- ACEs to prevent SNMP traffic
9. To facilitate the troubleshooting process, which inbound ICMP message should be permitted on an outside interface?
- echo request
- time-stamp request
- echo reply
- time-stamp reply
- router advertisement
10. Which command is used to activate an IPv6 ACL named ENG_ACL on an interface so that the router filters traffic prior to accessing the routing table?
- ipv6 access-class ENG_ACL in
- ipv6 traffic-filter ENG_ACL out
- ipv6 traffic-filter ENG_ACL in
- ipv6 access-class ENG_ACL out
11. When a Cisco IOS Zone-Based Policy Firewall is being configured via CLI, which step must be taken after zones have been created?
- Assign interfaces to zones.
- Establish policies between zones.
- Identify subsets within zones.
- Design the physical infrastructure.
12. A network administrator is implementing a Classic Firewall and a Zone-Based Firewall concurrently on a router. Which statement best describes this implementation?
- An interface must be assigned to a security zone before IP inspection can occur.
- Both models must be implemented on all interfaces.
- The two models cannot be implemented on a single interface.
- A Classic Firewall and Zone-Based Firewall cannot be used concurrently.
13. Which two rules about interfaces are valid when implementing a Zone-Based Policy Firewall? (Choose two.)
- If one interface is a zone member, but the other is not, all traffic will be passed.
- If neither interface is a zone member, then the action is to pass traffic.
- If both interfaces are members of the same zone, all traffic will be passed.
- If one interface is a zone member and a zone-pair exists, all traffic will be passed.
- If both interfaces belong to the same zone-pair and a policy exists, all traffic will be passed.
14. If the provided ACEs are in the same ACL, which ACE should be listed first in the ACL according to best practice?
- permit udp 172.16.0.0 0.0.255.255 host 172.16.1.5 eq snmptrap
- deny udp any host 172.16.1.5 eq snmptrap
- deny tcp any any eq telnet
- permit ip any any
- permit udp any any range 10000 20000
- permit tcp 172.16.0.0 0.0.3.255 any established
15. Which security tool monitors network traffic as it flows into and out of the organization and determines whether packets belong to an existing connection or are from an unauthorized source?
- web security appliance
- intrusion protection system
- application proxy
- stateful firewall
16. A company is deploying a new network design in which the border router has three interfaces. Interface Serial0/0/0 connects to the ISP, GigabitEthernet0/0 connects to the DMZ, and GigabitEthernet/01 connects to the internal private network. Which type of traffic would receive the least amount of inspection (have the most freedom of travel)?
- traffic that is going from the private network to the DMZ
- traffic that is returning from the DMZ after originating from the private network
- traffic that originates from the public network and that is destined for the DMZ
- traffic that is returning from the public network after originating from the private network
17. Refer to the exhibit. The ACL statement is the only one explicitly configured on the router. Based on this information, which two conclusions can be drawn regarding remote access network connections? (Choose two.)
![]()
- SSH connections from the 192.168.2.0/24 network to the 192.168.1.0/24 network are allowed.
- Telnet connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are allowed.
- Telnet connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are blocked.
- SSH connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are allowed.
- SSH connections from the 192.168.1.0/24 network to the 192.168.2.0/24 network are blocked.
- Telnet connections from the 192.168.2.0/24 network to the 192.168.1.0/24 network are allowed.
18. Consider the following access list.
access-list 100 permit ip host 192.168.10.1 any
access-list 100 deny icmp 192.168.10.0 0.0.0.255 any echo
access-list 100 permit ip any any
Which two actions are taken if the access list is placed inbound on a router Gigabit Ethernet port that has the IP address 192.168.10.254 assigned? (Choose two.)
- Only the network device assigned the IP address 192.168.10.1 is allowed to access the router.
- Devices on the 192.168.10.0/24 network are not allowed to reply to any ping requests.
- Only Layer 3 connections are allowed to be made from the router to any other network device.
- Devices on the 192.168.10.0/24 network are not allowed to ping other devices on the 192.168.11.0 network.
- A Telnet or SSH session is allowed from any device on the 192.168.10.0 into the router with this access list assigned.
19. What is the function of the pass action on a Cisco IOS Zone-Based Policy Firewall?
- logging of rejected or dropped packets
- inspecting traffic between zones for traffic control
- tracking the state of connections between zones
- forwarding traffic from one zone to another
20. Which command will verify a Zone-Based Policy Firewall configuration?
- show interfaces
- show zones
- show running-config
- show protocols
21. Refer to the exhibit. The network “A” contains multiple corporate servers that are accessed by hosts from the Internet for information about the corporation. What term is used to describe the network marked as “A”?
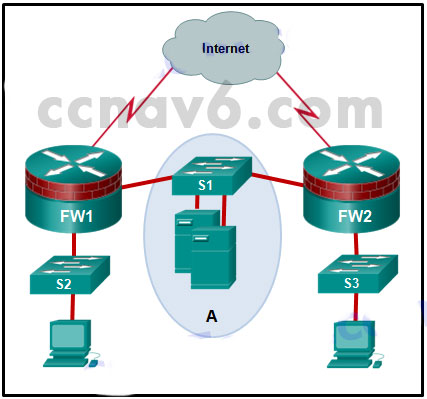
- internal network
- untrusted network
- perimeter security boundary
- DMZ
22. Which type of packet is unable to be filtered by an outbound ACL?
- multicast packet
- ICMP packet
- broadcast packet
- router-generated packet
23. When a Cisco IOS Zone-Based Policy Firewall is being configured, which two actions can be applied to a traffic class? (Choose two.)
- drop
- log
- forward
- hold
- inspect
- copy
24. Fill in the blank.
A stateful firewall monitors the state of connections as network traffic flows into and out of the organization.
25. Fill in the blank.
The pass action in a Cisco IOS Zone-Based Policy Firewall is similar to a permit statement in an ACL.
Download PDF File below:

The options provided for question 18 may have changed.
Consider the following access list.
access-list 100 permit ip host 192.168.10.1 any
access-list 100 deny icmp 192.168.10.0 0.0.0.255 any echo
access-list 100 permit ip any any
Which two actions are taken if the access list is placed inbound on a router Gigabit Ethernet port that has the IP address 192.168.10.254 assigned? (Choose two.)
Fixed, thank you
24.Which security tool monitors network traffic as it flows into and out of the organization and determines whether packets belong to an existing connection or are from an unauthorized source?
*stateful firewall
application proxy
web security appliance
intrusion protection system
25.What is the function of the pass action on a Cisco IOS Zone-Based Policy Firewall?
tracking the state of connections between zones
*forwarding traffic from one zone to another
logging of rejected or dropped packets
inspecting traffic between zones for traffic control