4.2.2.5 Lab – Port Scanning an IoT Device (Instructor Version)
Topology
Objectives
- Part 1: Perform a Nmap network discovery scan
- Part 2: Compare a Nmap TCP default port scan and full scan
- Part 3: Perform a Nmap UDP Scan
- Part 4: Perform Nmap OS and Service Foot Printing
Background / Scenario
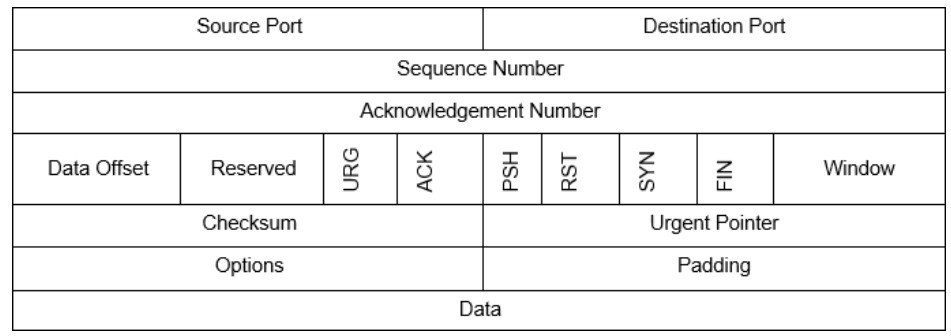
Nmap, or “Network mapper,” is a free and open source network port scanner. It can be used to test IoT devices and firewalls for open, closed, or filtered ports and additionally can provide an inventory of devices and services available on a network. Nmap uses the TCP header flag fields URG, ACK, PSH, RST, SYN, FIN, shown in the diagram, to accomplish its scans. It also uses other protocols such as UDP, ICMP and a built-in database of known OS and application signatures. Nmap is included with Kali, but can also be downloaded from https://nmap.org/. A comprehensive reference about how Nmap works and how it is used is available at the Nmap website.
Required Resources
- Raspberry Pi 3 Model B or later
- 8GB Micro SD card (minimum required)
- PC with IoTSec Kali VM
- Network connectivity between PC and Raspberry Pi
Part 1: Perform a Nmap Network Discovery Scan
Step 1: Use Kali to perform a host discovery scan.
The first step in network scanning is to discover the addresses of the hosts that are actually up on the network. This is because many network information gathering tasks, such as port scanning, are timeconsuming. Nmap first scans the network to identify the addresses of hosts that should be scanned in greater depth. Doing in-depth scans of an entire network of 254 hosts, for example, is unnecessary if only a fraction of those hosts are actually on and able to respond.
By default, Nmap conducts a scan of the network to generate a list of hosts that are available for further scanning. It then conducts a port scan of those hosts.
a. Set up the topology by connecting the Raspberry Pi to the PC.
b. Start the IoTSec Kali VM and log in.
c. Open a terminal and start the DHCP server on the Kali VM.
root@kali:~# lab_support_files/scripts/start_dhcp.sh
d. Verify that Kali VM is assigned an IP address on eth0.
root@kali:~# ifconfig
e. Open the man page for nmap in Kali VM and review the options that are available in Nmap.
root@kali:~# man nmap
Refer to the man page and complete the table below. There are many other resources available online to help you learn Nmap.
| Option | Name | Notes |
|---|---|---|
| -sL | list scan | Scans every address in the network or range of addresses. Uses reverse-DNS to attempt to discover the names of each host. |
| -sn | no port scan | Nmap will do host discovery scan, but will not do the normal port scan. |
| -Pn | no ping | Nmap does no host discovery at all. It conducts the normal port scan on all hosts in the network or range. |
| -n | no DNS resolution | Nmap skips the reverse DNS part of the host discovery process. This can speed up scanning drastically, and is useful when scanning LANs which usually don’t have DNS names provided to hosts. |
f. Perform a scan on your network by specifying the network address and bit mask.
root@kali:~# nmap 203.0.113.0/24
What is the IP address of the Raspberry Pi?
_____________________________________________________________
Answers will vary. The assigned IP address will be in the network of 203.0.113.0/24.
g. Sometimes a device would not reply to Nmap’s initial network discovery scan because of a firewall, IDS/IPS system etc. Instead of relying on the initial scan to discover hosts that are alive for further scanning, we can use Nmap to scan the network by assuming all hosts are alive.
root@kali:~# nmap -Pn 203.0.113.0/24
What is the IP address and MAC address of your Raspberry PI?
____________________________________________________________
Answers will vary.
Part 2: Compare a Nmap TCP Default Scan and Full Scan
Step 1: Using Wireshark to display Nmap scans
a. In a Kali VM terminal, start Wireshark. Wireshark is used to monitor the traffic while scanning the network using Nmap. Click OK for the warning message regarding running Wireshark as a root user.
root@kali:~# wireshark
b. Select the eth0 interface and click Capture to start capturing packets.
c. There can be a lot of traffic on the network. A display filter is applied to limit the number of captured packets displayed to just those that you are interested in. The interesting traffic is between the IP address of the Kali VM and the Raspberry Pi. Replace IP address of the Raspberry Pi with the IP address
Apply the following display filter in Wireshark using IP address of Kali VM as the source address and IP address of your Raspberry Pi as the destination address.
ip.src == 203.0.113.1 && ip.dst == 203.0.113.13
As an example in this lab, the IP address for the Raspberry Pi is 203.0.113.13.
Step 2: Nmap TCP default scan
a. In the terminal, enter the following command to start the Nmap scanning.
root@kali:~# nmap 203.0.113.13
After Nmap reports the result of the scan, stop the Wireshark capture. Click the arrow next to the display filter field to filter the results of the scan.
Review the Wireshark output. Which TCP flag is Nmap using to discover the open ports?
_____________________________________________________________
SYN
Notice the ports that are being tested. The default Nmap scan does not test all ports. How many ports does a default Nmap scan test? (Do a web search if necessary.)
_____________________________________________________________
Only 1,000 of the most common ports.
Look at the results of the nmap scan in the terminal. What ports are identified?
_____________________________________________________________
Answers may vary. Ports 22 and 80 should be open, but others may also be found.
Step 3: Nmap TCP full TCP port scan
a. Nmap by default only scan a limited number of TCP ports. We would like to scan all 65535 TCP ports.
b. Start a new Wireshark capture. Click Continue without Saving when prompted to save the capture. to start a new capture.
c. Enter the nmap command to scan all the TCP ports in Kali VM.
root@kali:~# nmap -p 1-65535 203.0.113.13
d. Watch the Wireshark capture screen. Notice you are sending TCP packets just as before, but the number of ports being scanned has increased.
e. Stop the Wireshark capture when finished and clear the filter.
Part 3: Perform a Nmap UDP scan
UDP Header Format
| Source Port | Destination Port |
| Length | Checksum |
Step 1: UDP scan with a new Wireshark filter.
a. Start a new Wireshark capture. Click Continue without Saving when prompted to save the capture.
b. Apply the following filter in Wireshark:
ip.src == 203.0.113.13 && udp
This will allow us to see the UDP traffic generated by nmap to the Raspberry PI. Notice in the UDP header above there are no flags. We can only send UDP packets and receive a possible “port unreachable or destination unreachable” message meaning the port is closed.
c. In the Kali VM terminal, enter the command nmap with -sU option scanning the IP address of your Raspberry Pi.
root@kail:~# nmap -sU -F 203.0.113.13
d. It will take a few minutes, but look at the Wireshark capture. As you scroll down the packets, you will see some “Destination unreachable” on different ports indicating the port is closed.
How many UDP ports are there? How many UDP ports does Nmap scan, by default? (Use web search as necessary.)
____________________________________________________________
There are 65,535 UDP ports. Nmap scans only the most commonly used 1,000.
What are the UDP ports that are open from the scan? What protocols use these UDP ports?
____________________________________________________________
Answers may vary. Ports 68 and 5353 are most likely. The bootp and Multicast DNS use these ports. These services are used by PL-App.
What is the meaning of the -F option? Try the same scan without the -F. What is the difference?
____________________________________________________________
The -F option stands for fast. Only the most common 100 ports are scanned. This makes the scan much faster.
e. Stop the Wireshark capture when finished and clear the filter.
Part 4: Perform Nmap OS and Service Foot Printing
Step 1: Use Nmap to find a device operating system.
Nmap can guess the operating system of a device based on its response to a series of TCP and UDP packets.
a. Start a new Wireshark capture. Click Continue without Saving when prompted to save the capture.
b. Apply the following filter in Wireshark using IP address of Kali VM as the source address and IP address of your Raspberry Pi as the destination address.
ip.src == 203.0.113.1 && ip.dst == 203.0.113.13
c. In the Kali VM terminal, enter the command nmap using the -O option scanning the IP address of your Raspberry Pi.
root@kali:~# nmap -O 203.0.113.13
What operating system did Nmap guess?
____________________________________________________________
Linux 3.2-4.8
Look at the packets in Wireshark. What protocols were used to determine the OS?
____________________________________________________________
Answers may vary. TCP, UDP, & ICMP
d. We can sometimes identify a device by looking at the time to live (TTL) field of a local ping response, which varies by device OS. See the table below:
| Operating System | TTL Response time |
|---|---|
| Cisco | 255 |
| Windows | 128 |
| Linux | 64 |
In the Kali VM terminal, enter the command to ping your Raspberry Pi with 4 ICMP packets.
root@kali:~# ping -c4 203.0.113.13
What is the response time? Is it consistent with the Nmap identification?
____________________________________________________________
The response time is 64 which is consistent with a Linux OS response.
e. Stop the Wireshark capture when finished.
Step 2: Use Nmap to find services versions
Nmap has a built-in database of about 2,200 well-known services that is used to help identify application service versions.
a. Start a new Wireshark capture. Click Continue without Saving when prompted to save the capture. Apply the same display filter as the previous step.
b. In the Kali VM, enter the nmap command with the -A option scanning the IP address of your Raspberry Pi.
root@kali:~# nmap -A 203.0.113.13
What are the identified applications running on the ports? Complete the table.
| Port Number | Application service identified |
|---|---|
| 22 | SSH-2.0-OpenSSH_7.4p1 |
| 80 | Tornado httpd 4.5.1 |
| 88 | nginx 1.10.3 |
| 89 | Node.js Express framework |
Answers may vary, but ports 22 and 80 should at least be open.
What is different in the port identification from the Nmap TCP scan in Part 2 of the lab and this application service scan? What implications does this have for IoT security?
_____________________________________________________________
In the normal TCP scan, only protocols are identified. In this scan, details about the running services are also shown. These details can be used to identify versions of software services that have well-known vulnerabilities.
What additional functions does this scan also perform?
_____________________________________________________________
Nmap also performs a traceroute, OS detection, and SSH details.
c. Stop the Wireshark capture when finished.
