Case 1:
Match the term with the respective description
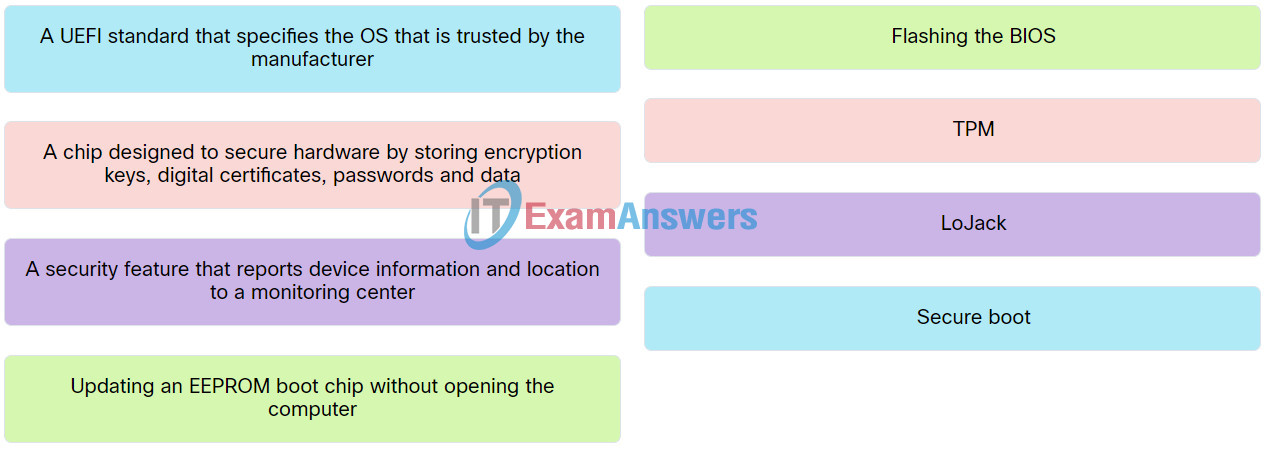
Explanation: Place the options in the following order:
| A chip designed to secure hardware by storing encryption keys, digital certificates, passwords and data. | TPM |
| A UEFI standard that specifies the OS that is trusted by the manufacturer. | Secure boot |
| Updating an EEPROM boot chip without opening the computer. | Flashing the BIOS |
| A security feature that reports device information and location to a monitoring center. | LoJack |
Case 2:
Match the term with the respective description.
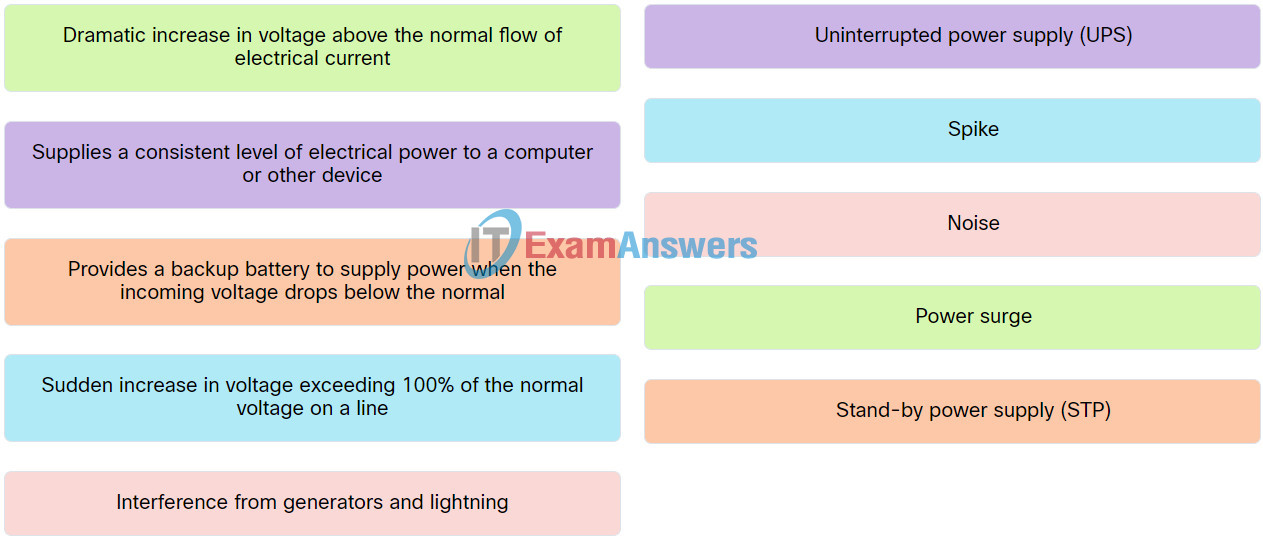
Explanation: Place the options in the following order:
| Interference from generators and lightning. | Noise |
| Sudden increase in voltage exceeding 100% of the normal voltage on a line. | Spike |
| Dramatic increase in voltage above the normal flow of electrical current. | Power surge |
| Supplies a consistent level of electrical power to a computer or other device. | Uninterrupted power supply (UPS) |
| Provides a backup battery to supply power when the incoming voltage drops below the normal-Stand. | by power supply (STP) |
Case 3:
Match the term with the respective description.
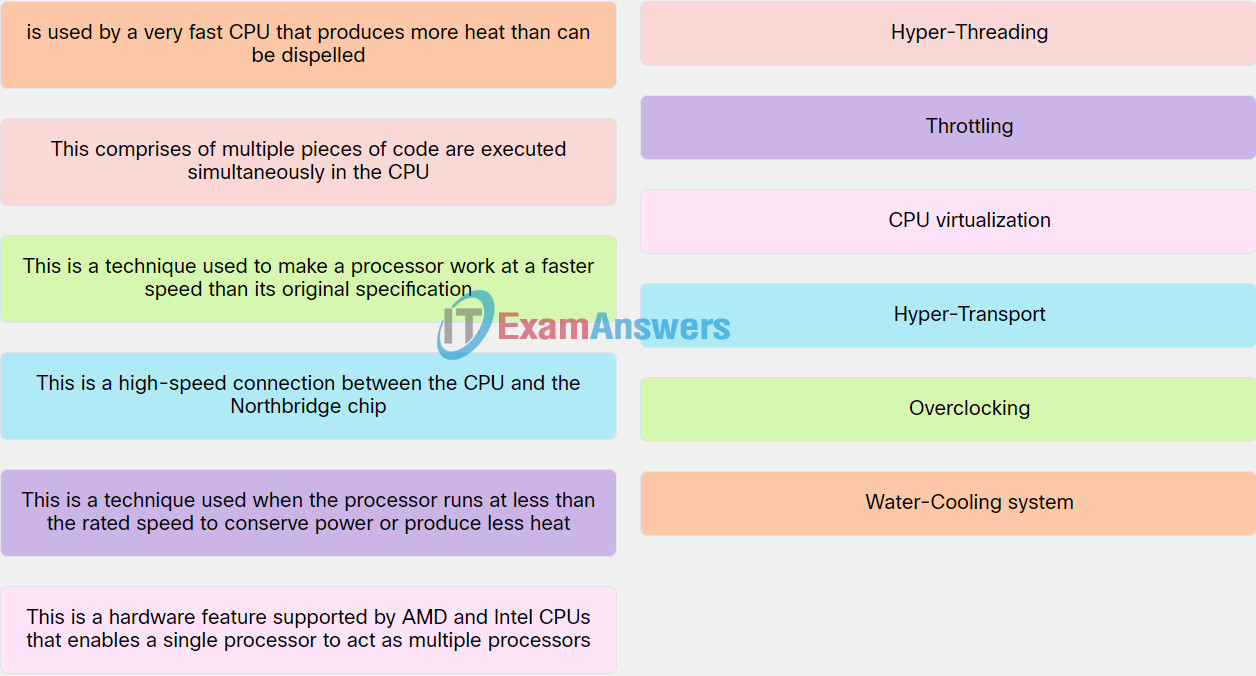
Explanation: Place the options in the following order:
| This comprises of multiple pieces of code are executed simultaneously in the CPU. | Hyper-Threading |
| This is a high-speed connection between the CPU and the Northbridge chip. | Hyper-Transport |
| This is a technique used to make a processor work at a faster speed than its original specification. | Power surge |
| Supplies a consistent level of electrical power to a computer or other device. | Uninterrupted power supply (UPS) |
| Provides a backup battery to supply power when the incoming voltage drops below the normal-Stand | by power supply (STP) |
Exam with this question: IT Essentials v8 Chapter 3 Check Your Understanding
Case 4:
Match the term with the respective description.
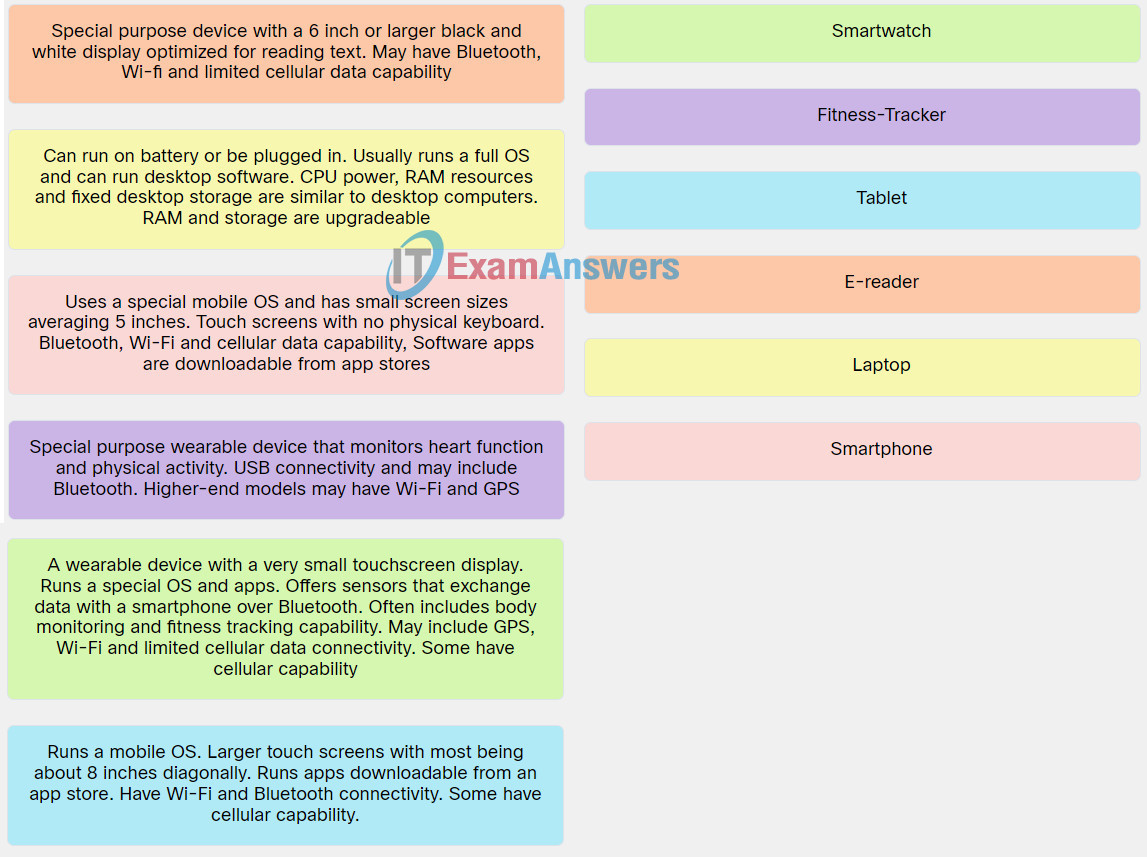
Explanation: Place the options in the following order:
| Uses a special mobile OS and has small screen sizes averaging 5 inches. Touch screens with no physical keyboard. Bluetooth, Wi-Fi and cellular data capability, Software apps are downloadable from app stores. | Smartphone |
| Runs a mobile OS. Larger touch screens with most being about 8 inches diagonally. Runs apps downloadable from an app store. Have Wi-Fi and Bluetooth connectivity. Some have cellular capability. | Tablet |
| A wearable device with a very small touchscreen display. Runs a special OS and apps. Offers sensors that exchange data with a smartphone over Bluetooth. Often includes body monitoring and fitness tracking capability. May include GPS, Wi-Fi and limited cellular data connectivity. Some have cellular capability. | Smartwatch |
| Special purpose wearable device that monitors heart function and physical activity. USB connectivity and may include Bluetooth. Higher-end models may have Wi-Fi and GPS. | Fitness-Tracker |
| Special purpose device with a 6 inch or larger black and white display optimized for reading text. May have Bluetooth, Wi-fi and limited cellular data capability. | E-reader |
| Can run on battery or be plugged in. Usually runs a full OS and can run desktop software. CPU power, RAM resources and fixed desktop storage are similar to desktop computers. RAM and storage are upgradeable. | Laptop |
Case 5:
Match the term with the respective description.
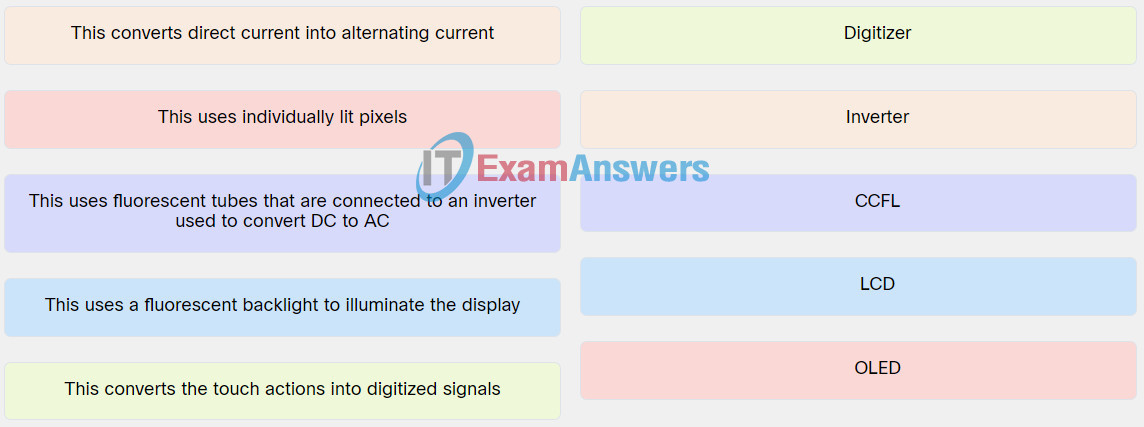
Explanation: Place the options in the following order:
| This uses a fluorescent backlight to illuminate the display. | LCD |
| This converts the touch actions into digitized signals. | Digitizer |
| This converts direct current into alternating current. | Inverter |
| This uses individually lit pixels. | OLED |
| This uses fluorescent tubes that are connected to an inverter used to convert DC to AC. | CCFL |
Exam with this question: IT Essentials v8 Chapter 7 Check Your Understanding
Case 6:
Match the term with the respective description.
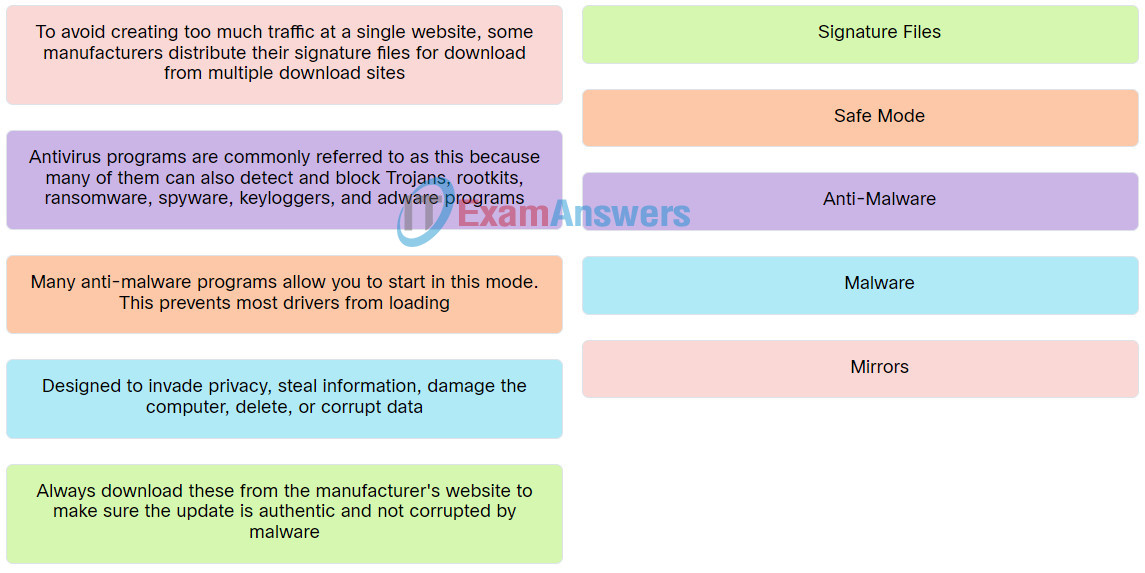
Explanation: Place the options in the following order:
| To avoid creating too much traffic at a single website, some manufacturers distribute their signature files for download from multiple download sites. | Mirrors |
| Designed to invade privacy, steal information, damage the computer, delete, or corrupt data. | Malware |
| Always download these from the manufacturer's website to make sure the update is authentic and not corrupted by malware. | Signature Files |
| Antivirus programs are commonly referred to as this because many of them can also detect and block Trojans, rootkits, ransomware, spyware, keyloggers, and adware programs. | Anti-Malware |
| Many anti-malware programs allow you to start in this mode. This prevents most drivers from loading. | Safe Mode |
Case 7:
Match the term with the respective description.
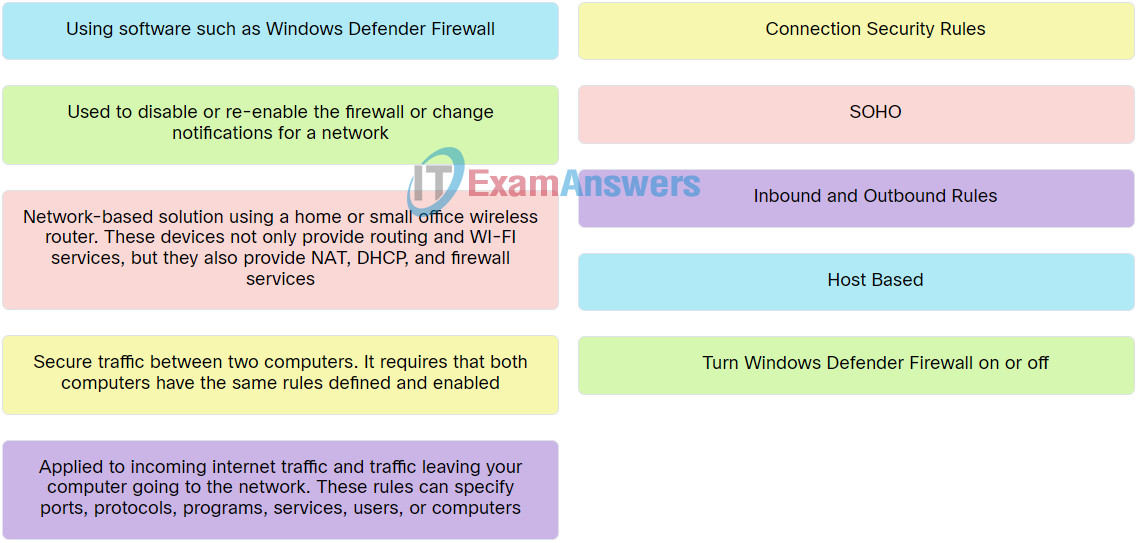
Explanation: Place the options in the following order:
| Network-based solution using a home or small office wireless router. These devices not only provide routing and WI-FI services, but they also provide NAT, DHCP, and firewall services. | SOHO |
| Using software such as Windows Defender Firewall. | Host Based |
| Used to disable or re-enable the firewall or change notifications for a network. | Turn Windows Defender Firewall on or off |
| Applied to incoming internet traffic and traffic leaving your computer going to the network. These rules can specify ports, protocols, programs, services, users, or computers. | Inbound and Outbound Rules |
| Secure traffic between two computers. It requires that both computers have the same rules defined and enabled. | Connection Security Rules |
Exam with this question: IT Essentials v8 Chapter 13 Check Your Understanding
Please login or Register to submit your answer
