Endpoint Security: My Knowledge Check Answers
How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
1. Which Windows version was the first to introduce a 64-bit Windows operating system?
- Windows NT
- Windows XP
- Windows 7
- Windows 10
Explanation: There are more than 20 releases and versions of the Windows operating system. The Windows XP release introduced 64-bit processing to Windows computing.
2. Employees in an organization report that the network access is slow. Further investigation reveals that one employee downloaded a third-party scanning program for the printer. What type of malware may have been introduced?
- Worm
- Trojan horse
- Spam
- Phishing
Explanation: Worms are malicious code that replicates by independently exploiting vulnerabilities in networks. Worms usually slow down networks. Whereas a virus requires a host program to run, worms can run by themselves. Other than the initial infection, worms no longer require user participation. After a worm affects a host, it is able to spread very quickly over the network. Worms share similar patterns. They all have an enabling vulnerability, a way to propagate themselves, and they all contain a payload.
3. Which two options are window managers for Linux? (Choose two.)
- File Explorer
- Gnome
- Kali
- KDE
- PenTesting
Explanation: The X Window System provides the basic framework for a GUI, but the GUI itself varies greatly between different distributions. Two window managers are Gnome and KDE.
4. On a Windows host, which tool can be used to create and maintain blacklists and whitelists?
- Task Manager
- Group Policy Editor
- Computer Management
- Local Users and Groups
Explanation: In Windows, blacklisting and whitelisting settings can be managed through the Group Policy Editor.
5. Users in a company have complained about network performance. After investigation, the IT staff has determined that an attacker has used a specific technique that affects the TCP three-way handshake. What is the name of this type of network attack?
- SYN flood
- DDoS
- DNS poisoning
- session hijacking
Explanation: The TCP SYN flood attack exploits the TCP three-way handshake. The threat actor continually sends TCP SYN session request packets with a randomly spoofed source IP address to an intended target.
6. Which parameter is commonly used to identify a wireless network name when a home wireless AP is being configured?
Explanation: The SSID is used to name a wireless network. This parameter is required in order for a wireless client to attach to a wireless AP.
7. What would be the target of an SQL injection attack?
Explanation: SQL is the language used to query a relational database. Cybercriminals use SQL injections to get information, create fake or malicious queries, or to breach the database in some other way.
8. Which of the following are foundational principles of the cybersecurity domain? (Choose three.)
- Security
- Integrity
- Policy
- Encryption
- Availability
- Confidentiality
Explanation: There are three foundational principles of security. These are confidentiality, integrity, and availability. Together these three principles make up the security triad.
9. A social media site is describing a security breach in a sensitive branch of a national bank. In the post, it refers to a vulnerability. What statement describes that term?
- The potential damage to the organization that is caused by the threat.
- The actions that are taken to protect assets by mitigating a threat or reducing risk.
- The likelihood that a particular threat will exploit a vulnerability of an asset and result in an undesirable consequence.
- A weakness in a system or its design that could be exploited by a threat.
Explanation: Review terms and descriptions from module 2.
10. Why is Kali Linux a popular choice in testing the network security of an organization?
- It is an open source Linux security distribution containing many penetration tools.
- It can be used to intercept and log network traffic.
- It can be used to test weaknesses by using only malicious software.
- It is a network scanning tool that prioritizes security risks.
Explanation: Kali is an open source Linux security distribution that is commonly used by IT professionals to test the security of networks.
11. What type of attack targets an SQL database using the input field of a user?
- XML injection
- Cross-site scripting
- SQL injection
- buffer overflow
Explanation: A criminal can insert a malicious SQL statement in an entry field on a website where the system does not filter the user input correctly.
12. A security specialist is asked for advice on a security measure to prevent unauthorized hosts from accessing the home network of employees. Which measure would be most effective?
- Implement intrusion detection systems.
- Implement a firewall.
- Implement a VLAN.
- Implement RAID.
Explanation: Protecting data confidentiality requires an understanding of the technologies used to protect data in all three data states.
13. Refer to the exhibit. An IT security manager is planning security updates on this particular network. Which type of network is displayed in the exhibit and is being considered for updates?
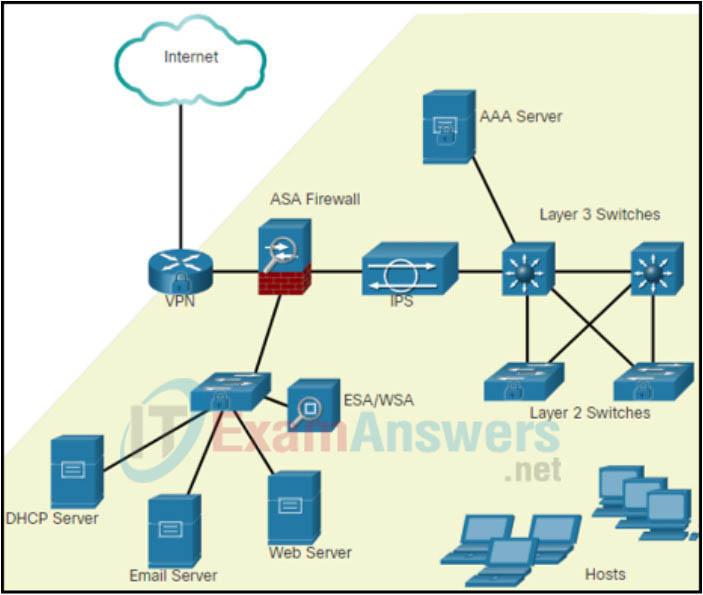
Explanation: A distinguishing factor of campus area networks (CANs) are that they have interconnected LANs.
14. Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.)
- nslookup cisco.com
- net cisco.com
- ping cisco.com
- nbtstat cisco.com
- ipconfig /flushdns
Explanation: The ping command tests the connection between two hosts. When ping uses a host domain name to test the connection, the resolver on the PC will first perform the name resolution to query the DNS server for the IP address of the host. If the ping command is unable to resolve the domain name to an IP address, an error will result.
Nslookup is a tool for testing and troubleshooting DNS servers.
15. What are three benefits of using symbolic links over hard links in Linux? (Choose three.)
- Symbolic links can be exported.
- They can be encrypted.
- They can be compressed.
- They can link to a directory.
- They can show the location of the original file.
- They can link to a file in a different file system.
Explanation: In Linux, a hard link is another file that points to the same location as the original file. A soft link (also called a symbolic link or a symlink) is a link to another file system name. Hard links are limited to the file system in which they are created and they cannot link to a directory; soft links are not limited to the same file system and they can link to a directory. To see the location of the original file for a symbolic link use the ls –l command.
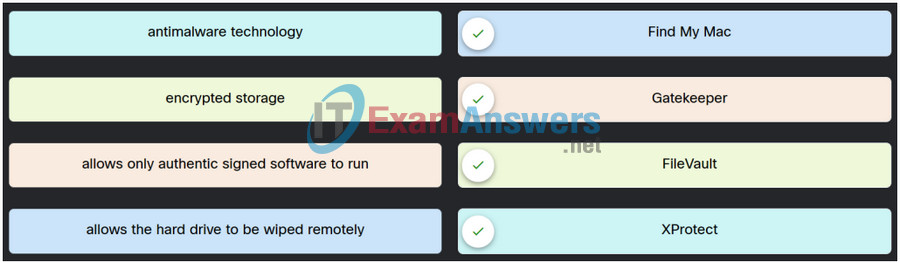
16. Match the Apple system security feature to its purpose.
17. A cyber criminal sends a series of maliciously formatted packets to the database server. The server cannot parse the packets and the event causes the server to crash. What is the type of attack the cyber criminal launches?
- packet Injection
- SQL injection
- DoS
- man-in-the-middle
Explanation: A cybersecurity specialist needs to be familiar with the characteristics of the different types of malware and attacks that threaten an organization.
18. Which field in the IPv4 header is used to prevent a packet from traversing a network endlessly?
- Time-to-Live
- Sequence Number
- Acknowledgment Number
- Differentiated Services
Explanation: The value of the Time-to-Live (TTL) field in the IPv4 header is used to limit the lifetime of a packet. The sending host sets the initial TTL value; which is decreased by one each time the packet is processed by a router. If the TTL field decrements to zero, the router discards the packet and sends an Internet Control Message Protocol (ICMP) Time Exceeded message to the source IP address. The Differentiated Services (DS) field is used to determine the priority of each packet. Sequence Number and Acknowledgment Number are two fields in the TCP header.
19. What is required in order to connect a Wi-Fi enabled laptop to a WPA secured wireless network?
- a security encryption key
- a MAC address
- a username and password
- an updated wireless driver
Explanation: Regardless of the levels of security configured on a WLAN, a WPA secured WLAN always requires the use of an encryption key. Without the proper key, a device cannot connect to the network.
20. Which network service allows administrators to monitor and manage network devices?
Explanation: SNMP is an application layer protocol that allows administrators to manage and monitor devices on the network such as routers, switches, and servers.
21. When considering network security, what is the most valuable asset of an organization?
- customers
- data
- financial resources
- personnel
Explanation: Data, such as research and development data, sales data, financial data, human resource and legal data, employee data, contractor data, and customer data, is likely to be the most valuable asset for an organization.
22. What is the primary means for mitigating virus and Trojan horse attacks?
- antivirus software
- encryption
- antisniffer software
- blocking ICMP echo and echo-replies
Explanation: Antivirus software is the primary means of mitigating both virus and Trojan horse attacks. By using up-to-date antivirus software, the spread of viruses and Trojan horse attacks can be reduced.
23. Which language is used to query a relational database?
Explanation: Cybercriminals use SQL injections to breach a relational database, create malicious SQL queries, and obtain sensitive data.
24. What does the term vulnerability mean?
- a weakness that makes a target susceptible to an attack
- a computer that contains sensitive information
- a method of attack to exploit a target
- a known target or victim machine
- a potential threat that a hacker creates
Explanation: A vulnerability is not a threat, but it is a weakness that makes the PC or the software a target for attacks.
25. What is an IPS signature?
- It is the timestamp that is applied to logged security events and alarms.
- It is the authorization that is required to implement a security policy.
- It is a set of rules used to detect typical intrusive activity.
- It is a security script that is used to detect unknown threats.
Explanation: An IPS signature uniquely identifies specific malware, protocol anomalies, or malicious traffic. IPS sensors are tuned to look for matching signatures or abnormal traffic patterns. IPS signatures are conceptually similar to the virus.dat file used by virus scanners.
26. Why would a rootkit be used by a hacker?
- to do reconnaissance
- to try to guess a password
- to gain access to a device without being detected
- to reverse engineer binary files
Explanation: Hackers use rootkits to avoid detection as well as hide any software installed by the hacker.
27. Which Windows tool can be used by a cybersecurity administrator to secure stand-alone computers that are not part of an active directory domain?
- Local Security Policy
- Windows Defender
- Windows Firewall
- PowerShell
Explanation: Windows systems that are not part of an Active Directory Domain can use the Windows Local Security Policy to enforce security settings on each stand-alone system.
28. Which file system is the primary file system used by Apple in current Macintosh computers?
Explanation: To use Force Quit, right-click on the application icon that is not responding from the Dock and close the application.
29. Which device in a LAN infrastructure is susceptible to MAC address-table overflow and spoofing attacks?
- server
- switch
- workstation
- firewall
Explanation: Switches are LAN infrastructure devices interconnecting endpoints. They are susceptible to LAN-related attacks including MAC address-table overflow attacks, spoofing attacks, LAN storm attacks, STP manipulation attacks, and VLAN attacks.
30. At a local college, students are allowed to connect to the wireless network without using a password. Which mode is the access point using?
- network
- open
- passive
- shared-key
Explanation: Network mode is not an authentication mode, it refers to WLAN standards for 802.11a/b/g/n/ac/ad and the ability for access points to operate in mixed mode to support different standards, but it is not an authentication mode. Open authentication is a null authentication mode because wireless connectivity is granted to any wireless device. This authentication is used where security is not a concern. Passive mode is not an authentication mode, it refers to the open advertisement of the SSID, standards, and security settings by an access point. Shared-key authentication uses a pre-shared key between the client and the access point.
31. What is the term used when a malicious party sends a fraudulent email disguised as being from a legitimate, trusted source?
- phishing
- vishing
- backdoor
- trojan
Explanation: Phishing is used by malicious parties who create fraudulent messages that attempt to trick a user into either sharing sensitive information or installing malware.
32. Which term describes a field in the IPv4 packet header used to detect corruption in the IPv4 header?
- header checksum
- version
- destination IPv4 address
- protocol
Explanation: The header checksum is used to determine if any errors have been introduced during transmission.
33. What is a nontechnical method that a cybercriminal would use to gather sensitive information from an organization?
- man-in-the-middle
- ransomeware
- social engineering
- pharming
Explanation: A cybersecurity specialist needs to be familiar with the characteristics of the different types of malware and attacks that threaten an organization.
34. Match the type of cyberattackers to the description. (Not all options are used.)
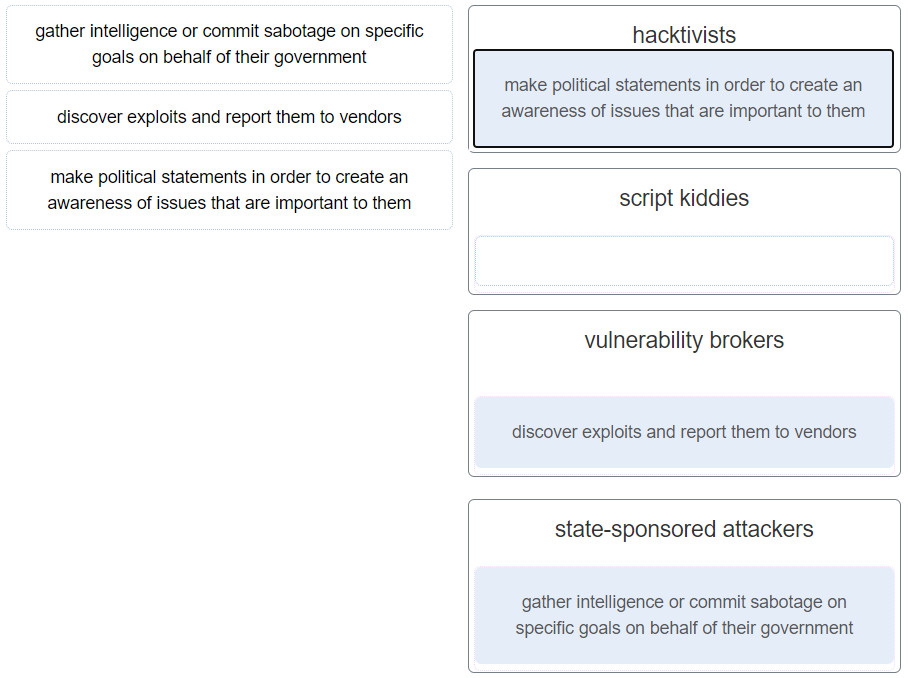
35. What is the purpose of a personal firewall on a computer?
- to protect the hardware against fire hazard
- to filter the traffic that is moving in and out of the PC
- to protect the computer from viruses and malware
- to increase the speed of the Internet connection
Explanation: The purpose of a firewall is to filter the traffic that is moving in and out of the PC. A computer firewall cannot deny all illegal traffic from a computer or increase the speed of any connection. It is also not able to protect hardware against fire hazards.
36. What technology was created to replace the BIOS program on modern personal computer motherboards?
Explanation: As of 2015, most personal computer motherboards are shipped with UEFI as the replacement for the BIOS program.
37. Which protocol provides authentication, integrity, and confidentiality services and is a type of VPN?
Explanation: IPsec services allow for authentication, integrity, access control, and confidentiality. With IPsec, the information exchanged between remote sites can be encrypted and verified. Both remote-access and site-to-site VPNs can be deployed using IPsec.
38. A new PC is taken out of the box, started up and connected to the Internet. Patches were downloaded and installed. Antivirus was updated. In order to further harden the operating system what can be done?
- Turn off the firewall.
- Remove the administrator account.
- Remove unnecessary programs and services.
- Install a hardware firewall.
- Give the computer a nonroutable address.
Explanation: When hardening an operating system, patching and antivirus are part of the process. Many extra components are added by the manufacturer that are not necessarily needed.
39. A cybercriminal sends a series of maliciously formatted packets to a database server, which causes the server to crash. What do you call this type of attack?
- Packet injection
- SQL injection
- DoS
- Man-in-the-middle
Explanation: A cybersecurity specialist needs to be familiar with the characteristics of the different types of malware and attacks that threaten an organization.
40. Which Linux command can be used to display the name of the current working directory?
Explanation: One of the most important commands in Linux is the pwd command, which stands for print working directory. It shows users the physical path for the directory they are working in.
41. A user creates a file with .ps1 extension in Windows. What type of file is it?
- PowerShell script
- PowerShell cmdlet
- PowerShell function
- PowerShell documentation
Explanation: The types of commands that PowerShell can execute include the following:
- cmdlets – perform an action and return an output or object to the next command that will be executed
- PowerShell scripts – files with a .ps1 extension that contain PowerShell commands that are executed
- PowerShell functions – pieces of code that can be referenced in a script
42. What principle prevents the disclosure of information to unauthorized people, resources, and processes?
- confidentiality
- integrity
- availability
- nonrepudiation
- accounting
Explanation: The security principle of confidentiality refers to the prevention of the disclosure of information to unauthorized people, resources, and processes.
43. What is a daemon?
- a background process that runs without the need for user interaction
- a record to keep track of important events
- a type of security attack
- an application that monitors and analyzes suspicious activity
Explanation: A daemon in Linux is a background process that runs without the need for user interaction. A network administrator can view log files in order to see information about daemons running on the Linux server.
44. Which technology is used to secure, monitor, and manage mobile devices?
- MDM
- VPN
- rootkit
- ASA firewall
Explanation: Mobile Device Management (MDM) is used to secure, monitor, and manage both corporate-owned and employee-owned devices such as smartphones, tablets, laptops, and desktops.
45. What kind of ICMP message can be used by threat actors to map an internal IP network?
- ICMP echo request
- ICMP router discovery
- ICMP mask reply
- ICMP redirects
Explanation: Common ICMP messages of interest to threat actors include these:
- ICMP echo request and echo reply: used to perform host verification and DoS attacks
- ICMP unreachable: used to perform network reconnaissance and scanning attacks
- ICMP mask reply: used to map an internal IP network
- ICMP redirects: used to lure a target host into sending all traffic through a compromised device and create a man-in-the-middle attack
- ICMP router discovery: used to inject bogus route entries into the routing table of a target host
46. Match typical Linux log files to the function.
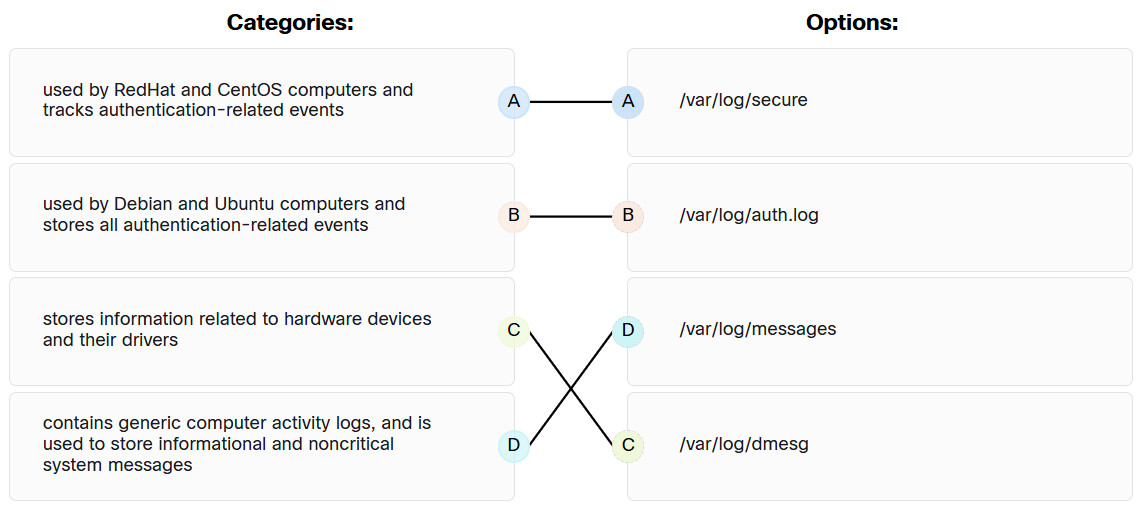
Explanation:
- used by RedHat and CentOS computers and tracks authentication-related events: /var/log/secure
- contains generic computer activity logs, and is used to store informational and noncritical system messages: /var/log/messages
- stores information related to hardware devices and their drivers: /var/log/dmesg
- used by Debian and Ubuntu computers and stores all authentication-related events: /var/log/auth.log
47. Which statement describes the term iptables?
- It is a DNS daemon in Linux.
- It is a DHCP application in Windows.
- It is a rule-based firewall application in Linux.
- It is a file used by a DHCP server to store current active IP addresses.
Explanation: Iptables is an application that allows Linux system administrators to configure network access rules.
48. Which wireless encryption method is the most secure?
- WPA
- WEP
- WPA2 with TKIP
- WPA2 with AES
Explanation: IEEE 802.11i and WPA2 both use the Advanced Encryption Standard (AES) for encryption. AES is currently considered the strongest encryption protocol. WPA2 does not use TKIP (Temporal Key Integrity Protocol). It is WPA that uses TKIP. Although WPA provides stronger encryption than WEP, it is is not as strong as WPA2 (AES).
49. Which statement describes the term attack surface?
- It is the network interface where attacks originate.
- It is the group of hosts that experiences the same attack.
- It is the total number of attacks toward an organization within a day.
- It is the total sum of vulnerabilities in a system that is accessible to an attacker.
Explanation: An attack surface is the total sum of the vulnerabilities in a system that is accessible to an attacker. The attack surface can consist of open ports on servers or hosts, software that runs on Internet-facing servers, wireless network protocols, and even users.
50. A secretary receives a phone call from someone claiming that their manager is about to give an important presentation but the presentation files are corrupted. The caller sternly asks that the secretary email the presentation right away to a personal email address. The caller also states that the secretary is being held personally responsible for the success of this presentation. What type of social engineering tactic is the caller using?
- Trusted partners
- Familiarity
- Intimidation
- Urgency
Explanation: Intimidation is a tactic that cybercriminals will often use to bully a victim into taking an action that compromises security.
51. How much RAM is addressable by a 32-bit version of Windows?
Explanation: A 32-bit operating system is capable of supporting approximately 4 GB of memory. This is because 2^32 is approximately 4 GB.
52. A threat actor uses a program to launch an attack by sending a flood of UDP packets to a server on the network. The program sweeps through all of the known ports trying to find closed ports. It causes the server to reply with an ICMP port unreachable message and is similar to a DoS attack. Which two programs could be used by the threat actor to launch the attack? (Choose two.)
- ping
- Smurf
- WireShark
- UDP Unicorn
- Low Orbit Ion Cannon
Explanation: A threat actor can use a tool like UDP Unicorn or Low Orbit Ion Cannon to send a flood of UDP packets to launch a UDP flood attack that causes all the resources on a network to become consumed. These types of programs will sweep through all the known ports trying to find closed ports. This causes the server to reply with an ICMP port unreachable message. Because of the many closed ports on the server, there is so much traffic on the segment that almost all the bandwidth gets used. The end result is very similar to a DoS attack.
53. Which antimalware software approach can recognize various characteristics of known malware files to detect a threat?
- routing-based
- behavior-based
- signature-based
- heuristics-based
Explanation: Antimalware programs may detect viruses using three different approaches:
- signature-based – by recognizing various characteristics of known malware files
- heuristics-based – by recognizing general features shared by various types of malware
- behavior-based – through analysis of suspicious activities
54. Which wireless parameter refers to the frequency bands used to transmit data to a wireless access point?
- SSID
- channel settings
- security mode
- scanning mode
Explanation: An access point can be manually set to a specific frequency band or channel in order to avoid interference with other wireless devices in the area.
55. What is the motivation of a white hat attacker?
- taking advantage of any vulnerability for illegal personal gain
- fine tuning network devices to improve their performance and efficiency
- studying operating systems of various platforms to develop a new system
- discovering weaknesses of networks and systems to improve the security level of these systems
Explanation: White hat attackers break into networks or computer systems in order to discover weaknesses for the purpose of improving the security of these systems. These break-ins are done with permission from the owner or the organization. Any results are reported back to the owner or the organization.
56. What is the reason for disabling SSID broadcasting and changing the default SSID on a wireless access point?
- Anyone with the default SSID can gain access to the access point and change the configuration.
- Disabling SSID broadcasting frees up radio frequency bandwidth and increases the data throughput of the access point.
- The access point stops broadcasting its own MAC address, thus preventing unauthorized wireless clients from connecting to the network.
- Wireless clients must then have the SSID manually configured to connect to the wireless network.
Explanation: The SSID is the name of the wireless network. Changing the default SSID forces device users to manually enter the SSID in order to gain access to the network. Broadcasting the SSID does not allow other devices to access the configuration, or to discover the MAC address of the device. SSID broadcasts do not affect radio frequency bandwidth.
57. Which statement describes a VPN?
- VPNs use dedicated physical connections to transfer data between remote users.
- VPNs use logical connections to create public networks through the Internet.
- VPNs use open source virtualization software to create the tunnel through the Internet.
- VPNs use virtual connections to create a private network through a public network.
Explanation: A VPN is a private network that is created over a public network. Instead of using dedicated physical connections, a VPN uses virtual connections routed through a public network between two network devices.
58. Consider the result of the ls -l command in the Linux output below. What are the file permissions assigned to the sales user for the analyst.txt file?
ls –l analyst.txt
-rwxrw-r-- sales staff 1028 May 28 15:50 analyst.txt
- write only
- read, write, execute
- read, write
- read only
Explanation: The file permissions are always displayed in the User, Group and Other order. In the example displayed, the file has the following permissions:
The dash (-) means that this is a file. For directories, the first dash would replaced with a “d”.
The first set of characters is for user permission (rwx). The user, sales, who owns the file can read, write and execute the file.
The second set of characters is for group permissions (rw-). The group, staff, who owns the file can read and write to the file.
The third set of characters is for any other user or group permissions (r–). Any other user or group on the computer can only read the file.
59. In Windows Firewall, when is the Domain profile applied?
- when the host accesses the Internet
- when the host checks emails from an enterprise email server
- when the host is connected to a trusted network such as an internal business network
- when the host is connected to an isolated network from the Internet by another security device
Explanation: The Domain profile in Windows Firewall configuration is for connections to a trusted network, such as a business network, that is assumed to have an adequate security infrastructure.
60. What are three states of data during which data is vulnerable? (Choose three.)
- stored data
- purged data
- data in-transit
- data encrypted
- data decrypted
- data in-process
Explanation: A cybersecurity specialist must be aware of each of the three states of data to effectively protect data and information. Purged data was stored data. Encrypted and decrypted data can be in any of the three states.
61. What does a rootkit modify?
- operating system
- programs
- screen savers
- notepad
- microsoft Word
Explanation: A rootkit commonly modifies an operating system to create a backdoor to bypass normal authentication mechanisms.
62. Which security technology is commonly used by a teleworker when accessing resources on the main corporate office network?
- IPS
- VPN
- SecureX
- biometric access
Explanation: VPNs are commonly used between corporate sites and between mobile or remote workers that connect to and use resources on the corporate network.
63. Which of the following statements describes a distributed denial of service (DDoS) attack?
- An attacker sends an enormous quantity of data that a server cannot handle
- An attacker monitors network traffic to learn authentication credentials
- One computer accepts data packets based on the MAC address of another computer
- A botnet of zombies, coordinated by an attacker, overwhelms a server with DoS attacks
Explanation: An attacker builds a network of infected hosts, called a botnet, comprised of zombies. Zombies are the infected hosts. The attacker uses handler systems to control the zombies. The zombie computers constantly scan and infect more hosts, creating more zombies. When ready, the hacker instructs the handler systems to make the botnet of zombies carry out a DDoS attack.
64. Match the network-based anti-malware solution to the function. (Not all options are used.)
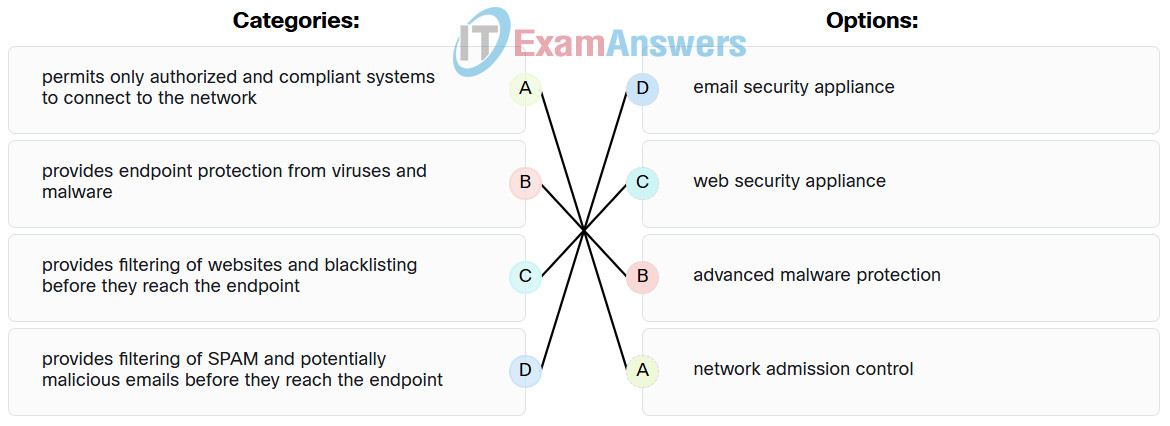
Explanation: Place the options in the following order:
| Provides filtering of SPAM and potentially malicious emails before they reach the endpoint |
Email security appliance |
| Provides filtering of websites and blacklisting before they reach the endpoint |
Web security appliance |
| Permits only authorized and compliant systems to connect to the network |
Network admission control |
| Provides dynamic IP addresses to authenticated endpoints |
No answer available |
| Provides endpoint protection from viruses and malware |
Advanced malware protection |
65. What is the result of a DHCP starvation attack?
- Legitimate clients are unable to lease IP addresses.
- Clients receive IP address assignments from a rogue DHCP server.
- The attacker provides incorrect DNS and default gateway information to clients.
- The IP addresses assigned to legitimate clients are hijacked.
Explanation: DCHP starvation attacks are launched by an attacker with the intent to create a DoS for DHCP clients. To accomplish this goal, the attacker uses a tool that sends many DHCPDISCOVER messages to lease the entire pool of available IP addresses, thus denying them to legitimate hosts.
66. Which two attacks target web servers through exploiting possible vulnerabilities of input functions used by an application? (Choose two.)
- SQL injection
- port scanning
- port redirection
- trust exploitation
- cross-site scripting
Explanation: When a web application uses input fields to collect data from clients, threat actors may exploit possible vulnerabilities for entering malicious commands. The malicious commands that are executed through the web application might affect the OS on the web server. SQL injection and cross-site scripting are two different types of command injection attacks.
67. A client device has initiated a secure HTTP request to a web browser. Which well-known port address number is associated with the destination address?
Explanation: Port numbers are used in TCP and UDP communications to differentiate between the various services running on a device. The well-known port number used by HTTPs is port 443.
68. What occurs when a rogue access point is added to a WLAN?
- Authorized access points can transmit excess traffic to rogue access points to help alleviate congestion.
- Unauthorized users can gain access to internal servers, thus causing a security hole.
- All traffic that uses the same channel as the rogue access point will be encrypted.
- All traffic that uses the same channel as the rogue access point will be required to authenticate.
69. What is the first line of defense to protect a device from improper access control?
- encryption
- end user license agreement (EULA)
- passwords
- shredding
Explanation: Improper access control is a common data loss vector. Passwords are the first line of defense because stolen or weak passwords provide a threat actor access to machines and data on the network.
70. What would be displayed if the netstat -abno command was entered on a Windows PC?
- a local routing table
- only active TCP connections in an ESTABLISHED state
- only active UDP connections in an LISTENING state
- all active TCP and UDP connections, their current state, and their associated process ID (PID)
Explanation: With the optional switch -abno, the netstat command will display all network connections together with associated running processes. It helps a user identify possible malware connections.
71. What three tasks are accomplished by a comprehensive security policy? (Choose three.)
- sets rules for expected behavior
- defines legal consequences of violations
- gives security staff the backing of management
- vagueness
- useful for management
- is not legally binding
Explanation: The security policy of an organization accomplishes several tasks:
- It demonstrates the commitment to security by an organization.
- It sets the rules for expected behavior.
- It ensures consistency in system operations, and software and hardware acquisition use and maintenance.
- It defines the legal consequences of violations.
- It gives security staff the backing of management.
72. What is the purpose of the cd∖ command?
- changes directory to the root directory
- changes directory to the next highest directory
- changes directory to the previous directory
- changes directory to the next lower directory
Explanation: CLI commands are typed into the Command Prompt window of the Windows operating system. The cd\ command is used to change the directory to the Windows root directory.
73. As described by the SANS Institute, which attack surface includes the exploitation of vulnerabilities in wired and wireless protocols used by IoT devices?
- human attack surface
- Internet attack surface
- network attack surface
- software attack surface
Explanation: The SANS Institute describes three components of the attack surface:
- Network Attack Surface – exploitation of vulnerabilities in networks
- Software Attack Surface – exploitation of vulnerabilities in web, cloud, or host-based software applications
- Human Attack Surface – exploitation of weaknesses in user behavior
74. Which term is used for bulk advertising emails flooded to as many end users as possible?
- Phishing
- Brute force
- Spam
- Adware
Explanation: Spam is annoying and unwanted bulk email that is sent to as many end users as possible.
75. A flood of packets with invalid source IP addresses requests a connection on the network. The server busily tries to respond, resulting in valid requests being ignored. What type of attack has occurred?
- UDP flood
- TCP session hijacking
- TCP reset
- TCP SYN flood
Explanation: The TCP SYN Flood attack exploits the TCP three-way handshake. The threat actor continually sends TCP SYN session request packets with a randomly spoofed source IP address to an intended target. The target device replies with a TCP SYN-ACK packet to the spoofed IP address and waits for a TCP ACK packet. Those responses never arrive. Eventually the target host is overwhelmed with half-open TCP connections and denies TCP services.
76. Which type of network attack involves randomly opening many Telnet requests to a router and results in a valid network administrator not being able to access the device?
- spoofing
- man-in-the-middle
- SYN flooding
- DNS poisoning
Explanation: The TCP SYN Flood attack exploits the TCP three-way handshake. The threat actor continually sends TCP SYN session request packets with a randomly spoofed source IP address to an intended target. The target device replies with a TCP SYN-ACK packet to the spoofed IP address and waits for a TCP ACK packet. Those responses never arrive. Eventually the target host is overwhelmed with half-open TCP connections and denies TCP services.
77. Which two options can limit the information discovered from port scanning? (Choose two.)
- authentication
- encryption
- firewall
- intrusion prevention system
- passwords
Explanation: Using an intrusion prevention system (IPS) and firewall can limit the information that can be discovered with a port scanner. Authentication, encryption, and passwords provide no protection from loss of information from port scanning.
78. What would be a reason for a computer user to use the Task Manager Performance tab?
- to increase the performance of the CPU
- to view the processes that are running and end a process if needed
- to view the services that are currently running on the PC
- to check the CPU usage of the PC
Explanation: The Performance tab is commonly used to check current computer performance. Two key areas that are shown are memory and CPU usage.
79. Which type of networks poses increasing challenges to cybersecurity specialists due to the growth of BYOD on campus?
- sneaker net
- wireless networks
- wired networks
- virtual networks
Explanation: A cybersecurity specialist must be familiar with the types of technologies used to store, transmit, and process data.
80. Which method can be used to harden a device?
- Allow users to re-use old passwords.
- Allow USB auto-detection.
- Force periodic password changes.
- Allow default services to remain enabled.
Explanation: The basic best practices for device hardening are as follows:
Ensure physical security.
Minimize installed packages.
Disable unused services.
Use SSH and disable the root account login over SSH.
Keep the system updated.
Disable USB auto-detection.
Enforce strong passwords.
Force periodic password changes.
Keep users from re-using old passwords.
Review logs regularly.
81. Which technology is used by Cisco Advanced Malware Protection (AMP) in defending and protecting against known and emerging threats?
- network admission control
- website filtering and blacklisting
- network profiling
- threat intelligence
Explanation: Cisco AMP uses threat intelligence along with known file signatures to identify and block policy-violating file types and exploitations.
82. Which user can override file permissions on a Linux computer?
- any user that has ‘group’ permission to the file
- root user
- any user that has ‘other’ permission to the file
- only the creator of the file
Explanation: A user has as much rights to a file as the file permissions allow. The only user that can override file permission on a Linux computer is the root user. Because the root user has the power to override file permissions, the root user can write to any file.
83. What do you call an impersonation attack that takes advantage of a trusted relationship between two systems?
- Sniffing
- Spamming
- Spoofing
- Man-in-the-middle
Explanation: In spoofing attacks, hackers can disguise their devices by using a valid address from the network and therefore bypass authentication processes. MAC addresses and IP addresses can be spoofed and can also be used to spoof ARP relationships.
84. Which device can control and manage a large number of corporate APs?
Explanation: A wireless LAN controller (WLC) can be configured to manage multiple lightweight access points (LWAPs). On the WLC, a network administrator can configure SSIDs, security, IP addressing, and other wireless network parameters in a centralized management environment.
85. Which HIDS is an open-source based product?
- Tripwire
- OSSEC
- Cisco AMP
- AlienVault USM
Explanation: The Open Source HIDS SECurity (OSSEC) software is an open-source HIDS that uses a central manager server and agents that are installed on the hosts that are to be monitored.
86. An attacker is using a laptop as a rogue access point to capture all network traffic from a targeted user. Which type of attack is this?
- trust exploitation
- buffer overflow
- man in the middle
- port redirection
Explanation: An access attack tries to gain access to a resource using a hijacked account or other means. The five types of access attacks include the following:password – a dictionary is used for repeated login attempts
trust exploitation – uses granted privileges to access unauthorized material
port redirection – uses a compromised internal host to pass traffic through a firewall
man-in-the-middle – an unauthorized device positioned between two legitimate devices in order to redirect or capture traffic
buffer overflow – too much data sent to a memory location that already contains data
87. A threat actor wants to interrupt a normal TCP communication between two hosts by sending a spoofed packet to both endpoints. Which TCP option bit would the threat actor set in the spoofed packet?
Explanation: A TCP reset attack can be used to terminate TCP communications between two hosts by sending a spoofed TCP RST packet. A TCP connection is torn down when it receives an RST bit.
88. Employees in an organization report that they cannot access the customer database on the main server. Further investigation reveals that the database file is now encrypted. Shortly afterward, the organization receives a threatening email demanding payment for the decryption of the database file. What type of attack has the organization experienced?
- DoS attack
- Man-in-the-middle attack
- Ransomware
- Trojan horse
Explanation: In a ransomware attack, the attacker compromises the victum computer and encrypts the hard drive so that data can no longer be accessed by the user. The attacker then demands payment from the user to decrypt the drive.
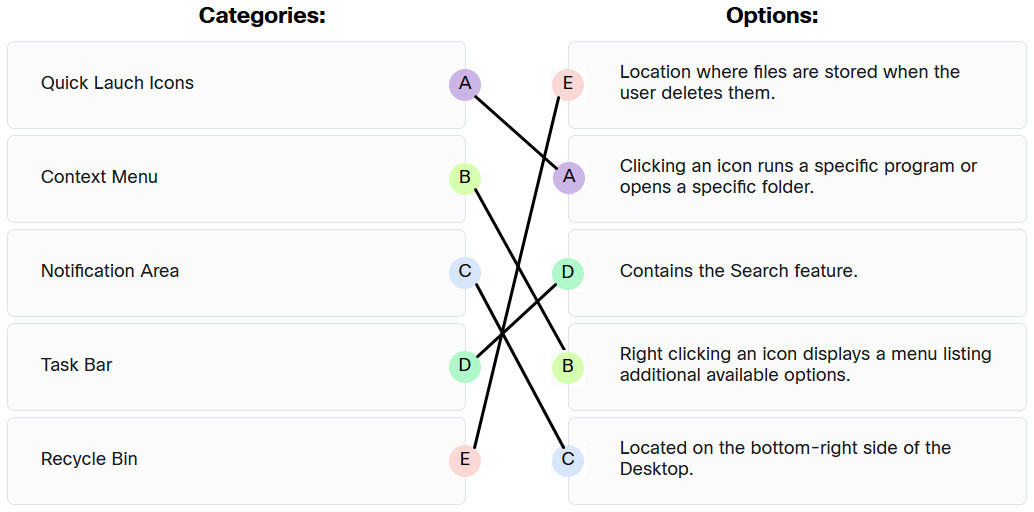
89. Match the Windows GUI term to the characteristic.
90. What three best practices can help defend against social engineering attacks? (Choose three.)
- Enable a policy that states that the IT department should supply information over the phone only to managers.
- Add more security guards.
- Resist the urge to click on enticing web links.
- Deploy well-designed firewall appliances.
- Educate employees regarding policies.
- Do not provide password resets in a chat window.
Explanation: A cybersecurity specialist must be aware of the technologies and measures that are used as countermeasures to protect the organization from threats and vulnerabilities.
91. Which Linux command would create a symbolic link for a file named file1.txt?
- ln file1.txt symbol1.txt
- ln -s file1.txt symbol1.txt
- ln -b file1.txt symbol1.txt
- ln – P file1.txt symbol1.txt
Explanation: The -s option specifies that you want to create a symbolic link.
92. Which type of DNS attack involves the cybercriminal compromising a parent domain and creating multiple subdomains to be used during the attacks?
- shadowing
- amplification and reflection
- tunneling
- cache poisoning
Explanation: Two threats to DNS are DNS shadowing and DNS tunneling attacks. DNS shadowing attacks compromise a parent domain and then the cybercriminal creates subdomains to be used in attacks. DNS tunneling attacks build botnets to bypass traditional security solutions. Three threats to DNS open resolvers are cache poisoning, amplification and reflection, and resource utilization attacks.
93. Which device in a LAN infrastructure is susceptible to MAC address-table overflow and spoofing attacks?
- firewall
- workstation
- server
- switch
Explanation: Switches are LAN infrastructure devices interconnecting endpoints. They are susceptible to LAN-related attacks including MAC address-table overflow attacks, spoofing attacks, LAN storm attacks, STP manipulation attacks, and VLAN attacks.
94. Match the step number to the description in a change password procedure on a Windows host.
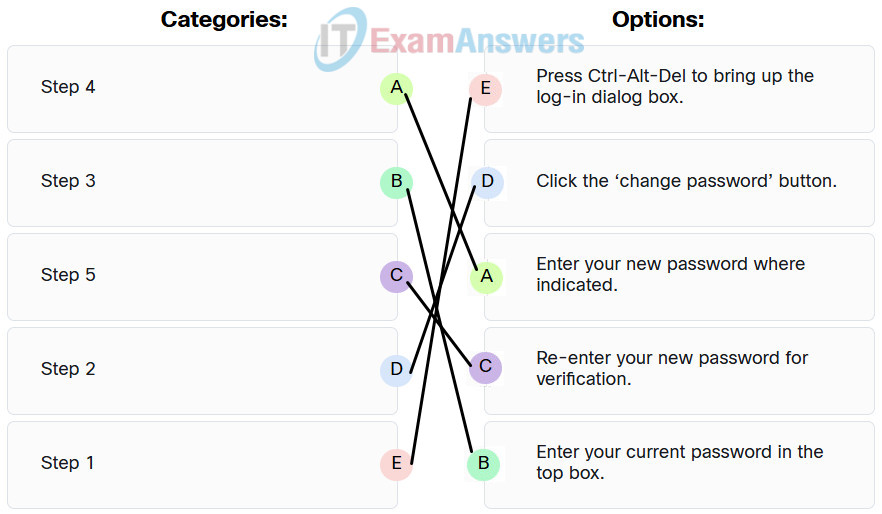
Explanation:
Step 1: Press Ctrl-Alt-Del to bring up the log-in dialog box.
Step 2: Click the ‘change password’ button.
Step 3: Enter your current password in the top box.
Step 4: Enter your new password where indicated.
Step 5: Re-enter your new password for verification.
95. What is a characteristic of the WLAN passive discover mode?
- The client must know the name of the SSID to begin the discover process.
- The client begins the discover process by sending a probe request.
- The beaconing feature on the AP is disabled.
- The AP periodically sends beacon frames containing the SSID.
Explanation: In passive mode, the wireless clients learn what networks and APs are available. The client learns this information from beacon frames, sent by the APs, that contain the WLAN SSID, supported standards, and security settings.
96. Which field in an IPv6 packet is used by the router to determine if a packet has expired and should be dropped?
- TTL
- Hop Limit
- Address Unreachable
- No Route to Destination
Explanation: ICMPv6, like IPv4, sends a Time Exceeded message if the router cannot forward an IPv6 packet because the packet has expired. However, the IPv6 packet does not have a TTL field. Instead, it uses the Hop Limit field to determine if the packet has expired.
97. Match the commonly used ports on a Linux server with the corresponding service. (Not all options are used.)
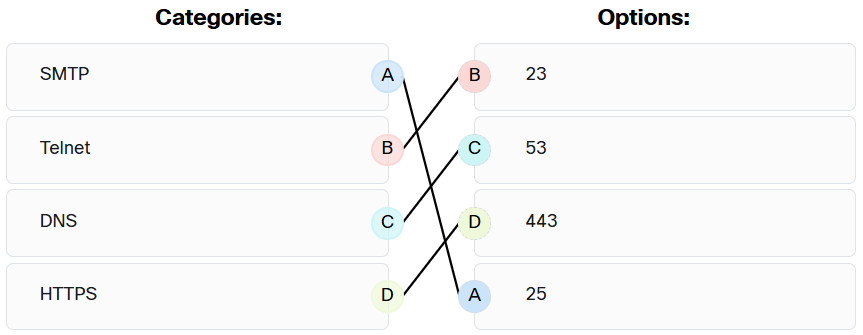
98. What is an example of a local exploit?
- Port scanning is used to determine if the Telnet service is running on a remote server.
- A threat actor performs a brute force attack on an enterprise edge router to gain illegal access.
- A buffer overflow attack is launched against an online shopping website and causes the server crash.
- A threat actor tries to gain the user password of a remote host by using a keyboard capture software installed on it by a Trojan.
Explanation: Vulnerability exploits may be remote or local. In a local exploit, the threat actor has some type of user access to the end system, either physically or through remote access. The exploitation activity is within the local network.
99. What are two drawbacks to using HIPS? (Choose two.)
- With HIPS, the success or failure of an attack cannot be readily determined.
- With HIPS, the network administrator must verify support for all the different operating systems used in the network.
- HIPS has difficulty constructing an accurate network picture or coordinating events that occur across the entire network.
- If the network traffic stream is encrypted, HIPS is unable to access unencrypted forms of the traffic.
- HIPS installations are vulnerable to fragmentation attacks or variable TTL attacks
Explanation: Two disadvantages of deploying HIPS are (1) that it cannot create a complete view of the network or have knowledge of events that might be occurring beyond an individual host and (2) every host operating system within the organization must be supported. However, an advantage of using HIPS is that it can monitor and protect the operating system as well as critical system processes on each network host.
100. Match the wireless and mobile device attack to the scenario.
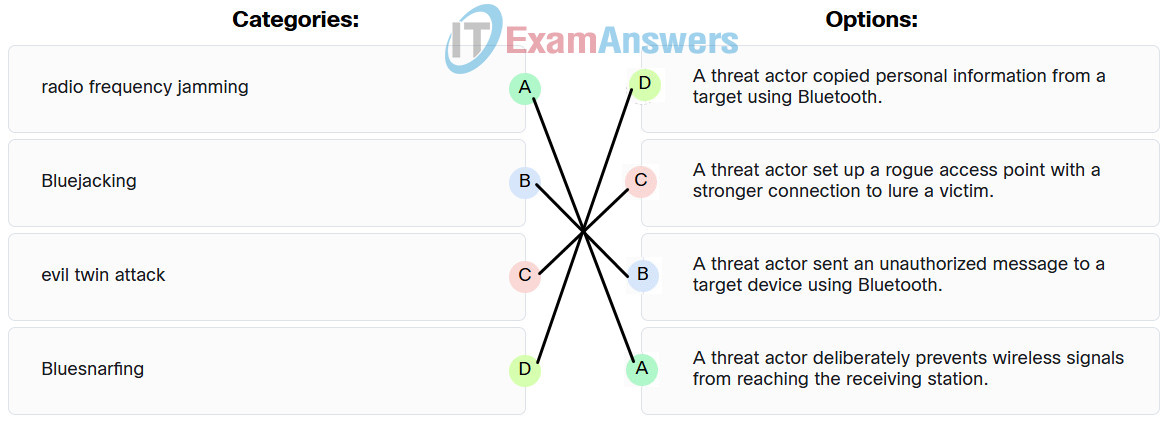
101. A system administrator issues the apt-get upgrade command on a Linux operating system. What is the purpose of this command?
- Every application installed will update itself to the latest version.
- Operating system updates are downloaded and will be installed.
- The remote repository of applications and dependencies will be updated to the latest version.
- A specific application named upgrade will be installed.
Explanation: When the apt-get upgrade command is isued in a Linux terminal, all installed applications will attempt to upgrade to the latest version available.
102. For security reasons a network administrator needs to ensure that local computers cannot ping each other. Which settings can accomplish this task?
- smartcard settings
- firewall settings
- MAC address settings
- file system settings
Explanation: Smartcard and file system settings do not affect network operation. MAC address settings and filtering may be used to control device network access but cannot be used to filter different data traffic types.
103. Which statement describes the policy-based intrusion detection approach?
- It compares the signatures of incoming traffic to a known intrusion database.
- It compares the operations of a host against well-defined security rules.
- It compares the antimalware definitions to a central repository for the latest updates.
- It compares the behaviors of a host to an established baseline to identify potential intrusion.
Explanation: With the anomaly-based intrusion detection approach, a set of rules or policies are applied to a host. Violation of these policies is interpreted to be the result of a potential intrusion.
104. City Center Hospital provides WLAN connectivity to its employees. The security policy requires that communication between employee mobile devices and the access points must be encrypted. What is the purpose of this requirement?
- to ensure that users who connect to an AP are employees of the hospital
- to prevent a computer virus on a mobile device from infecting other devices
- to prevent the contents of intercepted messages from being read
- to block denial of service attacks originating on the Internet
Explanation: Encrypting data during communication prevents the contents from intercepted communications from being read.
105. After host A receives a web page from server B, host A terminates the connection with server B. Match each option to its correct step in the normal termination proccess for a TCP connection.
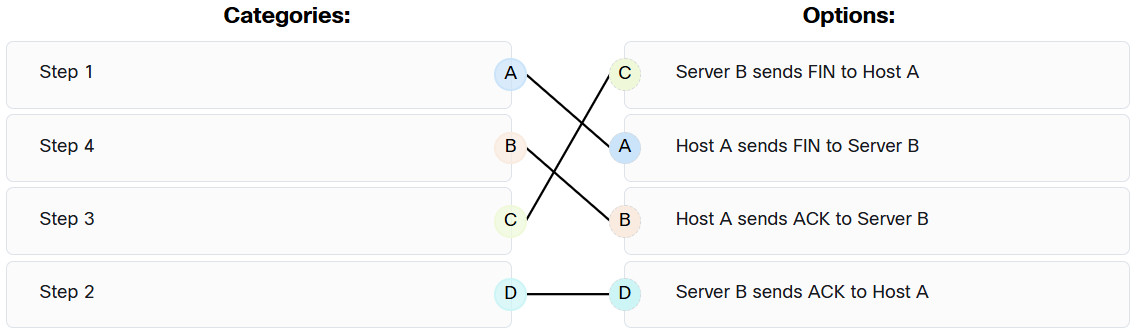
Explanation: Host A sends an ACK to server B. → Step 4
Host A sends a FIN to server B. → Step 1
Server B sends an ACK to host A. → Step 2
Server B sends a FIN to host A. → Step 3
106. Match the correct sequence of steps typically taken by a threat actor carrying out a domain shadowing attack.
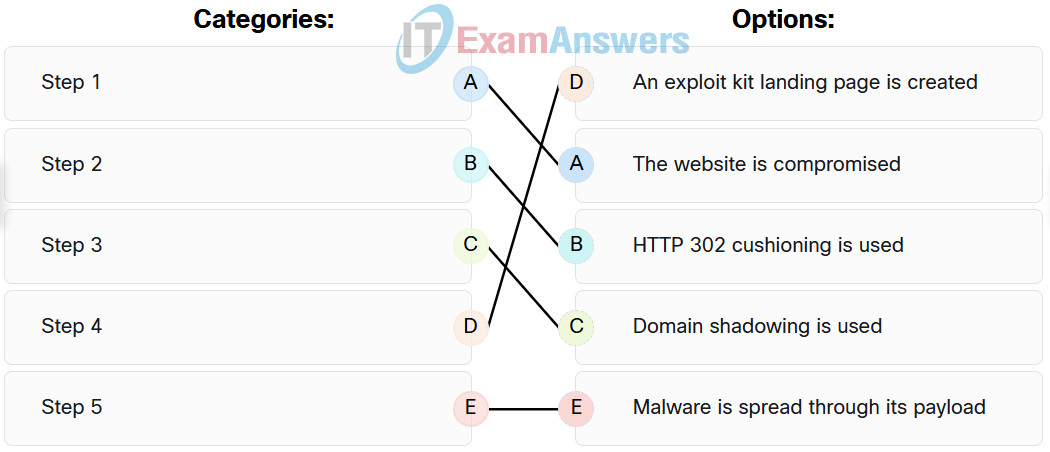
107. In the context of a Linux operating system, which command can be used to display the syntax and parameters for a specific command?
Explanation: The functions of listed CLI commands of a Linux system are as follows:
- cat – lists the contents of a file
- man – displays the documentation for a specific command
- crontab – manages the cron service for scheduling system tasks
- grep – searches for specific strings of characters within a file or other commands outputs
108. Which two methods help to ensure data integrity? (Choose two.)
- data consistency checks
- privacy
- hashing
- availability
- authorization
- repudiation
Explanation: Data integrity systems include one of the two data integrity methods.
109. Match the tabs of the Windows 10 Task Manager to their functions. (Not all options are used.)
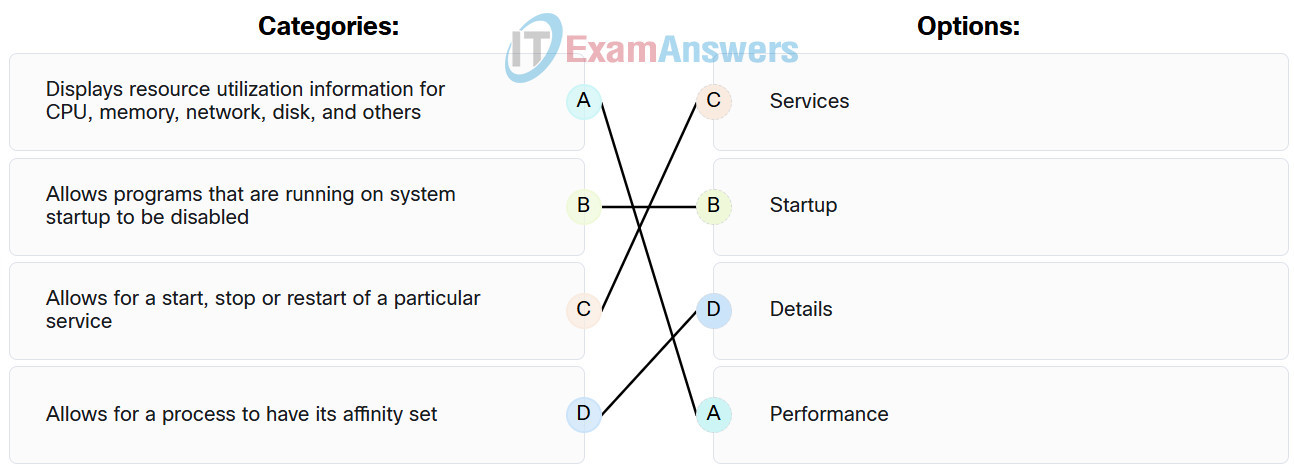
Explanation:
| Details |
Allows for a process to have its affinity set. |
| Performance |
Displays resource utilization information for CPU, memory, network, disk, and others. |
| Startup |
Allows programs that are running on system startup to be disabled. |
| Services |
Allows for a start, stop or restart of a particular service. |
110. A user is proposing the purchase of a patch management solution for a company. The user wants to give reasons why the company should spend money on a solution. What benefits does patch management provide? (Choose three.)
- Patches can be written quickly.
- Administrators can approve or deny patches.
- Patches can be chosen by the user.
- Updates cannot be circumvented.
- Computers require a connection to the Internet to receive patches.
- Updates can be forced on systems immediately.
Explanation: A centralized patch management system can speed up deployment of patches and automate the process. Other good reasons to using an automated patch update service include the following:
Administrators control the update process.
Reports are generated.
Updates are provided from a local server.
Users cannot circumvent the update process.
111. How is a source IP address used in a standard ACL?
- It is used to determine the default gateway of the router that has the ACL applied.
- It is the address that is unknown, so the ACL must be placed on the interface closest to the source address.
- It is the address to be used by a router to determine the best path to forward packets.
- It is the criterion that is used to filter traffic.
Explanation: The only filter that can be applied with a standard ACL is the source IP address. An extended ACL is used to filter on such traffic as the source IP address, destination IP address, type of traffic, and type of message.
112. What are two shared characteristics of the IDS and the IPS? (Choose two.)
- Both have minimal impact on network performance.
- Both are deployed as sensors.
- Both analyze copies of network traffic.
- Both use signatures to detect malicious traffic.
- Both rely on an additional network device to respond to malicious traffic.
Explanation: Both the IDS and the IPS are deployed as sensors and use signatures to detect malicious traffic. The IDS analyzes copies of network traffic, which results in minimal impact on network performance. The IDS also relies on an IPS to stop malicious traffic.
113. What type of cybersecurity laws protect you from an organization that might want to share your sensitive data?
- authentication
- confidentiality
- nonrepudiation
- privacy
- integrity
Explanation: Privacy laws control appropriate use of data and access to data.
114. What are two advantages of the NTFS file system compared with FAT32? (Choose two.)
- NTFS is easier to configure.
- NTFS provides more security features.
- NTFS supports larger files.
- NTFS allows faster access to external peripherals such as a USB drive.
- NTFS allows faster formatting of drives.
- NTFS allows the automatic detection of bad sectors.
Explanation: The file system has no control over the speed of access or formatting of drives, and the ease of configuration is not file system-dependent.
115. Which statement describes agentless antivirus protection?
- Host-based antivirus systems provide agentless antivirus protection.
- The antivirus protection is provided by the router that is connected to a cloud service.
- The antivirus protection is provided by the ISP.
- Antivirus scans are performed on hosts from a centralized system.
Explanation: Host-based antivirus protection is also known as agent-based. Agent-based antivirus runs on every protected machine. Agentless antivirus protection performs scans on hosts from a centralized system.
116. All employees in an organization receive an email stating that their account password will expire immediately and that they should reset their password within five minutes. Which of the following statements best describes this email?
- It is a piggyback attack
- It is an impersonation attack
- It is a hoax
- It is a DDoS attack
Explanation: A hoax is an act intended to deceive or trick someone. This type of email can cause unnecessary disruption, extra work, and fear.
117. Which security measure is best used to limit the success of a reconnaissance attack from within a campus area network?
- Implement restrictions on the use of ICMP echo-reply messages.
- Implement a firewall at the edge of the network.
- Implement access lists on the border router.
- Implement encryption for sensitive traffic.
Explanation: The implementation of an access list may provide extra security by permitting denying a flow of traffic, but it will not provide a direct response to limit the success of the attack. The implementation of a firewall on the network edge may prevent reconnaissance attacks from the Internet, but attacks within the local network are not prevented. By implementing restrictions on the sending of ICMP echo-reply messages within a local network, devices may not respond to ping messages, but port scans are not prevented and clear-text data sent on the network are still vulnerable. The best security measure is to encrypt as much network traffic as possible, both user data and network management traffic.
118. What tasks are accomplished by a comprehensive security policy? (Select three answers)
- It sets rules for expected behavior
- It defines legal consequences of violations
- It gives security staff the backing of management
- It provides vagueness
- It is is useful for management
- It is not legally binding
Explanation: A comprehensive security policy accomplishes several tasks:
– It demonstrates an organization’s commitment to security.
– It sets the rules for expected behavior.
– It ensures consistency in system operations and software and hardware acquisition, use, and maintenance.
– It defines the legal consequences of violations.
– It gives security staff the backing of management.
119. A network administrator of a small advertising company is configuring WLAN security by using the WPA2 PSK method. Which credential do office users need in order to connect their laptops to the WLAN?
- the company username and password through Active Directory service
- a user passphrase
- a key that matches the key on the AP
- a username and password configured on the AP
Explanation: When a WLAN is configured with WPA2 PSK, wireless users must know the pre-shared key to associate and authenticate with the AP.
120. Match the Linux command to the function. (Not all options are used.)
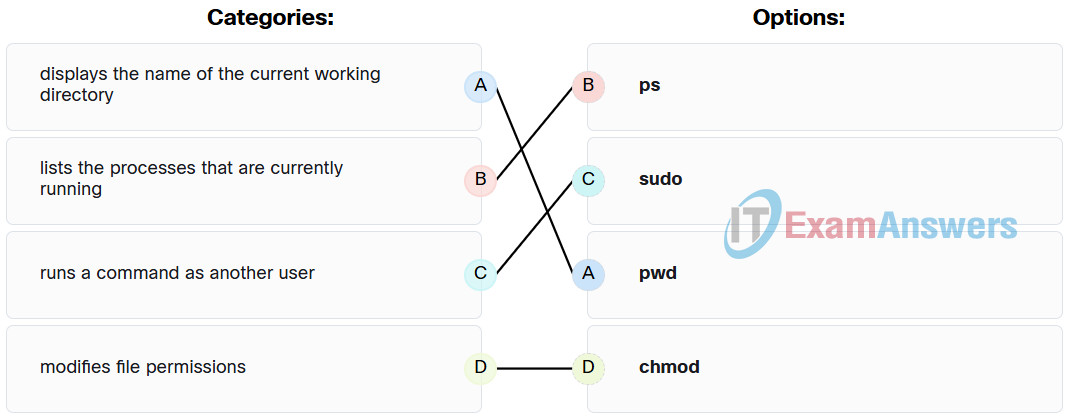
- Displays the name of the current working directory: pwd
- runs a command as another user: sudo
- modifies file permissions: chmod
- shuts down the system: Empty
- lists the processes that are currently running: ps
121. Which statement describes the anomaly-based intrusion detection approach?
- It compares the antivirus definition file to a cloud based repository for latest updates.
- It compares the behavior of a host to an established baseline to identify potential intrusions.
- It compares the signatures of incoming traffic to a known intrusion database.
- It compares the operations of a host against a well-defined security policy.
Explanation: With an anomaly-based intrusion detection approach, a baseline of host behaviors is established first. The host behavior is checked against the baseline to detect significant deviations, which might indicate potential intrusions.
122. A security incident has been filed and an employee believes that someone has been on the computer since the employee left last night. The employee states that the computer was turned off before the employee left for the evening. The computer is running slowly and applications are acting strangely. Which Microsoft Windows tool would be used by the security analyst to determine if and when someone logged on to the computer after working hours?
- Task Manager
- Event Viewer
- PowerShell
- Performance Monitor
Explanation: Event Viewer is used to investigate the history of application, security, and system events. Events show the date and time that the event occurred along with the source of the event. If a cybersecurity analyst has the address of the Windows computer targeted or the date and time that a security breach occurred, the analyst could use Event Viewer to document and prove what occurred on the computer.
123. What is a method of sending information from one device to another using removable media?
- wired
- infrared
- LAN
- packet
- wireless
- sneaker net
Explanation: Sneaker net refers to hand delivering the removable data.
124. What type of attack occurs when data goes beyond the memory areas allocated to an application?
- RAM spoofing
- SQL injection
- RAM injection
- Buffer overflow
Explanation: A buffer overflow occurs when data is written beyond the limits of a buffer. By changing data beyond the boundaries of a buffer, the application can access memory allocated to other processes. This can lead to a system crash or data compromise, or provide escalation of privileges.
125. Which technique could be used by security personnel to analyze a suspicious file in a safe environment?
- sandboxing
- baselining
- whitelisting
- blacklisting
Explanation: Sandboxing allows suspicious files to be executed and analyzed in a safe environment. There are free public sandboxes that allow for malware samples to be uploaded or submitted and analyzed.
126. What principle prevents the disclosure of information to unauthorized people, resources, and processes?
- integrity
- confidentiality
- nonrepudiation
- accounting
- availability
Explanation: The security principle of confidentiality refers to the prevention of the disclosure of information to unauthorized people, resources, and processes.
127. Which type of tool is used by a Linux administrator to attack a computer or network to find vulnerabilities?
- Firewall
- PenTesting
- Malware analysis
- Intrusion detection system
Explanation: PenTesting is known as penetration testing and includes tools that are used to search for vulnerabilities in a network or computer by attacking it.
128. What is a wireless security mode that requires a RADIUS server to authenticate wireless users?
- personal
- shared key
- enterprise
- WEP
Explanation: WPA and WPA2 come in two types: personal and enterprise. Personal is used in home and small office networks. Shared key allows three different authentication techniques: (1) WEP, (2) WPA, and (3) 802.11i/WPA2. WEP is an encryption method.














Match the step number to the description in a change password procedure on a Windows host.
“
Categories:
Step 4
A
Step 2
B
Step 1
C
Step 5
D
Step 3
E
Options:
Re-enter your new password for verification.
Press Ctrl-Alt-Del to bring up the log-in dialog box.
Enter your current password in the top box.
Click the ‘change password’ button.
Enter your new password where indicated.
missing
What type of cybersecurity laws protect you from an organization that might want to share your sensitive data?