Match the attack type with the respective description.
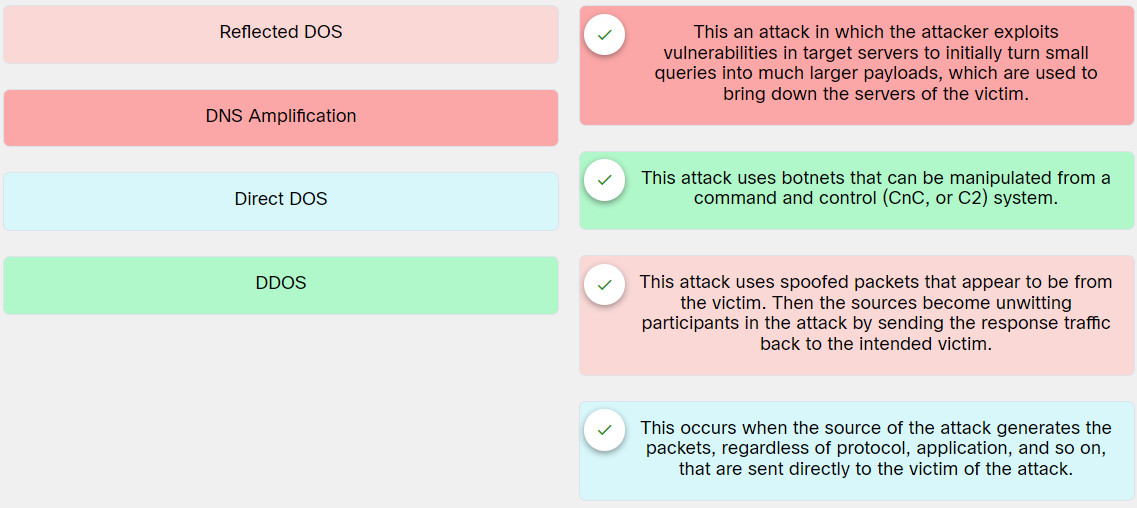
Explanation: Place the options in the following order:
| Reflected DOS | This attack uses spoofed packets that appear to be from the victim. Then the sources become unwitting participants in the attack by sending the response traffic back to the intended victim. |
| DNS Amplification | This an attack in which the attacker exploits vulnerabilities in target servers to initially turn small queries into much larger payloads, which are used to bring down the servers of the victim. |
| Direct DOS | This occurs when the source of the attack generates the packets, regardless of protocol, application, and so on, that are sent directly to the victim of the attack. |
| DDOS | This attack uses botnets that can be manipulated from a command and control (CnC, or C2) system. |
Exam with this question: 5.3.3 Quiz - Exploiting Wired and Wireless Networks Answers
Please login or Register to submit your answer
