IoT Sec 1.1 (Version 1.1) – IoT Fundamentals: IoT Security Final Exam Answers
How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
1. What process is used by blockchain technology to validate transactions?
- scope of work
- digital signatures
- synchronous key encryption
- proof of work
Explanation: Blockchain technology uses a process known as proof of work to validate transactions.
2. Which programming language is an example of an interpreted language?
Explanation: Python is an interpreted programming language. C, C#, and Java are compiled programming languages.
3. Which DFD symbol represents data output from sensing, actuating, traffic forwarding, analysis, and control systems?
- external entity
- data flow
- data store
- process
Explanation: DFDs use a series of four symbols:
External entity – users, contractors, and partners outside of the control of the system that send or receive data
Process – data output from sensing, actuating, traffic forwarding, analysis, and control systems
Data store – data at rest in local, fog, cloud, or data center storage
Data flow – single headed arrows that indicate uni-directional data flow; double headed arrows that indicate bi-directional data flow
4. What are three items that should be included in the documentation describing the components of the IoT system at each layer? (Choose three.)
- applications
- devices
- protocols
- technologies
- communications network
- the flow of data between components and layers
Explanation: During the step of documenting the IoT system architecture of the Threat Model Analysis for an IoT system, the document for components of the IoT system at each layer should include applications, communications network, and devices.
5. According to the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework by NIST, which work role in the risk management specialty area conducts comprehensive assessments of the management, operational, and technical security controls to determine their overall effectiveness?
- Security Architect
- Security Control Assessor
- Vulnerability Assessment Analyst
- Secure Software Assessor
Explanation: The Security Control Assessor work role is in the Securely Provision work category of the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework by NIST. This work role conducts comprehensive assessments of the management, operational, and technical security controls to determine their overall effectiveness.
6. Put the steps in the Threat Modeling process into the correct order. (Not all options are used.)
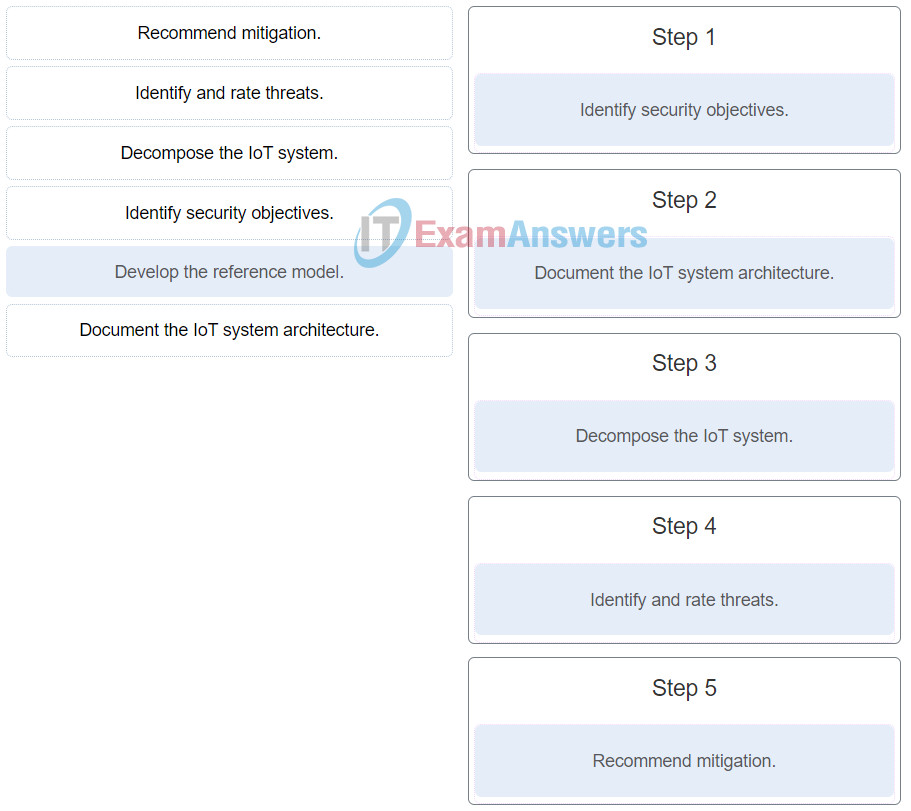
IoT Security (Version 1.0) – IoT Fundamentals: IoT Security Final Exam 38
7. A threat actor has used malicious commands to trick the database into returning unauthorized records and other data. Which web front-end vulnerability is the threat actor exploiting?
- cross-site scripting
- broken authentication
- security misconfiguration
- SQL injections
Explanation: Web front-end vulnerabilities apply to apps, APIs, and services. Some of the most significant vulnerabilities are as follows:
– Cross-site scripting : In a cross-site scripting (XSS) attack, the threat actor injects code, most often JavaScript, into the output of a web application. This forces client-side scripts to run the way that the threat actor wants them to run in the browser.
– SQL injections : In a SQLi the threat actor targets the SQL database itself, rather than the web browser. This allows the threat actor to control the application database.
– Broken authentication : Broken authentication includes both session management and protecting the identity of a user. A threat actor can hijack a session to assume the identity of a user especially when session tokens are left unexpired.
– Security misconfiguration : Security misconfiguration consists of several types of vulnerabilities all of which are centered on the lack of maintenance to the web application configuration.
8. According to the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework by NIST, which work role in the Vulnerability Assessment and Management specialty area performs assessments of IT systems and identifies where those systems deviate from acceptable configurations or policy?
- Vulnerability Assessment Analyst
- Secure Software Assessor
- Security Architect
- Security Control Assessor
Explanation: The Vulnerability Assessment Analyst work role is in the Securely Provision work category of the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework by NIST. This work role performs assessments of IT systems and identifies where those systems deviate from acceptable configurations or policy.
9. In a typical smart home setup, which two devices directly share the cable signal from the local cable service provider? (Choose two.)
- TV
- cable modem
- home gateway
- MCU or SBC board
- smart thermostat
Explanation: The TV and cable modem directly share the cable signal from the local cable service provider. Smart IoT devices, such as a thermostat, MCU and SBC board, and home gateway, all need to connect to a local or remote network. The connections are provided through the cable modem.
10. What are two OWASP communication layer vulnerabilities commonly found when securing the IoT device network services attack surface? (Choose two.)
- poorly implemented encryption
- LAN traffic
- lack of payload verification
- nonstandard protocols
- protocol fuzzing
Explanation: When the IoT device network services attack surface is being secured, the following vulnerabilities should be taken into account:
Information disclosure
Injection
Denial of service
Unencrypted services
Poorly implemented encryption
Test/development services
Vulnerable UDP services
Replay attack
Lack of payload verification
Lack of message integrity check
11. Which statement describes a security vulnerability of using a medical device on a legacy computer system in a hospital?
- The hard disk may become full.
- The OS of the PC may not receive up-to-date security patches.
- The CPU may become too slow for the medical application
- The memory may become the bottleneck for performance
Explanation: Many medical devices have a long period of use in hospitals and the computers used to operate them are often running old and unpatched operating systems, which poses many security vulnerabilities.
12. Match the feature of a personal fitness device to the supporting technology. (Not all targets are used.)
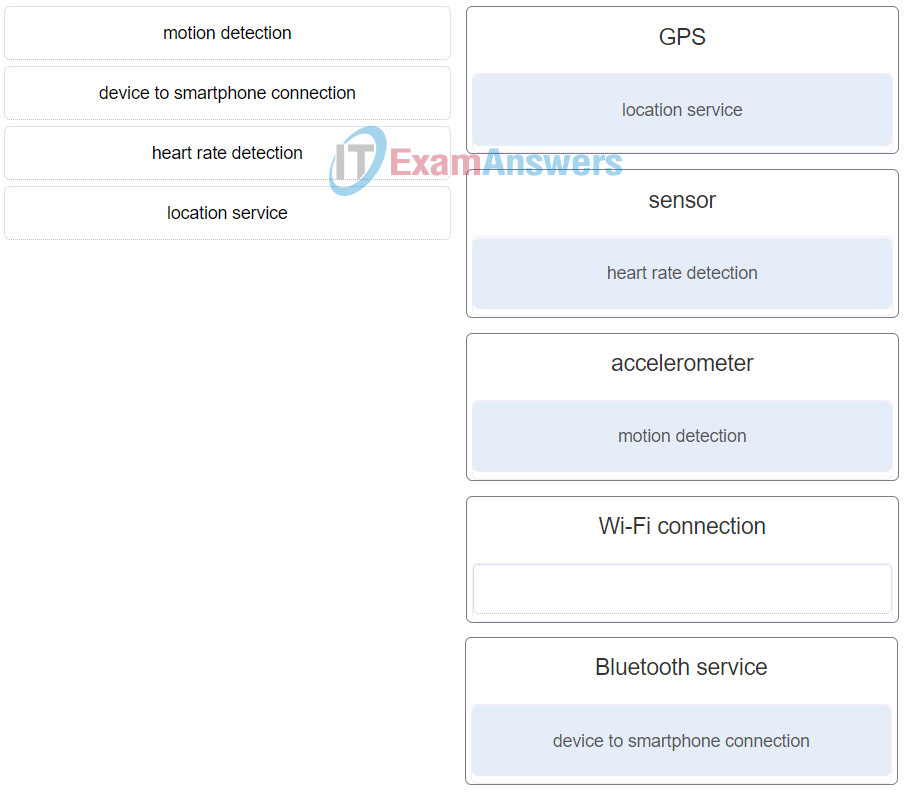
IoT Security (Version 1.0) – IoT Fundamentals: IoT Security Final Exam Q40
13. What is a local exploit used by threat actors?
- SQL injections
- device cloning
- eavesdropping attack
- routing attack
Explanation: Some of the most popular local exploits targeted by threat actors are as follows:
Firmware replacement – Updates and patches to devices are usually done remotely. If the process is not secure, threat actors could intercept the update and install their own malicious update, in which case they could have full control over the device and begin attacking other devices in the system.
Cloning – By creating a duplicate device, both in physical form and with the software and firmware running on that device, the threat actor could replace a legitimate device. When the device is up and running, the threat actor could then steal information, or compromise additional devices.
Denial of service (DoS) – The threat actor could launch a DoS attack to fill the communications channel causing devices to respond to requests late, or not at all. Depending on the devices, this could cause a lot of damage.
Extraction of security parameters – When a device is not protected properly, the threat actor may be able to extract security parameters from it such as authentication information or security keys.
14. A threat actor uses a newly discovered vulnerability to access the home wireless router of a user. The threat actor then changes the password for the wireless network served by the router and causes all wireless devices to lose connectivity. Which factor of smart home security is affected by this attack?
- firmware
- authentication
- WPA2
- encryption
Explanation: In general, the security requirements for a smart home should include the following:
WPA2 – The wireless network should use the latest Wi-Fi security, which is currently WPA2.
Encryption – It protects the confidentiality and integrity of information transmitted over a network.
Authentication – Strong authentication protects the device from unauthorized use or reconfiguration and prevents disclosure or modification of the data stored on the device.
Firmware – The IoT device manufacturers should update the firmware for any newly discovered vulnerabilities. The home IoT device users should enable the checking of updates automatically.
15. Which technology is used to secure IoT transactions?
- DREAD
- blockchain
- T-V pairing
- STRIDE
Explanation: Blockchain is a technology that is used to secure transactions. Blockchain came about as a technology used with bitcoin, a type of digital currency. STRIDE is used to identify threats. DREAD is a model used in risk assessment. Threat-vulnerability (T-V) pairing is used to create a risk baseline.
16. Match the IoT standard or protocol with a category.
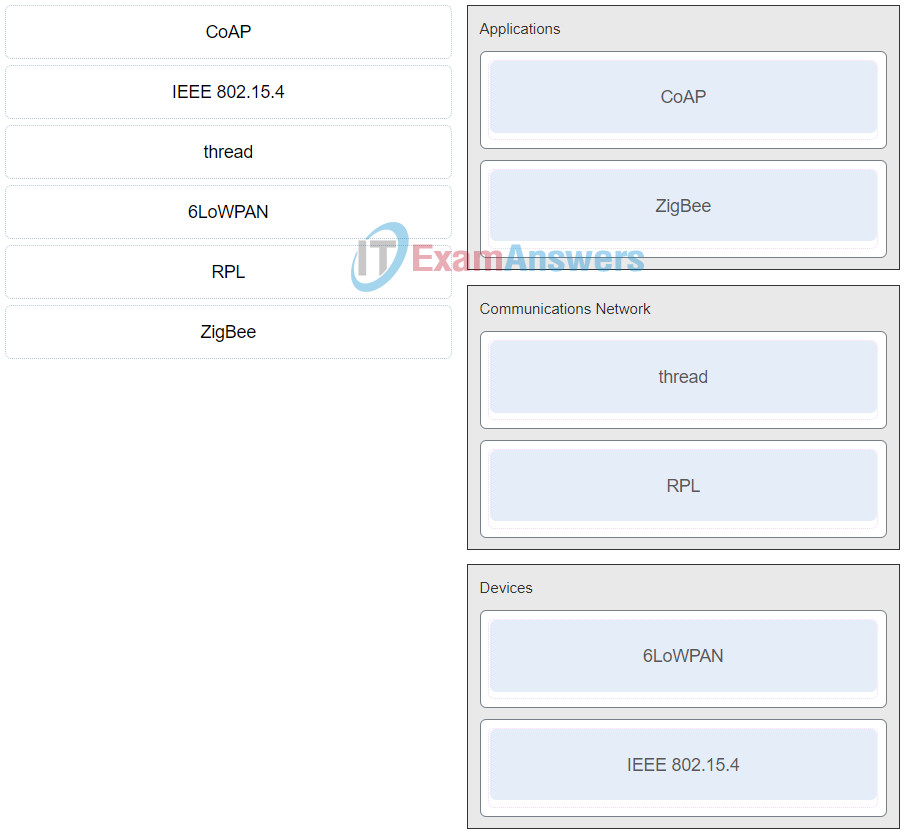
IoT Security (Version 1.0) – IoT Fundamentals: IoT Security Final Exam Q43
17. When creating devices for the home IoT market, what are vendors commonly sacrificing in order to provide simplicity of setup and administration?
- low costs
- advanced features
- security
- device lifespan.
Explanation: The home IoT market is predicted to be very large and many vendors are creating IoT devices that are easy to set up, which will then help increase sales. However, simplicity of setup and administration commonly sacrifices security for both the IoT device and the network it resides on.
18. Which measure should be taken to defeat a brute force attack?
- Only allow a limited number of authentication failures before an account is locked out.
- Only allow passwords to be stored in an encrypted format.
- Only use dictionary words that are greater than 10 characters.
- Only store the hashed equivalent of a password.
Explanation: Brute force attacks can be prevented by allowing a limited number of authentication failures before a specified user account is locked out. This will prevent excessive login attempts against a specific account.
19. Match the security requirement with the appropriate layer of the IoT functional model. (Not all options are used.)
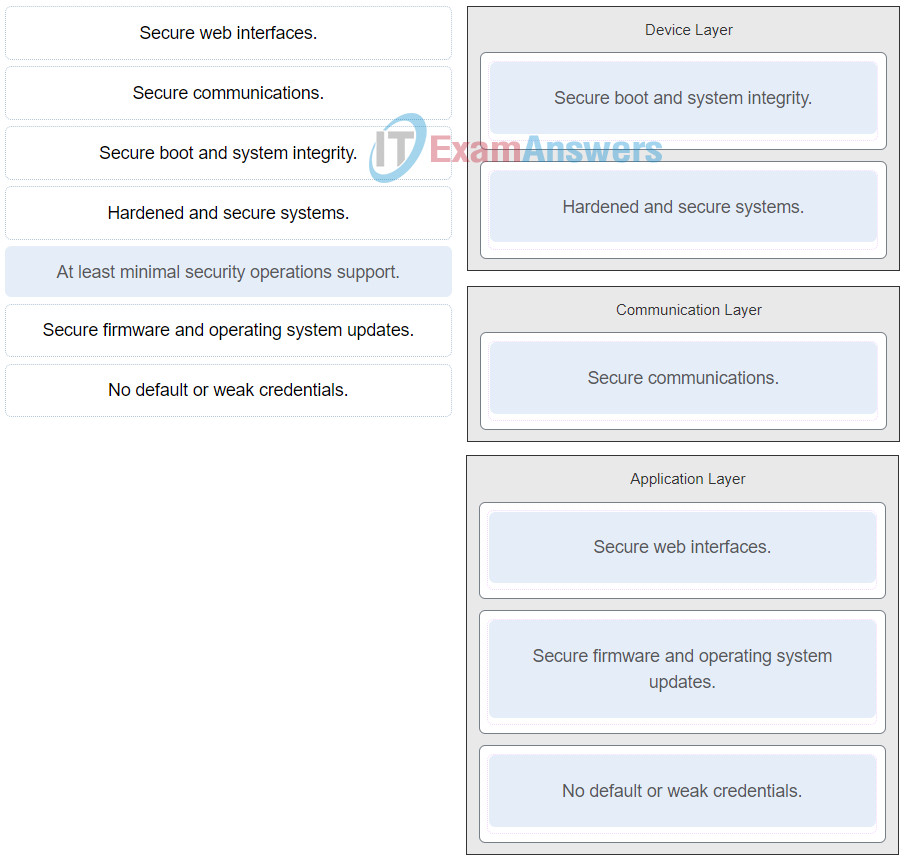
IoT Security (Version 1.0) – IoT Fundamentals: IoT Security Final Exam 29
20. What is the goal of a threat actor when performing a DoS attack?
- to prevent legitimate users from accessing online services
- to gain access to the physical network and hijack a session
- to monitor, capture, and control communications
- to discover subnets and hosts on a network
Explanation: The goal of a DoS attack is to prevent legitimate users from gaining access to network resources, such as websites, email, online accounts, and other services.
21. What are three variables used by DREAD? (Choose three.)
- privacy
- damage
- reputation
- exploitability
- denial of service
- affected users
Explanation: DREAD is an acronym that stands for the variables used to quantify, compare, and prioritize the amount of risk in each threat:
DREAD Risk Rating = ( D amage + R eproducibility + E xploitability + A ffected Users + D iscoverability)/5
22. For the IoT reference model, what are two security measures that should be considered? (Choose two.)
- The data in use on a device should use encryption and be secured.
- The hardware and software of each device connected to the IoT network should be secured.
- The movement of data and communications between each level should be secured.
- The legacy applications used on the IoT network should be removed and secured.
- The authentication method of users at each level should be secured.
Explanation: Security must permeate all the levels in the IoT reference model. Security measures include the following:
Securing the hardware and software of each device or system connected to the IoT network
Providing security for all the processes that occur at each level in the network
Securing the movement of data communications between each level
23. Which CVSS metric group contains metrics set by end users?
- Environmental metric group
- Extended metric group
- Temporal metric group
- Base metric group
Explanation: The metrics inside the Environmental metric group are optionally set by end users. The metrics inside the Base metric group and the Temporal metric group are set by vendors.
24. Which type of address spoofing is typically used in DoS attacks?
- destination IP address spoofing
- MAC address spoofing
- blind IP address spoofing
- non-blind IP address spoofing
Explanation: IP address spoofing attacks occur when a threat actor creates packets with false source IP address information. With blind spoofing, the threat actor cannot see the traffic that is being sent between the host and the target. Blind spoofing is used in DoS attacks.
25. What is the challenge that must be overcome with symmetric key cryptography?
- choosing the encryption algorithm to ensure the secure transfer of the key
- having the sender and receiver agree on the same secret key without anyone intercepting it
- identifying the strength of the symmetric keys for implementation
- selecting a central authority to manage the symmetric key
Explanation: With symmetric key encryption, the problem is getting the sender and receiver to agree on the same secret key without anyone else finding out. Because all keys in a secret-key cryptosystem must remain secret, the challenge has been with providing secure key management
26. What is the intent of a threat actor that is performing a port scan against a targeted device?
- to identify the IP address assigned to the device
- to intercept traffic that is addressed to another host
- to check if certain application protocols are enabled
- to test connectivity to the device
Explanation: Network applications use TCP or UDP ports. Threat actors conduct port scans of target devices to discover which application services are active.
27. A manufacturing organization is generating a large amount of data via their IoT sensors. At which location should the data be processed if it is to be processed close to the ground where the IoT sensors are connected to the network?
Explanation: Data that is processed at the mist layer is processed close to the ground where things are connected to the network.
28. What are three potential vulnerabilities related to attacks toward the memory of an IoT device? (Choose three.)
- privilege escalation
- sensitive data
- clear-text authentication credential
- removal of storage media
- encryption key
- damage
Explanation: Vulnerabilities related to the device memory include sensitive data, clear-text authentication credential, and weak or no encryption. Device damage is related to an IoT device itself. Removal of storage media and privilege escalation relate to the potential vulnerabilities of the interfaces on an IoT device.
29. Which technology type includes industrial control sytems such as SCADA?
- industry technology
- information technology
- operational technology
- consumer technology
Explanation: IoT security includes devices and applications from information technology (IT), operational technology (OT), and consumer technology (CT).
IT – includes devices in the data center, in the cloud, bring your own devices (BYODs), and thousands of sensors and actuators connected in the field
OT – includes industrial control systems (ICSs), supervisory control and data acquisition (SCADA) systems, and all the devices that connect to these systems
CT – includes connected devices in the home, wearable technology, smart cars, and more
30. What are three best practices used to mitigate XSS attacks? (Choose three.)
- SSL encryption
- escaping
- multifactor authentication
- payload encryption
- validating input
- password manager
- sanitizing
Explanation: An XXS attack can be best mitigated by escaping, validating input, and sanitizing. The best way is to use a combination of all three practices by using a mix of code review, static testing, and dynamic testing.
31. In the context of the importance of security in IoT networks, which model provides a common framework for understanding the placement of various standards and protocols in an IoT system?
Explanation: The ETSI model provides a common framework for understanding the placement of various standards and protocols in an IoT system.
32. A user is concerned that the SD card in surveillance cameras could be stolen or destroyed by an attacker. Which security measure can help protect the surveillance cameras?
- tamper proof enclosure
- battery backup for the device
- firewall appliance
- antimalware software
Explanation: Physical device security is important and necessary when IoT devices are installed in locations with public physical access. An enclosure for these devices will help protect them from tampering or damage.
33. Which type of IoT wireless network would use ruggedized network components to interconnect sensors and actuators at dispersed locations in challenging manufacturing environments?
- wireless body-area network
- wireless neighborhood-area network
- wireless home-area network
- wireless field-area network
Explanation: The IoT wireless field-area network would commonly use ruggedized network components to interconnect sensors and actuators at dispersed locations in challenging manufacturing environments.
34. Which two CPU types are based on the Complex Instruction Set Computing architecture? (Choose two.)
- Android
- iOS
- ARM
- AMD
- MIPS
- Intel
Explanation: CPUs from Intel and AMD are based on the Complex Instruction Set Computing architecture. CPUs from ARM and MIPS are based on the Reduced Instruction Set Computing architecture. Android and iOS are operating systems for mobile devices.
35. A network security engineer is reviewing security logs and notices an unauthorized device sending authenticated messages that occurred during a previous M2M session. Which basic security service would protect against this type of incident?
- message confidentiality
- access control
- replay protection
- message integrity
Explanation: There are four basic security services performed at the data link layer:
• Access control – prevents unauthorized devices from joining the network
• Message integrity – protects against alteration of data while it is in transit
• Message confidentiality – prevents threat actors from reading the transmitted data
• Replay protection – prevents threat actors from successfully capturing legitimate messages and sending them out on the network at a later time
36. A threat actor wants to interrupt a normal TCP communication between two hosts by sending a spoofed packet to both endpoints. Which TCP option bit would the threat actor set in the spoofed packet?
Explanation: A TCP reset attack can be used to terminate TCP communications between two hosts by sending a spoofed TCP RST packet. A TCP connection is torn down when it receives an RST bit.
37. When comparing the OSI and IoT reference models, what is the intent of the IoT reference model?
- to foster competition because products from different vendors will work together
- to assist in protocol design so that protocols operating at a specific layer have defined information that they act upon
- to provide common terminology and help clarify how information flows and is processed for a unified IoT industry
- to describe which functions occur at each layer of the model to encourage industry standardization
Explanation: The intent of the IoT reference model is to provide common terminology and help clarify how information flows and is processed for a unified IoT industry.
38. Which two types of IoT firmware vulnerabilities are caused by the use of default or weak login credentials? (Choose two.)
- distributed denial of Service (DDoS)
- back door installation
- out-of-date firmware
- default credentials
- buffer overflow
Explanation: Most general IoT attacks and distributed denial-of-service (DDoS) attacks are made possible via the use of default or weak login credentials.
39. What is one of the most widely exposed vulnerabilities listed by the Open Web Applications Security Project (OWASP)?
- spam
- phishing
- weak passwords
- malware
Explanation: According to the Open Web Applications Security Project (OWASP), the most widely exposed vulnerabilities are these:
Username enumeration – The threat actor is able to find valid usernames through the authentication application.
Weak passwords – Threat actors use default passwords that have not been changed or are able to set account passwords that they choose.
Account lockout – The threat actor finds a way to attempt to authenticate many times after multiple failed attempts.
Lack of multi-factor authentication – It is easier for a threat actor to gain access when only one form of authentication is required.
Insecure 3rd party components – As vulnerabilities are discovered, they often become patched. When components such as Secure Shell (SSH), BusyBox, or web servers are not kept up to date, the threat actor might expose these vulnerabilities and gain access.
40. Which IoT technology commonly benefits from the deployment of a star topology?
- wireless sensor
- home automation
- asset and inventory tracking
- industrial control
Explanation: In a star topology communication is established between devices and a single central controller. This allows each star network to operate independently. Applications that benefit from this topology include home automation, PC peripherals, toys, and games.
41. What are three technologies used by a blockchain? (Choose three.)
- security zones
- T-V pairing
- decentralized ledger
- blocks of hexadecimal digits
- digital signature
- algorithm for reaching consensus
Explanation: A blockchain uses digital signatures for authentication, a decentralized ledger to track the transaction process, an algorithm for reaching consensus to verify a transaction, and each block has a hash of the previous block thus forming a blockchain.
42. A threat actor has intercepted security keys that are used to establish communications. Which popular remote exploit was used by the threat actor?
- eavesdropping attack
- denial-of-service
- username enumeration
- extraction of security parameters
Explanation: Threat actors frequently attempt to access devices over the internet through communication protocols. Some of the most popular remote exploits are as follows:
Man-In-the-middle attack (MITM) – The threat actor gets between devices in the system and intercepts all of the data being transmitted. This information could simply be collected or modified for a specific purpose and delivered to its original destination.
Eavesdropping attack – When devices are being installed, threat actors can intercept data such as security keys that are used by constrained devices to establish communications once they are up and running.
SQL injection (SQLi) – Threat actors use a flaw in the Structured Query Language (SQL) application that allows them to have access to modify the data or gain administrative privileges.
Routing attack – A threat actor could either place a rogue routing device on the network or modify routing packets to manipulate routers to send all packets to the threat actor chosen destination. The threat actor could then drop specific packets, known as selective forwarding, or drop all packets, known as a sinkhole attack.
43. Why do some IoT devices rely on gateways for the internet connection?
- Many IoT devices do not have a network connector
- Many IoT devices use a low powered processor
- Many IoT devices do not support a full TCP/IP stack.
- Many IoT devices have limited memory capacity
Explanation: Because they are constrained devices, many IoT devices do not support a full Transport Control Protocol/Internet Protocol (TCP/IP) stack. These devices rely on gateways, which provide IP transmission services, to send sensor data for processing at remote data analysis and control applications.
44. Why are most IoT devices not directly connected to a Wi-Fi access point or router?
- services constraints
- device and compatibility constraints
- security and encryption constraints
- power and processing constraints
Explanation: Because of power and processing constraints, most IoT devices are not likely to be using Wi-Fi. An IoT gateway will be used to convert traffic to the appropriate Layer 2 encapsulation.
45. Which technology type describes a refrigerator that has become part of a botnet that is attacking businesses?
- consumer technology
- information technology
- industry technology
- operational technology
Explanation: IoT security includes devices and applications from information technology (IT), operational technology (OT), and consumer technology (CT).
IT – includes devices in the data center, in the cloud, bring your own devices (BYODs), and thousands of sensors and actuators connected in the field
OT – includes industrial control systems (ICSs), supervisory control and data acquisition (SCADA) systems, and all the devices that connect to these systems
CT – includes connected devices in the home, wearable technology, smart cars, and more
46. An IoT device uses Busybox. What is the purpose of entering the busybox command in the command line?
- to see the list of available commands
- to enter the interactive mode
- to run a script file named busybox
- to create a script named busybox
Explanation: Busybox uses a Linux kernel, which is loaded when the IoT device boots. When the busybox command is entered at the command prompt, a list of available commands and their usage display.
47. A security researcher has completed a vulnerability assessment and has documented a list of vulnerabilities. When performing a risk assessment, what should these documented items be translated into?
- threats
- risks
- assets
- vulnerabilities
Explanation: In a risk assessment, known vulnerabilities are translated into risks so that they may be prioritized and addressed accordingly.
48. What are two attributes of IoT that make applying traditional security methods challenging? (Choose two.)
- wireless protocols
- decentralized topologies
- device usage
- small device size
- limited device resources
Explanation: The decentralized topology and limited device resources in an IoT system make applying traditional security methods a challenge.
49. Which type of access control model assigns security level labels to information and is typically used in military or mission critical applications?
- nondiscretionary
- mandatory
- discretionary
- attribute-based
Explanation: Mandatory access control (MAC) assigns security level labels to information and enables users with access based on their security level clearance. This is the strictest access control and is typically used in military or mission critical applications.
50. Match the question to one of the three contributors to the determination of risk when performing a risk assessment. (Not all options are used.)
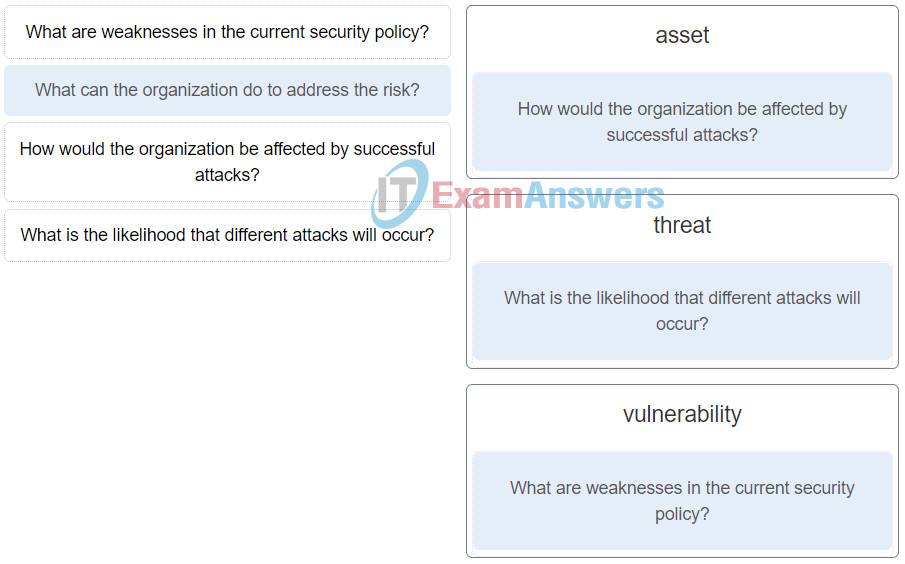
IoT Security (Version 1.0) – IoT Fundamentals: IoT Security Final Exam 22
Explanation: The three factors of vulnerability, threat, and asset contribute to determining the level of risk in risk management. The question “What can the organization do to address the risk?” is about mitigation options available to the organization.





