Refer to the exhibit. A VPN tunnel is configured on the WAN between R1 and R2. On which R1 interface(s) would a crypto map be applied in order to create a VPN between R1 and R2?
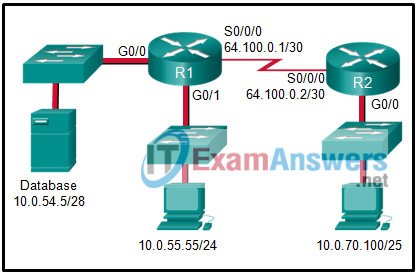
- G0/0 and G0/1
- G0/0
- all R1 interfaces
- S0/0/0
Explanation: The crypto map command is used to finish creating the IPsec security policy by doing the following
binding the interesting traffic ACL and transform set to the crypto map
specifying the IP address of the remote VPN site
configuring the Diffie-Hellman group
configuring the IPsec tunnel lifetime
The crypto map is bound to the S0/0/0 R1 interface.
Exam with this question: Checkpoint Exam: VPNs Group Exam Answers
Please login or Register to submit your answer
