Networking Devices and Initial Configuration Checkpoint Exam: Characteristics of Network Design Answers
1. A college is building a new dormitory on its campus. Workers are digging in the ground to install a new water pipe for the dormitory. A worker accidentally damages a fiber optic cable that connects two of the existing dormitories to the campus data center. Although the cable has been cut, students in the dormitories only experience a very short interruption of network services. What characteristic of the network is shown here?
- fault tolerance
- integrity
- quality of service (QoS)
- scalability
- security
Explanation: Fault tolerance is the characteristic of a network which allows it to quickly respond to failures of network devices, media, or services. Quality of service refers to the measures taken to ensure that network traffic requiring higher throughput receives the required network resources. Scalability refers to the ability of the network to grow to accommodate new requirements. Security refers to protecting networks and data from theft, alteration, or destruction. Integrity refers to the completeness of something and is generally not used as a characteristic of networks in the same way as the other terms.
2. Which feature relies on prioritization of network traffic and is used to ensure successful delivery of real-time services?
- security
- redundancy
- quality of service
- reliability
Explanation: Quality of Service (QoS) is implemented in networks to prioritize traffic. Traffic for real-time services such as voice and video requires a higher priority than data traffic to ensure reliable delivery of voice and video content to users.
3. A networking technician is working on the wireless network at a medical clinic. The technician accidentally sets up the wireless network so that patients can see the medical records data of other patients. Which of the four network characteristics has been violated in this situation?
- fault tolerance
- security
- scalability
- Quality of Service (QoS)
- reliability
Explanation: Network security includes protecting the confidentiality of data that is on the network. In this case, because confidential data has been made available to unauthorized users, the security characteristic of the network has failed.
4. Which term describes the state of a network when the demand on the network resources exceeds the available capacity?
- convergence
- synchronization
- congestion
- optimization
Explanation: When the demand on the network resources exceeds the available capacity, the network becomes congested. A converged network is designed to deliver multiple communication types, such as data, video and voice services, using the same network infrastructure.
5. Which is a characteristic of a Type 2 hypervisor?
- installs directly on hardware
- does not require management console software
- best suited for enterprise environments
- has direct access to server hardware resources
Explanation: Type 2 hypervisors are hosted on an underlaying operating system and are best suited for consumer applications and those experimenting with virtualization. Unlike Type 1 hypervisors, Type 2 hypervisors do not require a management console and do not have direct access to hardware.
6. What type of address is physically assigned to the NIC of a workstation?
- MAC address
- host address
- IP address
- network address
Explanation: A MAC address is physically assigned to the host NIC and is known as the physical address. The physical address remains the same regardless of where the host is placed on the network. The IP address is known as a logical address because it is assigned logically based on where the host is located. IP addresses contain two parts, network address and host address.
7. An administrator is adding voice and video service capabilities to an existing network. What design requirement is being satisfied by this situation?
- availability
- security
- manageability
- scalability
Explanation: Scalability refers to the ability of a network to expand to support new users, services, and applications. In this example, scalability allows the administrator to expand the ability of the network to support voice and video.
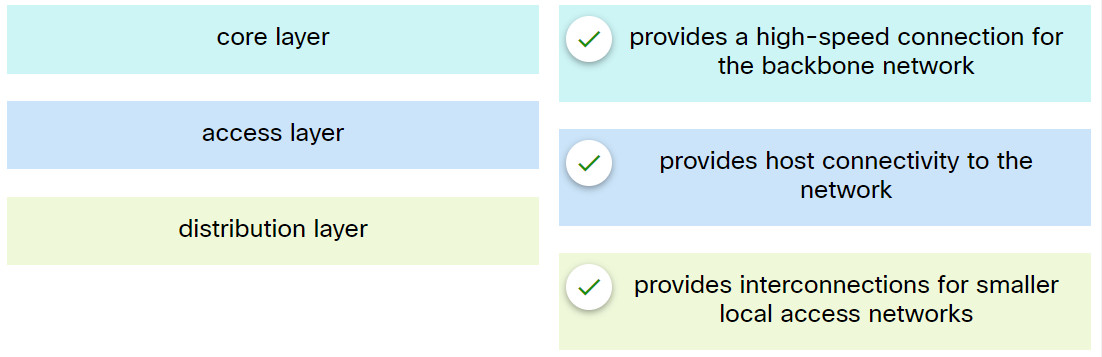
8. Match the hierarchical design layer with the description.
Networking Devices and Initial Configuration Module 1 – 3 Checkpoint Exam
Explanation: Place the options in the following order:
| access layer |
provides host connectivity to the network |
| core layer |
provides a high-speed connection for the backbone network |
| distribution layer |
provides interconnections for smaller local access networks |
9. Which characteristic defines a private cloud?
- created for a specific community
- composed of two or more clouds
- intended for a specific organization
- available to the general public
Explanation: A private cloud is one that is available to a specific organization and not to the general public.
10. A company is considering implementing virtualization solutions in a data center. What are three advantages of virtualization the company can expect to benefit from?(Choose three.)
- faster server provisioning
- improved disaster recovery
- reduced physical space requirements
- less employee training
- reduced security requirements
- shorter work week
Explanation: Virtualization is the ability to run many instances of an OS simultaneously on the same hardware platform. This reduces the amount of equipment that is required, thus resulting in less power consumption and improved disaster recovery.
11. Which Cloud computing service would be best for an organization that needs to collaboratively create applications and deliver them over the web?
Explanation: Platform as a service (PaaS) provides a collaborative environment where multiple developers can create software and host an application through a Cloud provider.
12. A company leases a cloud-based payroll system. Which cloud computing technology is this company using?
- wireless as a service (WaaS)
- infrastructure as a service (IaaS)
- software as a service (SaaS)
- platform as a service (PaaS)
Explanation: Software as a service (SaaS) refers to on demand software that is leased from the provider. Platform as a service (PaaS) is when the provider provides the platform for a developer. Infrastructure as a service (IaaS) is when key network devices such as routers and firewalls are leased from a provider. Wireless as a service (WaaS) is when a provider provides wireless connectivity at a fixed monthly cost.
13. What is the function of a hypervisor?
- to perform FCAPS functions for VNFs
- to centralize management of vSwitch configuration
- to create VMs and provide hardware abstraction to support them
- to create an isolated environment where containerized applications run
Explanation: A hypervisor is a software process that abstracts the hardware layer from the operating systems allowing multiple virtual machines to run simultaneously.
14. Which Cloud computing service would be best for a new organization that cannot afford physical servers and networking equipment and must purchase network services on-demand?
Explanation: Infrastructure as a service (IaaS) provides an environment where users have an on-demand infrastructure that they can install any platform as needed.
15. What is the decimal equivalent of the hexadecimal value of 3F?
Explanation: In order to convert a hexadecimal number to decimal, consider that the digit to the far right represents the 1s column where values 0 through F can appear. A hexadecimal value of A equals the decimal number 10. B equals 11, and so on through F equaling 15. The value of F in the number F equals 15. Next consider the value of 3 in the hexadecimal number of 3F. That place holder is the 16s column. Multiple the number 3 times 16 for a total of 48. Add 48 to 15 for the grand total of 63. Hexadecimal 3F equals a decimal value of 63.
16. Which IPv4 address format was created for ease of use by people and is expressed as 201.192.1.14?
- dotted decimal
- binary
- hexadecimal
- ASCII
Explanation: For ease of use by people, binary patterns are represented as dotted decimal. Computer systems were created to understand binary addressing.
17. How many unique values are possible using a single binary digit?
Explanation: Binary is a numbering system that consists of the digits 0 and 1 called bits. A binary number is a series of only 1s and 0s.
18. A student is learning number systems. What is the hexadecimal equivalent for the decimal number 165?
Explanation: Decimal 165 in binary is 10100101. 128+32+4+1 = 165.
Each 4 binary digits equates to 1 hexadecimal digit.
1010 = 10 (decimal) = A (hexadecimal)
0101 = 5 (decimal) = 5 (hexadecimal)
19. What is the hexadecimal equivalent for the binary number 10111010?
Explanation: Each 4 binary digits equates to 1 hexadecimal digit.
1011 = 11 (decimal) = B (hexadecimal)
1010 = 10 (decimal) = A (hexadecimal)
20. What is the dotted decimal representation of the IPv4 address which is represented as the binary string 00001010.01100100.00010101.00000001?
- 100.10.11.1
- 100.21.10.1
- 10.100.21.1
- 10.10.20.1
Explanation: Converting the binary string of 00001010.01100100.00010101.00000001 to dotted decimal gives 10.100.21.1
21. What are two differences between binary and decimal numbers? (Choose two.)
- Binary numbers are based on powers of 2.
- Decimal numbers are based on powers of 1.
- Decimal numbers include 0 through 9.
- Numbers typed on a keyboard are entered as binary and converted to decimal by the computer.
- Binary numbers consist of three states: on, off, null. Decimal numbers do not have states.
Explanation: Computing devices use the binary system for data processing and storage. Binary numbers are based on powers of 2 and decimal numbers are based on powers of 10.
22. How many bits make up the single IPv6 hextet :10CD:?
Explanation: A hextet consists of 4 hexadecimal characters. Each hexadecimal character is represented by four bits, giving a total of 16 bits.
23. Which statement accurately describes a Type 2 hypervisor?
- It is commonly an open source operating system.
- It runs as a software layer on top of a host operating system.
- It is the most common type of hypervisor in enterprise data centers.
- It sits directly on bare metal and provides the ability to virtualize the hardware for multiple virtual machines.
24. Which layer of the hierarchical design model provides a means of connecting devices to the network and controlling which devices are allowed to communicate on the network?
- application
- distribution
- network
- access
- core


How many bits make up the single IPv6 hextet :10CD:?
4
***16
8
32
I added all. Thank you so much.
Which statement accurately describes a Type 2 hypervisor?
It is commonly an open source operating system.
***It runs as a software layer on top of a host operating system.
It is the most common type of hypervisor in enterprise data centers.
It sits directly on bare metal and provides the ability to virtualize the hardware for multiple virtual machines.
Which layer of the hierarchical design model provides a means of connecting devices to the network and controlling which devices are allowed to communicate on the network?
application
distribution
network
***access
core