4.2.2.6 Lab – Packet Crafting to Exploit Unsecured Ports (Instructor Version)
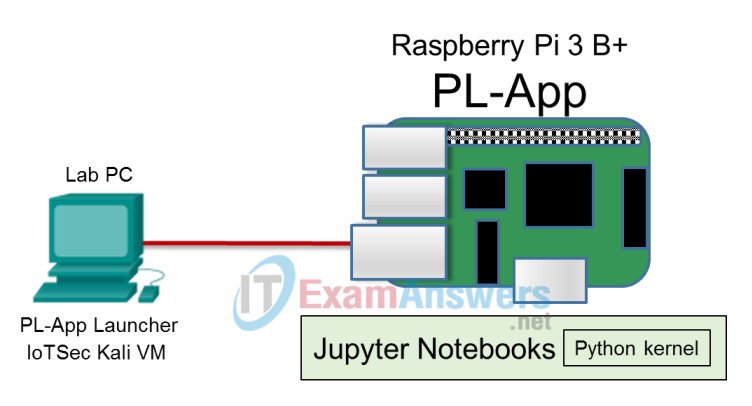
Topology
Objectives
- Part 1: Using hping3 for Port Scanning
- Part 2: Crafting Different Types of ICMP Messages
- Part 3: Launching DoS Attacks
Background / Scenario
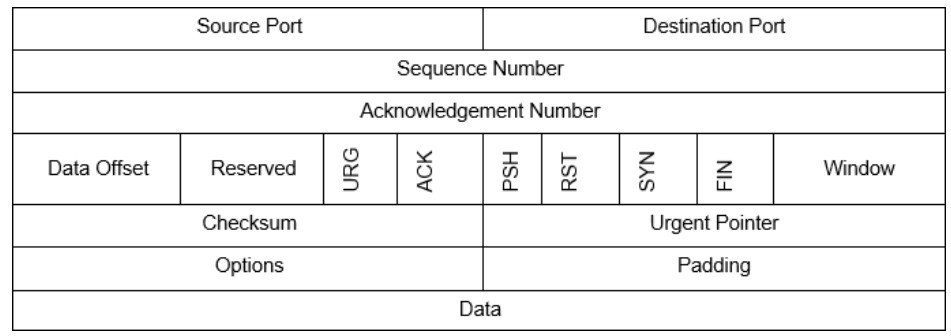
hping3 is a tool used to send custom-crafted TCP/IP packets to a network target in order to elicit a response. Many values in IP packets and TCP headers can be specified in hping3 and the resulting packets sent out on the network. Like Nmap, hping3 can use the TCP header flag fields URG, ACK, PSH, RST, SYN, and FIN to accomplish its scans. It can also craft packets with other protocols such as UDP and ICMP. Unlike Nmap, however, hping3 can use its ability to craft packets to attack a target. hping3 is included in Kali or can be downloaded from http://www.hping.org/. Because hping3 can be used for malicious purposes, avoid using it on production networks unless you have permission to do so.
Required Resources
- Raspberry Pi 3 Model B or later
- 8GB Micro SD card (minimum required)
- PC with IoTSec Kali VM
- Network connectivity between PC and Raspberry Pi
Part 1: Using hping3 for Port Scanning
a. Set up the topology by connecting the Raspberry Pi to the PC.
b. Start and log into IoTSec Kali VM.
c. Open a terminal and start the DHCP server on Kali VM.
root@kali:~# lab_support_files/scripts/start_dhcp.sh
d. Verify that the Kali VM is assigned an IP address on eth0.
root@kali:~# ifconfig
e. Determine the IP address of your Raspberry Pi.
f. Open the man page for hping3 in Kali VM and review the features and options that are available in hping3.
root@kali:~# man hping3
g. In a Kali VM terminal, start Wireshark to monitor what hping3 is doing when we are scanning.
root@kali:~# wireshark
h. In Wireshark, select the eth0 interface in packet capture.
i. You may have captured network traffic that is not relevant to this lab. We are going to restrict the type and of packets we see by using a display filter.
Apply the following filter in Wireshark using IP address of Kali VM as the source address and IP address of your Raspberry Pi as the destination address. In this example, 203.0.113.1 is IP address for Kali VM and 203.0.113.13 is the IP address of your Raspberry Pi.
ip.src == 203.0.113.1 && ip.dst == 203.0.113.13
j. We will first craft packets to do a port scan against the IP address of your Raspberry Pi.
root@kali:~# hping3 -8 0-100 -S 203.0.113.13
Refer to the Wireshark capture, the man pages, and other sources on the Internet. What do the options 8, 0-100 and -S do?
___________________________________________________________
-8 signifies scan mode, 0-100 is the port range to be scanned and -S is sets the SYN flag in the scan.
What ports are shown as open?
___________________________________________________________
Answers may vary. Ports 22 and 80 will be open at minimum.
k. Expand your scan to include ports up to 1000.
root@kali:~# hping3 -8 0-1000 -S 203.0.113.13
Did you find any additional ports?
__________________________________________________________
No
What TCP flag was set in the shown in Wireshark?
__________________________________________________________
SYN
Part 2: Crafting Different Types of ICMP Messages
ICMP has different message types that we can use to probe a target. For example, message types 8 – echo request and 0 – echo reply are used with the TCP/IP tool “ping.” However, if a target is configured not to respond to these ICMP message types, we can use other ICMP message types to attempt to get a response.
a. Open the man page for ICMP in Kali VM and review the features and options that are available in ICMP.
root@kali:~# man icmp
What is the RFC for ICMP?
____________________________________________________________
RFC 792
b. Start a new Wireshark capture. Click Continue without Saving when prompted to save the capture. Apply the same display filter as in the previous part.
c. In the terminal, enter the hping3 command followed by -1 to scan in ICMP mode. Add the scan target IP address, and enter -C followed by 13 to indicate that ICMP type 13 timestamp request messages should be sent.
root@kali:~# hping3 -1 203.0.113.13 -C 13
d. Review the Wireshark results and confirm that the ICMP timestamp request packets were sent out. To stop the requests, press Ctrl-C in the Kali VM terminal.
e. Start a new Wireshark capture. Click Continue without Saving when prompted to save the capture.
f. Apply the following filter in Wireshark using IP address of Kali VM as the source address and IP address of your Raspberry Pi as the destination address.
ip.src == 203.0.113.1 && ip.dst == 203.0.113.13
g. Repeat the hping3 command above, but this time send ICMP code 17.
h. Review the Wireshark results. Which ICMP message was sent?
__________________________________________________________
Address Mask Request
Part 3: Launching DoS Attacks
Hping3 can launch DoS attacks against ports you found previously in this lab. Using hping3 for this purpose is a good way to test how a network will react to various types of DoS attacks.
a. Start a new Wireshark capture. Click Continue without Saving when you are prompted to save the capture. To see two-way TCP traffic from between the Kali VM or the Raspberry Pi, enter only tcp as a display filter.
b. In the Kali VM terminal, enter the hping3 command to send a DoS attack.
root@kali:~# hping3 -S 203.0.113.13 -p 88 --flood
Looking at Wireshark and the hping3 documentation, what type of TCP messages were sent in this DoS attack? What was the destination TCP port of the attack?
___________________________________________________________
DoS SYN flood against port 88
Look at the source ports that hping3 uses to conduct the DoS flood. How does this scan assign source TCP ports?
____________________________________________________________
It starts at a random port and increments the source port number in each packet.
c. Press Ctrl-C to stop the flood.
d. Start a new Wireshark capture. Click Continue without Saving when prompted to save the capture. Display only traffic that has source or destination IP addresses that match the IP address of the Raspberry Pi. (Hint: Edit the ip.src and ip.dest display filter to both use the IP address of the Raspberry Pi. Instead of the && operator, use the || (or) operator.
e. In the Kali VM terminal, enter the hping3 command to send a DoS Land Attack. This attack sends a packet with the same source IP/port combination as the destination IP/port. In other words, the source IP address is “spoofed” by replacing the Kali VM address another value in the packets.
root@kali:~# hping3 -S 203.0.113.13 -a 203.0.113.13 -k -s 89 -p 89 --flood
Compare this scan with the SYN flood that you just ran. How were source ports used in this scan? What info does Wireshark report about the packets?
_____________________________________________________________
The source port is specified for the scan and it does not increment. Wirehark reports that TCP port numbers are reused
f. Press Ctrl-C to stop the flood.
g. Start a new Wireshark capture. Click Continue without Saving when prompted to save the capture. Apply the display filter that specifies the Kali VM as the source and the Raspberry Pi as the destination, as was done previously in this lab.
h. In the Kali VM terminal, enter the hping3 command to send a flood attack.
root@kali:~# hping3 --flood –-icmp -p 22 203.0.113.13
Look at Wireshark what type of ICMP messages are you seeing?
____________________________________________________________
Type 8 echo request
i. Press Ctrl-C to stop the flood.
j. Complete the following table for the hping3 options that you used in this lab. Use the hping3 man page or other information resources.
| Option | Name | Description |
|---|---|---|
| -8 | scan mode | scans a range of TCP ports on the target host address provided |
| -S | set SYN flag | sets the SYN flag in the TCP header of the packets to be sent |
| -1 | ICMP mode | sends ICMP echo request packet(s) unless another type of packet has been specified |
| -C | icmptype | used to set the ICMP packet type |
| –flood | N/A | send packets as fast as possible without waiting for replies |
| -a | spoof hostname | set a fake IP source address |
| -p | destport | specify destination TCP por |
| -s | baseport | specify TCP source port, or port at which to start a scan in which the port number is increased for each packet sent |
| -k | keep | retains the specified source port instead of incrementing it with each packet that is sent. |
