Match the attack type with the respective description.
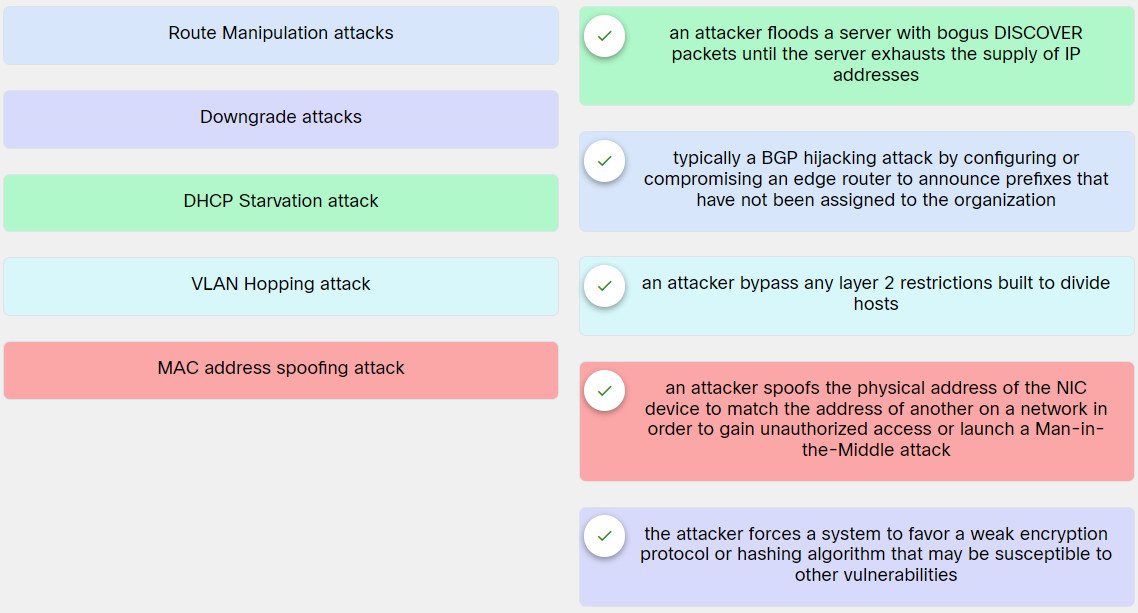
[alert-success]Explanation: Place the options in the following order:
| Route Manipulation attacks | typically a BGP hijacking attack by configuring or compromising an edge router to announce prefixes that have not been assigned to the organization |
| Downgrade attacks | the attacker forces a system to favor a weak encryption protocol or hashing algorithm that may be susceptible to other vulnerabilities |
| DHCP Starvation attack | an attacker floods a server with bogus DISCOVER packets until the server exhausts the supply of IP addresses |
| VLAN Hopping attack | an attacker bypass any layer 2 restrictions built to divide hosts |
| MAC address spoofing attack | an attacker spoofs the physical address of the NIC device to match the address of another on a network in order to gain unauthorized access or launch a Man-in-the-Middle attack |
Exam with this question: 5.3.3 Quiz - Exploiting Wired and Wireless Networks Answers
Please login or Register to submit your answer
