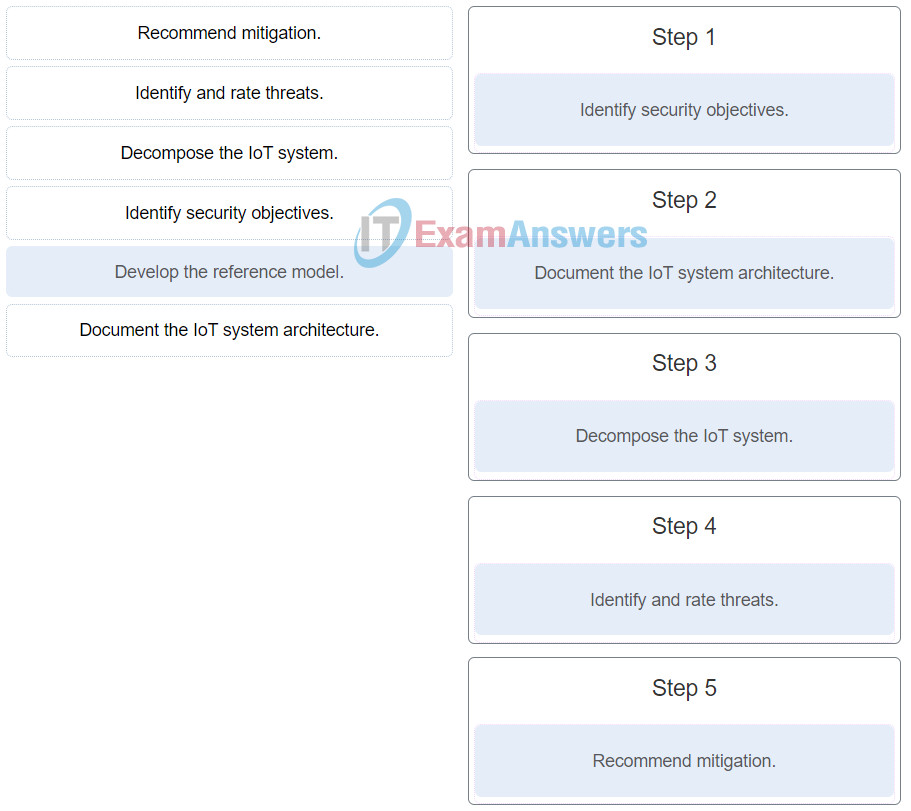
Put the steps in the Threat Modeling process into the correct order. (Not all options are used.)
Exam with this question: IoT Sec 1.1 Fundamentals: IoT Security Final Exam Answers
Please login or Register to submit your answer
Put the steps in the Threat Modeling process into the correct order. (Not all options are used.)

Exam with this question: IoT Sec 1.1 Fundamentals: IoT Security Final Exam Answers
Please login or Register to submit your answer