Refer to the exhibit. How is the traffic from the client web browser being altered when connected to the destination website of www.cisco.com?
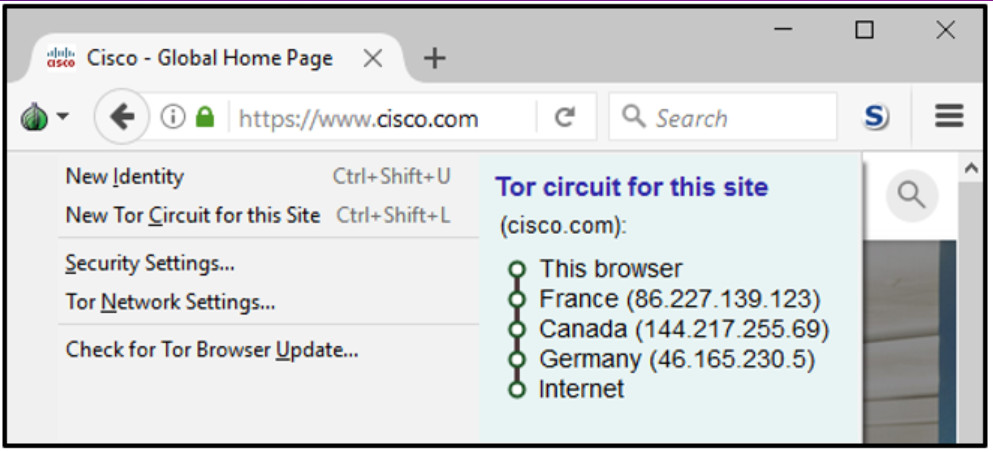
- Traffic is sent in plain-text by the user machine and is encrypted by the TOR node in France and decrypted by the TOR node in Germany.
- Traffic is encrypted by the user machine and sent directly to the cisco.com server to be decrypted.
- Traffic is encrypted by the user machine, and the TOR network only routes the traffic through France, Canada, Germany, and delivers it to cisco.com.
- Traffic is encrypted by the user machine, and the TOR network encrypts next-hop information on a hop-by-hop basis.
Explanation: When data is being sent into the TOR network, the data is only encrypted by the sending client itself. The next-hop information is encrypted and decrypted between the TOR relays on a hop-by-hop basis. In this way, no single device knows the entire path to the destination, and routing information is readable only by the device that requires it. Finally, at the end of the Tor path, the traffic reaches its Internet destination. The client data is not encrypted by the TOR network; that encryption is the responsibility of the user.
Exam with this question: CCNA Cyber Ops Chapter 11 Exam Answers
Please login or Register to submit your answer
