IT Essentials (Version 8.0) – IT Essentials v8.0 Composite (Chapters 1-14) Exam Answers
IT Essentials (Version 7.00) – IT Essentials 7.01 Final Exam Ch 1 – 14
1. In which situation would an ESD strike potentially cause harm to the PC?
- when replacing a mechanical hard drive with an M.2 SSD
- when installing an additional display in a workplace cubicle
- when using a grounded mat and working on a computer on an ungrounded workbench
- when installing a dual-voltage power supply
Other case
- when installing an additional display in a workplace cubicle
- when replacing high voltage laser printer parts
- while attaching speakers to a surround sound card
- when installing a UPS
- when installing RAM
2. A person has started a new technical job. In which situation would ESD be an issue?
- when installing a processor
- when using a grounded mat and working on a computer on an ungrounded workbench
- when installing a dual-voltage power supply
- while exchanging one laptop AC adapter with one that is not from the original equipment manufacturer
Other case
- when installing RAM
- when installing an additional display in a workplace cubicle
- when replacing high voltage laser printer parts
- while attaching speakers to a surround sound card
3. A technician is about to begin preventive maintenance on a company PC. In which situation would ESD be an issue?
- when replacing a motherboard
- while attaching speakers to a surround sound card
- when using a grounded mat and working on a computer on an ungrounded workbench
- when installing a dual-voltage power supply
4. An instructor has given a student an assignment to assemble a PC. In which situation should the student be aware that ESD is an issue?
- when installing RAM
- when working in a corporate environment that has carpet installed under tower PCs
- when using a grounded mat and working on a computer on an ungrounded workbench
- when installing a dual-voltage power supply
Case 2:
- when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
- when installing a UPS
- when working in a corporate environment that has carpet installed under tower PCs
- when replacing a mechanical hard drive with an M.2 SSD
Case 3:
- when using a grounded mat and working on a computer on an ungrounded workbench
- when working in a corporate environment that has carpet installed under tower PCs
- when installing a processor
- when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
5. What two motherboard components control the system boot operations? (Choose two.)
- BIOS chip
- UEFI chip
- Northbridge chip
- Southbridge chip
- CPU
6. A technician is upgrading an ATX motherboard with another ATX motherboard. Which component might be affected by this and need to be upgraded and bought as an additional purchase?
- BIOS
- chipset
- CMOS battery
- CPU
- PCIe adapter
7. A customer has requested that a PC be built that will support eSATA. Which component should be checked to be sure that this feature is supported?
- CPU
- chipset
- hard disk
- RAM module
8. Which memory module used to hold instructions for booting a PC and loading the OS, but is still used on adapters even though the memory contents cannot be changed?
- RAM
- ROM
- cache
- main memory
9. What is a characteristic of DDR SDRAM?
- It transfers data twice per clock cycle compared to once per clock cycle for SDRAM.
- DDR SDRAM modules have double the number of pins of SDRAM memory modules.
- It is dynamic memory whereas SDRAM is static memory.
- It operates at double the voltage of SDRAM memory.
10. What are two safety hazards when dealing with laser printers? (Choose two.)
- high voltage
- hot components
- heavy metals
- proprietary power bricks
- unwieldy card cages
11. Which component requires a technician to install screws externally through the PC case?
- RAM
- CPU
- motherboard
- power supply
12. A technician is installing an internal HDD. To which motherboard connector will the technician connect the data cable?
- ATX
- PCI
- PWR_SW
- SATA
13. Refer to the exhibit. A technician has been asked to install a video card. Which section of the motherboard will the technician use to install the card?
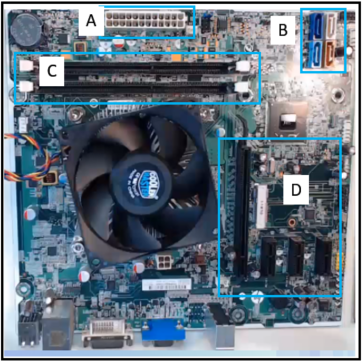
- section A
- section B
- section C
- section D
14. When a PC is being assembled, what component is connected to the motherboard with a SATA cable?
- the optical drive
- the network interface card
- the video card
- the power supply
15. A technician is troubleshooting a computer that is experiencing hardware failure detected by the BIOS. What is one way this failure is indicated?
- The computer automatically boots into Safe Mode and displays a warning on the screen.
- The screen flashes with a red background and displays a warning message.
- The computer emits a pattern of beeps indicating the failing device.
- The computer returns an error message that indicates the I/O address of the failing device.
16. Which three features can be configured in the BIOS settings to secure a computer? (Choose three.)
- MAC filtering
- drive encryption
- TPM
- file encryption
- TKIP key
- passwords
17. What is the purpose of RAID adapters?
- to allow older PCI technology expansion slots to be used
- to provide enhanced audio and graphic capabilities
- to connect multiple storage devices for redundancy or speed
- to connect peripheral devices to a PC to improve performance
18. When a new motherboard is being installed, between which two components must thermal compound be applied? (Choose two.)
- CPU
- RAM
- chassis
- heat sink
- chipset
- motherboard
19. What is the purpose of a Safety Data Sheet?
- to specify procedures for dealing with potentially hazardous materials
- to specify procedures in designing and building common computer systems
- to specify procedures for the operation of sensitive components and prevention of electrostatic discharge
- to specify procedures in the use of humidity control and prevention of moisture damage
20. Which negative environmental factor does cleaning the inside of a computer reduce?
- dust
- EMI
- rust
- ESD
21. What is a recommended procedure to follow when cleaning computer components?
- Remove the CPU before cleaning.
- Blow compressed air on cooling fans so that they will spin when dust is being removed.
- Use window cleaner on LCD screens.
- Hold cans of compressed air upright while spraying.
22. On the production floor, a furniture plant has laptops for process monitoring and reporting. The production floor environment is around 80 degrees Fahrenheit (27 degrees Celsius). The humidity level is fairly high around 70 percent. Fans are mounted in the ceiling for air circulation. Wood dust is prevalent. Which condition is most likely to adversely affect a laptop that is used in this environment?
- the temperature
- the humidity
- the air flow
- the dust
23. After a technician tests a theory of probable causes, what two actions should the technician take if the testing did not identify an exact cause? (Choose two.)
- Establish a new theory of probable causes.
- Randomly replace components one at a time until the problem is solved.
- Document each test tried that did not correct the problem.
- Verify full system functionality.
- Test all remaining possible causes starting with the most complex.
24. What would happen if a PC that contains a power supply that does not automatically adjust for input voltage is set to 230 volts and attaches to an outlet in the United States?
- The power supply would explode.
- The PC would not turn on.
- The PC would display an error code.
- The PC would emit a series of beeps.
25. Which type of network spans a single building or campus and provides services and applications to people within a common organizational structure?
- PAN
- WAN
- LAN
- MAN
26. What are two types of wired high-speed Internet connections? (Choose two.)
- cable
- satellite
- cellular
- DSL
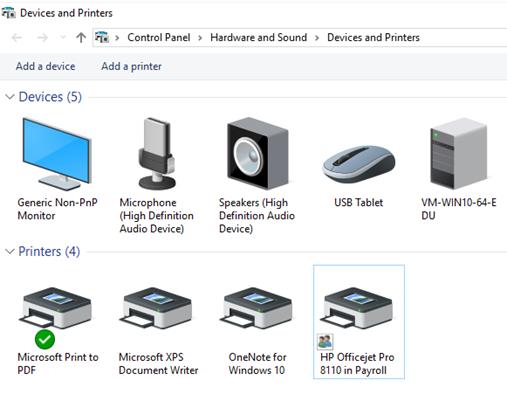
- dial-up
27. In what two situations would UDP be better than TCP as the preferred transport protocol? (Choose two.)
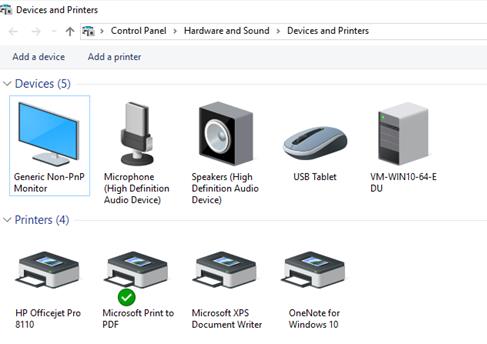
- when applications need to guarantee that a packet arrives intact, in sequence, and unduplicated
- when a faster delivery mechanism is needed
- when delivery overhead is not an issue
- when applications do not need to guarantee delivery of the data
- when destination port numbers are dynamic
28. The current IP configuration of a small company is done manually and is time-consuming. Because of increased network growth, a technician needs a simpler way for IP configuration of workstations. Which service would simplify the workstation IP configuration task?
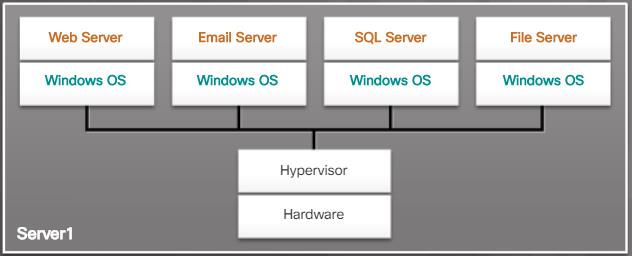
- APIPA
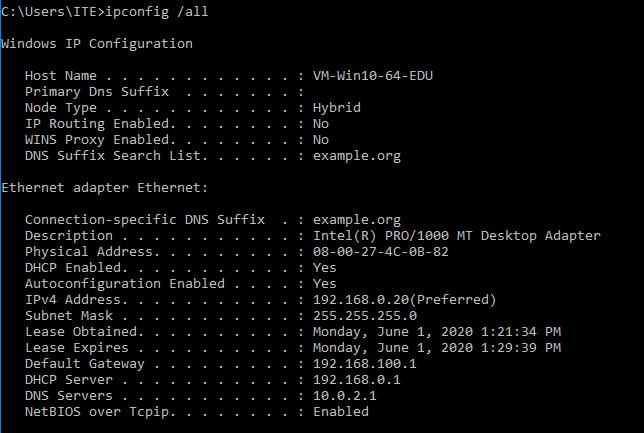
- DHCP
- DNS
- ICMP
29. A company is looking for a next-generation firewall that provides VPN functionality, IDS/IPS functionality, and DoS/DDoS protection. Which device would be best suited for this task?
- multipurpose device
- router
- endpoint management server
- UTM
- TPM
30. A student is helping a friend with a home computer that can no longer access the Internet. Upon investigation, the student discovers that the computer has been assigned the IP address 169.254.100.88. What could cause a computer to get such an IP address?
- static IP addressing with incomplete information
- interference from surrounding devices
- reduced computer power supply output
- unreachable DHCP server
31. What three values must be added to the IPv4 properties of a NIC in order for a computer to have basic connectivity with the network? (Choose three.)
- subnet mask
- DHCP server address
- domain name
- default gateway
- speed and duplex
- IP address
32. A device has an IPv6 address of 2001:0DB8:75a3:0214:0607:1234:aa10:ba01 /64. What is the host identifier of the device?
- 2001:0DB8:75a3
- 0607:1234:aa10:ba01
- 2001:0DB8
- ba01
33. How can a user prevent specific applications from accessing a Windows computer over a network?
- Enable MAC address filtering.
- Disable automatic IP address assignment.
- Block specific TCP or UDP ports in Windows Firewall.
- Change default usernames and passwords.
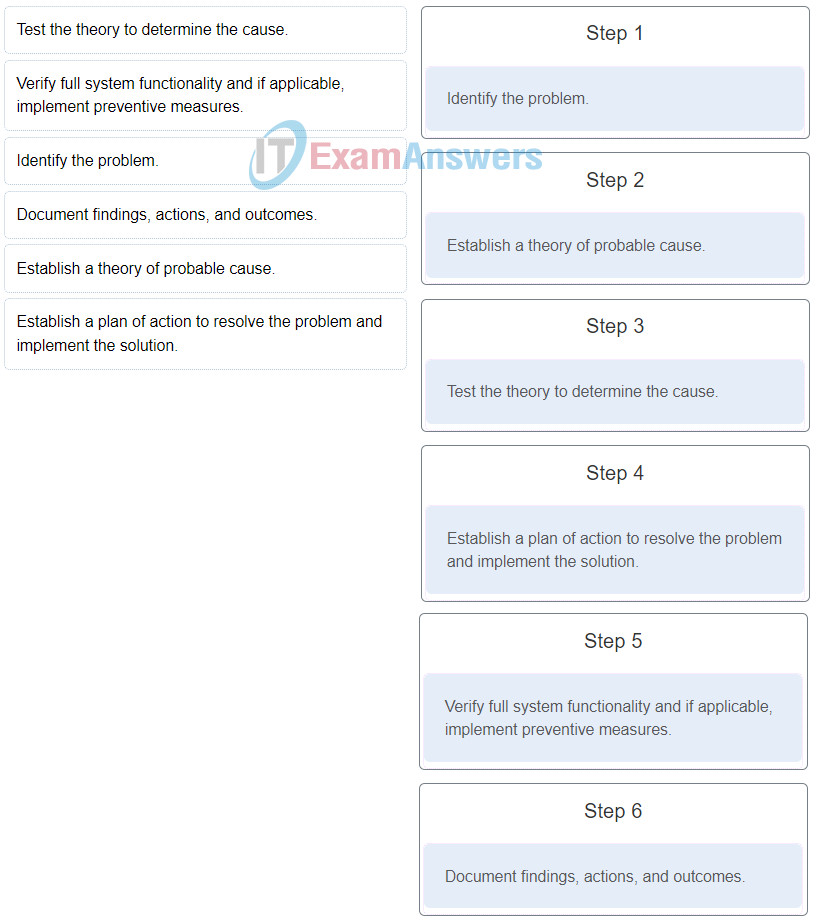
34. Place the six stages of the troubleshooting process in the correct order.
35. A technician has been asked to configure Wi-Fi calling on a corporate mobile device. In which situation would this feature be most advantageous?
- in an emergency situation and no minutes are left on the phone
- when sending WEA updates
- when in an area with poor cellular coverage
- in a store transaction making a payment using the mobile device
36. Which statement is true about laptops?
- Most of the internal components that are designed for laptops cannot be used for desktops.
- Laptop motherboards have standard form factors.
- Laptops use fewer components than desktops use.
- Laptop CPUs do not use cooling devices.
37. Which standard provides a bridge between laptop hardware and the operating system and a way for technicians to configure power management schemes to get the best performance?
- ACPI
- PCIe
- Bluetooth
- 802.11
38. Which two laptop components are considered replaceable by the customer. (Choose two.)
- battery
- integrated card reader
- mini-PCIe module
- RAM
- display
39. A user wants to synchronize some apps, movies, music, and ebooks between mobile devices. What are the two types of connections used to synchronize this type of data? (Choose two.)
- cellular
- Wi-Fi
- USB
- Bluetooth
- NFC
40. A technician is explaining the differences between inkjet printers and laser printers to a customer. Which two comparisons should the technician make? (Choose two.)
- Inkjet printers are less expensive as an initial purchase than laser printers.
- A laser printer is significantly slower than an inkjet printer.
- Both laser and inkjet printers produce poor quality images.
- The laser printer output is dry after printing, but an inkjet printer may still have wet ink on the paper after printing.
- Inkjet printers use plain paper to make economical prints, but laser printers require more expensive thermal paper.
41. A user chooses the collate option and prints two copies of a three-page document. What is the order in which the pages are printed?
- pages 1, 1, 2, 2, 3, 3
- pages 1, 2, 3, 1, 2, 3
- pages 3, 3, 2, 2, 1, 1
- pages 3, 2, 1, 3, 2, 1
42. A color laser printer is used to print documents with graphics and photographs. Users are complaining that printing takes too long. Which component of the printer should be upgraded in order to improve printing performance?
- CPU
- RAM
- hard drive
- toner cartridges
43. What service is available for Windows to provide software print server services to MAC OS clients?
- Bonjour Print Server
- Print to XPS
- Apple AirPort Extreme
- Apple AirPrint
44. Which three components are typically found in laser printer maintenance kits? (Choose three.)
- fuser assembly
- primary corona
- pickup rollers
- transfer rollers
- secondary corona
- paper trays
45. A technician is installing a new printer in a cool, damp environment. After the printer cabling is done, and the software and print driver are installed, the printer test page jams. What is the most likely cause of the print failure?
- incorrect printer driver
- too much humidity
- not enough printer memory
- loose printer cables
46. A data center has recently updated a physical server to host multiple operating systems on a single CPU. The data center can now provide each customer with a separate web server without having to allocate an actual discrete server for each customer. What is the networking trend that is being implemented by the data center in this situation?
- BYOD
- virtualization
- maintaining communication integrity
- online collaboration
47. How does virtualization help with disaster recovery within a data center?
- Power is always provided.
- Less energy is consumed.
- Server provisioning is faster.
- Hardware does not have to be identical.
48. Which two hypervisors are suitable to support virtual machines in a data center? (Choose two.)
- Virtual PC
- VMware Fusion
- VMware ESX/ESXi
- Oracle VM VirtualBox
- Microsoft Hyper-V 2012
49. A web designer accesses a company Windows 10 computer remotely. The designer often needs to simultaneously open multiple applications, such as a web page editor and a graphics editor. Rather than opening them in multiple windows, the designer opens them in different virtual desktops. What technology is being used by the designer?
- virtual reality
- Windows Virtual Desktop
- cloud-based applications
- virtual desktop infrastructure
50. Which Cloud computing service would be best for an organization that needs to collaboratively create applications and deliver them over the web?
- PaaS
- IaaS
- SaaS
- ITaaS
51. Which statement describes a feature of SDRAM?
- It requires constant power to function.
- Its connector always has 240 pins.
- It can process overlapping instructions in parallel.
- It is able to support two writes and two reads per CPU clock cycle.
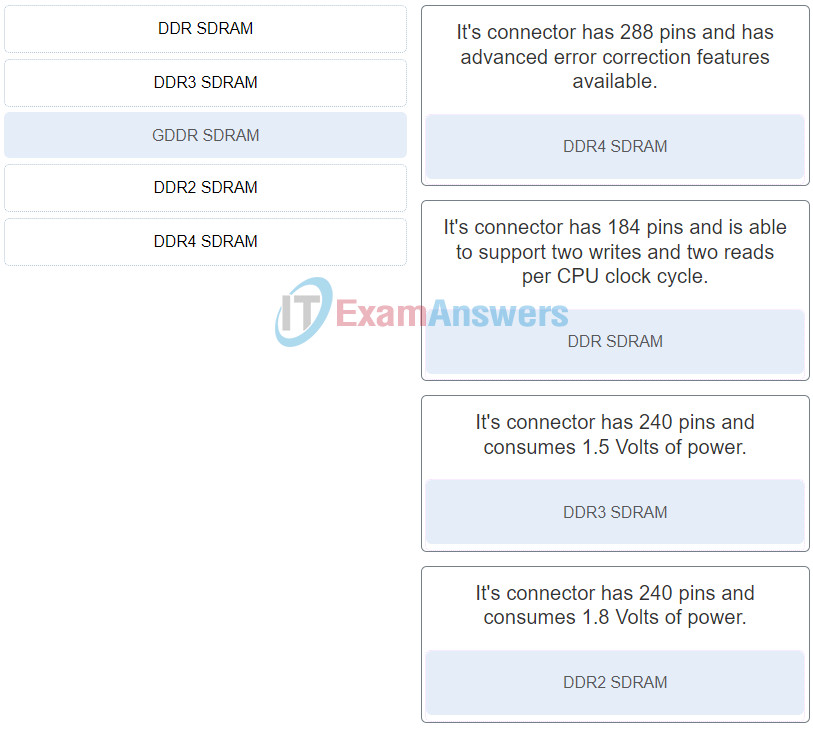
52. Match the memory type to the feature. (Not all options are used.)
53. A technician is troubleshooting a server that displays the error message “RAID not found” after a power outage over the weekend. What is a possible cause for this?
- The BIOS firmware needs updating.
- The FSB settings have changed and are wrong.
- The external RAID controller is not receiving power.
- The CPU multiplier is set too high.
54. A customer brings in a laptop with a touch screen that is not working correctly. The touch screen either does not respond at all or provides unusual or inaccurate responses. What is a possible cause for such behavior?
- The battery is not seated properly.
- The DC jack is not grounded or is loose.
- The digitizer is faulty.
- Too many apps are open.
55. What are two security risks associated with sharing printers in a corporate environment? (Choose two.)
- user authentication
- cached files
- document viewing in the print queue
- dumpster diving
- shoulder surfing
56. Which change management process component is concerned with the business processes that are affected by changes?
- assessment
- approval
- implementation
- identification
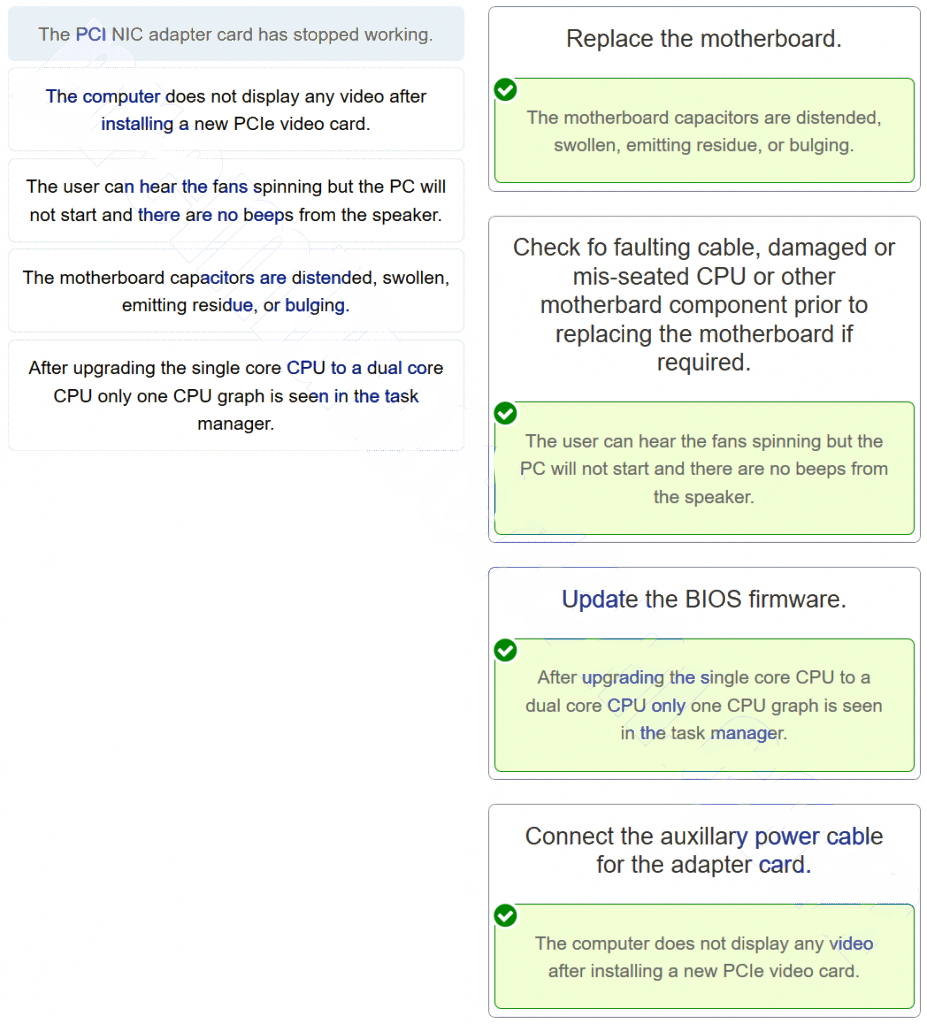
57. Match the problem to the possible solution. (Not all options are used.)
58. A computer technician is installing a RAID. If the RAID uses mirroring and striping, which RAID level is the technician using?
- 10
- 5
- 1
- 8
59. A computer technician is installing a RAID. If the RAID uses mirroring, which RAID level is the technician using?
- 1
- 6
- 5
- 3
60. A computer technician is installing a RAID. If the RAID uses striping with parity, which RAID level is the technician using?
- 5
- 6
- 1
- 4
61. A computer technician is installing a RAID. If the RAID uses striping, which RAID level is the technician using?
- 0
- 6
- 5
- 2
62. A computer technician is installing a RAID. If the RAID uses striping with double parity, which RAID level is the technician using?
- 6
- 1
- 5
- 7
63. A technician is upgrading many PCs used within the company. How should the technician dispose of an old battery?
- Throw it away.
- Take it to the garbage dump.
- Burn it.
- Recycle following local regulations.
64. A technician is upgrading many PCs used within the company. How should the technician dispose of a broken monitor?
- Bury it.
- Recycle following local regulations.
- Take it to the garbage dump.
- Burn it.
65. A technician is upgrading many PCs used within the company. How should the technician dispose of an old power supply?
- Burn it.
- Take it to the garbage dump.
- Recycle following local regulations.
- Bury it.
66. A technician is upgrading many PCs used within the company. How should the technician dispose of old RAM?
- Destroy it with a hammer.
- Burn it.
- Bury it.
- Recycle following local regulations.
67. A technician is upgrading many PCs used within the company. How should the technician dispose of an old motherboard?
- Seal in a plastic bag before putting in the garbage.
- Recycle following local regulations.
- Give it to your neighbor.
- Destroy it with a hammer.
68. A technician is upgrading many PCs used within the company. How should the technician dispose of an old hard drive?
- Seal in a cardboard box.
- Give it to your neighbor.
- Destroy it with a hammer.
- Recycle following local regulations.
69. After continuous morning use, a computer suddenly reboots without the intervention of the user. What are the two most likely hardware parts that could cause this problem? (Choose two.)
- CPU
- hard drive
- RAID
- power supply
- BIOS
- wireless NIC
70. A technician has been called in to investigate a problem with the computer rebooting randomly throughout the day. What two pieces of hardware could cause this problem? (Choose two.)
- power supply
- surge strip
- ROM
- wireless NIC
- motherboard
- CPU
71. For two days in a row, a user has noticed that the computer reboots several times before it eventually starts. What are two suspect components? (Choose two.)
- CPU
- power supply
- BIOS
- ROM
- wireless NIC
- motherboard
72. While a user is working on a spreadsheet, the computer reboots. What are two components that could cause this issue? (Choose two.)
- power supply
- ROM
- BIOS
- RAID
- CPU
- wireless NIC
73. A client packet is received by a server. The packet has a destination port number of 137. What service application is the client requesting?
- NetBIOS (NetBT)
- SMB/CIFS
- HTTPS
- SLP
74. A client packet is received by a server. The packet has a destination port number of 22. What service application is the client requesting?
- SMB/CIFS
- HTTPS
- SLP
- SSH
75. A client packet is received by a server. The packet has a destination port number of 143. What service application is the client requesting?
- IMAP
- SMB/CIFS
- HTTPS
- SLP
76. A client packet is received by a server. The packet has a destination port number of 23. What service application is the client requesting?
- SMB/CIFS
- Telnet
- HTTPS
- SLP
77. A client packet is received by a server. The packet has a destination port number of 161. What service application is the client requesting?
- SNMP
- SMB/CIFS
- HTTPS
- SLP
78. A client packet is received by a server. The packet has a destination port number of 389. What service application is the client requesting?
- SMB/CIFS
- HTTPS
- SLP
- LDAP
79. A client packet is received by a server. The packet has a destination port number of 25. What service application is the client requesting?
- SMB/CIFS
- HTTPS
- SMTP
- SLP
80. A client packet is received by a server. The packet has a destination port number of 427. What service application is the client requesting?
- SLP
- SMB/CIFS
- SMTP
- DNS
81. A client packet is received by a server. The packet has a destination port number of 53. What service application is the client requesting?
- SMTP
- DHCP
- TFTP
- DNS
82. Which is the compressed format of the IPv6 address 2001:0db8:0000:0000:0000:a0b0:0008:0001?
- 2001:db80:0:1::80:1
- 2001:db8::a0b0:8:1
- 2001:db8::ab8:1:0:1000
- 2001:db80:::1::80:1
83. Which is the compressed format of the IPv6 address fe80:09ea:0000:2200:0000:0000:0fe0:0290?
- fe80:9ea:0:2200::fe0:290
- fe80:9:20::b000:290
- fe80:9ea0::2020:0:bf:e0:9290
- fe80:9ea0::2020::bf:e0:9290
84. Which is the compressed format of the IPv6 address 2002:0042:0010:c400:0000:0000:0000:0909?
- 200:420:110:c4b::910:0:90
- 2002:4200::25:1090:0:99
- 2002:42::25:1090:0:99
- 2002:42:10:c400::909
85. Which is the compressed format of the IPv6 address 2002:0420:00c4:1008:0025:0190:0000:0990?
- 2002:4200::25:1090:0:99
- 2002:420:c4:1008:25:190::990
- 2002:42:10:c400::909
- 2002:42::25:1090:0:99
86. Which is the compressed format of the IPv6 address 2001:0db8:0000:0000:0ab8:0001:0000:1000?
- 2001:db8::a0b0:8:1
- 2001:db8:1::ab8:0:1
- 2001:db8:0:1::8:1
- 2001:db8::ab8:1:0:1000
87. Which is the compressed format of the IPv6 address fe80:0000:0000:0000:0220:0b3f:f0e0:0029?
- fe80::220:b3f:f0e0:29
- fe80:9ea0::2020:0:bf:e0:9290
- fe80:9ea:0:2200::fe0:290
- fe80:9ea0::2020::bf:e0:9290
88. Which is the compressed format of the IPv6 address fe80:9ea0:0000:2020:0000:00bf:00e0:9290?
- fe80:9:20::b000:290
- fe80:9ea:0:2200::fe0:290
- fe80:9ea0::2020:0:bf:e0:9290
- fe80::0220:0b3f:f0e0:0029
89. What ACPI power state describes when the CPU and RAM are off and the contents of RAM have been saved to a temporary file on the hard drive?
- S4
- S1
- S2
- S3
90. What ACPI power state describes when the CPU and RAM are still receiving power but unused devices are powered down?
- S1
- S2
- S3
- S4
91. What ACPI power state describes when the CPU is off, but the RAM is refreshed?
- S1
- S2
- S3
- S4
92. What ACPI power state describes when the computer is off?
- S1
- S2
- S3
- S5
93. What ACPI power state describes when the CPU is off and the RAM is set to a slow refresh rate, often called suspend mode?
- S4
- S2
- S3
- S5
94. What ACPI power state describes when the computer is on and the CPU is running?
- S0
- S4
- S3
- S5
95. A reporter is trying to print several high resolution photographs but the color laser printer is going extremely slowly. What should the technician do to resolve the issue?
- Rewind the ribbon.
- Connect the printer using wireless.
- Install a USB hub.
- Add more RAM to the printer.
- Update the BIOS.
96. A new printer has just been installed deep in a mine. When test pages are printed, the paper constantly jams. What should the technician do to resolve the issue?
- Move the printer to a less-humid location.
- Clean the printer.
- Connect the printer using wireless.
- Install a USB hub.
- Update the BIOS.
97. A user complains that recently every printed document has vertical lines and streaks on the paper. What should the technician do to resolve the issue?
- Distribute the toner more evenly within the cartridge.
- Clean the printer.
- Connect the printer using wireless.
- Install a USB hub.
- Update the BIOS.
98. A school is installing a new shared printer but the printer is not showing up on the list of available printers. What should the technician do to resolve the issue?
- Reset the page counter.
- Manually add the printer IP address.
- Connect the printer using wireless.
- Install a USB hub.
- Update the BIOS.
99. Employees are complaining that they send print jobs to a newly installed printer but the print jobs never print. What should the technician do to resolve the issue?
- The printer is connected to the wrong port. Modify the port.
- Check the vibration of the crystals.
- Connect the printer using wireless.
- Install a USB hub.
- Update the BIOS.
100. Users have noticed that the colors on their printed documents are different from the colors that they see on their computer screens. What should the technician do to resolve the issue?
- Install a USB hub.
- Reset the page counter.
- Check the vibration of the crystals.
- Connect the printer using wireless.
- Calibrate the printer.
101. A technician has just completed a preventive maintenance on the department printer. Users are now complaining that the printer is no longer available. What should the technician do to resolve the issue?
- Check that the printer is plugged into a power source.
- Connect the printer using wireless.
- Reset the page counter.
- Check the vibration of the crystals.
- Install a USB hub.
102. Employees of a small business are complaining that the printer is printing faded images. What should the technician do to resolve the issue?
- Replace the toner cartridge.
- Update the BIOS.
- Reset the page counter.
- Check the vibration of the crystals.
- Install a USB hub.
103. A photographer is complaining about the following printer issue: The printer issues a “Document failed to print” message. What are two possible causes of this issue? (Choose two.)
- A cable is loose or disconnected.
- The paper tray is flimsy.
- The printer is no longer shared.
- The laser printer is emitting too much radiation.
- The wrong printer type has been selected.
104. A reporter is complaining about the following printer issue: The printer is printing unknown characters. What are two possible causes of this issue? (Choose two.)
- The wrong or an outdated printer driver is installed.
- The laser printer is emitting too much radiation.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
- The printer has a loose connection.
105. A manager is complaining about the following printer issue: The printer is printing incorrect colors. What are two possible causes of this issue? (Choose two.)
- An incorrect cartridge could be installed.
- The printer is using the wrong cable.
- The printer has been installed on the wrong port.
- The print heads might need to be cleaned and calibrated.
- The paper tray is flimsy.
106. A technician is complaining about the following printer issue: The print appears faded on the paper. What are two possible causes of this issue? (Choose two.)
- The paper might be incompatible with the printer.
- The wrong printer type has been selected.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
- The toner cartridge is low.
107. A librarian is complaining about the following printer issue: The printer control panel displays no image. What are two possible causes of this issue? (Choose two.)
- The contrast of the screen may be set too low.
- The printer is not turned on.
- The room temperature is above normal.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
108. A teacher is complaining about the following printer issue: The paper is creased after printing. What are two possible causes of this issue? (Choose two.)
- The paper-feed tray might not be firmly adjusted against the edges of the printer.
- Print jobs are being sent to the wrong printer.
- The printer has been installed on the wrong port.
- The paper might be loaded incorrectly.
- The paper tray is flimsy.
109. A receptionist is complaining about the following printer issue: My impact printer produces faded or light characters. What are two possible causes of this issue? (Choose two.)
- The ribbon may be worn out.
- The ribbon may be damaged.
- The print queue is overloaded.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
110. A photographer is complaining about the following printer issue: The paper is not being fed into the printer. What are two possible causes of this issue? (Choose two.)
- The paper may be wrinkled.
- The paper tray is flimsy.
- The printer could be set to print to a different paper size than is currently loaded.
- The printer has been installed on the wrong port.
- The printer service is stopped or not working properly.
111. A laptop has an NVMe drive (C:) and a mechanical hard drive (D:). When the user tries to save a spreadsheet to the D: drive, the user notices that the D: drive is not there. What should the technician do to see if the drive is recognized by the operating system?
- Use the Msconfig utility.
- Boot into UEFI/BIOS and see if the drive appears.
- Remove the drive and attach it to the SATA port used by the SSD. Reboot the computer and see if the drive is recognized.
- Use the Disk Management Control Panel.
112. A computer has two mechanical hard drives. The second drive (D:) is used for data storage. When trying to save an email attachment to the local hard drive, the user notices that the D: drive is not an option. What should the technician do to see if the drive is recognized by the operating system?
- Use File Explorer.
- Swap the data cables of the mechanical drive and the SSD.
- Open a web browser and type the following: http://127.0.0.1. Verify if both drives appear in the list.
- Bring up a command prompt and type ipconfig.
113. A user reports that a drive is no longer there. The technician asks the user to demonstrate the problem. Within the application, the user demonstrates that the drive, that was present in the save options yesterday, is now no longer an option. What should the technician do to see if the drive is recognized by the operating system?
- Use Device Manager.
- Check the Startup folder.
- Bring up a command prompt and type ipconfig.
- Swap the data cables of the mechanical drive and the SSD.
114. A computer has an SSD for the operating system and applications and uses another mechanical hard drive for data storage. The user reports that data can no longer be saved to the mechanical hard drive. What should the technician do to see if the drive is recognized by the operating system?
- Swap the data cables of the mechanical drive and the SSD.
- Use File Explorer.
- Open a web browser and type the following: http://127.0.0.1. Verify if both drives appear in the list.
- Bring up a command prompt and type ipconfig.
115. A technician is working on a laptop and the GPS is not functioning. What is a probable cause for this situation?
- The GPU is overheating.
- A service is disabled.
- The screen resolution needs recalibration.
- The screen refresh rate is too low.
116. A technician is working on a laptop and an app is not loading. What is a probable cause for this situation?
- An app needs to be restarted.
- More than one app is open simultaneously.
- The screen resolution needs recalibration.
- The screen refresh rate is too low.
117. A technician is working on a laptop and an app is not responding. What is a probable cause for this situation?
- The battery is low.
- The GPU is overheating.
- An app needs to be restarted.
- Wi-Fi is turned off.
118. A technician is working on a laptop and an error message about decryption appears when opening an email. What is a probable cause for this situation?
- The display setting is incorrect.
- The GPU is overheating.
- Wi-Fi is turned off.
- A digital certificate is missing.
119. A PC technician has been asked by a supervisor to recommend a security solution for a small company that wants stateful firewall services. Which security technique should the technician recommend?
- Buy an ASA.
- Disable ports.
- Use a VPN.
- Setup footprinting.
120. A gamer is booting a desktop that has Windows 10 installed on dynamic drives. The boot process is currently working on the following step: WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers. What is the next step that will happen in the boot process?
- The Windows kernel takes over the boot process.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
- Winload uses the path specified in BOOTMGR to find the boot partition.
121. A technician is working on a laptop and an error message about decryption appears when opening an email. What is a possible solution for this situation?
- Install an appropriate certificate.
- Check the screen refresh rate.
- Ensure that only one app is open at a time.
- Ensure that Wi-Fi is turned off.
122. Users in the sales department want to be able to print from laptops and tablets. Which two wireless technologies should the IT technician look for when researching new printers for the sales department? (Choose two.)
- cellular
- Bluetooth
- ZigBee
- NFC
- 802.11 standard
123. What are three factors to consider when purchasing a replacement motherboard? (Choose three.)
- The existing power supply must provide the connections required by the new motherboard.
- The new motherboard must be the correct size to physically fit into the existing case.
- The replacement motherboard must have the same manufacturer as the existing case.
- The new motherboard must come from the same manufacturer as the existing motherboard.
- The socket and chipset on the new motherboard must match the existing CPU.
- The new motherboard must support the same UEFI BIOS as the previous motherboard.
124. What are two features of protocols used within the TCP/IP protocol stack? (Choose two.)
- TCP mechanisms retransmit data when an acknowledgment is not received from the destination system within a set period of time.
- UDP is used when an application must be delivered as quickly as possible and some loss of data can be tolerated.
- The Internet Layer IP protocol has built in mechanisms for ensuring the reliable transmission and receipt of data.
- The same Transport Layer source port is used for all of the tabs opened at the same time within a web browser.
- TCP and UDP destination port numbers are dynamically generated by the sending device in order to track the responses to requests.
125. A technician is working on a laptop and a key on the keyboard is not responding as it should. What is a possible solution for this situation?
- Clean with compressed air.
- Ensure that Bluetooth is not activated.
- Check the screen refresh rate.
- Check the display settings.
126. What two effects might suggest that an incorrect printer driver is loaded on the Windows PC? (Choose two.)
- The printer is printing unknown characters.
- Print jobs appear in the print queue, but are not printed.
- Toner is smearing or rubbing off the page.
- The printer does not print a test page.
- Paper jams are occurring frequently.
127. Why would a network technician change the wireless router IP address to a different private IP address during initial installation?
- to enable the router to become the DHCP server for the network and to perform NAT
- to limit the number of devices and users that can attach to the wireless network
- to ensure that users will have to manually configure the network name in their wireless clients
- to decrease the likelihood that someone could access the router using the default settings
- to strengthen the network mode login security and encryption settings
128. A technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?
- Verify that airplane mode is not activated.
- Ensure that Wi-Fi is turned off.
- Check the screen refresh rate.
- Check the display settings.
Case 2:
- Verify the status of service.
- Ensure that only one app is open at a time.
- Recharge the battery.
- Check the display settings.
129. Which factor can limit the amount of data that the CPU can receive and process at one time?
- whether CPU virtualization is enabled
- the width of the front side bus (FSB)
- the size of the CPU cache memory
- the amount of RAM memory installed
130. Which type of optical drive supports the greatest amount of storage and is able to read and write CDs, DVDs, and Blu-Ray media?
- BD-ROM
- BD-RE
- CD-RW
- DVD-RW
- DVD-ROM
132. Why would a manager need to use the sfc command?
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to move that file to a different Windows directory while also leaving the file in the current location
- to copy a group of files from one Windows directory to another
- to relocate a file from one Windows directory to another one
133. Why would a technician need to use the DISM command?
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
- to move that file to a different Windows directory while also leaving the file in the current location
- to copy a group of files from one Windows directory to another
- to relocate a file from one Windows directory to another one
134. Why would a technician need to use the tasklist command?
- to display a list of current processes running on a local or a remote computer
- to create a new Windows directory
- to remove an empty directory
- to change from the current working folder to another folder
135. Why would an analyst need to use the taskkill command?
- to end one or more processes on a PC based on process ID or image name
- to create a new Windows directory
- to remove an empty directory
- to change from the current working folder to another folder
136. Why would an analyst need to use the msconfig command?
- to select some programs that will automatically run at startup
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
137. Why would an analyst need to use the dir command?
- to show all of the files in the current directory
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
138. Why would a bank manager need to use the gpupdate command?
- to make the PC synchronize with new group policy settings
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
139. Why would a bank manager need to use the gpresult command?
- to verify the settings that are suspected to be incorrect
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
140. Why would a lawyer need to use the cd command?
- to change from the current working folder to another folder
- to remove an empty directory
- to erase one or more files from a Windows directory
- to create a new Windows directory
141. Which two activities are normally controlled by the Northbridge part of the chipset? (Choose two.)
- communication between the CPU and the I/O ports
- access to the RAM
- communication between the CPU and the hard drive
- access to the video card
- communication between the CPU and the sound card
142. A manager is booting a tablet that has Windows 8 installed. The boot process is currently working on the following step: WINLOGON.EXE displays the Windows Welcome screen What is the next step that will happen in the boot process?
- There are no more steps, the boot process is complete.
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager.
- Winload uses the path specified in BOOTMGR to find the boot partition.
143. An analyst is booting a tablet that has Windows 7 installed with media card reader. The boot process is currently working on the following step: WINLOGON.EXE displays the Windows Welcome screen What is the next step that will happen in the boot process?
- There are no more steps, the boot process is complete.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- The Windows kernel takes over the boot process.
144. Match the function performed by an OS to its description.
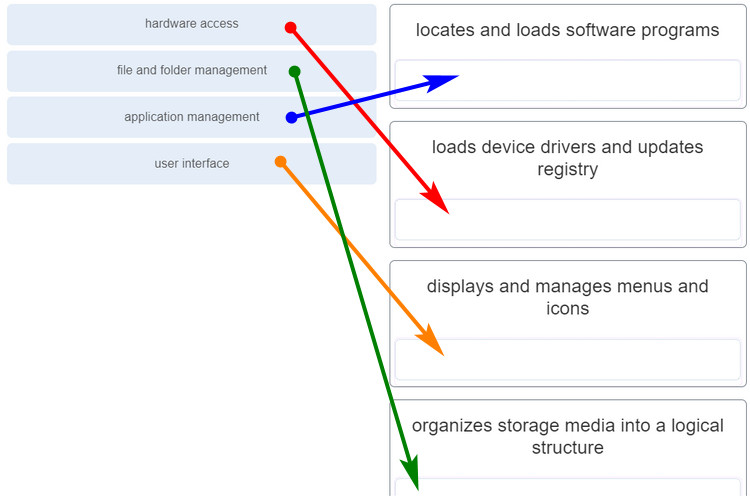
- hardware access — loads device drivers and updates
- file and folder management — organizes storage media into a logical structure
- application management — locates and loads software programs
- user interface — displays and manages menus and icons
145. Before installing the latest version of printer management software, an IT technician creates a restore point on the Windows 10 computer. The installation fails before it is complete, and now the printer shows as unavailable. Which Windows option should the technician use to reverse the software installation and return the system to its prior state without affecting users files and settings?
- Backup and Restore
- System Restore
- File History
- Registry editor
146. A new customer asks if all of its older company computers, which are still running Windows XP, can be immediately upgraded to Windows 10. What are two important concerns that the IT technician must discuss with the customer in order to determine if the OS upgrade can be done? (Choose two.)
- the availability of wireless 802.11 standards support in the new OS
- OS support for new printers and scanners they may purchase
- compatibility of existing applications and custom software with the new OS
- the timeframe for the end of support for Windows 10
- minimum memory and processor requirements for Windows 10
147. Which three wireless router settings should be disabled as a security best practice? (Choose three.)
- UPnP support
- WPS auto configuration
- SSID broadcast
- MAC address filtering
- parental controls
- 802.11i authentication
148. Match the Android or Apple element to its description.
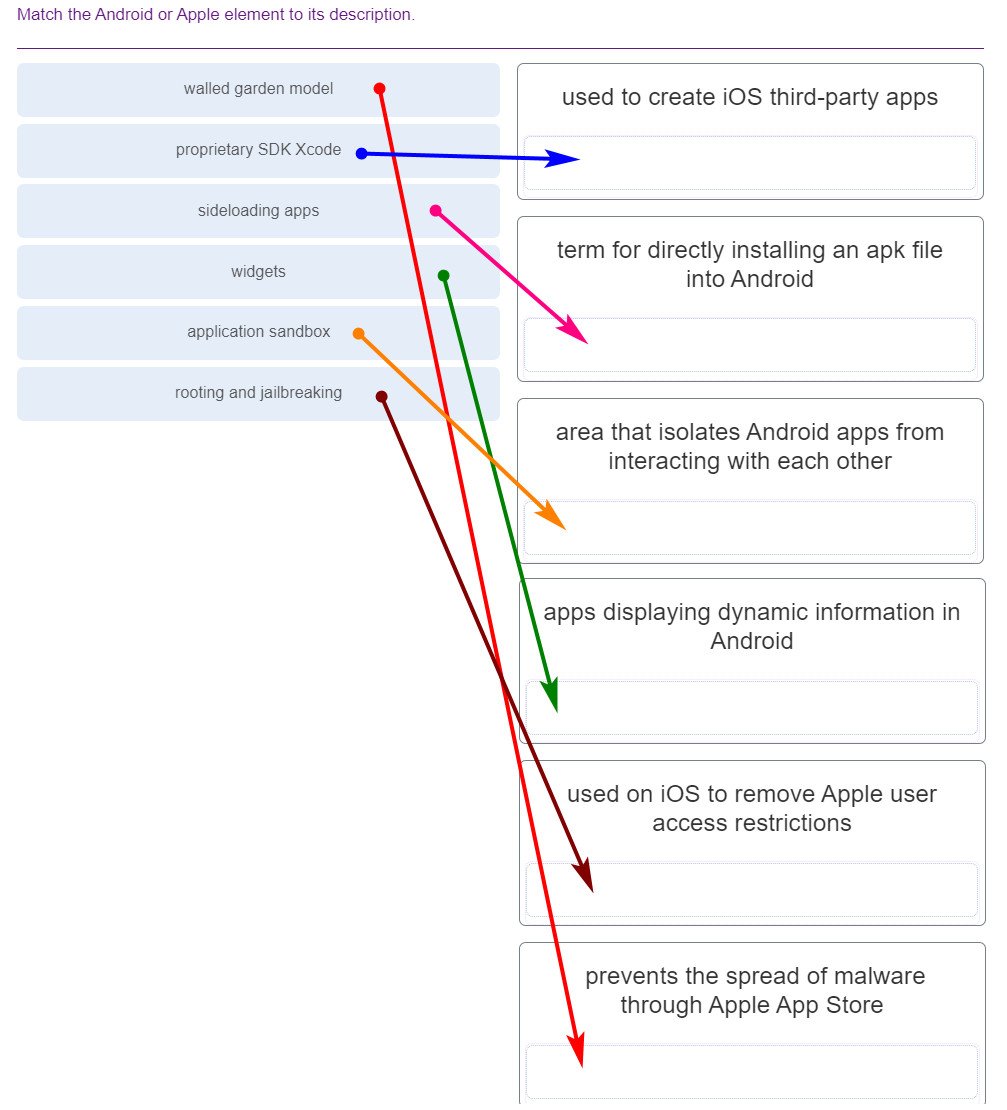
- walled garden model — prevents the spread of malware through Apple App Store
- proprietary SDK Xcode — used to create iOS third-party apps
- sideloading apps — term for directly installing an apk file into Android
- widgets — apps displaying dynamic information in Android
- application sandbox — area that isolates Android apps from interacting with each other
- rooting and jailbreaking — used on iOS to remove Apple user access restrictions
149. What are two symptoms that indicate that a computer system may be a victim of DNS spoofing? (Choose two.)
- The output of the nslookup command reports an unknown resolver name and IP address.
- Entering www.cisco.com in a browser displays a popular gaming site instead of the Cisco homepage.
- System files have been renamed and some user files are missing from the computer hard drive.
- The user receives Access Denied errors when attempting to download files from the network servers.
- A user is receiving thousands of junk emails each day and contacts report receiving spam from the user.
150. A PC technician has been asked by a supervisor to recommend a security solution for preventing tailgating. Which security technique should the technician recommend?
- Employ ping sweeps.
- Use a mantrap.
- Buy an ASA.
- Buy an IPS.
151. Match the computer or peripheral problem with a probable cause of the issue.
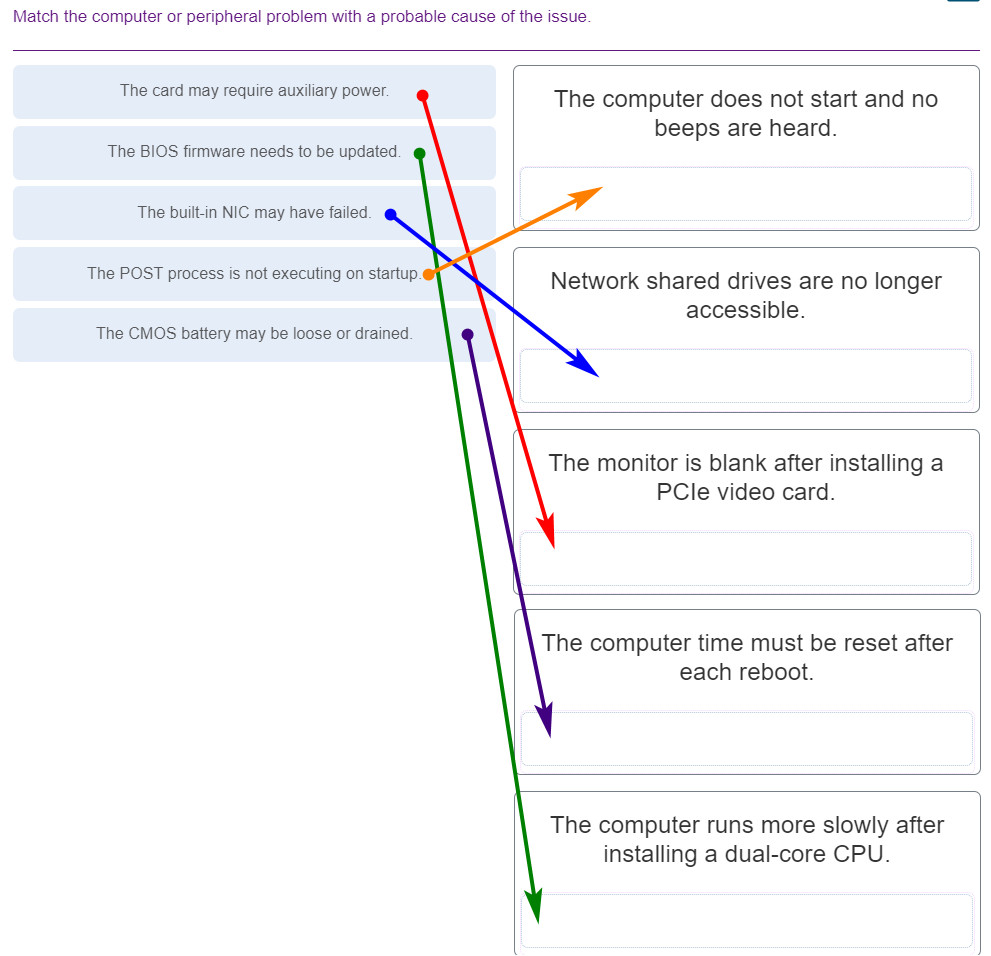
- The card may require auxiliary power. — The monitor is blank after installing a PCle video card.
- The BIOS firmware needs to be updated. — The computer runs more slowly after installing a dual-core CPU.
- The built-in NIC may have failed. — Network shared drives are no longer accessible.
- The POST process is not executing on startup. — The computer does not start and no beeps are heard.
- The CMOS battery may be loose or drained. — The computer time must be reset after each reboot.
152. A company contracts with a service provider to obtain IaaS and ITaaS services. What are two advantages of these types of cloud service implementation? (Choose two.)
- increased control over the types of equipment purchased
- less internet bandwidth required for the LAN
- fewer switch ports needed to connect LAN users
- less investment in local equipment and training
- protection from costly upgrades and software licenses
153. What are two methods of disabling cellular data when located in an area where it is limited or expensive? (Choose two.)
- turning on a personal hotspot
- enabling Bluetooth for data connections
- using a secure VPN connection
- placing the device in Airplane mode
- using Settings to turn off mobile data
154. Refer to the exhibit. A computer technician creates a bootable USB hard drive and loads a Linux operating system on it. When the technician reboots the computer, it does not boot to the Linux OS. Instead, the light on the optical drive flashes and then the computer loads Windows. What needs to be done to ensure that the computer automatically boots from the USB hard drive if it is connected?
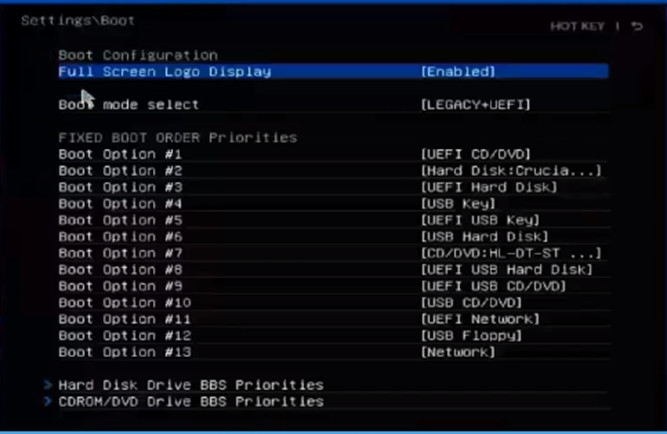
- Move the USB Key option to the top of boot order.
- Move the CD/DVD drive to the bottom of the boot order.
- Move both the CD/DVD and the hard disk options to the bottom of the boot order.
- Move the USB Hard Disk drive option to the top of the boot order.
155. A help desk technician receives a call from a user describing an issue with a computer. The user states that the computer will not power on, that it only makes a beeping sound. Why does the technician ask the user to restart the system and count how many beeps the computer makes?
- Different numbers of beeps can indicate different types of hardware issues discovered during POST.
- Fewer than 4 beeps usually indicate a problem with software loaded on the computer.
- The number of beeps indicates the severity of the hardware issue–more beeps mean a more severe problem.
- The number of beeps relates to beep codes that are standardized across all manufacturers.
156. A college uses Microsoft 365 Office and email services for its faculty, staff, and students. Data storage, custom applications, and Microsoft Active Directory services are delivered by virtual servers leased from a local data center. Single sign-on is implemented for both environments for authentication and authorization. Access control is managed locally. What type of cloud service implementation is the college using?
- hybrid cloud
- community cloud
- public cloud
- private cloud
157. The help desk receives a call from a customer who reports a computer issue that occurs after trying to install Windows 10 with a disc that the IT department provided. When the customer reboots the computer, instead of loading Windows, the computer displays the Windows installation program screen again. Which probable cause should the IT technician place at the top of the list of most obvious reasons for the error?
- The Windows 10 installation did not complete correctly.
- The boot order in the BIOS is incorrect.
- The hard drive in the computer is beginning to fail.
- The customer forgot to remove the disc from the optical drive.
158. Office workers in a software company are being temporarily relocated to a different area of the building while their previous office space is being reconfigured. Which type of network device should be installed to make it easy for the users to connect to the company network from all of their devices, including smart phones, tablets, and laptops?
- hub or repeater
- network switch
- access point
- modem
159. What is an example of an active cooling solution for a desktop PC?
- reducing the speed at which the CPU operates
- applying thermal paste on top of the CPU
- adding a heat sink on top of the CPU
- installing case and CPU cooling fans
160. What is a consequence of a computer not having enough RAM memory installed?
- Data may be swapped between the RAM and the slower hard drive more frequently.
- Data and program code may be swapped between RAM and faster EEPROMs.
- USB flash memory can be used instead of RAM to improve performance.
- Programs and files can be held temporarily on ROM chips on the motherboard.
161. Refer to the exhibit. A payroll department employee has shared a locally attached HP Officejet Pro 8110 printer over the network in Windows 10. What do the other Windows 10 users in the payroll department have to do in order to print to the shared printer?
- Enable File and printer sharing in the Network and Sharing Center > Advanced sharing settings screen.
- Nothing. The shared printer will automatically appear in the Devices and Printers listing when someone logs in.
- Download and install the latest HP Officejet Pro 8110 driver for Windows 10 from the HP web site.
- Use the Add a printer option and select the HP Officejet Pro 8110 in Payroll printer in the Select a printer screen.
162. Which type of power supply is the most commonly used and provides a separate power connection in order to directly power the CPU?
- ATX
- AT
- EPS12V
- ATX12V
163. Refer to the exhibit. A user calls the help desk to report a printer issue. The user explains that when selecting the print option from the menu bar, a dialog box pops up requesting a file name. After entering the filename, nothing prints on the attached HP printer. What is the cause of the issue that the user is experiencing?
- The HP printer is off-line or disconnected.
- The HP printer is not reachable over the network.
- The default printer is a virtual printer.
- An incorrect printer driver is loaded.
164. Which function is incorporated into some Intel CPUs that enables a single CPU to perform as though two CPUs are installed?
- overclocking
- HyperTransport
- Hyper-Threading
- 64-bit FSB
165. Which cloud computing characteristic enables multiple tenants to share the same storage, processing, and network bandwidth?
- on-demand provisioning
- client-side emulation
- broad network access
- resource pooling
166. Which three types of external ports can be used to connect an external storage device to a computer? (Choose three.)
- Thunderbolt
- USB
- eSATA
- SATA
- DVI
- HDMI
167. Which three computer components require separate cabling for power? (Choose three.)
- video graphics cards
- USB flash drives
- internal SATA hard drives
- case and CPU fans
- PS2 or USB keyboards
- wireless network adapters
168. In which two situations would thin clients be a good choice to meet the end-user computing needs? (Choose two.)
- when it is necessary for employees to store large amounts of information for off-line access
- in branch offices located in rural areas where broadband Internet is either not available or not reliable
- when it is necessary for employees to use tablets with minimal storage and processing capabilities
- when installed in an enterprise environment where there is a gigabit LAN and powerful servers
- in a small business where employees must install and maintain their own application software
169. Refer to the exhibit. Which two hypervisor software products are suitable for the virtualization environment shown in the exhibit? (Choose two.)
- Oracle VirtualBox
- Virtual PC
- VMware Workstation
- VMware vSphere
- Oracle VM Server
170. Refer to the exhibit. The help desk is receiving numerous calls from employees in the payroll department. It appears that their computers can print to the local network printer, but cannot access the cloud-based payroll service. One employee sends a screen print showing the result of issuing an ipconfig /all command. What is the cause of the issue being experienced by the users?
- The DHCP server is configured with the wrong default gateway address.
- The DHCP server is down or unreachable over the network.
- No DNS server is configured for this network.
- The static IP configuration on the payroll department PCs is incorrect.
- The PCs are using IPv6 as the preferred communication protocol.
171. An employee recently purchased a smartwatch. Following the instructions from the watch manufacturer, the employee downloads the wearable app and installs it on an Android phone. The smartwatch shows that it is in discoverable mode, but the app cannot connect to the watch. What is one issue that might cause this problem?
- 5G is not active on the Android phone.
- NFC communications is not enabled on the smartwatch.
- The new smartwatch WiFi connection is faulty.
- Bluetooth is disabled on the Android phone.
172. Which member of the DDR SDRAM family has the fastest clock rate and consumes the least amount of power?
- GDDR5 SDRAM
- DDR3 SDRAM
- DDR4 SDRAM
- DDR2 SDRAM
173. Refer to the exhibit. What is one function that a technician can accomplish using this graphical interface?

- configure a wireless SSID and password
- set passwords to allow for access to the BIOS
- change screen resolution and lock screen settings
- change the amount of power provided to USB ports
174. A network technician suspects that there may be a short or a termination error in the wiring that connects an Ethernet switch to the network. Which tool would be the best choice for the technician to use to identify the issue?
- loopback adapter
- tone generator and probe
- cable tester
- multimeter
175. A client packet is received by a server. The packet has a destination port number of 110. What service application is the client requesting?
- HTTP
- POP3
- NetBIOS (NetBT)
- SMB/CIFS
176. Why would a university student need to use the taskkill command?
- to display a list of current processes running on a local or a remote computer
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to end one or more processes on a PC based on process ID or image name
177. Which term describes a partition scheme that supports storing a backup of a partition table?
- basic disk
- GPT
- logical drive
- dynamic disk
178. How can a hard drive that is using an MBR be partitioned in order to support additional logical drives?
- Expand the size of the active partition into unallocated space available on the drive.
- Make one primary partition an extended partition to contain the logical drives.
- Create multiple logical partitions within the active partition.
- Create a large dynamic volume that spans more than one disk.
179. A computer technician uses Windows tools to gather information such as system components, operating system, users, and disk drives on multiple systems within the company. Another technician suggests that the tasks would take less time if they were automated. Which two built-in scripting capabilities in Windows enable a technician to run a simple text file, created in Notepad, which contains the necessary commands and variables? (Choose two.)
- PowerShell ISE script interpreter
- command line batch script interpreter
- Linux Bash shell script interpreter
- JavaScript client-side scripting language
- C++ and C# built-in compiler
180. Match the IT policy type with its description.
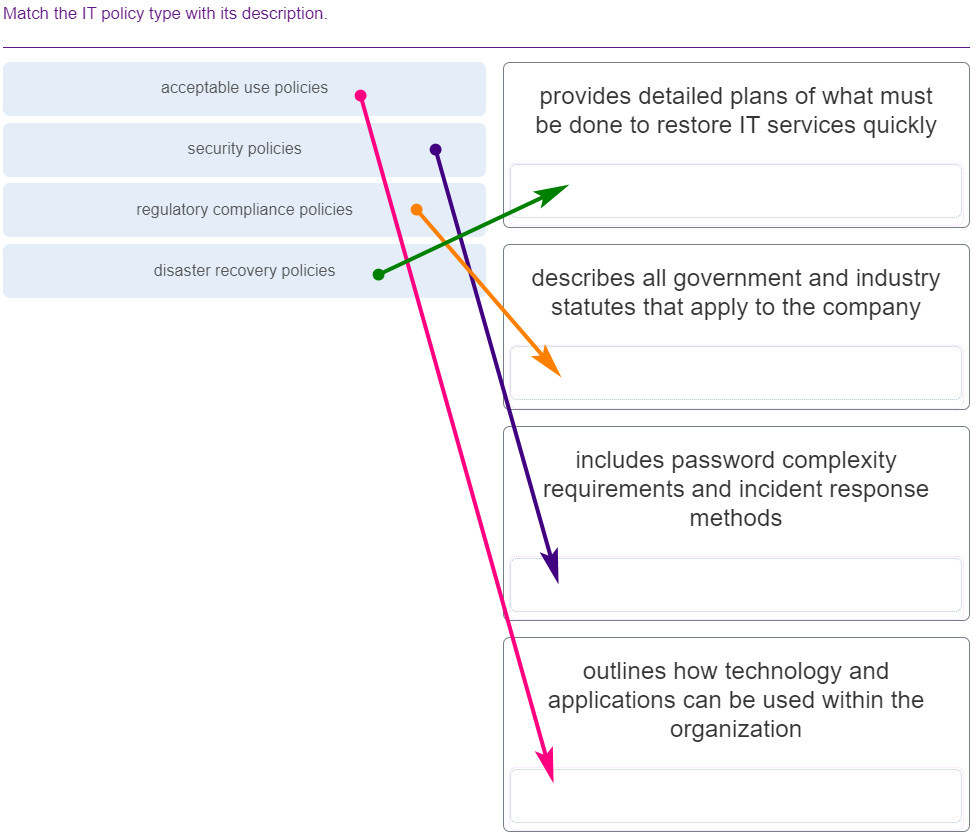
- acceptable use policies — outlines how technology and applications can be used within the organization
- security policies — includes password complexity requirements and incident response methods
- regulatory compliance policies — describes all government and industry statutes that apply to the company
- disaster recovery policies — provides detailed plans of what must be done to restore IT services quickly
181. Refer to the exhibit. Examine both the output and the source code of the Linux shell script sample.sh. Which two statements describe the variables contained in the sample.sh script? (Choose two.)
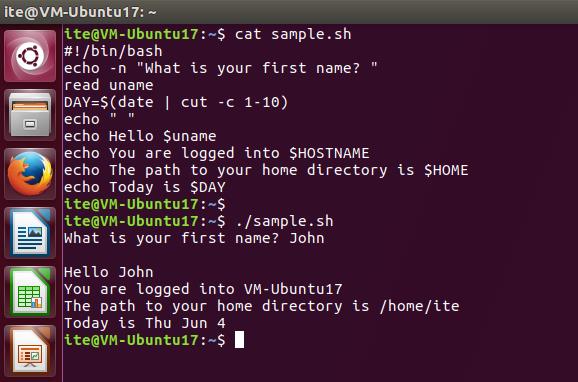
- The $HOSTNAME variable is defined within the script.
- The $uname variable is an input variable defined within the script.
- The $DAY variable is a standard environmental variable in Linux.
- The value of the $HOME variable is the same for all logged in users.
- The $HOSTNAME variable is an environmental variable initialized by the system.
- The $uname variable contains the username of the logged in user.
182. Why would a lawyer need to use the tracert command?
- to verify activity on the PC by displaying all active TCP connections on the device
- to query the Domain Name Sysytem (DNS) to get domain names and mapping information
- to quickly verify connectivity by sending echo-request messages to the destination and receiving a series of echo-reply messages from that destination
- to display a list of the near-side router interfaces between the source device and the destination device
183. A network analyst is booting a laptop that has Windows 7 installed with cellular SIM slot. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is thenext step that will happen in the boot process?
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
- The Windows kernel takes over the boot process.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
184. A company purchases 15 USB flash drives to use for data analysis training for company accountants. The data analysis training requires that actual company data be stored on the drives, so a secure method of erasing the data is needed before the flash drives can be reused for other training classes. What method should the IT technicians use to ensure that the data on the USB flash drives cannot be recovered?
- a quick formatting utility to overwrite the data
- a degaussing wand to erase the data
- a secure erase software utility to wipe the drive
- an electromagnetic device to wipe the drive
185. Refer to the exhibit. What can be determined about the contents of the ite_user home directory?
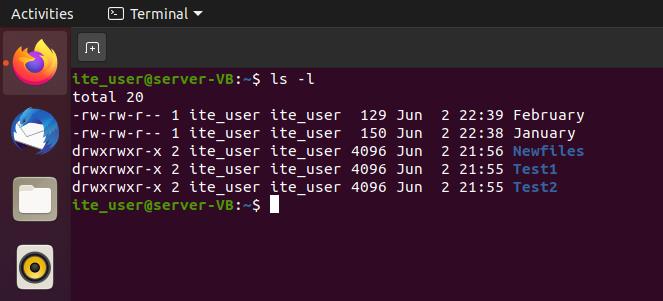
- The octal representation of the permissions for January is 755.
- All users have read, write, and execute permissions to files within the directories.
- There are two data files and three directories contained in this user directory.
- The data files in this user directory contain no data.
186. Refer to the exhibit. What is true of this mobile device screen?

- Tapping and holding the arrow at the bottom left will display the Home screen.
- Text messages, news, photos and other content can be displayed in the different tiles.
- Icons and buttons are used to represent the different apps on the phone.
- Unpinning an app from this view will uninstall the app from the phone.
- Tile sizes depend on the size of the app.
187. An on-site IT technician needs to work on systems installed in a small health clinic located in New York state. When the technician arrives, the office manager asks if the technician is aware of HIPAA regulations. Which two situations are breaches of PHI and could possibly lead to severe penalties under HIPAA? (Choose two.)
- sending the software support technician a text of the error messages that pop up when viewing patient records
- sending screenshots of multiple patient health records that contain error messages to a second level technician
- making a backup of the clinic patient data in order to recreate the issues on a server in the IT support office
- calling the software support help desk and describing an issue occurring when patient records are printed
- watching the office manager demonstrate an issue using a copy of the clinic database that contains test data
188. Why would a manager need to use the del command?
- to relocate a file from one Windows directory to another one
- to remove an empty directory
- to move that file to a different Windows directory while also leaving the file in the current location
- to erase one or more files from a Windows directory
189. A technician is working on a laptop and an app is not responding. What is a possible solution for this situation?
- Ensure that Bluetooth is not activated.
- Perform a reset.
- Ensure that Wi-Fi is turned off.
- Ensure that only one app is open at a time.
190. An end user wants to be able to recover an older version of a document that was created earlier in the day. Assuming that Windows Backup is enabled, which Windows 10 function can provide a user access to recover specific versions of a file?
- File History
- System Restore
- Windows Recovery
- Reset this PC
191. An IT technician attempts to copy a large file to a USB flash drive that contains other data but the copy fails. The technician checks the properties of the flash drive and finds that it was formatted using FAT32. Which method can the technician use to easily change the file system to NTFS without losing the data files currently stored on the disk?
- Open the Command Prompt (Admin) window and use the convert command.
- Back up the data on the flash drive, reformat the drive as NTFS, and restore the data.
- Use the Disk Management utility on Windows 10 to change the formatting.
- Create a new partition on the flash drive and format it as NTFS.
192. An employee wants to keep a local backup of iPhone data on a Windows laptop. What type of software does the employee need on the laptop to create this backup?
- Google sync
- Finder
- Time Machine
- iTunes
193. What can an IT technician accomplish using the Manage Storage Spaces feature in Windows 8 and 10?
- configure RAID controllers in the BIOS
- automatically configure disk backup utilities
- create storage pools and configure disk arrays
- update disk device drivers in the Windows registry
194. While troubleshooting an issue on a customer computer, an on-site technician believes that the problem can be resolved by using Windows Restore. What type of information is not restored when using Windows Restore with a recent restore point snapshot?
- device drivers
- operating system files
- registry entries
- user data files
- installed program settings
195. A technician is booting a PC that has Windows 10 installed on dynamic drives. The boot process is currently working on the following step: POST. What is the next step that will happen in the boot process?
- There are no more steps, the boot process is complete.
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
- WINLOGON.EXE displays the Windows Welcome screen
- BIOS locates and reads the configuration settings that are stored in the CMOS memory.
196. What are two features of multicore processors? (Choose two.)
- Applications such as gaming and video editing benefit from having multicore processors available.
- Each core in a multicore processor has its own independent connection to reserved RAM.
- Multiple single-core processors use less power and generate less heat than a multicore processor does.
- Multicore processors can execute instructions more quickly than single-core processors can.
- L2 and L3 cache is shared in all types of multicore processors in order to improve performance.
197. Which two statements describe characteristics of network addresses? (Choose two.)
- A MAC address is also referred to as a physical address because it is permanently embedded on the NIC.
- A statically assigned IP address will be valid on any network to which the device connects.
- DHCP is used to dynamically assign both MAC and IP addresses to devices connected to the network.
- A valid public IPv4 or IPv6 address is needed in order for devices to communicate over the internet.
- The MAC address of a device will change when that device moves from one Ethernet network to another.
198. An on-site technician is asked to check a laptop used by an executive who occasionally works from home. The technician observes that the image on the laptop screen flickers and appears dull, even though the same image displayed on another monitor attached to the laptop docking station is normal. What are two issues that could cause the symptoms the technician observed? (Choose two.)
- The inverter may be failing.
- The LCD cutoff switch is damaged.
- The laptop is overheating.
- The GPU has failed.
- The backlight needs adjustment or is failing.
199. A technician must replace a power supply. Which two features should the technician consider when selecting the replacement? (Choose two.)
- physical size
- output voltage less than 3V
- UPS support
- wattage
- support for eSATA
200. Why is unbuffered memory a better choice than buffered memory for gaming or general use computers?
- The additional control circuitry on the unbuffered RAM module speeds up memory reads.
- Buffered memory cannot support the larger quantities of RAM that are necessary for gaming computers.
- The computer can read data directly from the unbuffered memory banks, making unbuffered memory faster than buffered memory.
- The control chip built into the unbuffered RAM module assists the memory controller to manage large amounts of RAM.
201. A UTM appliance, such as a Cisco ASA 5506-X, includes the functionality of which two standalone devices? (Choose two.)
- DSL modem
- external Storage drive
- stateful firewall
- IPS/IDS
- 24-port LAN switch
202. An on-site IT technician is attempting to resolve an issue with application performance on a customer laptop. The technician backs up the customer data and then replaces the memory in the laptop with known good memory. It does not resolve the performance issue. What are the next two actions the technician should take? (Choose two.)
- Call the laptop manufacturer technical support line.
- Continue to test the next likely probable cause.
- Document that the possible solution did not work.
- Reinstall the original memory sticks.
- Escalate the issue to the next level support technician.
203. A user wants VirtualBox to run automatically when Windows 10 starts up. Which action will enable VirtualBox to load and run on system startup?
- Copy the shortcut for VirtualBox from its location to the startup folder.
- Right click on the application in the Start menu and choose the startup option.
- Use msconfig to change the startup option from manual to automatic.
- Use the Startup tab in Task Manager to add VirtualBox to the list of programs.
204. An on-site IT technician finished the removal of malware from a customer computer and installed new virus protection software. An hour after the technician left the site, the customer called the help desk to report that a critical web-based application was no longer functioning properly. Which step in the troubleshooting process did the IT technician fail to properly complete?
- Document findings and actions.
- Identify the problem.
- Establish a plan of action.
- Test the theory of probable cause.
- Verify full system functionality.
205. What are two characteristics of the hotend nozzle on a 3D printer? (Choose two.)
- The hotend nozzle heats to different temperatures depending on the type of filament used.
- Hotend nozzles are designed to last the life of the printer and do not need to be replaced.
- The heating temperature of the hotend nozzle is the same (190 degrees Celsius) for all materials.
- Hotend nozzles are considered consumables and should be replaced during normal maintenance.
- Replacing a hotend nozzle can be a complicated and time-consuming process.
206. Refer to the exhibit. What can be determined from the output of this command?
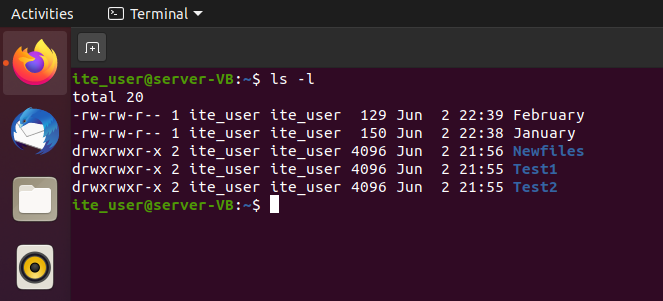
What can be determined from the output of this command
- The owner, group, and others have read permissions to January.
- All users have read, write, and execute permissions to files within the directories.
- The data files in this directory contain no data.
- There are three data files and two directories contained in this directory.
207. Which type of disk drive can provide a very fast boot experience and also provide high capacity storage?
- SSD
- DVD
- HDD
- SSHD
208. Refer to the exhibit. Which type of adapter card may require the width of two slots in order to accommodate additional cooling, even though it only has one PCIe x16 connector?

- USB-C controller
- video capture card
- graphics card
- wireless network adapter
209. A technician follows the instruction manual that came with a new Bluetooth speaker to place the speaker in discoverable mode. In this mode, what type of information will the speaker transmit to the laptop in order to start the pairing process?
- device name and Bluetooth capabilities
- Bluetooth PIN and device ID
- protocol and radio frequency settings
- username and telephone number
210. A technician is booting a PC that has Windows 10 installed on dynamic drives. The boot process is currently working on the following step: BIOS locates and reads the configuration settings that are stored in the CMOS memory. What is the next step that will happen in the boot process?
- The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager.
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- POST.
- BIOS locates and reads the configuration settings that are stored in the CMOS memory.
211. A network analyst is booting a laptop that has Windows 7 installed with cellular SIM slot. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is the next step that will happen in the boot process?
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- The Windows kernel takes over the boot process.
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
212. Why would a bank manager need to use the bootrec command?
- to help to repair the MBR that is suspected of having issues
- to manage a PCs drives, disks, partitions, volumes, and virtual drives
- to prepare a hard drive to accept Windows files
- to display the IPv6 address of the PC
213. A gamer is booting a tablet that has Windows 7 installed with 4 GB RAM. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is the next step that will happen in the boot process?
- WINLOGON.EXE displays the Windows Welcome screen
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- There are no more steps, the boot process is complete.
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
214. Why would a user need to use the gpresult command?
- to create a new Windows directory
- to make the PC synchronize with new group policy settings
- to verify the settings that are suspected to be incorrect
- to change from the current working folder to another folder
215. An accountant is booting a desktop that has Windows 8 installed. The boot process is currently working on the following step: WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL. What is the next step that will happen in the boot process?
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- Winload uses the path specified in BOOTMGR to find the boot partition.
- The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
216. A user is booting a desktop that has Windows 10 installed that also uses an extended partition. The boot process is currently working on the following step: The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager. What is the next step that will happen in the boot process?
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager.
- Winload uses the path specified in BOOTMGR to find the boot partition.
217. A technician is working on a laptop and an app is not loading. What is a possible solution for this situation?
- Perform a reset.
- Ensure that only one app is open at a time.
- Check the display settings.
- Check the screen refresh rate.
218. Which term describes a file system that supports a partition size up to 2 TB?
- FAT32
- formatting
- dynamic disk
- basic disk
219. Why would a technician need to use the copy command?
- to copy files, directories, and subdirectories from one location to another
- to move that file to a different Windows directory while also leaving the file in the current location
- to copy a group of files from one Windows directory to another
- to relocate a file from one Windows directory to another one
220. Match the Windows 10 boot sequence after the boot manager (bootmgr.exe) loads.
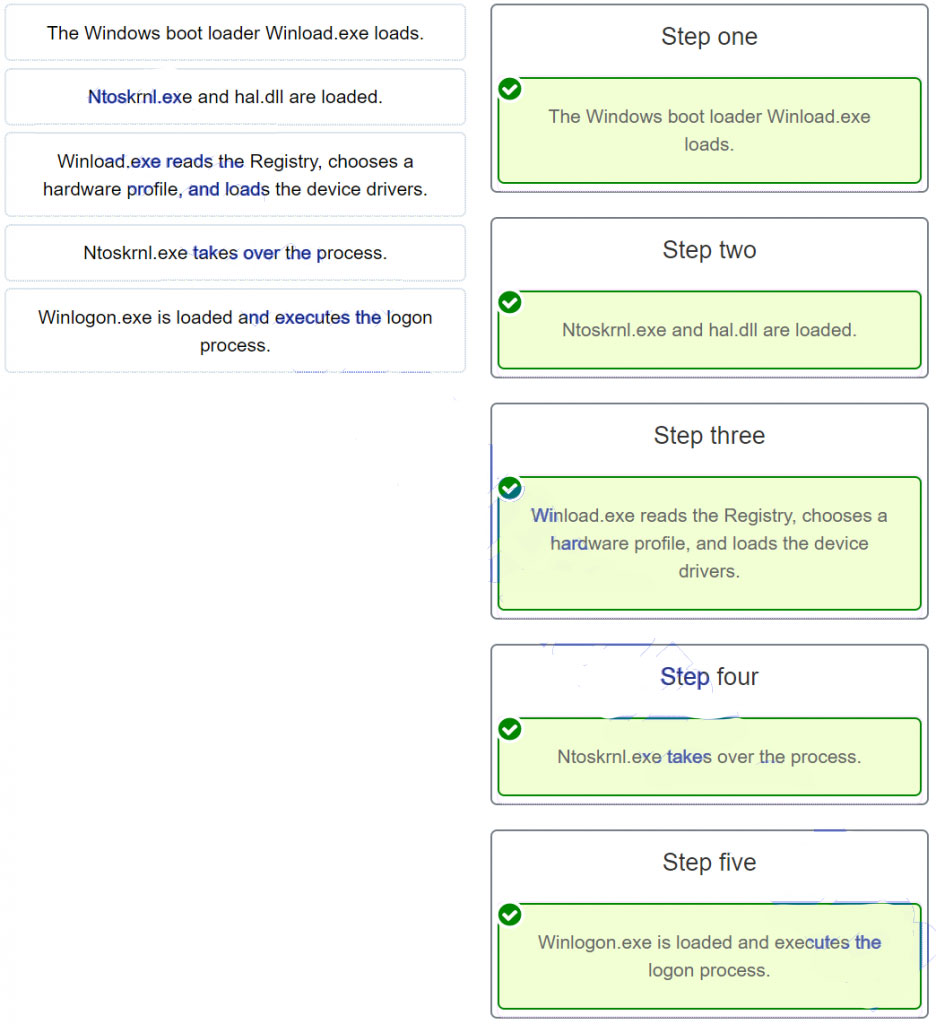
221. Match the correct API with its function within the Windows 10 environment.
222. Which two tools are available to transfer user data and settings from an old Windows computer to a Windows operating system on a new computer? (Choose two.)
- Windows Easy Transfer
- Windows User Manager
- Windows Upgrade Assistant
- Windows Upgrade Advisor
- User State Migration tool
223. A user wants to extend a primary partition formatted with the NTFS file system with the unallocated space on the hard disk. What must the user do after the primary partition is extended to make it usable?
- Convert the disk type to dynamic.
- Ensure that the disk type is basic.
- Format the disk with the FAT64 file system.
- Partition the new space as a basic disk.
224. Why is a full format more beneficial than a quick format when preparing for a clean OS installation?
- A full format is the only method of installing Windows 8.1 on a PC that has an operating system currently installed.
- A full format will delete files from the disk while analyzing the disk drive for errors.
- A full format will delete every partition on the hard drive.
- A full format uses the faster FAT32 file system, whereas a quick format uses the slower NTFS file system.
225. A technician wishes to prepare the computers in the network for disaster recovery. The network consists of a variety of desktops and laptops from different vendors. All the computers are running either a 32-bit version of Windows 10 Pro or a 64-bit version of Windows 10 Pro. How would the technician prepare the recovery media?
- Prepare one 64-bit recovery disc for all the computers.
- Prepare one 32-bit recovery disc for all the computers.
- Prepare individual recovery discs for all the computers.
- Prepare one image restore for all the computers.
226. A technician wishes to deploy Windows 10 Pro to multiple PCs through the remote network installation process. The technician begins by connecting the new PCs to the network and booting them up. However, the deployment fails because the target PCs are unable to communicate with the deployment server. What is the possible cause?
- The wrong network drivers are loaded in the image file.
- The SID has not been changed in the image file.
- The NIC cards on the new PCs are not PXE-enabled.
- Sysprep was not used before building the image file.
227. Which condition is required when planning to install Windows on a GPT disk?
- The computer must be UEFI-based.
- Only one primary partition can contain an OS.
- The maximum partition size cannot exceed 2 TB.
- The maximum number of primary partitions that can co-exist is 4.
228. A technician wishes to perform a customized unattended network installation of Windows 10 on a PC. The requirements include the installation of specific applications and device drivers through the use of an answer file. What would the technician use to create the answer file?
- Recovery partition
- Windows SIM
- disk cloning
- System Restore
229. An organization has purchased a custom application for the sales staff that can only be installed on a 64-bit Windows operating system. Each member of the sales staff has a Windows 8.1 32-bit PC. What must the IT department do in order to install and run the application on the sales staff computers?
- Downgrade the 32-bit Windows 8.1 to 64-bit Windows 7.
- Upgrade the 32-bit Windows 8.1 to 64-bit Windows 10.
- Perform a clean installation of 64-bit Windows 10.
- Download and install 64-bit hardware drivers in the current OS.
230. Match the tabs of the Windows 10 Task Manager to their functions. (Not all options are used.)
231. Match the drive status indicators in the Disk Management utility with their description. (Not all options are used.)
232. Match the wireless security settings to the description. (Not all options are used.)
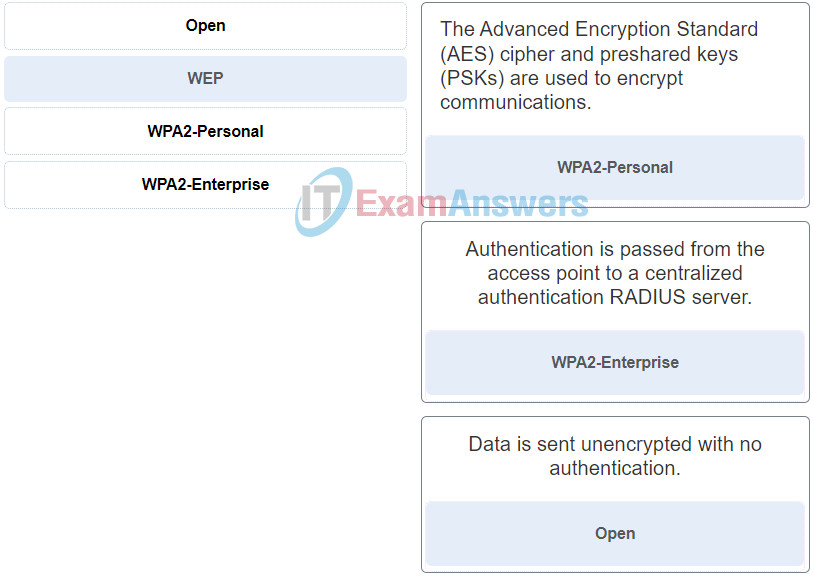
233. What are two possible solutions to any Windows computer restarting continuously and never displaying the desktop? (Choose two.)
- Upgrade the processor.
- Press F8 to open the Advanced Options menu and choose Disable Automatic Restart on System Failure.
- Access the BIOS and change the boot order options.
- Run chkdsk /F /R from the recovery console.
- Upgrade the video card.
- Reset the hard drive jumpers.
234. A technician uses Microsoft Deployment Image Servicing and Management (DISM) tool to create a Windows image file on one of the workstations running Windows 10. When the technician tries to clone another workstation with the image file, the workstation exhibits network connectivity issues on completion. What could cause this?
- The SID of the original PC is not cleared when creating the image with DISM.
- The technician used the wrong tool to create the image file.
- The network drivers were not added to the image file.
- The Sysprep utility should have been turned off prior to the creation of the image file.
235. A user complains that user files cannot be synced with the network file server while the user is traveling out of the office. The user had access to the internet but no access to the company network server. How can this be addressed?
- Ensure that the user only uses a single device and not multiple devices when accessing networked files.
- Turn off the activation of Offline Files feature in the Sync Center.
- Setup a Sync partnership with the networked file location.
- Setup a Sync partnership between the network server, Microsoft OneDrive, and the user.
236. A technician has connected a new internal hard drive to a Windows 10 PC. What must be done in order for Windows 10 to use the new hard drive?
- Initialize the new hard drive.
- Extend the partition on an existing hard drive to the new hard drive.
- Run chkdsk on the new hard drive.
- Mount the new hard drive.
237. What service does PRINT$ provide?
- It provides a network share for accessing shared printers.
- It provides printer drivers for printer administrators.
- It provides a group of hidden printers that only administrative users have permissions to send print jobs to.
- It provides an administrative Printer share accessible by all local user accounts.
238. A technician is troubleshooting a Windows 10 laptop infected with a virus that has damaged the master boot record. The technician has booted the laptop using the installation media and is attempting to repair the laptop from the command line interface. Which command can the technician use to repair the corrupt master boot record?
- bootrec /fixmbr
- chkdsk
- msconfig
- sfc /scannow
239. A user reports that a Windows 10 PC displays the error message “Invalid Boot Disk” during the boot process. The IT technician attempts to boot the computer and finds that the error message occurs immediately after the POST. What could be the possible cause?
- A recently installed device driver is incompatible with the boot controller.
- BOOTMGR is corrupted.
- The MBR/GPT is corrupted.
- A service failed to start during the booting process.
240. Which port number is used by Virtual Network Computing (VNC) to provide remote screen sharing between devices?
- 22
- 23
- 389
- 3389
- 5900
241. Which feature is included with macOS and provides the ability for a remote user to view and change files, folders, and applications on the local computer?
- Screen Sharing
- Remote Assistance
- Virtual Network Computing
- Remote Desktop
242. Which area of concern falls under the operations and planning category in IT documentation?
- inventory management
- disaster recovery policies and procedures
- logical and physical network topology diagrams
- end-user manual for hardware and software
243. Match the individual languages with their corresponding classification.
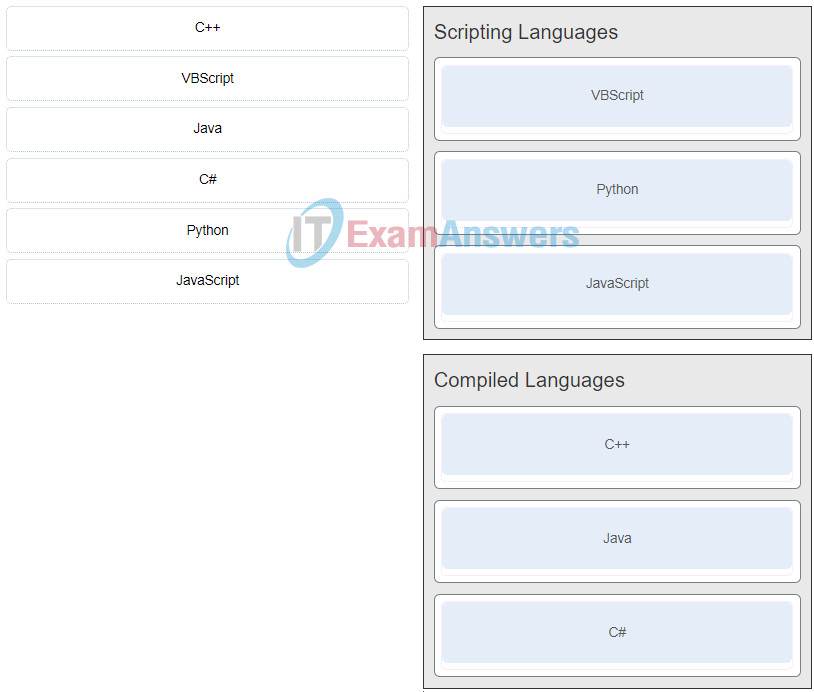
244. Which two actions should a technician take if illegal content, such as child pornography, is discovered on the hard drive of a customer computer? (Choose two.)
- Confront the customer immediately.
- Remove and destroy the hard drive.
- Contact a first responder.
- Shut down the computer until authorities arrive.
- Document as much information as possible.
245. What are three pieces of information a level one technician should gather from a customer? (Choose three.)
- contact information
- description of the problem
- details of any recent changes to the computer
- output from diagnostic software
- output from a remote connection to the customer computer
- current CMOS settings
246. What two actions are appropriate for a support desk technician to take when assisting customers? (Choose two.)
- Interrupt customers if they start to solve their own problems.
- Comfort a customer by minimizing the customer problem.
- Let a customer finish talking before asking additional questions.
- If you have to put the customer on hold, ask the customer for permission.
- As soon as you detect customer anger, pass the angry customer to the next level.
247. A support desk technician is dealing with an angry customer. Which two approaches should the technician take in dealing with the customer? (Choose two.)
- Ask socially related questions to direct the customer away from the problem.
- Work to redirect the conversation to solving the problem.
- Immediately transfer the customer to a higher level technician.
- Reply to the customer with the same level of anger.
- Let the customer explain the problem without interrupting.
248. What two kinds of problems should be escalated from a level one technician to a level two technician? (Choose two.)
- problems that require rebooting the equipment
- problems that can be solved in a short time
- problems that are complicated and will take a long time to resolve
- problems that do not fit into the “down call” category
- problems that are beyond the scope of the knowledge of the level one technician
249. An IT technician in a service company has provided extensive remote IT support with product deployment for a customer. After the completion of the contract, a complaint is filed against the IT technician for not following company policy by sending unsolicited emails about services and products that are not related to the contract. What two things should the IT support technician have done differently? (Choose two.)
- The IT technician should have researched the company policy about personal communication with customers on company time.
- The IT technician should have used encryption to hide the purpose of the emails.
- The IT technician should have added the customer to a chain letter with many recipients instead.
- The IT technician should have asked the customer if the customer was interested in receiving information regarding other new services and products.
- The IT technician should have requested permission from a supervisor to send the customer emails.
250. A third-party security firm is performing a security audit of a company and recommends the company utilize the Remote Desktop Protocol. What are two characteristics of the Microsoft Remote Desktop Protocol (RDP)? (Choose two.)
- RDP connects on TCP port 22.
- RDP requires a Windows client.
- RDP uses an encrypted session.
- RDP is a command-line network virtual terminal protocol.
- RDP connects on TCP port 3389.
251. Which subject area describes collecting and analyzing data from computer systems, networks, and storage devices, as part of an investigation of alleged illegal activity?
- cyber law
- computer forensics
- cryptography
- disaster recovery
252. In a computer forensics investigation, which type of data is considered volatile data and can be lost if power is removed from the computer?
- data stored on magnetic disks
- data stored on an internal drive
- data in transit between RAM and the CPU
- data stored on an external drive
253. Refer to the exhibit. During the troubleshooting of software that is installed on a computer system, a level one technician requires help from a level two technician. The file shown in the exhibit must be sent to the level two technician. How should the level one technician deliver this file?
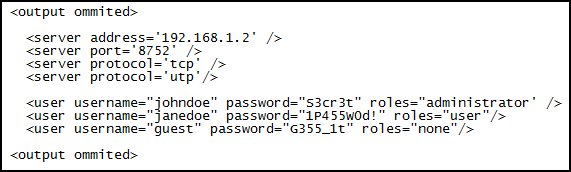
- This file should not be shared with the level two technician.
- Replace all passwords in the file with <password omitted> before emailing the file and then supply the passwords by secure means, if required.
- Send the file as it is to the level two technician.
- Deliver the file in printed format only.
254. What skill is essential for a level one technician to have?
- the ability to gather relevant information from the customer and pass it to the level two technician so it can be entered into the work order
- the ability to ask the customer relevant questions, and as soon as this information is included in the work order, escalate it to the level two technician
- the ability to translate a description of a customer problem into a few succinct sentences and enter it into the work order
- ability to take the work order prepared by the level two technician and try to resolve the problem
255. What is used to control illegal use of software and content?
- chain of custody
- service level agreement
- End User License Agreement
- digital rights management
256. What determines the level of support that a call center technician will provide to an individual customer?
- Support is based on the SLA for that customer.
- All customers receive the same level of support by the call center.
- A level one technician will provide a higher level of support than a level two technician.
- An individual call center technician chooses the level of support based on the time available to assist the customer.
257. A bench technician enters the server room and finds the backup server computer case open. The hard drives containing patient medical data are all physically disconnected from the motherboard and the SATA data cables are hanging outside the case. Which step should the technician immediately take?
- Reconnect the SATA data cables to ensure continued data backup.
- Disconnect the SATA power cables to prevent the loss of persistent data.
- Place the hard drives in an external enclosure and begin backing up the data before releasing the drives to first responders.
- Locate an employee qualified to collect evidence.
- Dust the server computer case for fingerprints.
258. What is the difference between a scripting language and a compiled language?
- Scripting languages need to be converted into executable code using a compiler, while compiled languages are interpreted as they are executed.
- Compiled languages are executed by the operating system, while scripting languages are executed by the CPU.
- Scripting languages are interpreted and executed line by line when a script is run, while compiled languages need to be converted into executable code.
- Compiled languages are executed by a command interpreter, while scripting languages are executed by the CPU.
259. Which methods can be used to implement multifactor authentication?
- VPNs and VLANs
- IDS and IPS
- passwords and fingerprints
- tokens and hashes
260. When responding to a call from a customer who is experiencing problems with a computer, the technician notices that a number of system files on the computer have been renamed. Which two possible solutions could the technician implement to resolve the problem? (Choose two.)
- Use antivirus software to remove a virus.
- Restore the computer from a backup.
- Change the folder and file permissions of the user.
- Reset the password of the user.
- Upgrade the file encryption protocol.
261. A technician suspects that a security issue is causing problems with a computer. What two actions could be performed to test theories of probable cause when troubleshooting the PC? (Choose two.)
- Log in as a different user.
- Disconnect the computer from the network.
- Search helpdesk repair logs for more information.
- Discuss solutions with the customer.
- Ask the customer open-ended questions about the problem.
262. The CIO wants to secure data on company laptops by implementing file encryption. The technician determines the best method is to encrypt each hard drive using Windows BitLocker. Which two things are needed to implement this solution? (Choose two.)
- at least two volumes
- USB stick
- password management
- TPM
- EFS
- backup
263. What is an accurate description of asymmetric encryption technology?
- Asymmetric encryption is an encryption process that compares traffic on both ends to make sure the traffic has not been altered.
- It is an encryption process that uses identical keys on both ends to establish the VPN.
- It is an encryption protocol that is used to encrypt data as the data is sent over the VPN.
- It is an encryption process that uses a public and private key pair to encrypt/decrypt data.
264. Which type of security threat can be transferred through email and is used to gain sensitive information by recording the keystrokes of the email recipient?
- adware
- Trojan
- worm
- virus
- grayware
265. A manager reports that unusual things are happening on a Windows computer. The technician determines that malware is the culprit. What can the technician do to remove stubborn malware?
- Ensure that the computer is connected to the wired network so that antimalware updates can be installed.
- Enter Safe Mode and do a system restore.
- Install adware protection.
- Train the user on identifying trusted and untrusted sources.
266. An employee that has worked at the company for many years has started a home-based business selling crafts. While leaving an office meeting, a company supervisor notices the employee buying supplies for the personal crafting business of the employee. What section of the security policy should the supervisor review when determining how to handle this situation?
- acceptable use policies
- identification and authentication policies
- incident handling policies
- remote access policies
267. What Windows utility should be used to configure password rules and account lockout policies on a system that is not part of a domain?
- Event Viewer security log
- Local Security Policy tool
- Active Directory Security tool
- Computer Management
268. A customer brings in a computer that is asking for a password as soon as it powers on, even before the operating system boots. Which type of password is enabled?
- BIOS
- login
- multifactor
- network
- synchronous
269. When attempting to improve system performance for Linux computers with a limited amount of memory, why is increasing the size of the swap file system not considered the best solution?
- A swap file system only supports the ex2 file system.
- A swap file system does not have a specific file system.
- A swap file system cannot be mounted on an MBR partition.
- A swap file system uses hard disk space to store inactive RAM content.
270. What are three features of GPS on mobile devices? (Choose three.)
- phone number lookup
- navigation
- specialized search results
- device tracking
- remote wipe
- gas mileage calculations
271. Which three components are used to assign file and directory permissions in Linux systems? (Choose three.)
- root
- group
- owner
- all users
- super group
- admin group
272. A user downloads a widget onto his Android phone but is puzzled to see that when the widget is touched an app is launched. What is a possible cause?
- The user has downloaded a virus.
- The widget is corrupt.
- The security settings of the Android OS have been compromised.
- The widget is associated with the app and this is the normal behavior.
273. What is the purpose of running mobile device apps in a sandbox?
- to enable the phone to run multiple operating systems
- to prevent malicious programs from infecting the device
- to enable separate app icons to be displayed on the home screen
- to bypass phone carrier restrictions that prevent access to unauthorized apps
274. Which built-in tool is available on a Mac OS X machine to perform disk backups?
- Disk Utility
- Deja Dup
- Finder
- Time Machine
275. A user calls the help desk reporting that a laptop with Linux freezes on startup and displays kernel panic. What could cause this problem?
- A driver has become corrupted.
- GRUB or LILO has been deleted.
- GRUB or LILO has been corrupted.
- An application is using a resource that has become unavailable.
276. A user calls the help desk to report that a mobile device exhibits very slow performance. What could cause this problem?
- The touchscreen is not calibrated.
- An app is not compatible with the device.
- The operating system is corrupt.
- A power-intensive app is running in the background.
277. Which term describes a partition that is used to store and boot an operating system by default?
- logical drive
- active partition
- basic disk
- extended partition
278. Which term describes a file system that supports a partition size up to 16 exabytes?
- extended partition
- NTFS
- logical drive
- active partition
279. Which term describes a file system for USB flash drives that supports files larger than 4 GB?
- extended partition
- exFAT
- logical drive
- active partition
280. Which term describes a partition that supports up to 23 logical drives?
- logical drive
- extended partition
- basic disk
- active partition
281. Which term describes a file system for optical disk media?
- extended partition
- CDFS
- logical drive
- active partition
282. Which term describes a type of partition that would only exist on a hard disk that has an MBR?
- extended partition
- logical drive
- basic disk
- active partition
283. Which term describes a type of storage device that supports a partition to be extended into adjacent unallocated space as long as it is contiguous?
- NTFS
- basic disk
- FAT32
- formatting
284. Which term describes a general name for physical areas on a hard drive?
- NTFS
- partition
- FAT32
- formatting
285. Which term describes a partition scheme that takes a portion of disk space of 512 bytes long and that contains the boot loader?
- NTFS
- MBR
- FAT32
- formatting
286. Which term describes a type of storage device that supports a volume that can span across more than one disk?
- NTFS
- dynamic disk
- FAT32
- formatting
287. A technician is booting a laptop that has Windows 10 installed with 2 GB RAM. The boot process is currently working on the following step: NTOSKRNL.EXE starts the login file called WINLOGON.EXE. What is the next step that will happen in the boot process?
- WINLOGON.EXE displays the Windows Welcome screen.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- Winload uses the path specified in BOOTMGR to find the boot partition.
288. A user is booting a tablet that has Windows 10 installed. The boot process is currently working on the following step: WINLOGON.EXE displays the Windows Welcome screen What is the next step that will happen in the boot process?
- There are no more steps, the boot process is complete.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- Winload uses the path specified in BOOTMGR to find the boot partition.
289. A manager is booting a tablet that has Windows 8 installed. The boot process is currently working on the following step: POST. What is the next step that will happen in the boot process?
- BIOS locates and reads the configuration settings that are stored in the CMOS memory.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- The Windows kernel takes over the boot process.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
290. An accountant is booting a PC that has Windows 8 installed. The boot process is currently working on the following step: BIOS locates and reads the configuration settings that are stored in the CMOS memory. What is the next step that will happen in the boot process?
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- The Windows kernel takes over the boot process.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
291. A network analyst is booting a PC that has Windows 7 installed with 2 GB RAM. The boot process is currently working on the following step: The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager. What is the next step that will happen in the boot process?
- Winload uses the path specified in BOOTMGR to find the boot partition.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- The Windows kernel takes over the boot process.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
292. An analyst is booting a desktop that has Windows 7 installed with 4 GB RAM. The boot process is currently working on the following step: Winload uses the path specified in BOOTMGR to find the boot partition. What is the next step that will happen in the boot process?
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
- There are no more steps, the boot process is complete.
- WINLOGON.EXE displays the Windows Welcome screen
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
293. A gamer is booting a desktop that has Windows 7 installed on dynamic drives. The boot process is currently working on the following step: WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers. What is the next step that will happen in the boot process?
- The Windows kernel takes over the boot process.
- There are no more steps, the boot process is complete.
- WINLOGON.EXE displays the Windows Welcome screen
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
294. A technician is booting a laptop that has Windows 10 installed with 2 GB RAM. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is the next step that will happen in the boot process?
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
- There are no more steps, the boot process is complete.
- WINLOGON.EXE displays the Windows Welcome screen
- The Windows kernel takes over the boot process.
295. A user is booting a laptop that has Windows 10 installed. The boot process is currently working on the following step: WINLOGON.EXE displays the Windows Welcome screen What is the next step that will happen in the boot process?
- WINLOGON.EXE displays the Windows Welcome screen
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
- There are no more steps, the boot process is complete.
- The Windows kernel takes over the boot process.
296. A manager is booting a tablet that has Windows 8 installed. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is the next step that will happen in the boot process?
- The Windows kernel takes over the boot process.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- WINLOGON.EXE displays the Windows Welcome screen
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
297. Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker was using a specific technique that affected the TCP three-way handshake. What is the type of network attack?
- DDoS
- SYN flood
- DNS poisoning
- zero-day
298. Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a technique that compares hashed passwords to potential hashes the hacker has. What is the type of network attack?
- rainbow table
- DDoS
- DNS poisoning
- SYN flood
299. Users in a company have complained about network performance. After investigation, the IT staff has determined that the DNS server was sent with an enormous amount of false requests, thus overwhelming the server. What is the type of network attack?
- DNS poisoning
- SYN flood
- DoS
- zero-day
300. Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a vulnerability that is known to the software vendor, but not patched yet. What is the type of network attack?
- zero-day
- DDoS
- DNS poisoning
- SYN flood
301. Users in a company have complained about network performance. After investigation, the IT staff has determined that zombies were used to attack the firewall. What is the type of network attack?
- DDoS
- DNS poisoning
- SYN flood
- zero-day
302. Users in a company have complained about network performance. After investigation, the IT staff has determined that zombies were used to attack the firewall. What is the type of network attack?
- zero-day
- dictionary
- SYN flood
- DDoS
303. Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker is using a table of words that potentially could be used as passwords. What is the type of network attack?
- dictionary
- SYN flood
- zero-day
- DNS poisoning
304. Users in a company have complained about network performance. After investigation, the IT staff has determined that the attacker injected false records on the server that translates IP addresses to domain names. What is the type of network attack?
- zero-day
- DNS poisoning
- dictionary
- SYN flood
305. What is required as an additional verification mechanism on iOS mobile devices when setting up biometric screen locks, such as Touch ID or Face ID?
- a passcode
- a swipe code
- a linked email account
- a pattern lock
306. Which situation can be prevented by creating a UEFI password?
- malware installing a keystroke logger to collect user login credentials
- an unauthorized person acting as the logged in user on an unlocked computer
- a hacker using a password obtained through phishing to access network data
- an unauthorized person changing the boot order on the computer to boot to another OS
307. A PC technician has been asked by a supervisor to recommend a security solution for a company that wants a device to monitor incoming and outgoing traffic and stop any malicious activity. Which security technique should the technician recommend?
- Buy an IPS.
- Implement a RAID.
- Provide security awareness training.
- Use SSL.
308. A PC technician has been asked by a supervisor to recommend a security solution for a machine where the antimalware software cannot remove all of the malware. Which security technique should the technician recommend?
- Implement a RAID.
- Provide security awareness training.
- Use Windows Safe Mode.
- Use encryption.
309. A PC technician has been asked by a supervisor to recommend a security solution for preventing tailgating. Which security technique should the technician recommend?
- Use a mantrap.
- Implement a RAID.
- Provide security awareness training.
- Use encryption.
310. A PC technician has been asked by a supervisor to recommend a security solution for drive redundancy. Which security technique should the technician recommend?
- Buy an ASA.
- Use a VPN.
- Implement dual authentication.
- Implement a RAID.
311. A PC technician has been asked by a supervisor to recommend a security solution for phishing. Which security technique should the technician recommend?
- Provide security awareness training.
- Buy an ASA.
- Use a VPN.
- Employ ping sweeps.
312. A PC technician has been asked by a supervisor to recommend a security solution for protecting a computer used to log in at a dental clinic from someone using a bootable disk containing hacking tools. Which security technique should the technician recommend?
- Buy an ASA.
- Use a VPN.
- Run vulnerability scanners.
- Disable ports.
313. A PC technician has been asked by a supervisor to recommend a security solution for a manager traveling who needs access to internal corporate resources. Which security technique should the technician recommend?
- Buy an ASA.
- Use a VPN.
- Disable ports.
- Run vulnerability scanners.
314. Why would a gamer need to use the move command?
- to relocate a file from one Windows directory to another one
- to prepare a hard drive to accept Windows files
- to manage a PCs drives, disks, partitions, volumes, and virtual drives
- to copy files, directories, and subdirectories from one location to another
315. Why would a gamer need to use the copy command?
- to move that file to a different Windows directory while also leaving the file in the current location
- to prepare a hard drive to accept Windows files
- to manage a PCs drives, disks, partitions, volumes, and virtual drives
- to copy files, directories, and subdirectories from one location to another
316. Why would a university student need to use the robocopy command?
- to copy a group of files from one Windows directory to another
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to shutdown several remote computers one at a time
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
317. Why would a university student need to use the xcopy command?
- to copy files, directories, and subdirectories from one location to another
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to shutdown several remote computers one at a time
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
318. Why would a technical support representative need to use the format command?
- to prepare a hard drive to accept Windows files
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to shutdown several remote computers one at a time
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
319. Why would a technical support representative need to use the bootrec command?
- to help to repair the MBR that is suspected of having issues
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to shutdown several remote computers one at a time
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
320. Why would a technical support representative need to use the ipconfig command?
- to display the IPv6 address of the PC
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to shutdown several remote computers one at a time
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
321. Why would a user need to use the netstat command?
- to verify activity on the PC by displaying all active TCP connections on the device
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to shutdown several remote computers one at a time
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
322. Why would a user need to use the nslookup command?
- to query the Domain Name Sysytem (DNS) to get domain names and mapping information
- to scan and verify the integrity of all protected system files and replace incorrect versions with correct versions
- to shutdown several remote computers one at a time
- to repair, prepare, and fix Windows images and the recovery image within an installation of the operating system
323. Why would a manager need to use the ping command?
- to quickly verify connectivity by sending echo-request messages to the destination and receiving a series of echo-reply messages from that destination
- to change from the current working folder to another folder
- to create a new Windows directory
- to remove an empty directory
324. What are two probable causes of a user unable to access local resources such as file shares or printers on a wired network? (Choose two.)
- bad cabling
- DNS name resolution not working
- ISP down
- incorrect gateway address
- poor Wi-Fi signal
325. The IT department has just purchased 15 wireless access points in order to provide full wireless coverage for all 100 employees within the company and is looking to deploy the most secure and scalable wireless implementation. Which open source authentication method would perform authentication on behalf of all 15 wireless network devices?
- TACACS+
- TKIP
- RADIUS
- WPA2-PSK
326. A technician is upgrading many PCs used within the company. How should the technician dispose of an old inkjet printer cartridge?
- Recycle following local regulations.
- Give it to your neighbor.
- Take it home.
- Seal in a plastic bag before putting in the garbage.
327. A technician is about to begin preventive maintenance on a company PC. In which situation would ESD be an issue?
- when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
- when installing a UPS
- while attaching speakers to a surround sound card
- when installing a processor
328. A client packet is received by a server. The packet has a destination port number of 67. What service application is the client requesting?
- DHCP
- SSH
- Telnet
- SMTP
329. A client packet is received by a server. The packet has a destination port number of 443. What service application is the client requesting?
- HTTPS
- SSH
- Telnet
- SMTP
330. A client packet is received by a server. The packet has a destination port number of 69. What service application is the client requesting?
- TFTP
- SSH
- Telnet
- SMTP
331. A client packet is received by a server. The packet has a destination port number of 445. What service application is the client requesting?
- SMB/CIFS
- SSH
- Telnet
- SMTP
332. A client packet is received by a server. The packet has a destination port number of 548. What service application is the client requesting?
- AFP
- HTTP
- TFTP
- POP3
333. A client packet is received by a server. The packet has a destination port number of 80. What service application is the client requesting?
- HTTP
- POP3
- TFTP
- NetBIOS (NetBT)
334. A client packet is received by a server. The packet has a destination port number of 3389. What service application is the client requesting?
- RDP
- HTTP
- TFTP
- POP3
335. Why would a user need to use the gpupdate command?
- to change from the current working folder to another folder
- to verify the settings that are suspected to be incorrect
- to make the PC synchronize with new group policy settings
- to create a new Windows directory
336. Which protocol is used by Windows for file and printer sharing?
- SMB
- SMTP
- HTTPS
- IMAP
337. Which laptop LCD technology uses tilting crystals to provide a much higher contrast ratio than other types?
- Vertical alignment (VA)
- In-Plane switching (IPS)
- Twisted Nematic (TN)
- Organic light-emitting diode (OLED)
338. Which two statements are true regarding GPT partitions? (Choose two.)
- They are commonly used in computers with UEFI firmware.
- They are commonly used in computers with BIOS based firmware.
- They store a backup of the partition table.
- They have a maximum partition size of 2TB.
- They store the partition and boot data in one place.
339. A technician wishes to use the reset option to repair a Windows 10 installation and chooses the option that will retain the user’s personal files. Which statement is true based on using this option?
- All user files and applications will be restored together with the complete reinstallation of Windows 10.
- Only user files will be restored together with the complete reinstallation of Windows 10.
- All user files and applications will be deleted, and a complete reinstallation of Windows 10 will occur.
- Only corrupt files of the Windows 10 installation will be replaced and repaired.
340. A user is trying to execute a file using elevated permission. The user right-clicks the file, chooses Run as Administrator, and chooses Yes in the User Account Control (UAC) window. The operation fails. What is the reason?
- The UAC does not have the elevated privileges option.
- The user is not a member of the administrator group.
- The directory housing the file is read-only.
- The login password of the user is invalid.
341. What is a possible situation when it might be necessary to boot Windows 10 from a bootable recovery USB device?
- to disable background services
- to delete registry keys
- to partition the hard drive
- to repair the operating system
342. An accountant is booting a PC that has Windows 10 installed. The boot process is currently working on the following step: BIOS locates and reads the configuration settings that are stored in the CMOS memory. What is the next step that will happen in the boot process?
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- The Windows kernel takes over the boot process.
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
343. A manager is booting a tablet that has Windows 10 installed. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is the next step that will happen in the boot process?
- NTOSKRNL.EXE starts the login file called WINLOGON.EXE.
- The Windows kernel takes over the boot process.
- WinLoad reads the registry files, chooses a hardware profile, and loads the device drivers.
- WINLOGON.EXE displays the Windows Welcome screen
344. An analyst is booting a desktop that has Windows 10 installed with 4 GB RAM. The boot process is currently working on the following step: Winload uses the path specified in BOOTMGR to find the boot partition. What is the next step that will happen in the boot process?
- WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL.
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager.
- The Windows kernel takes over the boot process.
345. A user notes that the username and password are automatically populated in the Microsoft Edge browser when logging into a secure site. When the user tries to log into the same site using Google Chrome, the username and password do not save automatically. Why is this occurring?
- Google Chrome does not support that secure site.
- The certificate for that site has not been authenticated.
- Google Chrome does not automatically save web credentials.
- The Google Chrome browser is corrupt.
346. Which statement is true regarding libraries in Windows 10?
- Libraries allow Windows 10 to support file names longer than 20 characters.
- Libraries allow Windows 10 to link multiple different directories.
- Libraries allow Windows 10 to enforce the EFS file system.
- Libraries allow Windows 10 to index files faster.
347. Match the steps that will lead to the loading of bootmgr.exe in a 32 bit Windows 10 environment.
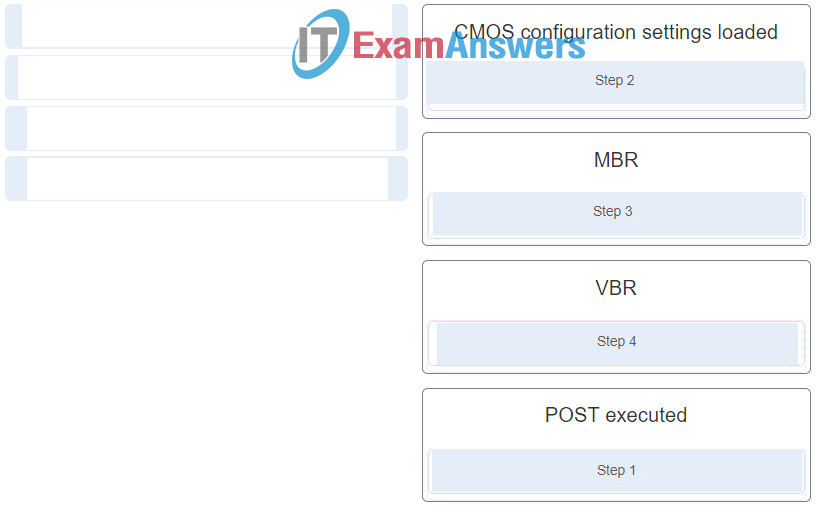
348. Select the Windows 10 version that best meets the described use.
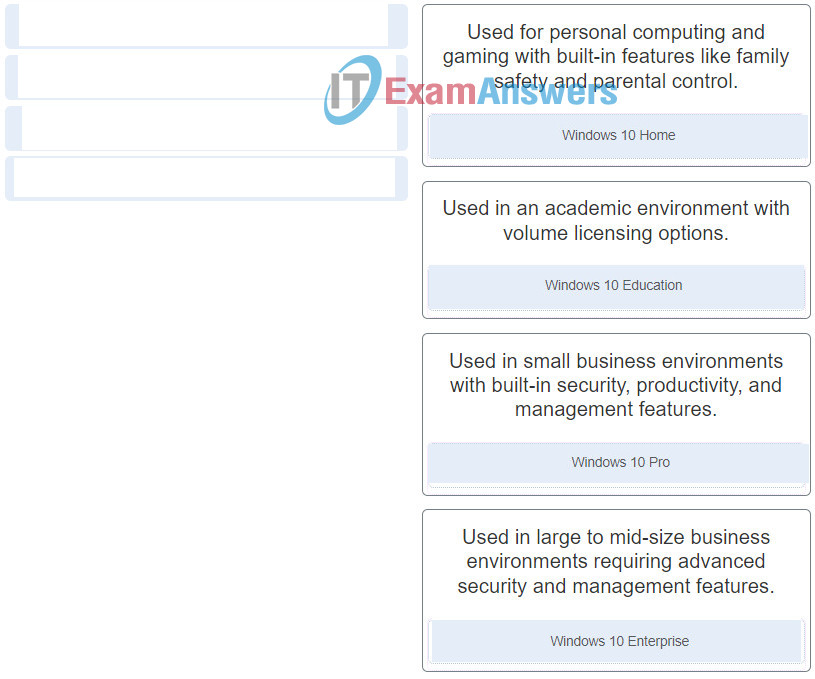
349. Match the file system with the respective description.
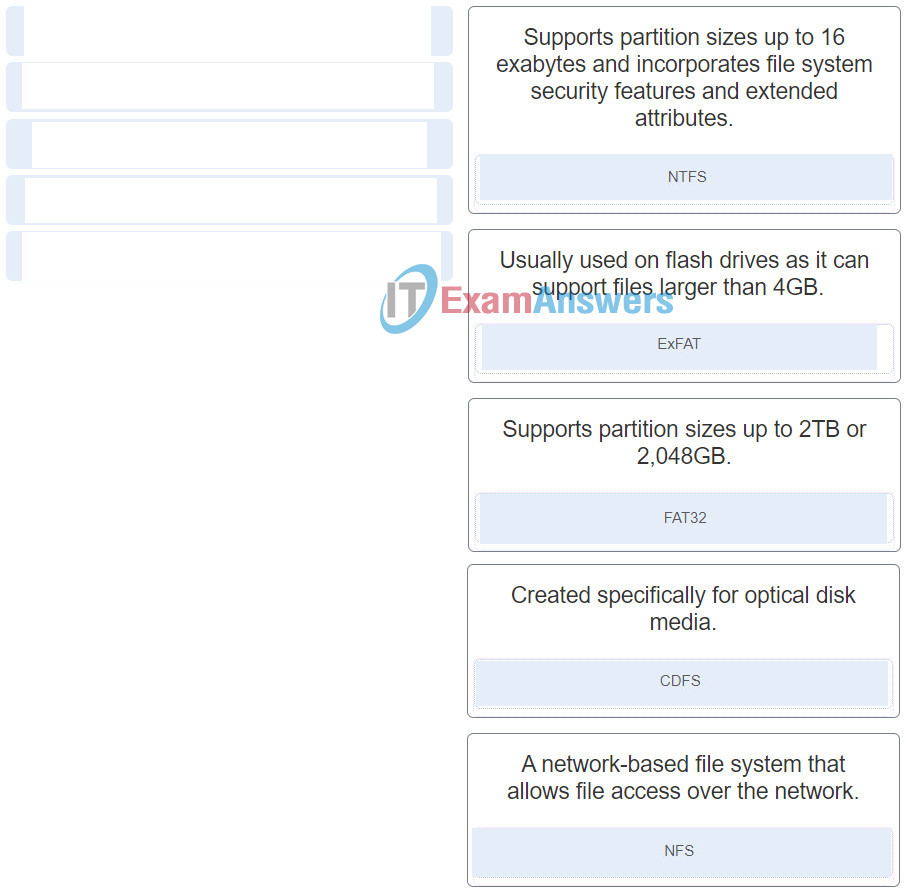
350. A corporation would like to use three or more factors for the password authentication policy. How can this be achieved?
- 2FA
- SFA
- bitlocker
- MFA
351. A person has started a new technical job. In which situation would ESD be an issue?
- while exchanging one laptop AC adapter with one that is not from the original equipment manufacturer
- when using a grounded mat and working on a computer on an ungrounded workbench
- when replacing a motherboard
- when installing a dual-voltage power supply
352. A manager is booting a tablet that has Windows 10 installed. The boot process is currently working on the following step: WINLOGON.EXE displays the Windows Welcome screen What is the next step that will happen in the boot process?
- Winload uses the path specified in BOOTMGR to find the boot partition.
- The BIOS boots the computer using the first drive that contains a valid boot sector.
- The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager.
- There are no more steps, the boot process is complete.

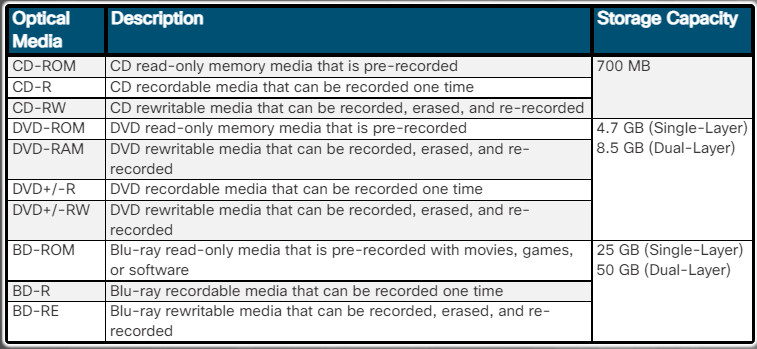
There is no answer to question 131
A typo
Does this include the most recent version of the exam (8.01)?
Is this the most recent version of the test?
Learned the Questions and answers and made 100%
Thanks a lot
What is a usual feature of the tip of a screwdriver in the toolkit of a PC technician?
Hi IT Administrator i have discovered an error in this question 153. What are two methods of disabling cellular data when located in an area where it is limited or expensive? (Choose two.)
you had only one marked as right and i think the second should be placing the device in an airplane mode, I may be wrong just sayin
I fixed it, thank you.
A person has started a new technical job. In which situation would ESD be an issue?
I added. Thank you.
153. What are two methods of disabling cellular data when located in an area where it is limited or expensive? (Choose two.)
“placing the device in Airplane mode” as the 2nd choice as the question asks for 2 selections
I fixed it, thank you.
1
What is required as an additional verification mechanism on iOS mobile devices when setting up biometric screen locks, such as Touch ID or Face ID?
Which cloud computing characteristic enables multiple tenants to share the same storage, processing, and network bandwidth?
This is false answer. True answer is Resource pooling.
Resource pooling, the provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model. Each model, each tenant (i.e., customer) shares the different physical and virtual resources dynamically assigned and reassigned according to consumer demand. Examples of resources that can be pooled and shared include storage, processing, memory, and network bandwidth.
I fixed it. Thanks a lot
resource pooling
Dear IT administrator,
I believe that there are some mistakes with the answers of questions 123, 126, 130, 182, 208, 306.
I think the answers should be:
123. What are three factors to consider when purchasing a replacement motherboard? (Choose three.)
Because you have to match the motherboard with the parts like power supply form factor, case form factor, cpu socket/chipset, RAM that will remain the same. You replace only the motherboard in this case.
126. What two effects might suggest that an incorrect printer driver is loaded on the Windows PC?
Reason why I believe that:
104. A reporter is complaining about the following printer issue: The printer is printing unknown characters. What are two possible causes of this issue? (Choose two.)
130. Which type of optical drive supports the greatest amount of storage and is able to read and write CDs, DVDs, and Blu-Ray media?
182. Why would a lawyer need to use the tracert command?
208. Refer to the exhibit. (where is the exhibit?) Which type of adapter card may require the width of two slots in order to accommodate additional cooling, even though it only has one PCIe x16 connector? (PCIe x16 slots are generally intended for use with Graphics Cards. Capture devices usually use PCIe 1x slots)
306. Which situation can be prevented by creating a UEFI password?
Please check again and correct the faults if I am right. If I am wrong, could you please explain me why?
Yes, you are right. I have reviewed and corrected those questions, thank you very much!
Is this still up to date? I am going to write the exam in a few weeks, are here all the possible questions for the it essential 7.02?
Did you pass exam?
was it the same or not?
This is nice staff
Which two activities are normally controlled by the Northbridge part of the chipset? (Choose two
A technician is working on a laptop and GPS is not functioning. What is a possible solution for this situation?
Verify the status of service.
in the 122 it says to choose 2 but only one is highlighted
What’s the answer to this? It said to choose two, and the answer above is only one.
An on-site IT technician is attempting to resolve an issue with application performance on a customer laptop. The technician backs up the customer data and then replaces the memory in the laptop with known good memory. It does not resolve the performance issue. What are the next two actions the technician should take? (Choose two.)
Um técnico deseja implantar o Windows 10 pro em vários PCs através do processo de instalação de rede remota. O técnico começa a conectando os novos computadores à rede e inicializando-os. No entanto, a implantação falha porque os computadores de destino não podem se comunicar com o servidor de implantação. Qual é possível a causa?
An instructor has given a student an assignment to assemble a PC. In which situation should the student be aware that ESD is an issue?
when walking across a carpeted area and then touching a keyboard that is attached to a tower PC
when installing a UPS
when working in a corporate environment that has carpet installed under tower PCs
when replacing a mechanical hard drive with an M.2 SSD
Navigation Bar
how many questions will be included in the test
THANK YOU
i haveCCNA ITE exams next week will i find these questions in exams?
i have ccna ite exams next week will i find these questions in exams?
If The Final exam is Activated again. Will the questions be the same? Or will they change the questions?
They will change 50% questions, but it still in here
¿Qué se necesita como mecanismo de verificación adicional en los dispositivos móviles con iOS cuando se configuran los bloqueos de pantalla biométricos, como la identificación táctil o del rostro?
Why would a user need to use the gpupdate command?
Answer: to make the PC synchronize with new group policy settings
Thanks for your sharing!
An analyst is booting a tablet that has Windows 7 installed with media card reader. The boot process is currently working on the following step: WINLOGON.EXE displays the Windows Welcome screen What is the next step that will happen in the boot process?
Answer: There are no more steps, the boot process is complete.
This morning, he calls to ask for assistance. He is unable to connect to the school’s Wi-Fi Internet on his laptop. What steps would you suggest to Anita to resolve the issue?
Why would a technician need to use the copy command?
Thanks for your sharing!!
So if I focus on all of these questions I should have a good chance at the Final Exam, right? The name of the exam is exactly the same as this one.
Yes, it same
thanks bro
I will soon have the final exam Version 7.0 and it contains 60 questions. But here I see 218. I have to learn them all
Which term describes a file system that supports a partition size up to 2 TB?
answer: FAT32
Thanks for your sharing!
A technician is working on a laptop and an app is not loading. What is a possible solution for this situation?
Added, thanks for sharing!
perform a reset
A user is booting a desktop that has Windows 10 installed that also uses an extended partition. The boot process is currently working on the following step: The code in the boot sector is executed and the control of the boot process is given to Windows Boot Manager. What is the next step that will happen in the boot process?
Thanks for your sharing!
Admins,
Should I be concentrating on the composite questions are should i be looking at the Ch1-9 and Ch10-14 as the composite has different questions to the Chapter questions?
Many thanks
Many questions vary, so you should concentrate on all exams/chapters
Refer to the exhibit. The help desk is receiving numerous calls from employees in the payroll department. It appears that their computers can print to the local network printer, but cannot access the cloud-based payroll service. One employee sends a screen print showing the result of issuing an ipconfig /all command. What is the cause of the issue being experienced by the users?
= The DHCP server is configured with the wrong default gateway address.
An accountant is booting a desktop that has Windows 8 installed. The boot process is currently working on the following step: WinLoad loads two files that make up the core of Windows: NTOSKRNL.EXE and HAL.DLL. What is the next step that will happen in the boot process?
Added, thanks for sharing!
can cisco tell if you are cheating and using this website during the exam? has anyone been caught cheating? I’m curious because I know cisco uses canvas to monitor their exams and they can see if you switched tabs or went off the screen. if you’ve taken the exam already while using this website, did they ever find out??
No. Unless you are getting perfect scores every single test you are fine. Just be sure you know a decent amount of the subject itself if questioned.
-T
Why would a user need to use the gpresult command?
Thanks for sharing!
A gamer is booting a tablet that has Windows 7 installed with 4 GB RAM. The boot process is currently working on the following step: The Windows kernel takes over the boot process. What is the next step that will happen in the boot process?
Thanks for sharing!
Refer to the exhibit. Which type of adapter card may require the width of two slots in order to accommodate additional cooling, even though it only has one PCIe x16 connector?
Shouldn’t the correct answer be the Graphics card instead?
A technician follows the instruction manual that came with a new Bluetooth speaker to place the speaker in discoverable mode. In this mode, what type of information will the speaker transmit to the laptop in order to start the pairing process?
Added, thanks for sharing!
A technician is booting a PC that has Windows 10 installed on dynamic drives. The boot process is currently working on the following step: BIOS locates and reads the configuration settings that are stored in the CMOS memory. What is the next step that will happen in the boot process?
Thanks for sharing!
A technician follows the instruction manual that came with a new Bluetooth speaker to place the speaker in discoverable mode. In this mode, what type of information will the speaker transmit to the laptop in order to start the pairing process?
Refer to the exhibit. What can be determined from the output of this command?
Added all. Thanks for sharing
In which situation would an ESD strike potentially cause harm to the PC?
i think is when you install ram
Which type of disk drive can provide a very fast boot experience and also provide high capacity storage?
ssd
1) Why is unbuffered memory a better choice than buffered memory for gaming or general use computers?
– The additional control circuitry on the unbuffered RAM module speeds up memory reads.
– Buffered memory cannot support the larger quantities of RAM that are necessary for gaming computers.
* The computer can read data directly from the unbuffered memory banks, making unbuffered memory faster than buffered memory.
– The control chip built into the unbuffered RAM module assists the memory controller to manage large amounts of RAM.
2) A UTM appliance, such as a Cisco ASA 5506-X, includes thè functionality of which two standalone devices? (Choose two.)
– DSL modem
– external Storage drive
* stateful firewall
* IPS/IDS
– 24-port LAN switch
3) An on-site IT technician is attempting to resolve an issue with application performance on a customer laptop. The technician backs up the customer data and then replaces the memory in the laptop with known good
memory. It does not resolve the performance issue. What are the next two actions the technician should take? (Choose two.)
– Call the laptop manufacturer technical support line
– Continue to test the nextlikely probable cause
– Document that the possible solution did notwork
– Reinstall the original memory sticks
– Escalate the issueto the next level support technician
4) A user wants VirtualBox to run automatically when Windows 10 starts up. Which action will enable VirtualBox to load and run on system startup?
* Copy the shortcut for VirtualBox from its location to the startup folder.
– Right click on the application in the Start menu and choose the startup option.
– Use msconfig to change the startup option from manual to automatic.
– Use the Startup tab in Task Manager to add VirtualBox to the list of programs.
Updated, thanks for sharing!
An on-site IT technician finished the removal of malware from a customer computer and installed new virus protection software. An hour after the technician left the site, the customer called the help desk to report that a critical web-based application was no longer functioning properly. Which step in the troubleshooting process did the IT technician fail to properly complete?
Thanks for sharing
A person has started a new technical job. In which situation would ESD be an issue?
what is the answer?
https://itexamanswers.net/question/a-person-has-started-a-new-technical-job-in-which-situation-would-esd-be-an-issue
when installing RAM