Refer to the exhibit. The ISAKMP policy for the IKE Phase 1 tunnel was configured, but the tunnel does not yet exist. Which action should be taken next before IKE Phase 1 negotiations can begin?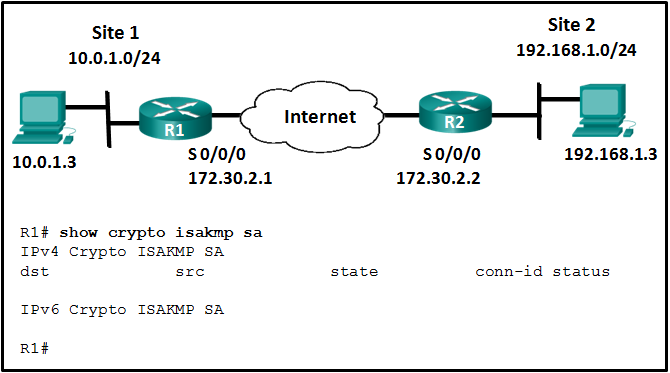
- Configure the set of encryption and hashing algorithms that will be used to transform the data sent through the IPsec tunnel.
- Bind the transform set with the rest of the IPsec policy in a crypto map.
- Configure the IPsec tunnel lifetime.
- Configure an ACL to define interesting traffic.
Explanation: Although the ISAKMP policy for the IKE Phase 1 tunnel is configured, the tunnel does not yet exist as verified with the show crypto isakmp sa command. Interesting traffic must be detected before IKE Phase 1 negotiations can begin. To define interesting traffic, each router has to be configured with an ACL to permit traffic from the local LAN to the remote LAN.
Exam with this question: CCNA Security Practice Final Exam Answers
Exam with this question: Module 19: Quiz – Implement Site-to-Site IPsec VPNs Network Security
Please login or Register to submit your answer
