Match the intrusion event defined in the Diamond Model of intrusion to the description.
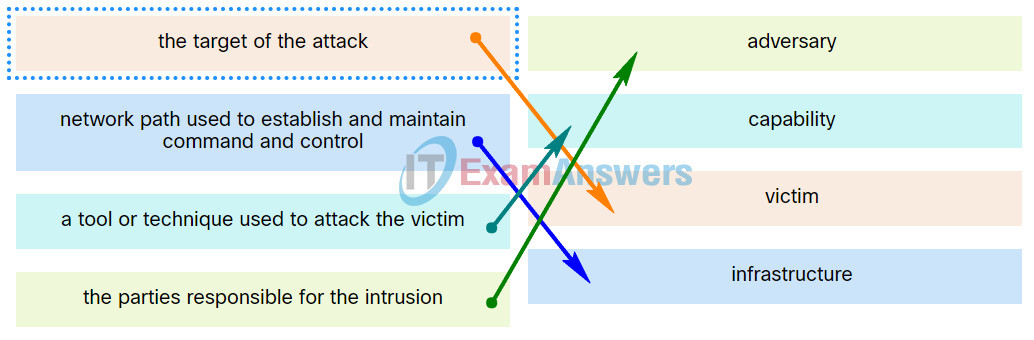
| network path used to establish and maintain command and controlk | infrastructure |
| a tool or technique used to attack the victim | capability |
| the parties responsible for the intrusion | adversary |
| the target of the attack | victim |
Exam with this question: Checkpoint Exam: Analyzing Security Data Group Exam
Exam with this question: Checkpoint Exam: Incident Response Answers
Please login or Register to submit your answer
