1. Select the mobile malware that best matches the scenario text.
- You just downloaded and installed a free game and suddenly a new “search” toolbar has appeared in your browser. – Adware
- You booted your computer and it is displaying a page that states your files are encrypted and that you must send Bitcoins to decrypt your hard drive. – Ransomware
- A cybercriminal has installed a very hard to detect malware on your computer to gain system-level privileges and can now control it remotely. – Rootkit
- Whenever you access a secure site on your computer, a program is secretly capturing the login credentials and sending them to a cybercriminal. – Spyware
- After visiting a free gaming site, your computer displayed a pop-up window saying it discovered several viruses and to fix it you must download and run the free antivirus software. You download and scan your computer and it reports that all viruses have been removed. However, the free antivirus software installed a backdoor application allowing a cybercriminal access to your host. – Trojan horse
- You opened an email attachment and suddenly your computer shut down. You try to reboot it but it keeps shutting down. – Virus
- The corporate network is suddenly very noticeably slow and unresponsive. – Worm
2. Match the malware to the respective description.

Explanation: Place the options in the following order:
| Malicious software that executes a specific, unwanted, and often harmful function on a computer. |
Virus |
| Malware that executes arbitrary code and installs copies of itself in the memory of the infected computer. The main purpose of this malware is to automatically replicate from system to system across the network. |
Worm |
| Non-self-replicating type of malware. It often contains malicious code that is designed to look like something else, such as a legitimate application or file. It attacks the device from within. |
Trojan Horse |
| Malware used to gather information about a user, and, without the user’s consent, sends the information to another entity. |
Spyware |
| Malware that typically displays annoying pop-ups to generate revenue for its author. |
Adware |
| Malware that attempts to convince people to divulge sensitive information. |
Phishing |
| Malware that includes scam software that uses social engineering to shock, cause anxiety, or cause the perception of a threat. It is generally directed at an unsuspecting user. |
Scareware |
| Malware that is installed on a compromised system and provides privileged access to the hacker. |
Rootkit |
| Malware that denies access to the infected computer system and demands a person be paid in order for the restriction to be removed. |
Ransomware |
3. Match the term with the respective description.
Explanation: Place the options in the following order:
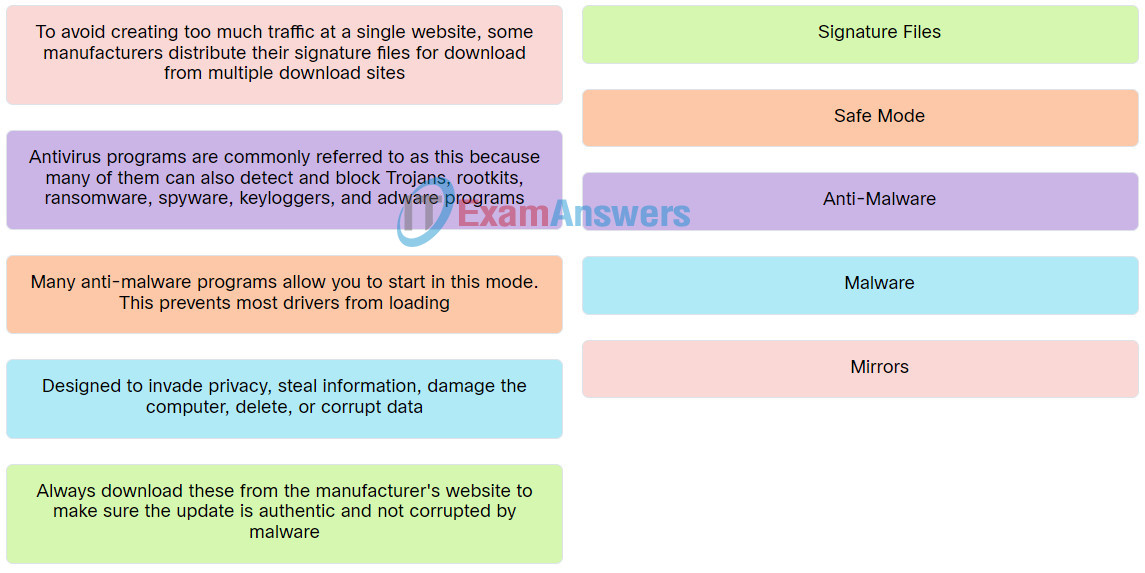
| To avoid creating too much traffic at a single website, some manufacturers distribute their signature files for download from multiple download sites. |
Mirrors |
| Designed to invade privacy, steal information, damage the computer, delete, or corrupt data. |
Malware |
| Always download these from the manufacturer’s website to make sure the update is authentic and not corrupted by malware. |
Signature Files |
| Antivirus programs are commonly referred to as this because many of them can also detect and block Trojans, rootkits, ransomware, spyware, keyloggers, and adware programs. |
Anti-Malware |
| Many anti-malware programs allow you to start in this mode. This prevents most drivers from loading. |
Safe Mode |
4. Match TCP/IP attack type to the respective description.
Explanation: Place the options in the following order:
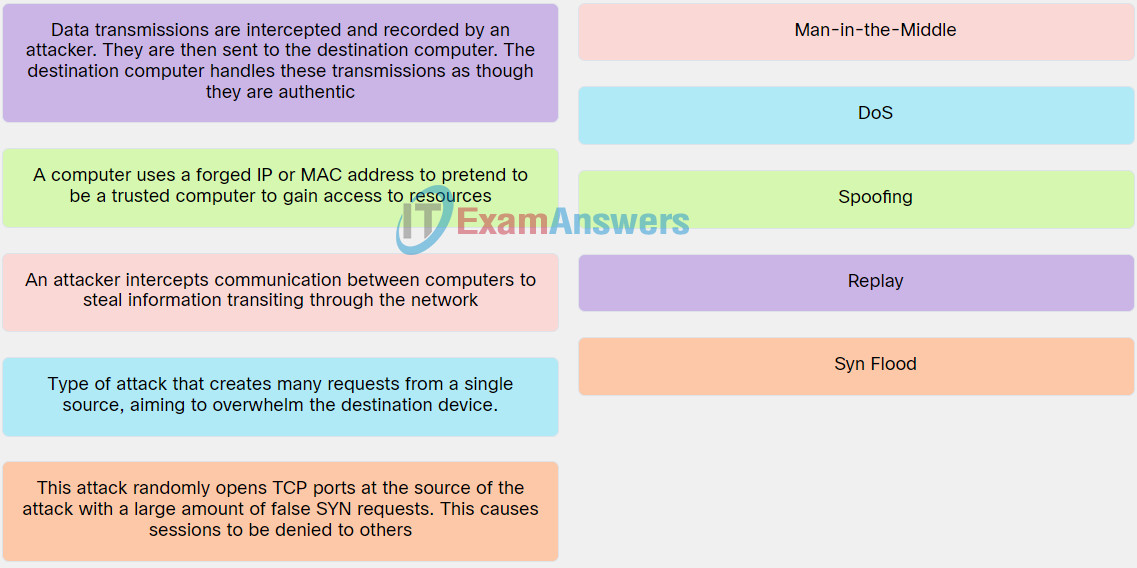
| An attacker intercepts communication between computers to steal information transiting through the network. |
Man-in-the-Middle |
| Type of attack that creates many requests from a single source, aiming to overwhelm the destination device. |
DoS |
| A computer uses a forged IP or MAC address to pretend to be a trusted computer to gain access to resources. |
Spoofing |
| Data transmissions are intercepted and recorded by an attacker. They are then sent to the destination computer. The destination computer handles these transmissions as though they are authentic. |
Replay |
| This attack randomly opens TCP ports at the source of the attack with a large amount of false SYN requests. This causes sessions to be denied to others. |
Syn Flood |
5. Select the social engineering technique that best matches the scenario text.
- You found a USB drive in the parking lot and inserted it into your laptop unknowingly installing malware on your computer. – Baiting
- An attacker has just retrieved hard copies of recently outdated device configuration files from a trash bin. – Dumpster diving
- A person claiming to be from your heating and ventilation contractor asks you if you could let him into a secure area. – Impersonation
- You received an email from your bank stating that your account has been compromised and that you should click an enclosed link to rectify the problem. When you click, you unknowingly just installed malware on your device. – Phishing
- Your “bank” calls you to say your account may be compromised and they would like to confirm your identity by requesting your personal and financial data. – Pretexting
- You notice a fellow employee purposely overlooking your supervisor’s shoulder as they are entering their login credentials. – Shoulder surfing
- You received a survey in an email for a cool free t-shirt in which you have to provide personal identifiable information. – Something for Something
- An attacker sends malicious emails containing harmful links, malware, or deceptive content to a large number of random individuals. – Spam
- An attacker has created a targeted phishing attack tailored specifically for the chief executive officer of a large organization. – Spear phishing
- A person you have never seen before has quickly followed you into a secure building entrance saying that he forgot his security badge. – Tailgating
6. Match the attack type with the respective description.
Explanation: Place the options in the following order:
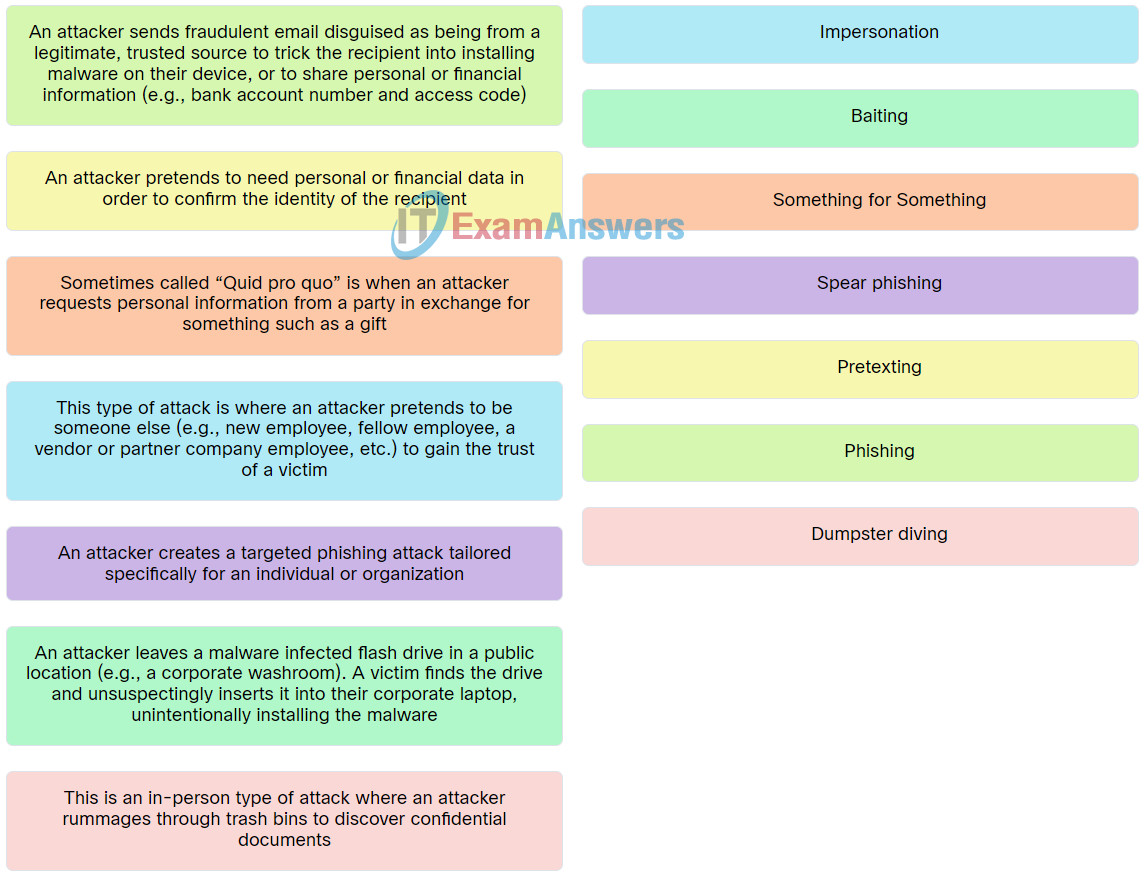
| This is an in-person type of attack where an attacker rummages through trash bins to discover confidential documents. |
Dumpster diving |
| This type of attack is where an attacker pretends to be someone else (e.g., new employee, fellow employee, a vendor or partner company employee, etc.) to gain the trust of a victim. |
Impersonation |
| An attacker sends fraudulent email disguised as being from a legitimate, trusted source to trick the recipient into installing malware on their device, or to share personal or financial information (e.g., bank account number and access code). |
Phishing |
| An attacker creates a targeted phishing attack tailored specifically for an individual or organization. |
Spear phishing |
| An attacker leaves a malware infected flash drive in a public location (e.g., a corporate washroom). A victim finds the drive and unsuspectingly inserts it into their corporate laptop, unintentionally installing the malware. |
Baiting |
| Sometimes called “Quid pro quo” is when an attacker requests personal information from a party in exchange for something such as a gift. |
Something for Something |
| An attacker pretends to need personal or financial data in order to confirm the identity of the recipient. |
Pretexting |
7. Match the locking mechanism term to the respective description.
Explanation: Place the options in the following order:
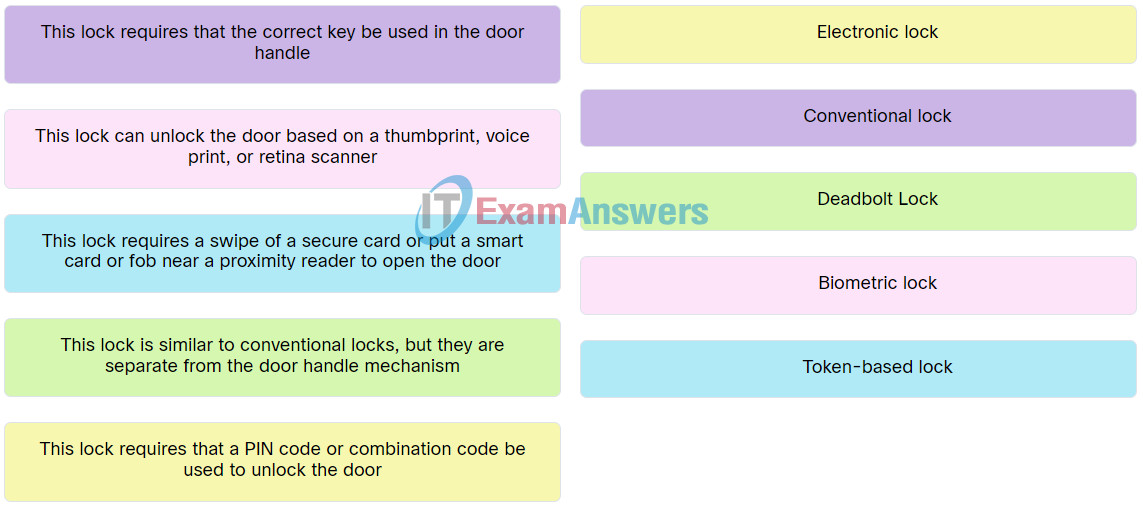
| This lock requires that a PIN code or combination code be used to unlock the door. |
Electronic lock |
| This lock requires a swipe of a secure card or put a smart card or fob near a proximity reader to open the door. |
Token-based lock |
| This lock is similar to conventional locks, but they are separate from the door handle mechanism. |
Deadbolt Lock |
| This lock requires that the correct key be used in the door handle. |
Conventional lock |
| This lock can unlock the door based on a thumbprint, voice print, or retina scanner. |
Biometric lock |
8. Match the data protection term to the respective description.
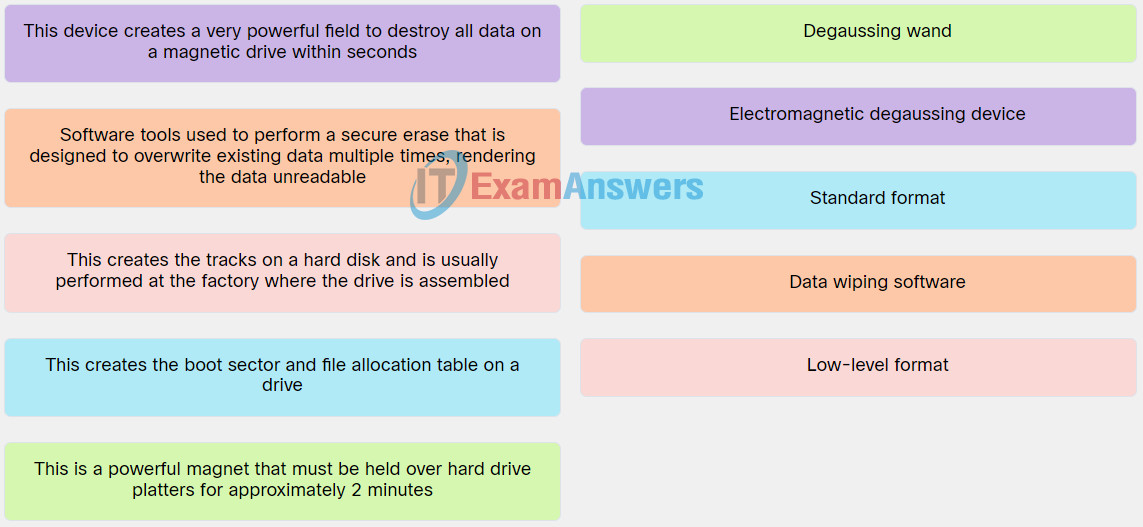
Explanation: Place the options in the following order:
| This creates the tracks on a hard disk and is usually performed at the factory where the drive is assembled. |
Low-level format |
| This creates the boot sector and file allocation table on a drive. |
Standard format |
| This is a powerful magnet that must be held over hard drive platters for approximately 2 minutes. |
Degaussing wand |
| This device creates a very powerful field to destroy all data on a magnetic drive within seconds. |
Electromagnetic degaussing device |
| Software tools used to perform a secure erase that is designed to overwrite existing data multiple times, rendering the data unreadable. |
Data wiping software |
9. Match the statement with True or False category.
- Setting a BIOS or UEFI password can prevent someone from altering the configured settings – True
- Dynamic lock is a feature that makes Windows lock when a pre-paired device such as a cell phone goes out of range of the PC – True
- The PIN feature enables Windows to use facial recognition or use your fingerprint to access Windows – False
- Local passwords can be managed under Control Panel > Personalization – False
Explanation: true because:
- Setting a BIOS or UEFI password can prevent someone from booting the computer. It also prevents someone from altering the configured settings.
- Windows 10 has Windows Hello, PIN, and Picture password as options to secure the workstation. In addition, the Dynamic lock feature makes Windows lock when a pre-paired device such as a cell phone goes out of range of the PC.
The following are false because:
- Windows Hello is a feature that enables Window to use facial recognition or use your fingerprint to access Windows.
- Local passwords are managed under Control Panel > User Accounts.
10. Match the Local Security Policy related statement to the respective true of false category.
Use Account Policies > Password Policy to prevent brute force attacks.
True
The Local Security Policy can export an extensive configured local policy from one Windows host to another.
True
Use the Local Policies > Audit Policy to log successful and unsuccessful login attempt.
True
Explanation: true because:
- The Local Security Policy can be exported and copied to other Windows hosts by using the Action > Export List… feature, saving the policy, and then importing it the Local Security Policy file of other Windows hosts.
- The Local Policies > Audit Policy > Audit account login events can be enabled for all logon events.
The following is false because:
- The Account Policies > Account Lockout Policy is used to prevent brute-force attacks. The Account Policies > Password Policy is used to enforce password requirements.
11. Match the Windows 10 OS term with the respective description.
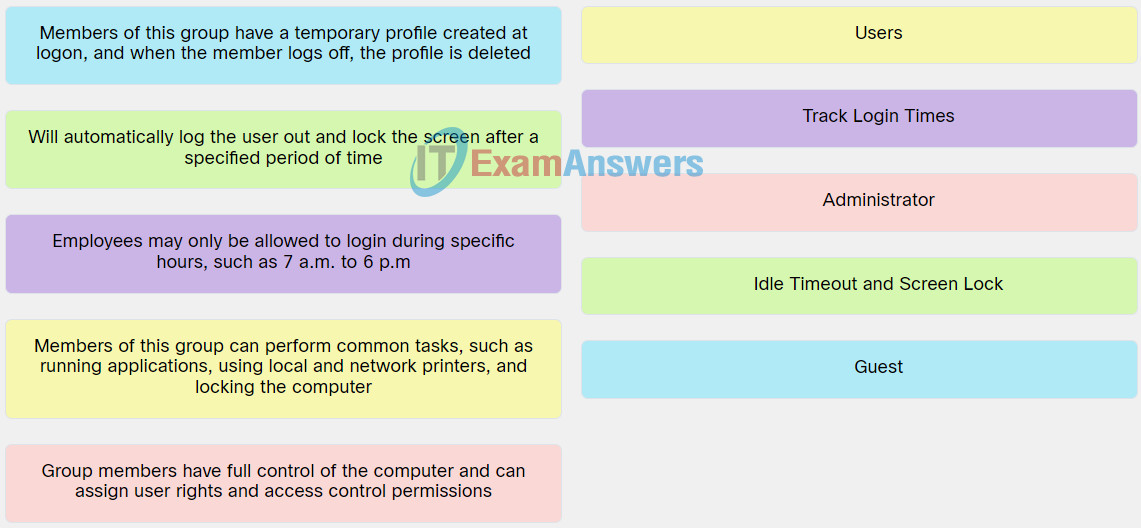
Explanation: Place the options in the following order:
| Group members have full control of the computer and can assign user rights and access control permissions. |
Administrator |
| Members of this group have a temporary profile created at logon, and when the member logs off, the profile is deleted. |
Guest |
| Will automatically log the user out and lock the screen after a specified period of time. |
Idle Timeout and Screen Lock |
| Employees may only be allowed to login during specific hours, such as 7 a.m. to 6 p.m. |
Track Login Times |
| Members of this group can perform common tasks, such as running applications, using local and network printers, and locking the computer. |
Users |
12. Match the term with the respective description.
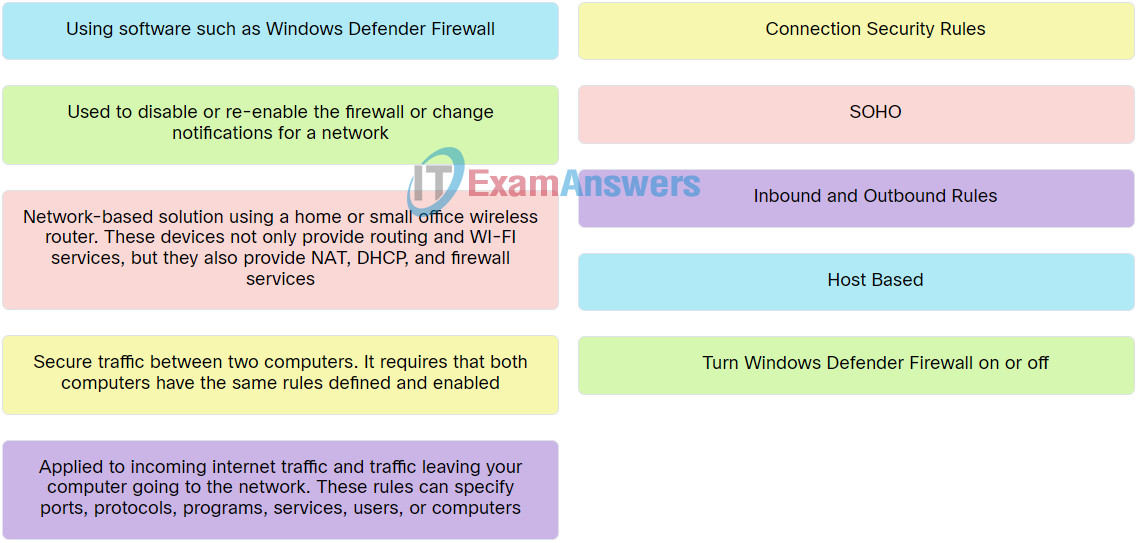
Explanation: Place the options in the following order:
| Network-based solution using a home or small office wireless router. These devices not only provide routing and WI-FI services, but they also provide NAT, DHCP, and firewall services. |
SOHO |
| Using software such as Windows Defender Firewall. |
Host Based |
| Used to disable or re-enable the firewall or change notifications for a network. |
Turn Windows Defender Firewall on or off |
| Applied to incoming internet traffic and traffic leaving your computer going to the network. These rules can specify ports, protocols, programs, services, users, or computers. |
Inbound and Outbound Rules |
| Secure traffic between two computers. It requires that both computers have the same rules defined and enabled. |
Connection Security Rules |
13. Match the term to the respective description.
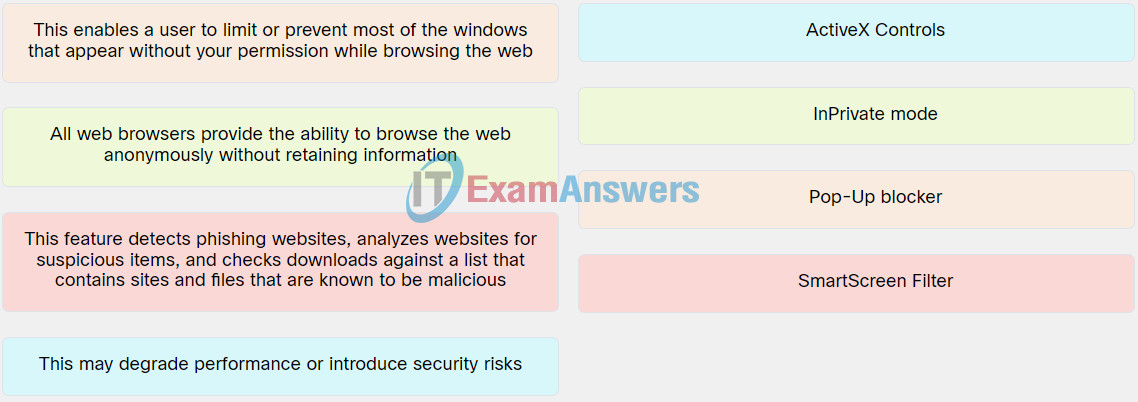
Explanation: Place the options in the following order:
| All web browsers provide the ability to browse the web anonymously without retaining information. |
InPrivate mode |
| This enables a user to limit or prevent most of the windows that appear without your permission while browsing the web. |
Pop-Up blocker |
| This feature detects phishing websites, analyzes websites for suspicious items, and checks downloads against a list that contains sites and files that are known to be malicious. |
SmartScreen Filter |
| This may degrade performance or introduce security risks. |
ActiveX Controls |
14. Match the Windows 10 OS term with the respective description.
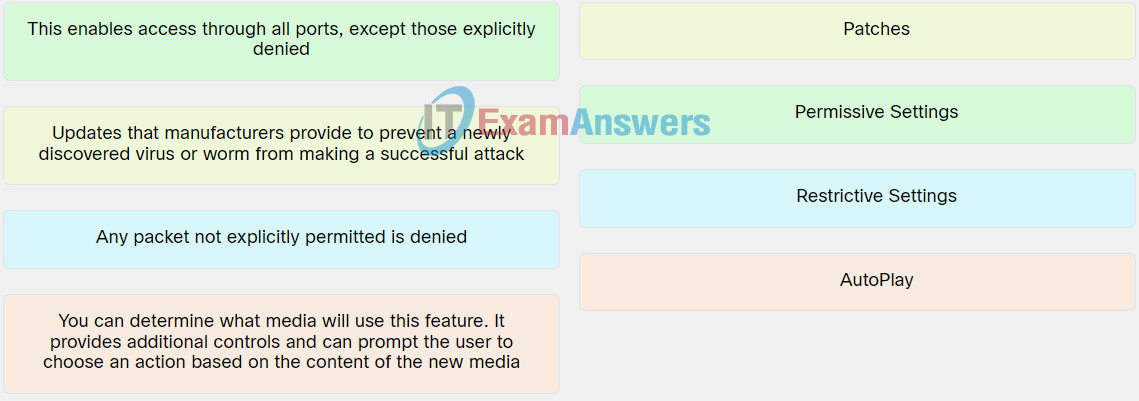
Explanation: Place the options in the following order:
| Updates that manufacturers provide to prevent a newly discovered virus or worm from making a successful attack. |
Patches |
| You can determine what media will use this feature. It provides additional controls and can prompt the user to choose an action based on the content of the new media. |
AautoPlay |
| This enables access through all ports, except those explicitly denied. |
Rrmissive Settings |
| Any packet not explicitly permitted is denied. |
Restrictive Settings |
15. Select the network security term that best matches the scenario text.
- In a local restaurant, you notice a sign that says “Free WiFi”. Looking at your phone, you see a network called “ForOurGuests”. – SSID
- You notice a wireless network named StaffOnly with a lock symbol on it. When you try to connect, a password prompt appears. – WPA
- A cybercriminal has requested port forwarding targeting your internal network printer. – UPnP
- An email from your wireless router manufacturer warns of a vulnerability and recommends that you update the device. – Firmware
- After learning about remote vulnerabilities, you decide to install a device that carefully monitors and filters network traffic. – Firewall










