Category: CCNPv8 ENCOR
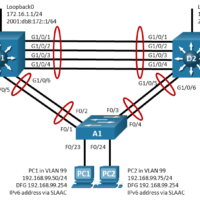
15.1.5 Lab – Implement GLBP (Answers) Topology Addressing Table Device Interface IP Address Default Gateway D1 VLAN 99 192.168.99.1/24 N/A VLAN 99 2001:db8:99::1/64 Loopback 0 172.16.1.1/24 Loopback 0 2001:db8:172::1/64 D2 VLAN 99 192.168.99.2/24 N/A VLAN 99 2001:db8:99::2/64 Loopback 0 172.16.1.1/24 Loopback 0 2001:db8:172::1/64 PC1 NIC 192.168.99.75/24 192.168.99.1 SLAAC …
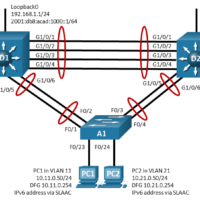
15.1.4 Lab – Implement VRRP (Answers) Topology Addressing Table Device Interface IP Address Default Gateway D1 Lo 0 192.168.1.1/24 N/A 2001:db8:acad:1000::1/64 VLAN 11 10.11.0.1/24 2001:db8:acad:11::1/64 VLAN 21 10.21.0.1/24 2001:db8:acad:21::1/64 D2 Lo 0 192.168.1.1/24 N/A 2001:db8:acad:1000::1/64 VLAN 11 10.11.0.2/24 2001:db8:acad:11::1/64 VLAN 21 10.21.0.2/24 2001:db8:acad:21::2/64 PC1 NIC 10.11.0.50/24 10.11.0.254 IPv6 …
15.1.3 Lab – Implement HSRP (Answers) Topology Addressing Table Device Interface IP Address Default Gateway D1 Lo 0 192.168.1.1/24 N/A Lo 0 2001:db8:acad:1000::1/64 N/A VLAN 11 10.11.0.1/24 N/A VLAN 11 2001:db8:acad:11::1/64 N/A VLAN 21 10.21.0.1/24 N/A VLAN 21 2001:db8:acad:21::1/64 N/A D2 Lo 0 192.168.1.1/24 N/A Lo 0 2001:db8:acad:1000::1/64 …
30. Which two configuration management tools are developed using Python? (Choose two.) Chef Ansible Puppet SaltStack NETCONF 31. Which term is used to describe a set of instructions for execution by the configuration management tool SaltStack? Pillar Manifest Playbook Cookbook 32. What is the maximum number of nodes …
1. What is the function of a hypervisor? to create VMs and provide hardware abstraction to support them to create an isolated environment where containerized applications run to perform FCAPS functions for VNFs to centralize management of vSwitch configuration 2. What are three characteristics of containers on a …
14. A network administrator configures an ACL with the command R1(config)# access-list 1 permit 172.16.0.0 0.0.15.255. Which two IP addresses will match this ACL statement? (Choose two.) 172.16.0.255 172.16.15.36 172.16.16.12 172.16.31.24 172.16.65.21 15. Which service can be disabled to help mitigate man-in-the-middle intrusion attacks that exploit spoofed MAC …
1. Which Cisco security architectural framework helps design secure solutions for the various places in the network (PINs)? Cisco SAFE Cisco DNA Cisco ENFV Cisco NGFW 2. Which Cisco SAFE secure domain is concerned with the technologies involving access control, VPNs, and encryption? secure services security intelligence threat …
25. Which network service allows administrators to monitor and manage network devices? NTP SNMP syslog NetFlow 26. By default, where do Cisco routers send syslog messages? to a syslog server to the VTY lines to the console line to an SNMP server 27. What network monitoring tool copies …
13. Which IGP is used in the automated underlay model of the Cisco SD-Access architecture? IS-IS OSPF EIGRP BGP 14. Which SD-Access functionality replaces manual device configuration with network device management by using Cisco DNA Center for faster, lower-risk deployment? network automation network assurance network virtualization policy enforcement …
1. What is a characteristic of the distribution layer in the three layer hierarchical model? acts as the backbone for the network, aggregating and distributing network traffic throughout the campus provides access to the rest of the network through switching, routing, and network access policies distributes access to …