Match the steps in a typical vulnerability scan to the description.
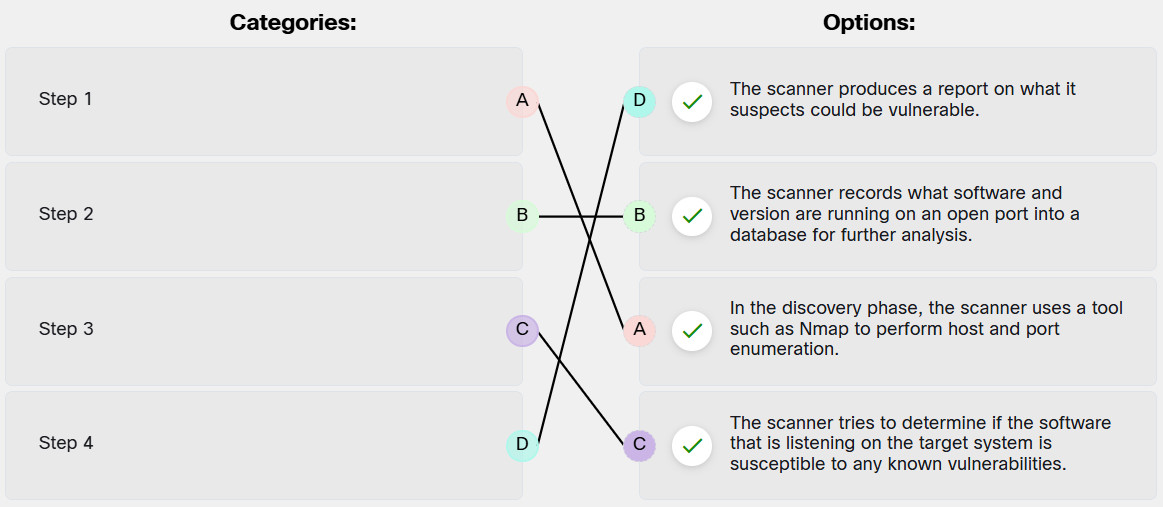
| Step 1 | In the discovery phase, the scanner uses a tool such as Nmap to perform host and port enumeration. |
| Step 2 | The scanner records what software and version are running on an open port into a database for further analysis. |
| Step 3 | The scanner tries to determine if the software that is listening on the target system is susceptible to any known vulnerabilities. |
| Step 4 | The scanner produces a report on what it suspects could be vulnerable. |
Exam with this question: 3.3.3 Practice - How a Typical Automated Vulnerability Scanner Works
Please login or Register to submit your answer
