Match TCP/IP attack type to the respective description.
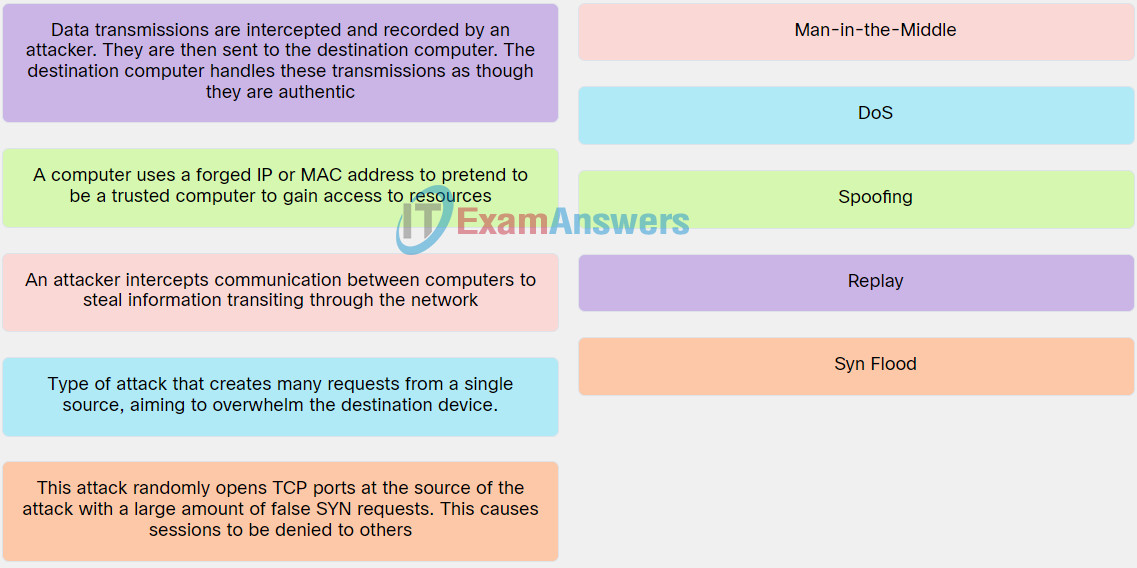
Explanation: Place the options in the following order:
| An attacker intercepts communication between computers to steal information transiting through the network. | Man-in-the-Middle |
| Type of attack that creates many requests from a single source, aiming to overwhelm the destination device. | DoS |
| A computer uses a forged IP or MAC address to pretend to be a trusted computer to gain access to resources. | Spoofing |
| Data transmissions are intercepted and recorded by an attacker. They are then sent to the destination computer. The destination computer handles these transmissions as though they are authentic. | Replay |
| This attack randomly opens TCP ports at the source of the attack with a large amount of false SYN requests. This causes sessions to be denied to others. | Syn Flood |
Exam with this question: IT Essentials v8 Chapter 13 Check Your Understanding
Please login or Register to submit your answer
