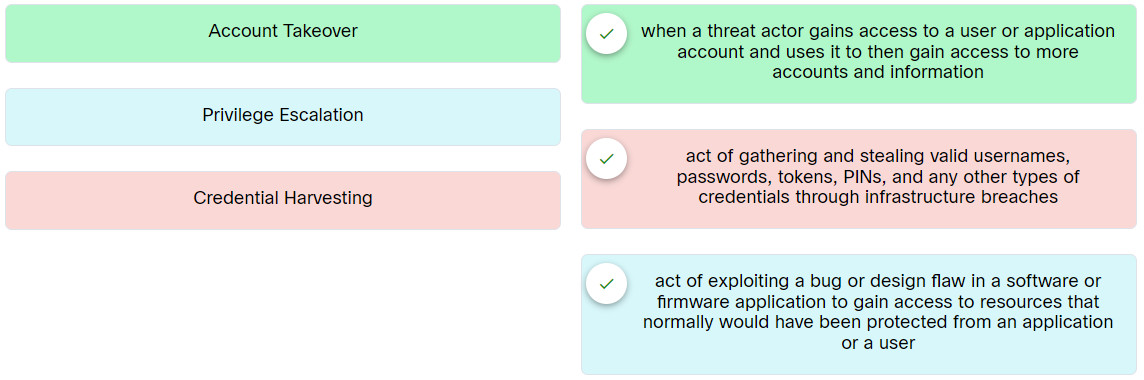
Match the cloud attack to the description.
Place the options in the following order:
| Credential Harvesting | act of gathering and stealing valid usernames, passwords, tokens, PINs, and any other types of credentials through infrastructure breaches |
| Privilege Escalation | act of exploiting a bug or design flaw in a software or firmware application to gain access to resources that normally would have been protected from an application or a user |
| Account Takeover | when a threat actor gains access to a user or application account and uses it to then gain access to more accounts and information |
Exam with this question: Ethical Hacker: Course Final Exam Answers
Please login or Register to submit your answer
