Match the cybersecurity term with the respective description.
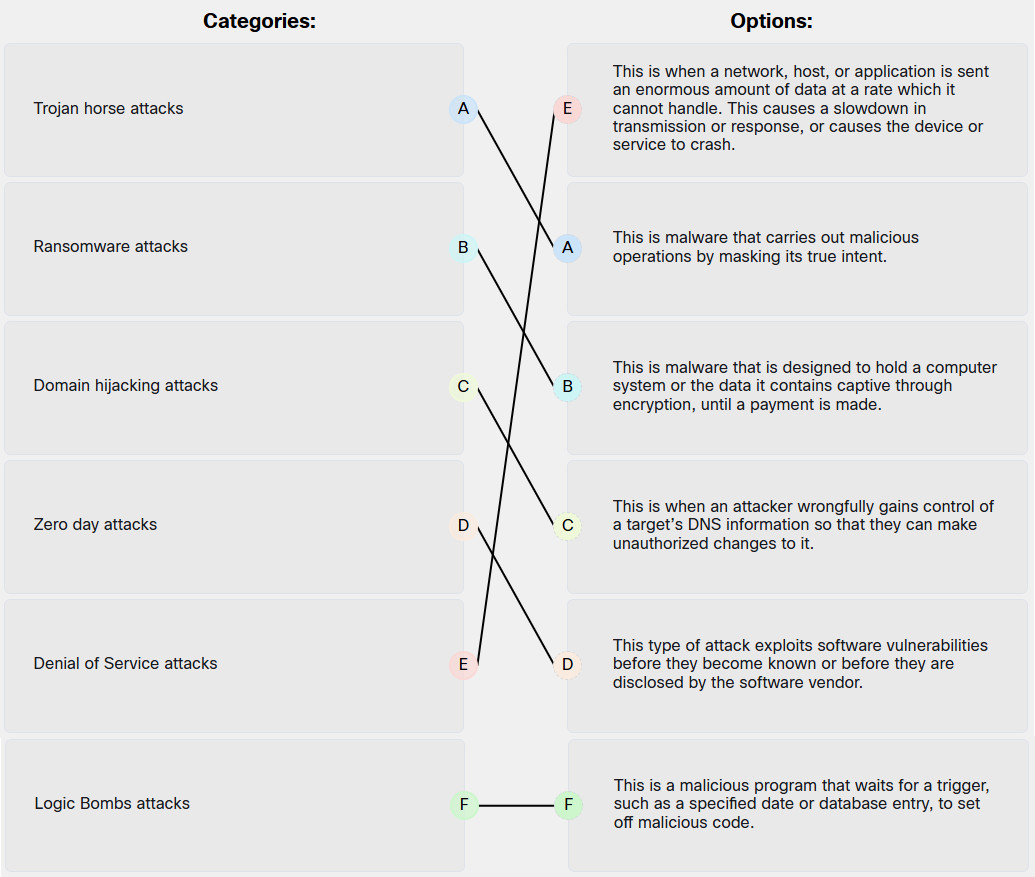
Explanation: Place the options in the following order:
| Trojan horse attacks | This is malware that carries out malicious operations by masking its true intent. |
| Ransomware attacks | This is malware that is designed to hold a computer system or the data it contains captive through encryption, until a payment is made. |
| Domain hijacking attacks | This is when an attacker wrongfully gains control of a target’s DNS information so that they can make unauthorized changes to it. |
| Zero day attacks | This type of attack exploits software vulnerabilities before they become known or before they are disclosed by the software vendor. |
| Denial of Service attacks | This is when a network, host, or application is sent an enormous amount of data at a rate which it cannot handle. This causes a slowdown in transmission or response, or causes the device or service to crash. |
| Logic Bombs attacks | This is a malicious program that waits for a trigger, such as a specified date or database entry, to set off malicious code. |
Exam with this question: 2.3.13 Check Your Understanding - Cyber Attacks
Please login or Register to submit your answer
