Endpoint Security (ESec) Final Exam Answers (Course Final Exam)
1. Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.)
- ping cisco.com
- net cisco.com
- ipconfig /flushdns
- nslookup cisco.com
- nbtstat cisco.com
2. A technician notices that an application is not responding to commands and that the computer seems to respond slowly when applications are opened. What is the best administrative tool to force the release of system resources from the unresponsive application?
- Event Viewer
- Add or Remove Programs
- System Restore
- Task Manager
3. What is required in order to connect a Wi-Fi enabled laptop to a WPA secured wireless network?
- a MAC address
- a username and password
- a security encryption key
- an updated wireless driver
4. Why would an attacker want to spoof a MAC address?
- so that the attacker can launch another type of attack in order to gain access to the switch
- so that the attacker can capture traffic from multiple VLANs rather than from just the VLAN that is assigned to the port to which the attacker device is attached
- so that a switch on the LAN will start forwarding frames to the attacker instead of to the legitimate host
- so that a switch on the LAN will start forwarding all frames toward the device that is under control of the attacker (that can then capture the LAN traffic)
5. What is a wireless security mode that requires a RADIUS server to authenticate wireless users?
- personal
- enterprise
- shared key
- WEP
6. What are three functions provided by the syslog service? (Choose three.)
- to select the type of logging information that is captured
- to provide traffic analysis
- to specify the destinations of captured messages
- to provide statistics on packets that are flowing through a Cisco device
- to gather logging information for monitoring and troubleshooting
- to periodically poll agents for data
7. A network administrator is checking the system logs and notices unusual connectivity tests to multiple well-known ports on a server. What kind of potential network attack could this indicate?
- access
- denial of service
- reconnaissance
- information theft
8. A technician has installed a third party utility that is used to manage a Windows 7 computer. However, the utility does not automatically start whenever the computer is started. What can the technician do to resolve this problem?
- Set the application registry key value to one.
- Use the Add or Remove Programs utility to set program access and defaults.
- Change the startup type for the utility to Automatic in Services.
- Uninstall the program and then choose Add New Programs in the Add or Remove Programs utility to install the application.
9. What is the motivation of a white hat attacker?
- discovering weaknesses of networks and systems to improve the security level of these systems
- studying operating systems of various platforms to develop a new system
- fine tuning network devices to improve their performance and efficiency
- taking advantage of any vulnerability for illegal personal gain
10. Which two types of hackers are typically classified as grey hat hackers? (Choose two.)
- hacktivists
- cyber criminals
- state-sponsored hackers
- script kiddies
- vulnerability brokers
11. What are two shared characteristics of the IDS and the IPS? (Choose two.)
- Both have minimal impact on network performance.
- Both analyze copies of network traffic.
- Both are deployed as sensors.
- Both rely on an additional network device to respond to malicious traffic.
- Both use signatures to detect malicious traffic.
12. An attacker is sitting in front of a store and wirelessly copies emails and contact lists from nearby unsuspecting user devices. What type of attack is this?
- bluejacking
- RF jamming
- bluesnarfing
- smishing
13. An organization allows employees to work from home two days a week. Which technology should be implemented to ensure data confidentiality as data is transmitted?
- SHS
- VLANS
- RAID
- VPN
14. A new PC is taken out of the box, started up and connected to the Internet. Patches were downloaded and installed. Antivirus was updated. In order to further harden the operating system what can be done?
- Turn off the firewall.
- Remove unnecessary programs and services.
- Disconnect the computer from the network.
- Give the computer a nonroutable address.
- Install a hardware firewall.
- Remove the administrator account.
15. Which type of networks poses increasing challenges to cybersecurity specialists due to the growth of BYOD on campus?
- wired networks
- virtual networks
- wireless networks
- sneaker net
16. What are two types of attacks used on DNS open resolvers? (Choose two.)
- ARP poisoning
- resource utilization
- cushioning
- amplification and reflection
- fast flux
17. What would be the target of an SQL injection attack?
- database
- DHCP
- DNS
18. A security specialist is asked for advice on a security measure to prevent unauthorized hosts from accessing the home network of employees. Which measure would be most effective?
- Implement a VLAN.
- Implement intrusion detection systems.
- Implement RAID.
- Implement a firewall.
19. Match the network service with the description.
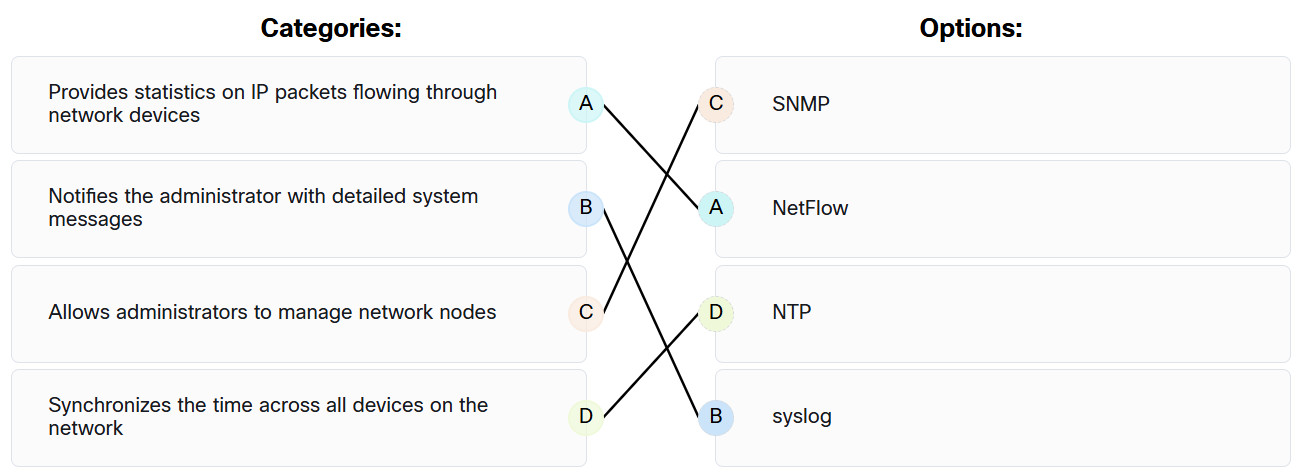
Endpoint Security (ESec) Final Exam Answers 19
20. Which method can be used to harden a device?
- allow USB auto-detection
- use SSH and disable the root account access over SSH
- allow default services to remain enabled
- maintain use of the same passwords
21. Which user can override file permissions on a Linux computer?
- root user
- any user that has ‘group’ permission to the file
- only the creator of the file
- any user that has ‘other’ permission to the file
22. Which wireless parameter is used by an access point to broadcast frames that include the SSID?
- passive mode
- channel setting
- active mode
- security mode
23. What is the outcome when a Linux administrator enters the man man command?
- The man man command provides documentation about the man command
- The man man command provides a list of commands available at the current prompt
- The man man command opens the most recent log file
- The man man command configures the network interface with a manual address
24. Which technique could be used by security personnel to analyze a suspicious file in a safe environment?
- whitelisting
- baselining
- blacklisting
- sandboxing
25. What are three benefits of using symbolic links over hard links in Linux? (Choose three.)
- Symbolic links can be exported.
- They can be compressed.
- They can link to a file in a different file system.
- They can link to a directory.
- They can be encrypted.
- They can show the location of the original file.
26. Which field in the IPv6 header points to optional network layer information that is carried in the IPv6 packet?
- traffic class
- version
- flow label
- next header
27. What is the term used when a malicious party sends a fraudulent email disguised as being from a legitimate, trusted source?
- phishing
- backdoor
- Trojan
- vishing
28. Which technology is used by Cisco Advanced Malware Protection (AMP) in defending and protecting against known and emerging threats?
- website filtering and blacklisting
- threat intelligence
- network admission control
- network profiling
29. After host A receives a web page from server B, host A terminates the connection with server B. Match each option to its correct step in the normal termination proccess for a TCP connection.
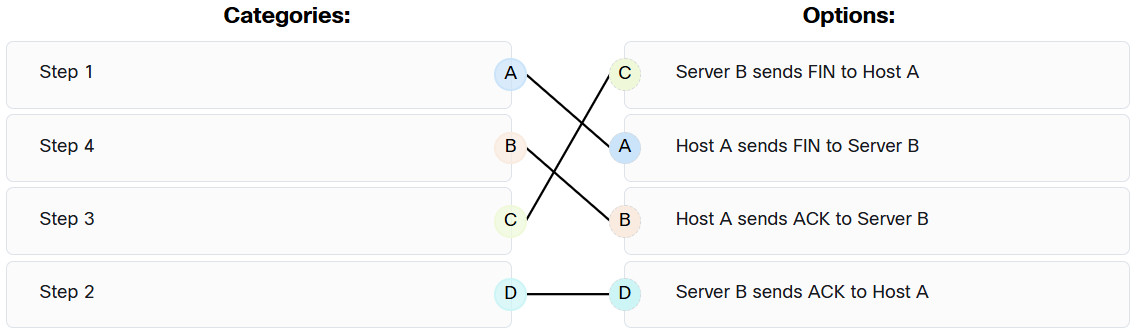
30. A flood of packets with invalid source IP addresses requests a connection on the network. The server busily tries to respond, resulting in valid requests being ignored. What type of attack has occurred?
- TCP session hijacking
- TCP reset
- TCP SYN flood
- UDP flood
31. Which Windows tool can be used by a cybersecurity administrator to secure stand-alone computers that are not part of an active directory domain?
- Windows Defender
- Local Security Policy
- Windows Firewall
- PowerShell
32. Match the correct sequence of steps typically taken by a threat actor carrying out a domain shadowing attack.
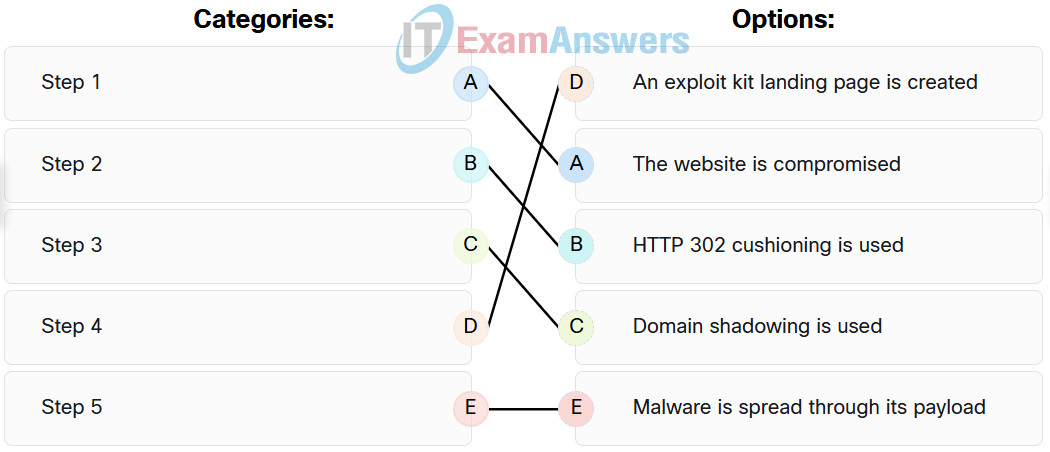
33. What is a feature of distributed firewalls?
- They combine the feature of host-based firewalls with centralized management.
- They all use an open sharing standard platform.
- They use only TCP wrappers to configure rule-based access control and logging systems.
- They use only iptables to configure network rules.
34. What does the telemetry function provide in host-based security software?
- It updates the heuristic antivirus signature database.
- It enables host-based security programs to have comprehensive logging functions.
- It blocks the passage of zero-day attacks.
- It enables updates of malware signatures.
35. What is an attack vector as it relates to network security?
- a path by which a threat actor can gain access to an internal network device
- a defense-in-depth approach to security
- a particular section of a network design where security is applied
- a method of reverse engineering binary files
36. What occurs when a rogue access point is added to a WLAN?
- Authorized access points can transmit excess traffic to rogue access points to help alleviate congestion.
- Unauthorized users can gain access to internal servers, thus causing a security hole.
- All traffic that uses the same channel as the rogue access point will be encrypted.
- All traffic that uses the same channel as the rogue access point will be required to authenticate.
37. What is the reason for disabling SSID broadcasting and changing the default SSID on a wireless access point?
- The access point stops broadcasting its own MAC address, thus preventing unauthorized wireless clients from connecting to the network.
- Anyone with the default SSID can gain access to the access point and change the configuration.
- Disabling SSID broadcasting frees up radio frequency bandwidth and increases the data throughput of the access point.
- Wireless clients must then have the SSID manually configured to connect to the wireless network.
38. Which two options can limit the information discovered from port scanning? (Choose two.)
- encryption
- firewall
- authentication
- intrusion prevention system
- passwords
39. What does a rootkit modify?
- Microsoft Word
- operating system
- programs
- Notepad
- screen savers
40. What is a nontechnical method that a cybercriminal would use to gather sensitive information from an organization?
- pharming
- man-in-the-middle
- social engineering
- ransomeware
41. Match the commonly used ports on a Linux server with the corresponding service.
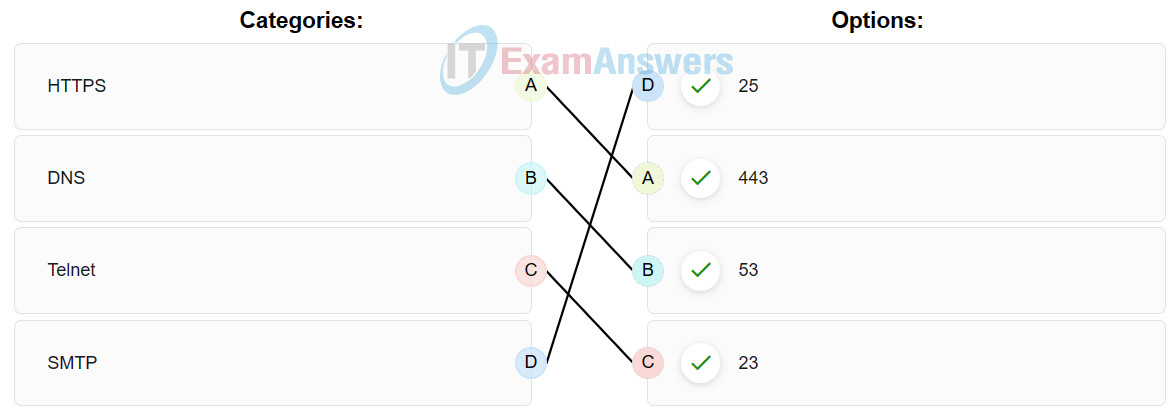
42. Which statement describes the anomaly-based intrusion detection approach?
- It compares the antivirus definition file to a cloud based repository for latest updates.
- It compares the signatures of incoming traffic to a known intrusion database.
- It compares the operations of a host against a well-defined security policy.
- It compares the behavior of a host to an established baseline to identify potential intrusions.
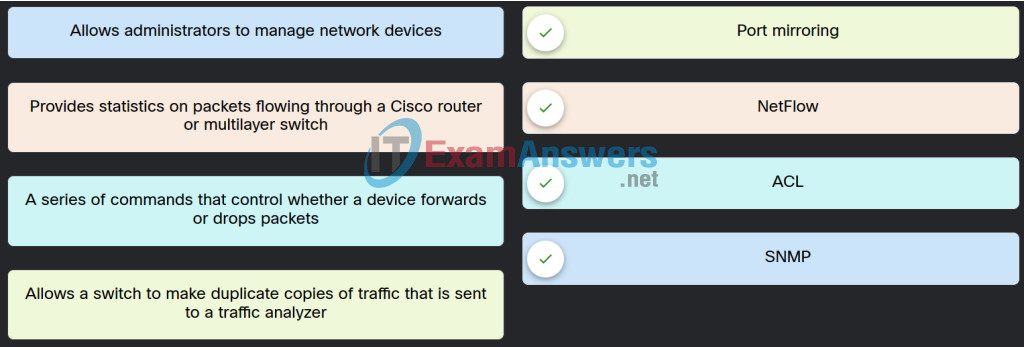
43. Match the security service with the description.
44. What is an example of a local exploit?
- A threat actor tries to gain the user password of a remote host by using a keyboard capture software installed on it by a Trojan.
- A buffer overflow attack is launched against an online shopping website and causes the server crash.
- Port scanning is used to determine if the Telnet service is running on a remote server.
- A threat actor performs a brute force attack on an enterprise edge router to gain illegal access.
45. Match the tabs of the Windows 10 Task Manager to their functions.
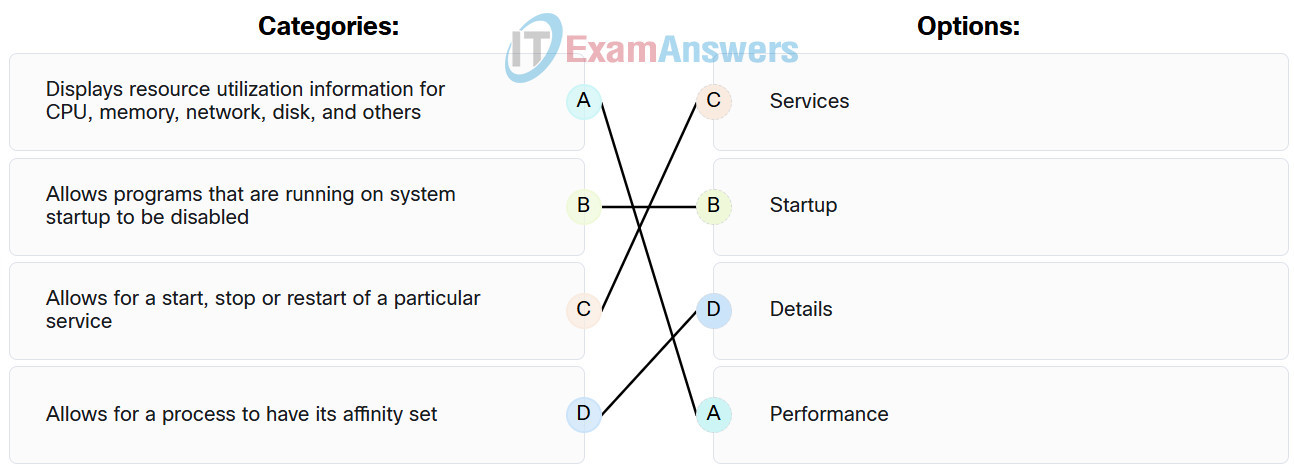
| Details | Allows for a process to have its affinity set. |
| Performance | Displays resource utilization information for CPU, memory, network, disk, and others. |
| Startup | Allows programs that are running on system startup to be disabled. |
| Services | Allows for a start, stop or restart of a particular service. |
46. In an attempt to prevent network attacks, cyber analysts share unique identifiable attributes of known attacks with colleagues. What three types of attributes or indicators of compromise are helpful to share? (Choose three.)
- netbios names of compromised firewalls
- BIOS of attacking systems
- features of malware files
- IP addresses of attack servers
- changes made to end system software
- system ID of compromised systems
47. Which data state is maintained in NAS and SAN services?
- data in-process
- stored data
- data in-transit
- encrypted data
48. What is the result of a passive ARP poisoning attack?
- Network clients experience a denial of service.
- Multiple subdomains are created.
- Data is modified in transit or malicious data is inserted in transit.
- Confidential information is stolen.
49. The entrepreneur is concerned about company employees having uninterrupted access to important resources and data. Which of the CIA triad components would address the concern?
- integrity
- availability
- authentication
- confidentiality

The entrepreneur is concerned about company employees having uninterrupted access to important resources and data. Which of the CIA triad components would address the concern?
it should actually be: availability
Fixed, thanks!
Which type of device provides an Internet connection through the use of a phone jack?
cable modem
Wi-Fi AP
satellite modem
DSL modem
Which three steps must be completed to manually connect an Android or IOS device to a secured wireless network? (Choose three.)
Change the MAC address.
Choose the correct security type.
Activate the Bluetooth antenna.
Input the authentication password.
Set the IP address.
Enter the network SSID.
A network technician attempts to ping http://www.example.net from a customer computer, but the ping fails. Access to mapped network drives and a shared printer are working correctly. What are two potential causes for this problem? (Choose two.)
The HTTP protocol is not working properly on the target server.
The target web server is down.
The computer has been assigned a static IP address.
The Windows domain or workgroup name that is configured on the computer is incorrect.
DNS service is unavailable on the customer network.
What layer is responsible for routing messages through an internetwork in the TCP/IP model?
session
internet
network access
transport
An employee is having connectivity issues. Why might a network technician try to ping the default gateway from the employee laptop?
to verify that the SVI interface on the switch is configured correctly
to determine if the laptop address is included in the DNS server
to verify that an IP address was provided by the DHCP server
to verify connectivity with the device that provides access to remote networks
What occurs when a rogue access point is added to a WLAN?
I added. Thank you.