Select the corresponding delivery method for each characteristic.
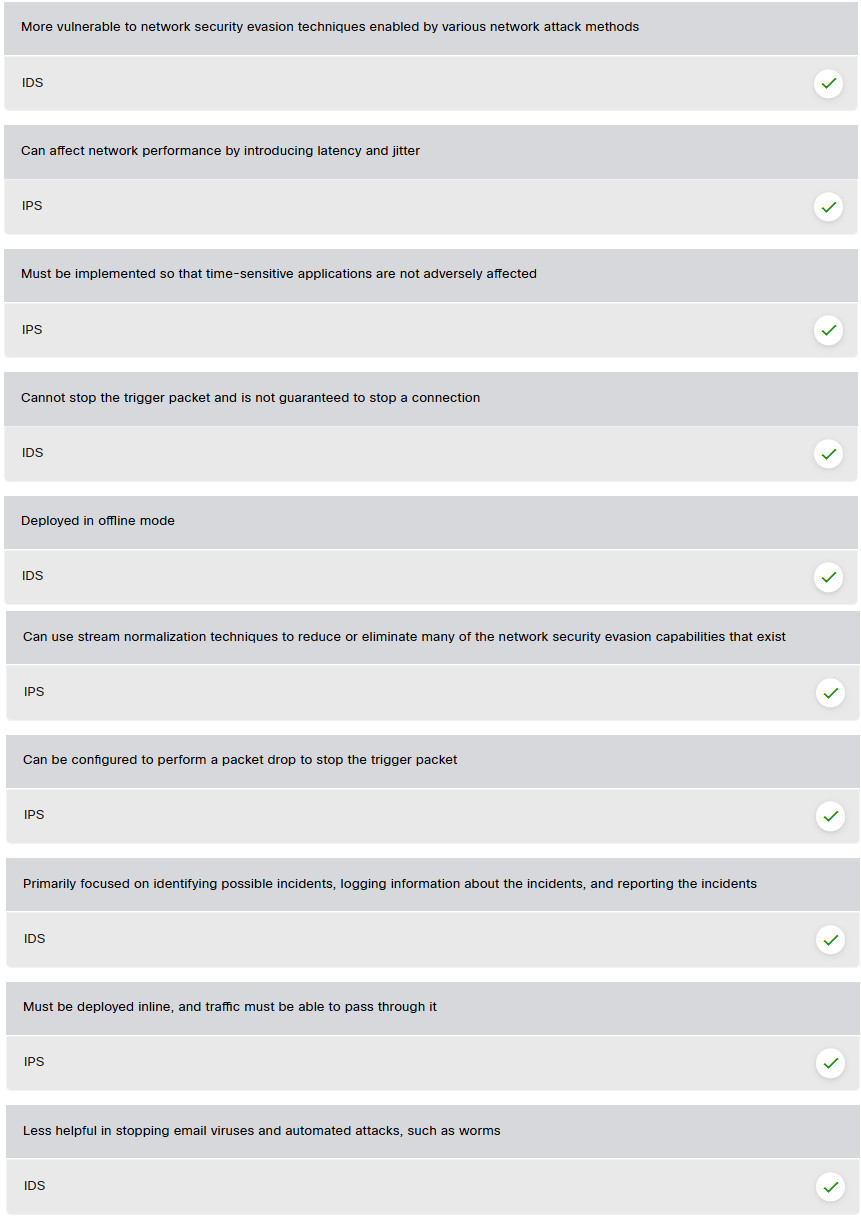
More vulnerable to network security evasion techniques enabled by various network attack methods
- IDS
Can affect network performance by introducing latency and jitter
- IPS
Must be implemented so that time-sensitive applications are not adversely affected
- IPS
Cannot stop the trigger packet and is not guaranteed to stop a connection
- IDS
Deployed in offline mode
- IDS
Can use stream normalization techniques to reduce or eliminate many of the network security evasion capabilities that exist
- IPS
Can be configured to perform a packet drop to stop the trigger packet
- IPS
Primarily focused on identifying possible incidents, logging information about the incidents, and reporting the incidents
- IDS
Must be deployed inline, and traffic must be able to pass through it
- IPS
Less helpful in stopping email viruses and automated attacks, such as worms
- IDS
Exam with this question: 6.1.10 Check Your Understanding - Compare IDS and IPS Characteristics
Please login or Register to submit your answer
