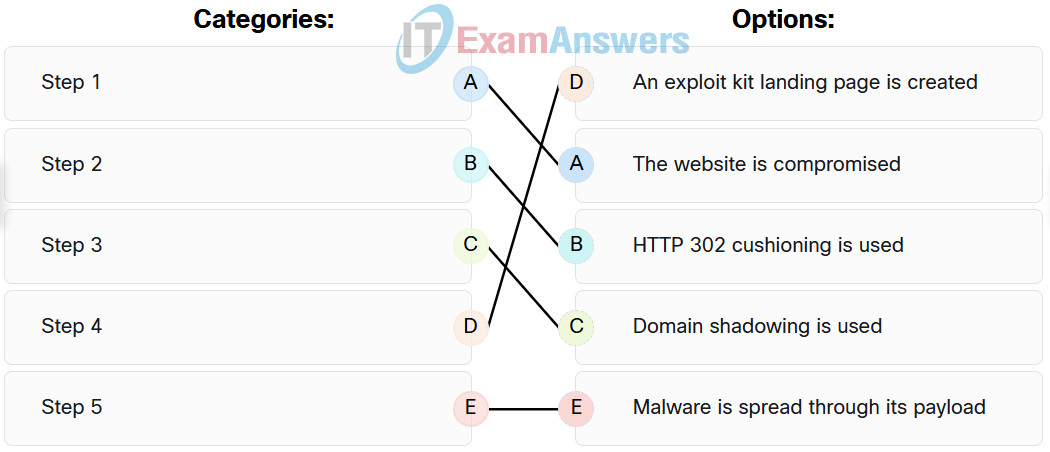
Match the correct sequence of steps typically taken by a threat actor carrying out a domain shadowing attack.
Exam with this question: CyberOps Associate Final Exam Answers
Exam with this question: Endpoint Security (ESec) Final Exam Answers (Course Final)
Exam with this question: Endpoint Security: My Knowledge Check Answers
Please login or Register to submit your answer
