Match the network security testing technique with how it is used to test network security. (Not all options are used.)
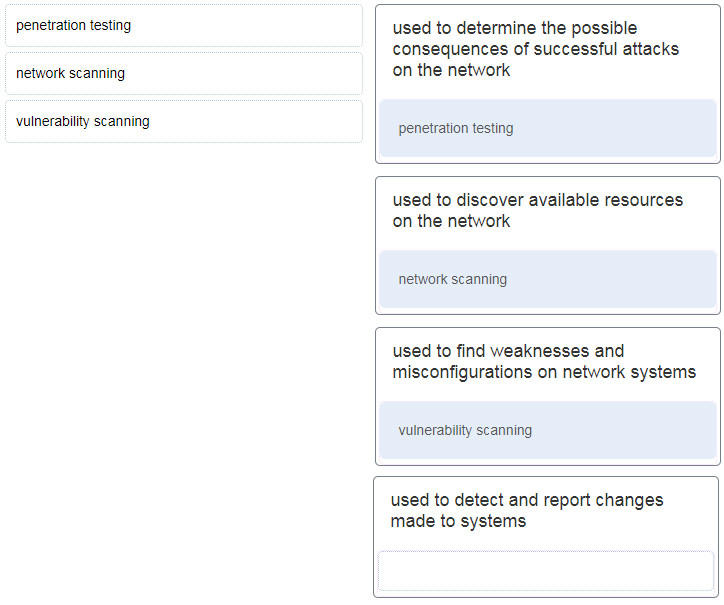
- Penetration testing = used to determine the possible consequences of successful attacks on the network.
- Vulnerability scanning = used to find weaknesses and misconfigurations on network systems.
- Network scanning = used to discover available resources on the network.
Explanation: Network scanning tools are used to probe network devices, servers and hosts for open TCP or UDP ports. Vulnerability scanning tools are used to discover security weaknesses in a network or computer system. Penetration testing tools are used to determine the possible outcome of a successful attack on a network or computer system.
Exam with this question: CCNA Security Pretest Exam Answers
Exam with this question: CCNA Cyber Ops (v1.1) – Chapter 6 Exam Answers
Exam with this question: CyberOps Associate (Version 1.0) - CyberOps Associate 1.0 Practice Final exam
Exam with this question: CCNA Security Final Exam Answers
Please login or Register to submit your answer
