1. What are two advantages of using Layer 3 devices instead of Layer 2 switches at the distribution layer of a hierarchical network? (Choose two.)
- allows connectivity between different VLANs
- results in fewer IP subnets to configure and manage
- provides reliable connectivity to the end user
- reduces the number of required redundant links
- enables traffic filtering that is based on subnet addresses
2. Refer to the exhibit. What result can be expected for STP in VLAN1?
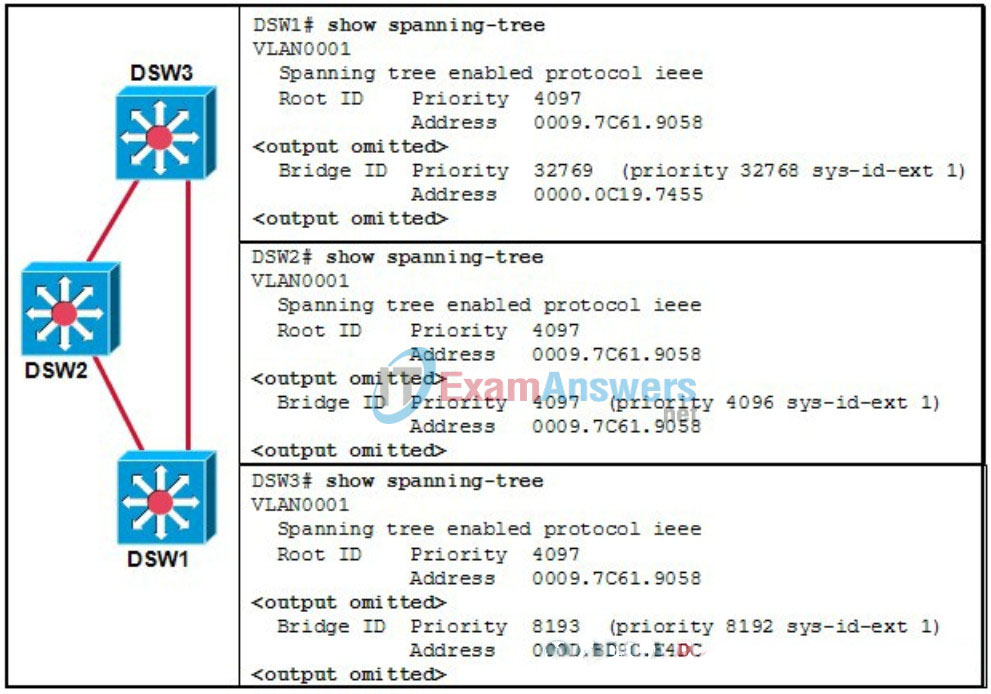
- DSW1 is the root bridge. DSW3 would become root upon failure of DSW1.
- DSW3 is the root bridge. DSW1 would become root upon failure of DSW3.
- DSW3 is the root bridge. DSW2 would become root upon failure of DSW3.
- DSW2 is the root bridge. DSW3 would become root upon failure of DSW2.
3. A network administrator needs to transfer an IOS image to a router using a TFTP server. What should be verified prior to beginning the transfer process?
- The TFTP server must connect to the router via a serial connection.
- The TFTP server and the router must be on different networks for the transfer.
- The TFTP server software must be the same version as the Cisco IOS software.
- Connectivity between the TFTP server and the router should have been established.
4. A web-based retail company is considering updating its WAN connection with new technologies that are offered by the ISP. What testing platform should be used by the network team of the company to validate the performance and capacity of the new technology using real world data?
- pilot
- prototype
- emulation software
- simulation software
5. A router has been removed from the network for maintenance. A new Cisco IOS software image has been successfully downloaded to a server and copied into the flash of the router. What should be done before placing the router back into service?
- Back up the new image.
- Restart the router and verify that the new image starts successfully.
- Copy the running configuration to NVRAM.
- Delete the previous version of the Cisco IOS software from flash.
6. To reduce unwanted incoming traffic from the outside, a network technician is tasked with establishing the filtering rules for the network firewall. Which traffic should be allowed?
- incoming ICMP traffic
- all incoming connections to internal servers
- incoming responses to traffic that is generated from the inside
- incoming connections from the outside that duplicate inside addresses
7. In configuring CHAP authentication for PPP, what is important to know about the format of usernames and passwords?
- Only the passwords are case sensitive.
- The usernames and passwords are case sensitive.
- Neither the usernames nor the passwords are case sensitive.
- The usernames are case sensitive but the passwords are not.
8. Refer to the exhibit. Before the encapsulation was changed to Frame Relay, the administrator verified physical connectivity by successfully pinging the remote router. After the encapsulation was changed, the administrator attempted to ping the remote router on the Frame Relay circuit but was not successful. A show frame-relay pvc command was issued. What could be the problem?
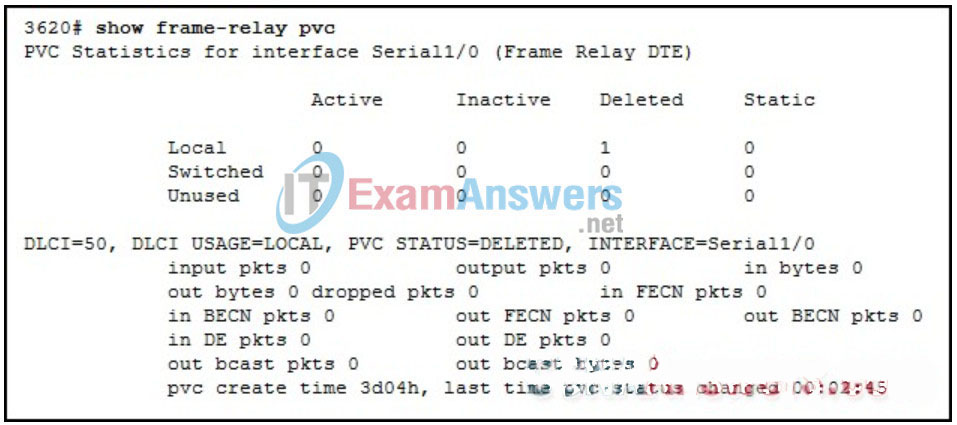
- The DLCI is incorrect.
- The IP address is incorrect.
- The interface needs to be re-enabled after the encapsulation is changed.
- The network is not included in the routing table.
9. Refer to the exhibit. A network technician wishes to allow all traffic to internal LANs except traffic from network 10.0.0.0/10 that enters the router on its leased-line Internet connection. What will be apparent once these commands are entered into the router?
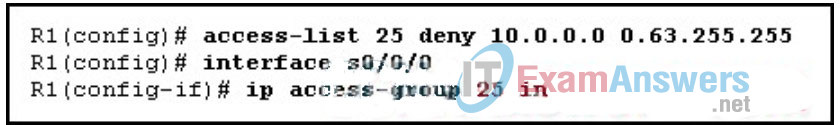
- The wild card mask is wrong.
- The required objective will have been achieved.
- All traffic that enters the router on s0/0/0 will be blocked.
- The access-list is applied in the wrong direction.
10. Which protocol allows redundant Layer 2 links without switching loops?
- DHCP
- RSTP
- HSRP
- MPLS
11. Refer to the exhibit. A pre-sales system engineer receives a diagram of the current WAN from a customer. EIGRP is the routing protocol that is used on the WAN. Based on the default operation of EIGRP, which statement is true about the routing table on router RE?
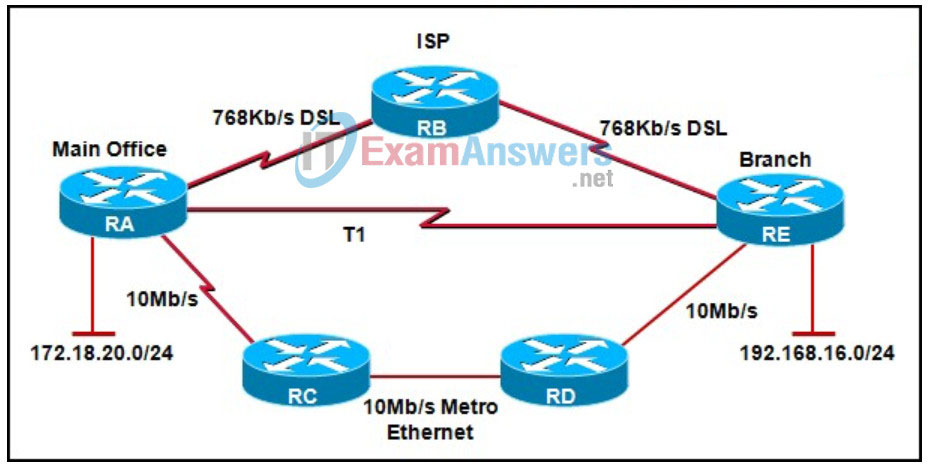
- There is a single route to the 172.18.20.0/24 LAN via the 10 Mb Ethernet connection.
- There is a single route to the 172.18.20.0/24 LAN via the T1 connection.
- There is a single route to the 172.18.20.0/24 LAN via the DSL connection.
- EIGRP installs all three routes to the 172.18.20.0/24 LAN and load balances the traffic.
12. A network designer must select a routing protocol for the network of a customer. The currently installed network contains both Cisco and non-Cisco routers, and there is no budget to replace them. The designer plans on implementing both VLSM and route summarization in the new network design. Which two protocols can provide the necessary functionality for this LAN? (Choose two.)
- RTP
- RSTP
- RIPv1
- EIGRP
- RIPv2
- OSPF
13. What are two suggested best practices to implement when securing network devices? (Choose two.)
- Configure VLAN 1 as the native VLAN.
- Disable unused ports on switches.
- Consolidate guest traffic and internal employee traffic.
- Enable SSH and disable Telnet.
- Ensure that logs are stored locally on routers.
14. When should a network designer specify that a dedicated firewall appliance be used at the perimeter of the network rather than a router with a Cisco IOS software-based firewall feature set?
- There are multiple servers in the DMZ.
- The network is large in size and network traffic can overload the device.
- Traffic filtering is needed on the internal network.
- Multiple levels of access to the network are needed.
15. What supports the ability of streaming video to be sent to a group of viewers simultaneously without congesting the entire network?
- traffic queues
- multicast
- multiple Layer 4 sessions
- high priority from QoS
16. During prototype testing, a LAN switch fails. As the switch re-initializes using the default parameters, a port that has a PC attached transitions to the forwarding state within one second. What protocol would support this feature?
- STP
- RIP
- BGP
- VTP
- RSTP
17. Refer to the exhibit. A customer has a problem with connectivity in the network. Based on the IP addressing scheme, what is causing the problem?
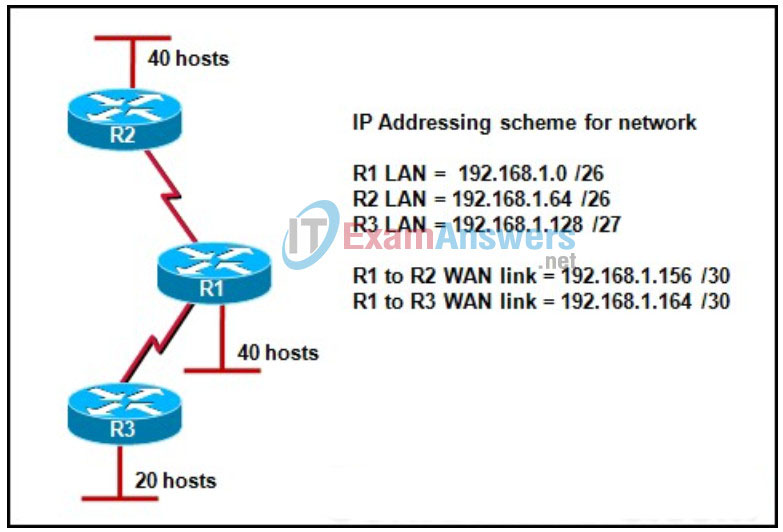
- The WAN link that connects R1 to R3 has an incorrect mask.
- The WAN links need IP addresses from a different major network.
- The WAN link that connects R1 to R2 overlaps with the R3 LAN.
- The IP addressing in R1 LAN is incorrect because subnet zero cannot be used with VLSM.
18. Refer to the exhibit. The routers are configured with RIPv2 with default configurations. When attempting to communicate with other networks, hosts from 10.0.11.0/24 are experiencing connectivity issues. What could be done to resolve this issue?
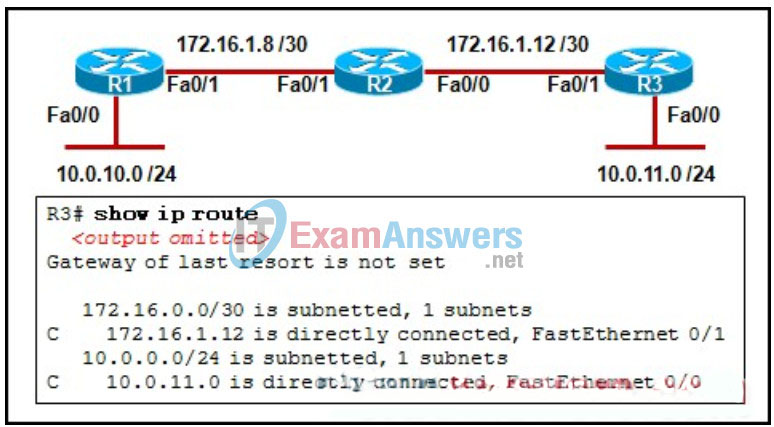
- Change to a public IP addressing scheme.
- Use EIGRP with its default configuration as the routing protocol.
- Change the subnet mask on the link between R2 and R3 to 255.255.255.0.
- Disable automatic route summarization on all routers in the network.
19. What are two accurate descriptors of a DLCI? (Choose two.)
- Frame Relay Layer 2 address
- one DLCI allowed per local loop
- locally significant circuit endpoint
- signaling standard between DTE and DCE
- establishes the data transfer rate through a Frame Relay network
20. What is meant by “tunneling” in the context of migrating from IPv4 to IPv6?
- obtaining IPv6 addresses from an IPv4 DHCP server
- allowing both protocol stacks to run on the same network device
- encapsulating one protocol packet within another protocol
- enabling direct communication between hosts that use different versions of the IP protocol
21. Refer to the exhibit. A network associate is configuring a new router to provide routing between VLANs. The associate removes the router from the box and connects the Fa0/0 interface to a trunking port on the switch. After the configuration is applied to the router, the traffic between VLANs still fails. What is causing this to occur?
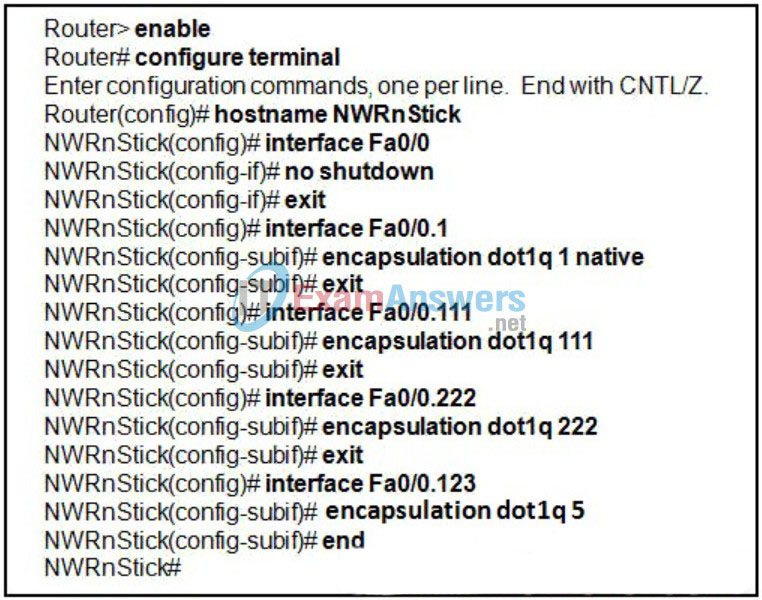
- The router needs a routing protocol configured.
- The router needs additional Fast Ethernet interfaces installed.
- All the subinterfaces of the router should be configured in the same VLAN.
- The subinterfaces must be the same value as the VLAN ID that they are routing for.
- The subinterfaces of the router should have IP addresses applied.
22. A school district decides to use the 172.30.0.0/16 network for its LAN networks. The network administrator must create an addressing scheme to support 500 users in the admin office, 200 at the high school, 60 at the elementary school and 28 at the district office. Which VLSM addressing scheme will correctly address the network with minimal waste?
- 172.30.0.0/20 admin
172.30.1.0/21 high school
172.30.1.8/22 elementary
172.30.1.12/26 district - 172.30.0.0/22 admin
172.30.4.0/23 high school
172.30.5.0/24 elementary
172.30.6.0/26 district - 172.30.0.0/23 admin
172.30.2.0/24 high school
172.30.3.0/26 elementary
172.30.3.64/27 district - 172.30.0.0/23 admin
172.30.2.0/24 high school
172.30.3.0/25 elementary
172.30.3.127/26 district
23. A company has just transitioned from traditional telephony to an IP Telephony solution for their voice requirements. What statement describes a characteristic of the new system?
- connects through a PBX to the PSTN
- replaces a digital system with an analog one
- combines data and voice into a converged network
- requires manual configuration for adding, moving or changing phones
- enables web applications and phone directories to be available to every PC on the network
24. The main office of a NetworkingCompany customer currently connects to three branch offices via three separate point-to-point T1 circuits. The customer network uses RIPv2 as the routing protocol within both the LAN and the WAN. The account manager proposes a change to a Frame Relay network because the costs are lower. A single local loop connection can be installed at the main office with three separate PVCs to connect the branch offices. How can the main office edge router be configured to enable the customer to continue to use RIP as the WAN routing protocol?
- Enable Inverse ARP on the serial interface in order to learn the routes to the IP addresses of the remote routers.
- To prevent the Frame Relay network from causing a routing loop, disable split horizon on the serial interface.
- Create three separate point-to-point subinterfaces on the serial interface and assign a different subnet IP address to each one.
- Configure the serial interface with a single interface DLCI number and create frame-relay map statements for each remote site address.
25. Refer to the exhibit. Based on the show cdp neighbors detail command, which interface on Switch1 is connected to Router1?
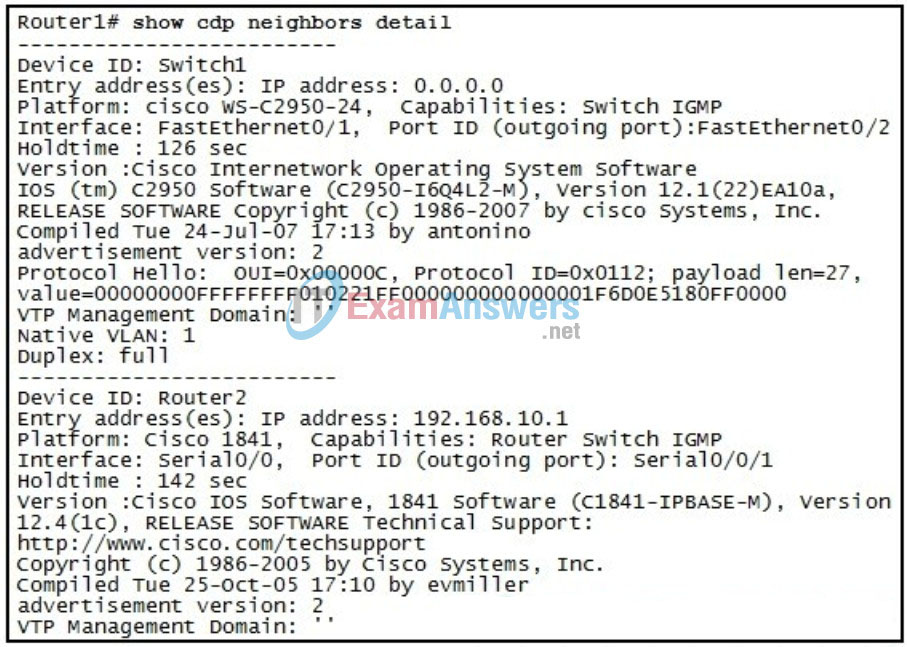
- FastEthernet0/1
- FastEthernet0/2
- Serial0/0
- Serial0/0/1
26. A network administrator is determining which network address can be assigned to a new remote site with thirty-one users. The logical topology documentation is referenced and it is concluded that the 172.24.32.0/19 and 172.24.128.0/25 address blocks are available. Which network address could be assigned to the new remote site while wasting the fewest addresses?
- 172.24.32.0/27
- 172.24.64.64/26
- 172.24.128.64/27
- 172.24.160.32/27
- 172.24.48.0/26
- 172.24.192.0/26
27. When designing a prototype network for a new server farm, a network designer chooses to use redundant links to connect to the rest of the network. Which business goal will be addressed by this choice?
- security
- scalability
- availability
- manageability
28. Refer to the exhibit. What is the purpose of this configuration?
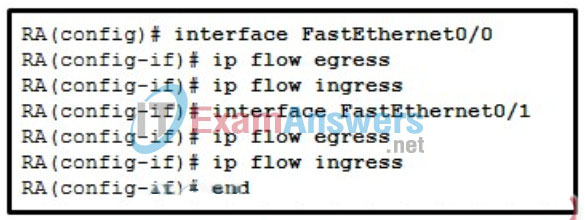
- auditing the network traffic with NBAR
- capturing network traffic to send to a syslog server
- applying the named ACLs egress and ingress to the Ethernet interfaces
- monitoring the network traffic with NetFlow
29. Which IOS command can a network designer use to help document the active routing status of an existing network?
- show ip route
- show vlan
- show running-config
- show cdp neighbors detail
30. What is a benefit of using CIDR to summarize multiple classful networks into a single network?
- It allows RIPv1 to function as a classless routing protocol.
- It reduces the number of entries in routing tables.
- It allows the routing protocol to define a more accurate best path selection.
- It increases the amount of information transmitted in routing protocol updates.
31. What is a characteristic of voice traffic in a converged network?
- It is assigned secondary priority to data traffic.
- It is processed in real time and cannot be retransmitted.
- It consists of large packets with long, irregular data flows.
- It uses the error-checking features of TCP to ensure good voice quality.
32. A customer has asked a network engineer to prototype the new IP addressing and summarization strategy for a large, multisite network implementation. Which tool is appropriate for testing the complete addressing scheme?
- Cisco SDM
- actual network equipment in a lab
- network simulation tool
- current network of the customer
33. A company has an IT staff that is not highly trained. What two features or technologies must the network designer identify as training needs in order for the staff to understand the basic operation of VPNs? (Choose two.)
- access control lists
- encryption algorithms
- Frame Relay configuration
- QoS operation
- tunneling protocols
- VLAN configuration
34. Refer to the exhibit. An extended ACL has been created to deny traffic from the 192.168.30.0/24 network to the web server with IP address 209.165.201.30. According to Cisco best practices, where should the ACL be applied?
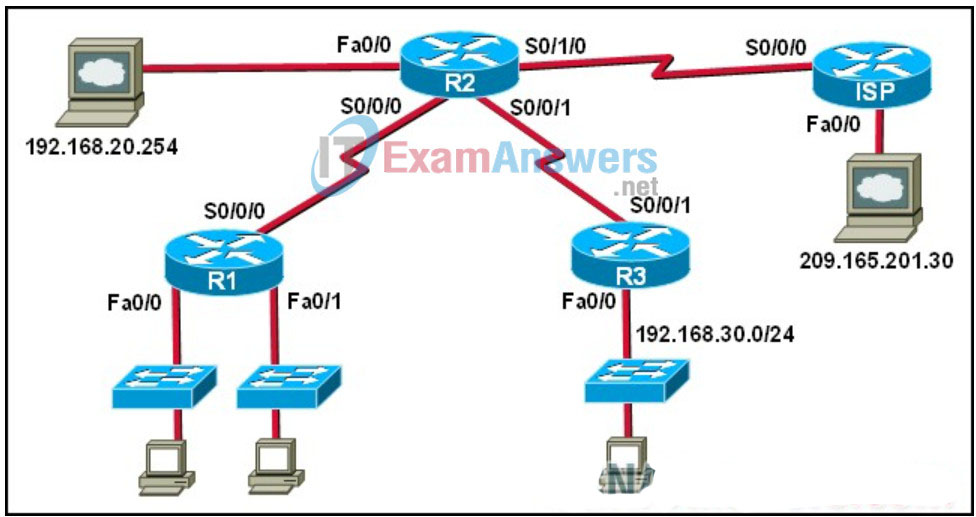
- R3 Fa0/0 inbound
- R3 S0/0/1 outbound
- R2 S0/0/1 inbound
- ISP Fa0/0 outbound
35. Which IOS component can be used for classification and protocol discovery of network traffic and applications in use?
- CDP
- NBAR
- ACL logging
- Network Assistant
36. While troubleshooting a Frame Relay link, the network administrator executes the show ip interface brief command on both sides of the PVC link. All interfaces show a configured IP address and that the line protocol is up. Further investigation reveals that the IP address of the remote router does not appear in the Frame Relay table. Which step would solve this problem?
- Change the LMI type on the local router.
- Verify that the DLCI number is the same on both sides of the PVC.
- Configure the router using the frame-relay map ip command.
- Verify that the remote router has Frame Relay encapsulation enabled.
37. During a review of the proposed bill of materials, the ABC Networking Company account manager realizes that the systems engineer included a lower cost, less capable switch model for the access layer connectivity than was specified by the network designer. When questioned, the systems engineer responds that the switches that were recommended by the designer cannot be purchased within the budget limitations of the customer. Which action should the account manager take?
- Inform the customer that the project cannot be completed given the unreasonable budget constraints.
- Communicate any risks that are associated with the equipment substitution and obtain customer approval to proceed.
- Because the customer is probably aware that the budget limitations will require lower cost, less capable equipment, the account manager should do nothing.
- Inform the customer that the project budget must be increased.
38. After a WIC is installed in a two-slot router, the network engineer issues the show running-config command, but the newly installed interfaces in the WIC cannot be seen in the router output. What is a possible reason why the newly installed interfaces are not shown?
- The new interfaces are in a shutdown state.
- The WIC was put into slot 0 instead of slot 1.
- The WIC was not pushed completely into the slot.
- The show running-config command cannot be used to validate the presence of installed interfaces.
39. What is the advantage of choosing EasyVPN for a new VPN implementation?
- to provide encryption algorithms unavailable in other systems
- to ensure that remote workers actually use the VPN for connectivity
- to allow a greater variety of network devices to be used for VPN connections
- to simplify the configuration tasks for the device that is used as the VPN server
40. A small bookstore would like to offer wireless connectivity for customers with laptops. Which wireless components or devices will provide connectivity to the Internet for the customers with the least possible cost to the bookstore?
- wireless LAN controllers
- wireless network cards for an ad hoc WLAN
- lightweight access point and wireless LAN controller
- standalone access points
41. While configuring a router with EIGRP, a technician enters the EIGRP command:
Router(config-router)# variance 3
What is the effect of entering this command?
- It enables unequal cost load balancing.
- It adjusts the cost of all EIGRP routes to 3.
- It restricts the number of EIGRP feasible successor routes to 3.
- It enables EIGRP equal cost load balancing over a maximum of 3 routes.
42. A configuration file needs to be loaded into the RAM of a router from a TFTP server. What should an administrator know before accomplishing this task?
- the TFTP server IP address and the name of the configuration file on the server
- the router IP address and the operating system that is used by the TFTP server
- the router IP address and the name of the router configuration file in NVRAM
- the TFTP server IP address and the value of the configuration register on the router
43. What best describes the function of QoS in data networks?
- provides preferred service to specified network traffic
- prioritizes data traffic over all other types of traffic
- increases bandwidth on a link to ensure voice quality
- automatically assigns the highest priority to web and database traffic
44. What can be broadcast over the wireless network to help a user connect to the network and use wireless services?
- WPA encryption keys
- voice VLAN parameters
- IP address of the access point
- SSID
- management VLAN parameters
45. What is the main purpose of the access layer in a hierarchically designed network?
- perform routing and packet manipulation
- supply redundancy and failover protection
- provide a high-speed, low-latency backbone
- serve as a network connection point for end-user devices
46. What is the result of implementing a Frame Relay service with a CIR value of zero?
- Data will not cross the Frame Relay WAN.
- All frames that enter the Frame Relay WAN will be marked as DE.
- Only frames that exceed the local access rate will be marked as DE.
- CIR is disabled, which allows all data traffic to pass through the Frame Relay WAN.
47. Which component in a Frame Relay WAN would set the BECN bit in the Frame Relay header if congestion is experienced?
- source DTE device
- Frame Relay switch
- destination DTE device
- router through which communication was first initiated
48. Refer to the exhibit. Following a test plan, the network systems engineer completes the configuration of an access layer switch and connects three PCs to test the configuration. The engineer attempts to ping from each PC to the other connected PCs. Which three statements describe the expected results of pinging from one host to another? (Choose three.)
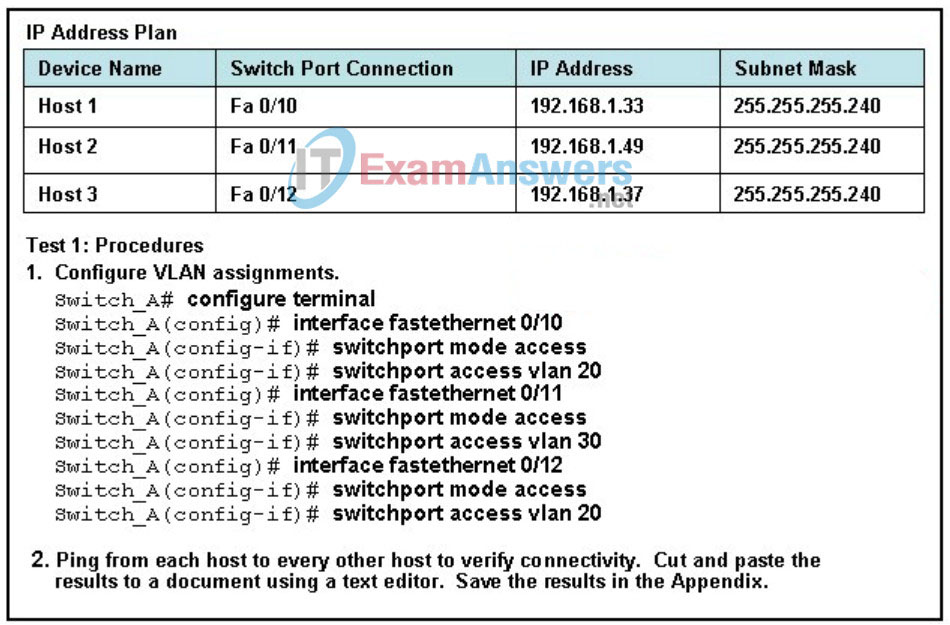
- Host 1 can ping Host 2.
- Host 1 cannot ping Host 2.
- Host 2 cannot ping Host 3.
- Host 3 can ping Host 1.
- Host 3 can ping Host 2.
- Host 3 cannot ping Host 1.
49. An HWIC-4ESW, four-port switch module needs to be installed in a Cisco 1841 router that currently has a WIC-2T module in slot 0. What should the network technician do first?
- Install the hot-swappable option module.
- Turn off the power to the router before installing the new module.
- Remove the WIC-2T module so that the new module can be installed in slot 0.
- Shut down all Fast Ethernet ports on the router until the switch module installation is complete.
- Configure the Cisco IOS software to support an internal trunk link between the switch and router module.
50. Refer to the exhibit. A NetworkingCompany designer is reviewing a diagram of a customer network. What two risks or issues can be identified in the topology that is shown? (Choose two.)
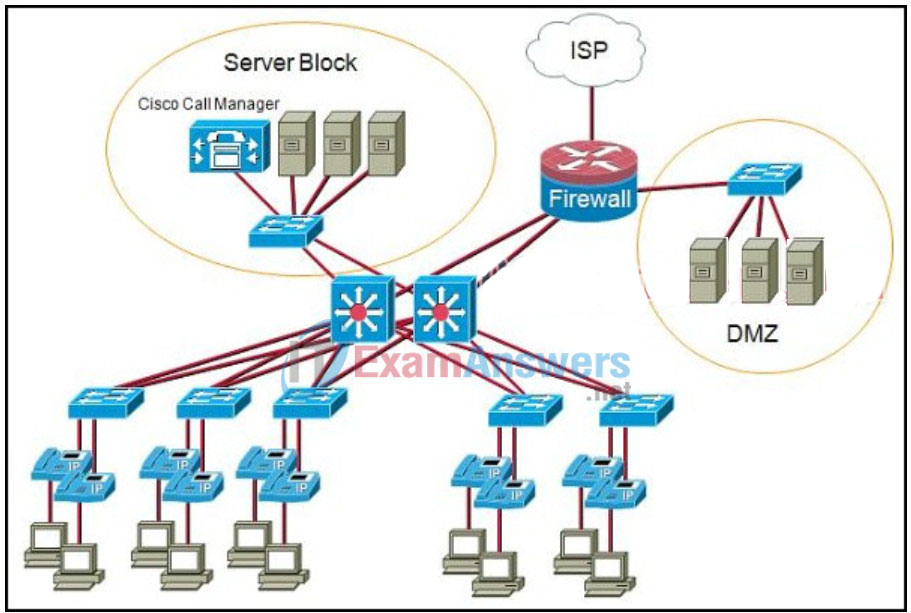
- The firewall router and ISP connection represent a single point of failure.
- A failure of the switch that connects the Cisco Call Manager to the network will cause the entire IP telephony system to fail.
- Using Layer 3 switches to interconnect the data center servers to the IP phones introduces too much delay.
- The IP phones need to be redundantly connected to the switches to prevent single points of failure at the access layer.
- If one of the Layer 3 switches fails, the Cisco Call Manager will be unreachable.
