1. Which two functions are provided by the upper layers of the OSI model? (Choose two.)
- placing electrical signals on the medium for transmission
- initiating the network communication process
- encrypting and compressing data for transmission
- segmenting and identifying data for reassembly at the destination
- choosing the appropriate path for the data to take through the network
2. Which is a function of the transport layer of the OSI model?
- routes data between networks
- converts data to bits for transmission
- delivers data reliably across the network using TCP
- formats and encodes data for transmission
- transmits data to the next directly connected device
3. An investment company has multiple servers that hold mission critical datThey are worried that ifsomething happens to these servers, they will lose this valuable information. Which type of plan isneeded for this company to help minimize loss in the event of a server crash?
- business security
- business continuity
- network maintenance
- service level agreement
4. Which two router parameters can be set from interface configuration mode? (Choose two.)
- IP address
- Telnet password
- hostname
- console password
- subnet mask
- enable secret password
5. Which common Layer 1 problem can cause a user to lose connectivity?
- incorrect subnet mask
- incorrect default gateway
- loose network cable
- NIC improperly installed
6. A DoS attack crippled the daily operations of a large company for 8 hours. Which two optionscould be implemented by the network administrator to possibly prevent such an attack in the future?(Choose two.)
- install security devices with IDS and IPS at the enterprise edge
- reset all user passwords every 30 days
- filter packets based on IP address, traffic pattern, and protocol
- deny external workers VPN access to internal resources
- ensure critical devices are physically secure and placed behind the demarc
7. A network administrator must define specific business processes to implement if a catastrophicdisaster prevents a company from performing daily business routines. Which portion of the networkdocumentation is the administrator defining?
- business security plan
- business continuity plan
- network solvency plan
- service level agreement
- network maintenance plan
8. A network administrator needs to configure Telnet access to a router. Which group of commandsenable Telnet access to the router?
- Router(config)# enable password class
Router(config)# line con 0
Router(config-line)# login
Router(config-line)# password cisco - Router(config)# ip host 192.168.1.1 NewYork
Router(config)# enable password cisco - Router(config)# line aux 0
Router(config-line)# login
Router(config-line)# password cisco - Router(config)# enable password class
Router(config)# line vty 0 4
Router(config-line)# login
Router(config-line)# password cisco
9. Which two types of information should be included in a business continuity plan? (Choose two.)
- maintenance time periods
- intrusion monitoring records
- offsite data storage procedures
- alternate IT processing locations
- problem resolution escalation steps
10. Which two devices protect a corporate network against malicious attacks at the enterprise edge ?(Choose two.)
- demarc
- IP security (IPSec)
- Data Service Unit (DSU)
- intrusion prevention system (IPS)
- intrusion detection system (IDS)
11. Which three steps must be performed to remove all VLAN information from a switch but retain therest of the configuration? (Choose three.)
- Remove all VLAN associations from the interfaces.
- Remove the 802.1q encapsulation from the interface
- Issue the command copy start run.
- Issue the command delete flash:vlan.dat.
- Issue the command erase start.
- Reload the switch.
12. Which two situations require a network administrator to use out-of-band management to change arouter configuration? (Choose two.)
- Network links to the router are down.
- No Telnet password has been configured on the router.
- The administrator can only connect to the router using SSH.
- The network interfaces of the router are not configured with IP addresses.
- Company security policy requires that only HTTPS be used to connect to routers.
13. A network manager wants to have processes in place to ensure that network upgrades do not affectbusiness operations. What will the network manager create for this purpose?
- business security plan
- business continuity plan
- service level agreement
- network maintenance plan
14. When searching for information about authentication methods and usernames of companypersonnel, where can a network administrator look?
- Business Continuity Plan
- Business Security Plan
- Network Maintenance Plan
- Service Level Agreement
15. Refer to the exhibit. Which statement is true about port Fa5/1?
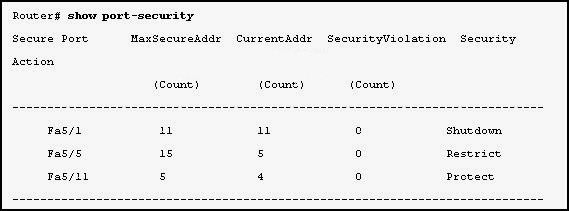
- When a violation is detected, the port will log the information to a syslog server.
- When a violation is detected, the port will go into err-disable mod
- There have been 11 security violations since the last reload
- The port is currently in the shutdown state.
16. What is the demarcation?
- physical point where the ISP responsibilty ends and the customer responsibilty begins
- physical location where all server farm connections meet before being distributed into the Core
- point of entry for outside attacks and is often vulnerable
- point of entry for all Access Layer connections from the Distribution Layer devices
17. What information can an administrator learn using the show version command?
- Cisco IOS filename
- configured routing protocol
- status of each interface
- IP addresses of all interfaces
18. It is crucial that network administrators be able to examine and configure network devices fromtheir homes. Which two approaches allow this connectivity without increasing vulnerability to externalattacks? (Choose two.)
- Configure a special link at the POP to allow external entry from the home computer.
- Set up VPN access between the home computer and the network.
- Install a cable modem in the home to link to the network.
- Configure ACLs on the edge routers that allow only authorized users to access management portson network devices.
- Configure a server in the DMZ with a special username and password to allow external access.
19. What type of connection point is a point of presence (POP)?
- between a client and a host
- between two local networks
- between a computer and a switch
- between an ISP and an Enterprise network
20. Which three command line utilities are most commonly used to troubleshoot issues at Layer 3? (Choose three.)
- ping
- a packet sniffer
- Telnet
- ipconfig
- Traceroute
21. Which address is used by the router to direct a packet between networks?
- source MAC address
- destination MAC address
- source IP address
- destination IP address
22. What is the correct encapsulation order when data is passed from Layer 1 up to Layer 4 of the OSI model?
- bits, frames, packets, segments
- frames, bits, packets, segments
- packets, frames, segments, bits
- segments, packets, frames, bits
23. What are two goals of the ISP help desk? (Choose two.)
- conserving support resources
- network optimization
- competitive scalability
- customer retention
- sales of network services
24. In what two ways do Level 1 and Level 2 help desk technicians attempt to solve a customer’s problems? (Choose three.)
- talking to the customer on the telephone
- upgrading hardware and software
- using various web tools
- making an onsite visit
- installing new equipment
- with remote desktop sharing applications
25. A customer calls the help desk about setting up a new PC and cable modem and being unable to access the Internet. What three questions would the technician ask if the bottom-up troubleshooting approach is used? (Choose three.)
- Is the NIC link light blinking?
- What is the IP address and subnet mask?
- Can the default gateway be successfully pinged?
- Is the network cable properly attached to the modem?
- Is the Category 5 cable properly connected to the network slot on the PC?
- Can you access your e-mail account?
26. A customer calls to report a problem accessing an e-commerce web site. The help desk technician begins troubleshooting using a top-down approach. Which question would the technician ask the customer first?
- Can you access other web sites?
- Is there a firewall installed on your computer?
- What is your IP address?
- Is the link light lit on your NIC card?
27. Which statement describes the process of escalating a help desk trouble ticket?
- The help desk technican resolves the customer problem over the phone and closes the trouble ticket.
- Remote desktop utilities enable the help desk technician to fix a configuration error and close the trouble ticket.
- After trying unsuccessfully to fix a problem, the help desk technician sends the trouble ticket to the onsite support staff.
- When the problem is solved, all information is recorded on the trouble ticket for future reference.
28. What are two functions of the physical layer of the OSI model? (Choose two.)
- adding the hardware address
- converting data to bits
- encapsulating data into frames
- signal generation
- routing packets
29. A customer calls the ISP help desk after setting up a new PC with a cable modem but being unable to access the Internet. After the help desk technician has verified Layer 1 and Layer 2, what are three questions the help desk technician should ask the customer? (Choose three.)
- What is your subnet mask?
- What is your IP address?
- Is the NIC link light blinking?
- Can you ping the default gateway?
- Is the network cable properly attached to the cable modem?
- Is the network cable correctly connected to the network port on the PC?
30. Which scenario represents a problem at Layer 4 of the OSI model?
- An incorrect IP address on the default gateway.
- A bad subnet mask in the host IP configuration.
- A firewall filtering traffic addressed to TCP port 25 on an email server.
- An incorrect DNS server address being given out by DHCP.
31. What are two basic procedures of incident management? (Choose two.)
- opening a trouble ticket
- using diagnostic tools to identify the problem
- surveying network conditions for further analysis
- configuring new equipment and software upgrades
- adhering to a problem-solving strategy
- e-mailing a problem resolution to the customer
32. Which level of support is supplied by an ISP when providing managed services?
- Level 1
- Level 2
- Level 3
- Level 4
33. What is the first step that is used by a help desk technician in a systematic approach to helping a customer solve a problem?
- identify and prioritize alternative solutions
- isolate the cause of the problem
- define the problem
- select an evaluation process
34. A network technician has isolated a problem at the transport layer of the OSI model. Which question would provide further information about the problem?
- Do you have a firewall that is configured on your PC?
- Do you have a link light on your network card?
- Is your PC configured to obtain addressing information using DHCP?
- What default gateway address is configured in your TCP/IP settings?
- Can you ping http://www.cisco.com?
35. An ISP help desk technician receives a call from a customer who reports that no one at their business can reach any websites, or get their e-mail. After testing the communication line and finding everything fine, the technician instructs the customer to run nslookup from the command prompt. What does the technician suspect is causing the customer’s problem?
- improper IP address configuration on the host
- hardware failure of the ISR used to connect the customer to the ISP
- bad cables or connections at the customer site
- failure of DNS to resolve names to IP addresses
36. Which layers of the OSI model are commonly referred to as the upper layers?
- application, presentation, session application, session, network
- presentation, transport, network
- presentation, network, data link
- session, transport, network
37. Which device is responsible for moving packets between multiple network segments?
- router
- switch
- CSU/DSU
- IDS device
