Match the cybersecurity threat term with the respective description.
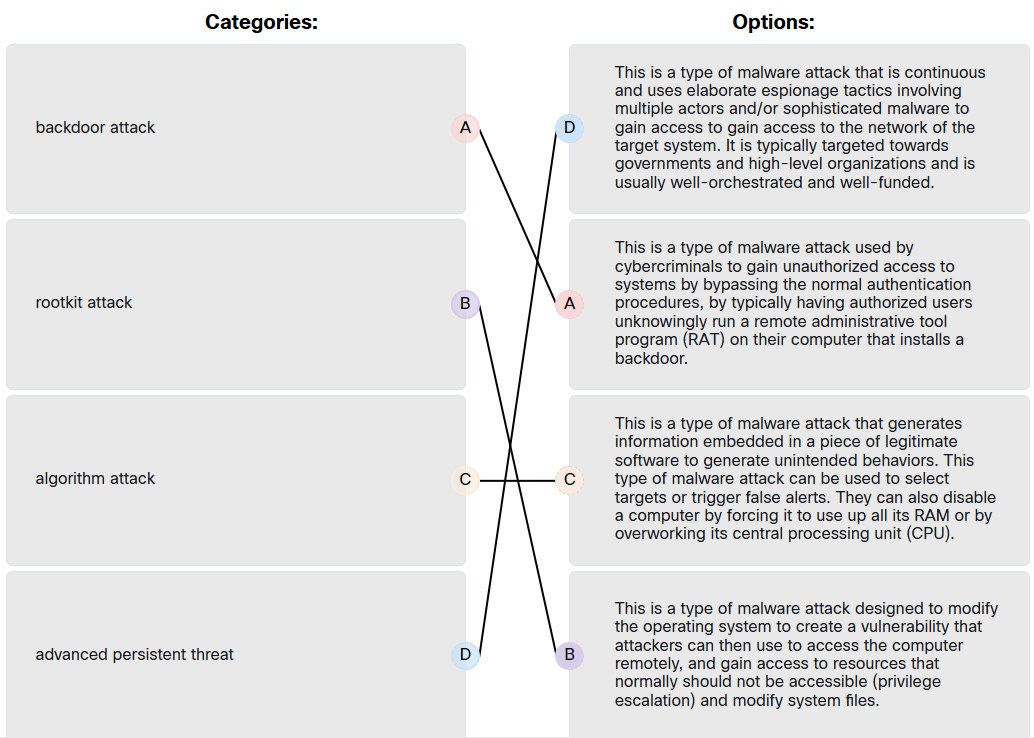
Explanation: Place the options in the following order:
| backdoor attack | This is a type of malware attack designed to modify the operating system to create a vulnerability that attackers can then use to access the computer remotely, and gain access to resources that normally should not be accessible (privilege escalation) and modify system files. |
| rootkit attack | This is a type of malware attack used by cybercriminals to gain unauthorized access to systems by bypassing the normal authentication procedures, by typically having authorized users unknowingly run a remote administrative tool program (RAT) on their computer that installs a backdoor. |
| algorithm attack | This is a type of malware attack that generates information embedded in a piece of legitimate software to generate unintended behaviors. This type of malware attack can be used to select targets or trigger false alerts. They can also disable a computer by forcing it to use up all its RAM or by overworking its central processing unit (CPU). |
| advanced persistent threat | This is a type of malware attack that is continuous and uses elaborate espionage tactics involving multiple actors and/or sophisticated malware to gain access to gain access to the network of the target system. It is typically targeted towards governments and high-level organizations and is usually well-orchestrated and well-funded. |
Exam with this question: 2.1.15 Check Your Understanding - Common Threats
Please login or Register to submit your answer
