Category: 120 Labs CCNA
120 Labs and solutions to give you the confidence and speed to pass the practical teste in your Cisco CCNA and CCENT exams: Exam CCNA 200-125, Exam ICND1 100-105, Exam ICND2 200-105
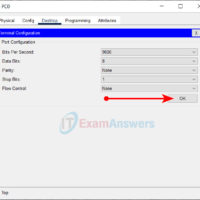
In Packet Tracer, to access the command line interface (CLI) of a Switch or Router, you can use one of the following two ways: The CLI tab Console port The CLI tab This is the simplest way to access the Command Line Interface (CLI) of a Switch/Router. Click …
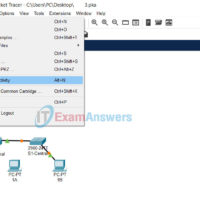
Use Reset Activity if you want to clear your work, which starts the activity over, or gain more practice. Step 1: Open Activity Packet Tracer .PKA file Step 2: Click File menu > Reset Activity (Alt + N)
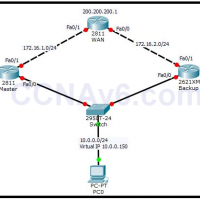
High availability and redundancy is one of the most important factor to enhance the productivity and reputation of an organization. The redundancy can be applied at the various levels such as Server level, Disk-level, and even the network device-level. In this exercise, we will explain the high availability …
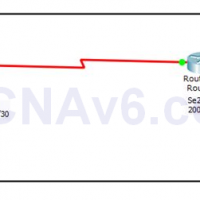
There are many ways to interconnect routers. One of the most popular and traditional way to interconnect routers on a WAN network is using the Serial interfaces. A serial cable has two ends: Data Communication Equipment (DCE) and Data Terminal Equipment (DTE). The DCE end is typically located …
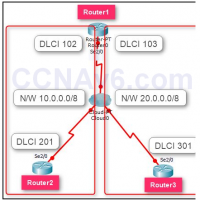
Frame-relay is a WAN technology that supports up to 44.3 Mbps of speed. Nowadays it is not so much popular and heavily replaced by the latest technologies such as ATM. We assume that you know the basics of Frame-relay technology and are familiar with the basic components such …
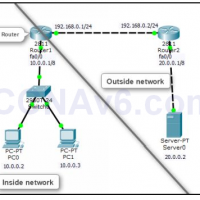
Network Address Translation (NAT) technique translates private IP addresses into public IP addresses. NAT enhances the security of the network by hiding the actual IP information from the external users. The external users see the translated IP addresses rather than actual IP addresses. This is also called masking. …
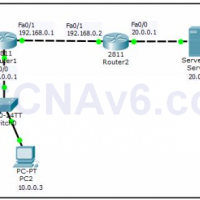
Access Control List (ACL) is a security feature that allows you to filter the network traffic based on configured statements. An ACL can be used to filter either inbound or outbound traffic on an interface. Once you applied an access list on a router, the router examine every …
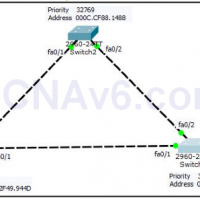
We know that Spanning-Tree Protocol (STP) help us to prevent to occur switching loop. However, spanning-tree sometime can also create a problem for your network. For example, suppose you have a server that is connected into your switch. You are sure that there are no chances to occur …
Network loop can create a huge problem in a network. Routing protocols such as RIP and IGRP have their own techniques to stop network loops from occurring at the Network layer of the OSI model. Unfortunately they (routing protocols) cannot be used to stop loops from occurring at …
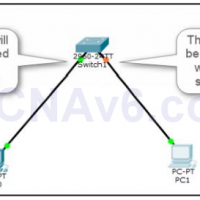
You can control to access your switch port. For example, you can control who can access a specific interface of a switch or how many devices could be connected to a specific switch interface. There is a feature called Switch Port Security that allow you to do so. …