Match the insecure code practice to the description.
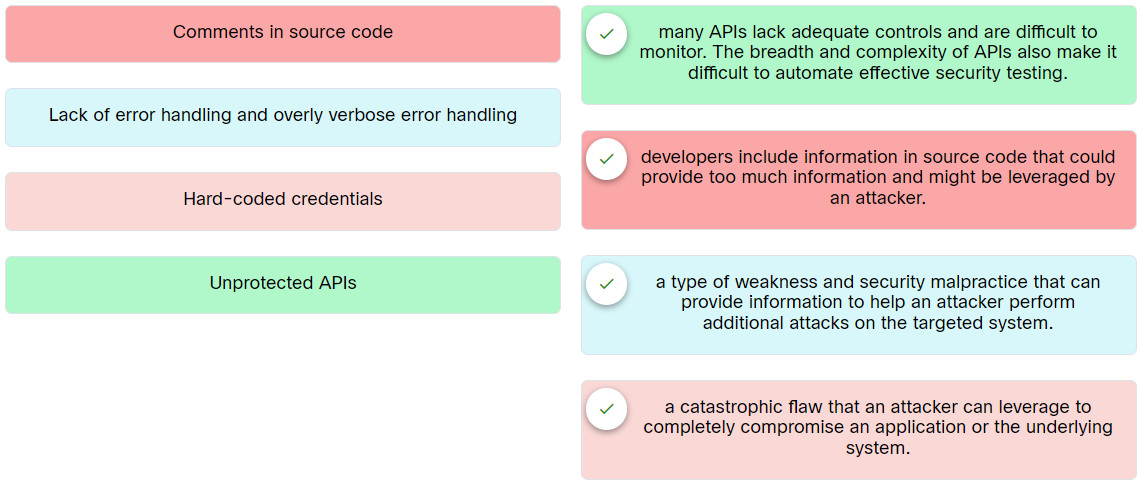
Place the options in the following order:
| Hard-coded credentials | a catastrophic flaw that an attacker can leverage to completely compromise an application or the underlying system. |
| Comments in source code | developers include information in source code that could provide too much information and might be leveraged by an attacker. |
| Lack of error handling and overly verbose error handling | a type of weakness and security malpractice that can provide information to help an attacker perform additional attacks on the targeted system. |
| Unprotected APIs | many APIs lack adequate controls and are difficult to monitor. The breadth and complexity of APIs also make it difficult to automate effective security testing. |
Exam with this question: Ethical Hacker: Course Final Exam Answers
Please login or Register to submit your answer
