Match the attack type with the respective description.
Explanation: Place the options in the following order:
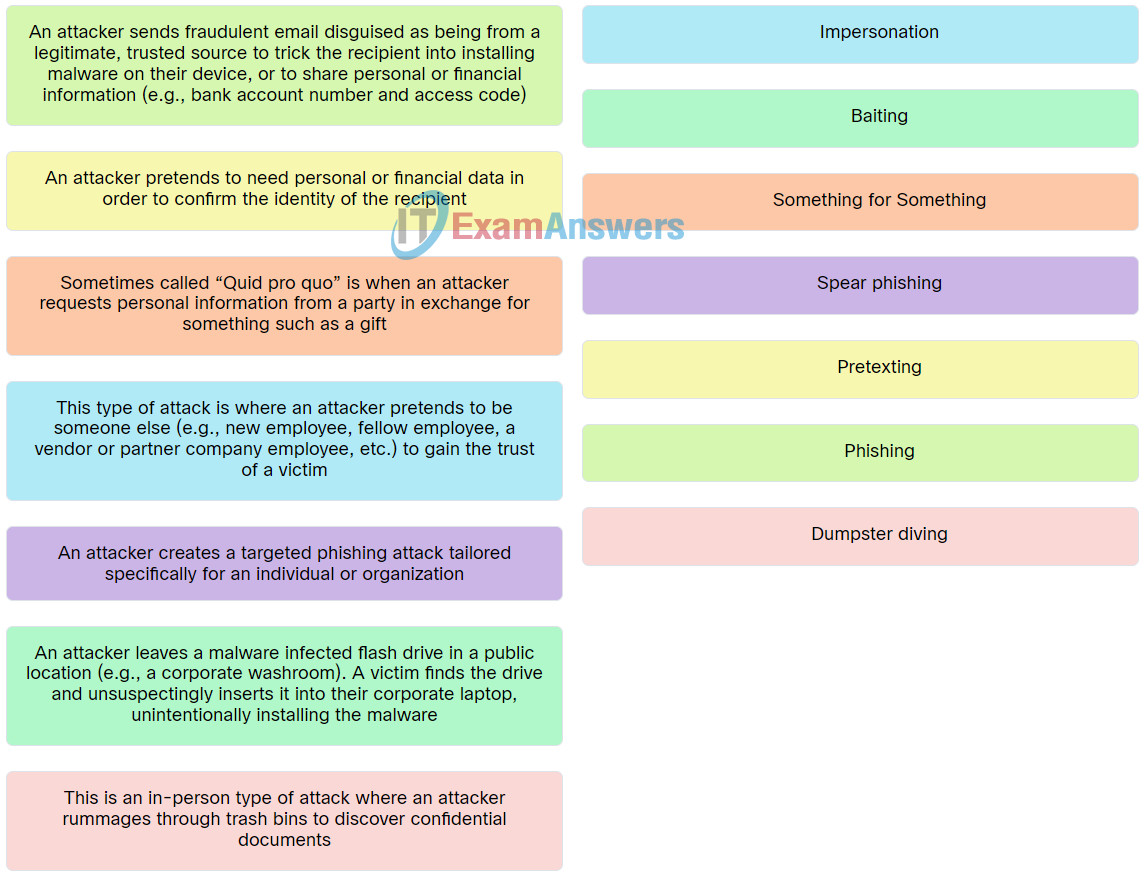
| This is an in-person type of attack where an attacker rummages through trash bins to discover confidential documents. | Dumpster diving |
| This type of attack is where an attacker pretends to be someone else (e.g., new employee, fellow employee, a vendor or partner company employee, etc.) to gain the trust of a victim. | Impersonation |
| An attacker sends fraudulent email disguised as being from a legitimate, trusted source to trick the recipient into installing malware on their device, or to share personal or financial information (e.g., bank account number and access code). | Phishing |
| An attacker creates a targeted phishing attack tailored specifically for an individual or organization. | Spear phishing |
| An attacker leaves a malware infected flash drive in a public location (e.g., a corporate washroom). A victim finds the drive and unsuspectingly inserts it into their corporate laptop, unintentionally installing the malware. | Baiting |
| Sometimes called “Quid pro quo” is when an attacker requests personal information from a party in exchange for something such as a gift. | Something for Something |
| An attacker pretends to need personal or financial data in order to confirm the identity of the recipient. | Pretexting |
Exam with this question: IT Essentials v8 Chapter 13 Check Your Understanding
Please login or Register to submit your answer
