1. A company is developing an Internet store for its website. Which protocol should be used to transfer credit card information from customers to the company web server?
- FTPS
- HTTP
- HTTPS
- WEP2
- TFTP
2. Refer to the exhibit. A new branch office has been added to the corporate network and a new router is to be installed to allow branch office users to access the database server at headquarters. How should the serial 0/0/0 interface of the new branch office router be configured to connect to the headquarters router?
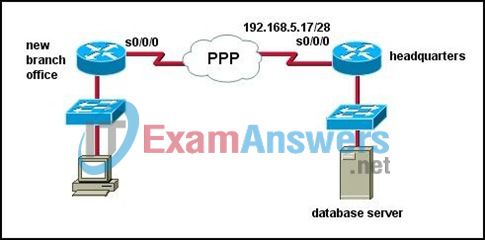
- branch_23(config-if)# ip address 192.168.5.19 255.255.255.240
branch_23(config-if)# no shutdown - branch_23(config-if)# encapsulation hdlc
branch_23(config-if)# ip address 192.168.5.25 255.255.255.240
branch_23(config-if)# no shutdown - branch_23(config-if)# encapsulation ppp
branch_23(config-if)# no shutdown - branch_23(config-if)# encapsulation ppp
branch_23(config-if)# ip address 192.168.5.33 255.255.255.240 - branch_23(config-if)# encapsulation ppp
branch_23(config-if)# ip address 192.168.5.21 255.255.255.240
branch_23(config-if)# no shutdown
3. Which two commands ensure that any password that permits access to the privileged EXEC mode is not shown in plain text when the configuration files are displayed? (Choose two.)
- Router(config)# enable secret cisco
- Router(config)# enable cisco
- Router(config)# encryption-password all
- Router(config)# enable login encrypted
- Router(config)# enable password encryption
- Router(config)# service password-encryption
4. A new network is to be configured on a router. Which of the following tasks must be completed to configure this interface and implement dynamic IP routing for the new network? (Choose three.)
- Select the routing protocol to be configured.
- Assign an IP address and subnet mask to the interface.
- Update the ip host configuration information with the device name and new interface IP address.
- Configure the routing protocol with the new network IP address.
- Configure the routing protocol with the new interface IP address and subnet mask.
- Configure the routing protocol in use on all other enterprise routers with the new network information.
5. How does TCP ensure the reliable transfer of data?
- If data segments are not received from the source, the destination requests that the segments be resent.
- If an acknowledgment of the transmitted segments is not received from the destination in a predetermined amount of the time, the source resends the data.
- TCP uses the SYN-ACK portion of the three-way handshake to ensure that all data has been received.
- The TCP Protocol Interpreter process verifies the transmitted data at source and destination.
6. A network administrator is asked to design a system to allow simultaneous access to the Internet for 250 users. The ISP for this network can only supply five public IPs. What can be used to accomplish this task?
- routable translation
- dynamic translation
- static translation
- port address translation
7. What is the most commonly used exterior routing protocol?
- BGP
- RIP
- OSPF
- EIGRP
8. Refer to the exhibit. The network administrator needs to configure the router with a name. Which command will the administrator use to configure the router name?
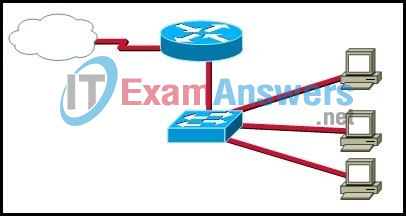
- Router# ip hostname Boise
- Router# enable hostname Boise
- Router(config-line)# name Boise
- Router(config)# hostname Boise
- Router(config)# ip hostname Boise
9. Why are port numbers included in the TCP header of a segment?
- to indicate the correct router interface that should be used to forward a segment
- to identify which switch ports should receive or forward the segment
- to determine which Layer 3 protocol should be used to encapsulate the data
- to enable a receiving host to forward the data to the appropriate application
- to allow the receiving host to assemble the packet in the proper order
10. What is the purpose of the routing process?
- to encapsulate data that is used to communicate across a network
- to select the paths that are used to direct traffic to destination networks
- to convert a URL name into an IP address
- to provide secure Internet file transfer
- to forward traffic on the basis of MAC addresses
11. Which two statements are true about the use of the debug ip rip command on a Cisco router? (Choose two.)
- The debug ip rip command displays RIP routing activity in real time.
- The debug ip rip command can be issued at the user EXEC configuration mode.
- The debug ip rip command displays a combination of the information that is displayed by the show ip route and show ip protocols commands.
- Because of router processor usage, the debug ip rip command should be used only when necessary.
- The debug ip rip command should be used instead of the show ip route command whenever possible.
12. What minimum configurations must be set on a host to allow a request to be sent to http://www.cisco.com/? (Choose four.)
- DNS server
- WINS server
- IP address
- NetBIOS
- subnet mask
- default gateway
13. A Catalyst 2960 switch has been taken out of storage to be used as a temporary replacement for another switch that needs to be repaired. About a minute after the switch has started, the SYST LED on the front of the switch transitions from blinking green to amber. What is the meaning of the amber SYST LED?
- The switch has no configuration file in NVRAM.
- The switch has failed POST and must be sent for service.
- The switch is functioning properly.
- The switch is in half-duplex mode.
14. Refer to the exhibit. Which combination of cables and symbols is correct?
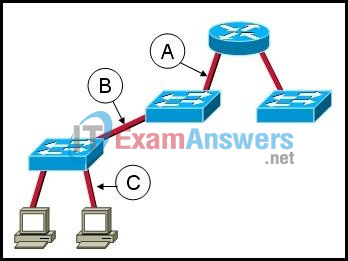
- A – crossover, B – straight-through, C – straight-through
- A – crossover, B – rollover, C – straight-through
- A – straight-through, B -crossover, C – straight-through
- A – straight-through, B -straight-through, C – straight-through
- A – straight-through, B – straight-through, C – crossover
- A – rollover, B – straight-through, C – straight-through
15. After an unsuccessful ping to the local router, the technician decides to investigate the router. The technician observes that the lights and fan on the router are not operational. In which layer of the OSI model is the problem most likely occurring?
- transport
- network
- data link
- physical
16. What are three characteristics of the TCP protocol? (Choose three.)
- exchanges datagrams unreliably
- is used to send IP error messages
- forces the retransmission of unacknowledged packets
- creates a virtual session between end-user applications
- carries the IP address of the destination host in the TCP header
- is responsible for breaking messages into segments and reassembling them at their destination
17. Refer to the exhibit. The network shown is connected using services from the same ISP. How will the Fohi router dynamically learn routes to the 192.168.16.16/28, 192.168.16.32/28, and 192.168.16.64/28 subnetworks?
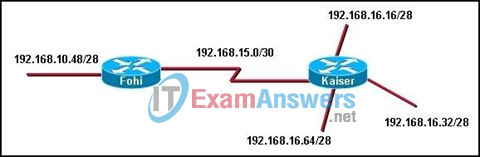
- with BGP
- with a static route
- with a directly connected route
- with an interior routing protocol
18. Refer to the exhibit. Which type of UTP cable should be used to connect Host A to Switch1?

- rollover
- console
- crossover
- straight-through
19. When customers use credit cards to make purchases at a small business, a modem is heard dialing a telephone number to transfer the transaction data to the central office. What type of WAN serial connection is in use?
- leased line
- packet switched
- circuit switched
- point-to-point
20. A user reports being unable to access the Internet. The help desk technician employs a bottom-up approach to troubleshooting. The technician first has the user check the patch cable connection from the PC to the wall, and then has the user verify that the NIC has a green link light. What will the technician have the user do next?
- Enter an IP address into the WWW browser address bar to see if DNS is at fault.
- Use traceroute to identify the device along the path to the ISP that may be at fault.
- Verify the IP address, subnet, and gateway settings using ipconfig on the PC.
- Connect to the user home router to check firewall settings for blocked TCP ports.
21. A ping 192.1.1.20 command is issued on workstation A to determine if workstation B can be reached. What events will occur if this command is successful? (Choose two.)
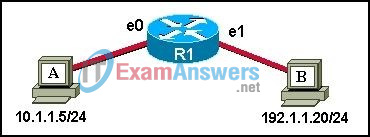
- The router will block the ping request message.
- The router will reply to the echo request with a proxy ping response.
- Workstation A will send a UDP ping request message to workstation B.
- Workstation B will send a UDP ping reply message to workstation A.
- Workstation A will send an ICMP echo request message to workstation B.
- Workstation B will send an ICMP echo reply message to workstation A.
22. How does a router know of paths to destination networks? (Choose two.)
- inspection of the destination IP address in data packets
- ARP requests from connected routers
- manual configuration of routes
- updates from other routers
- DHCP information broadcasts
- updates from the SMTP management information base
23. Refer to the exhibit. Which two statements describe the data conversation shown? (Choose two.)
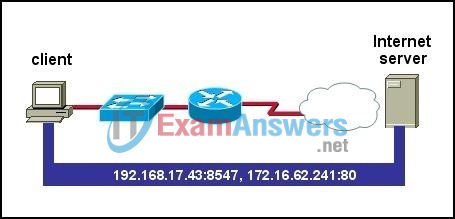
- The data conversation was started by the HTTP application process running on the client.
- The data conversation is identified by TCP port 80 on the client.
- The user started the data conversation by sending an e-mail.
- The IP address of the Internet server is 192.168.17.43.
- The Internet server will send data to port 8547 on the client.
24. What is one purpose of the TCP three-way handshake?
- sending echo requests from the source to the destination host to establish the presence of the destination
- determining the IP address of the destination host in preparation for data transfer
- requesting the destination to transfer a binary file to the source
- synchronizing sequence numbers between source and destination in preparation for data transfer
25. Which type of address is 192.168.17.111/28?
- host address
- network address
- broadcast address
- multicast address
26. A customer reports connectivity problems to an ISP technician. Upon questioning the customer, the technician discovers that all network applications are functioning except for FTP. What should the technician suspect is the problem?
- misconfigured firewall
- bad port on switch or hub
- misconfigured IP addressing on the customer’s workstation
- wrong DNS server configured on the customer’s workstation
- wrong default gateway configured on the customer’s workstation
27. The show ip route command was executed on one of the routers shown in the graphic and the following output was displayed:
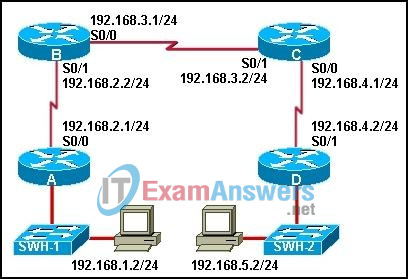
C 192.168.4.0/24 is directly connected, Serial0/0 R 192.168.5.0/24 [120/1] via 192.168.4.2, 00:00:19, Serial0/0 R 192.168.1.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1 R 192.168.2.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1 C 192.168.3.0/24 is directly connected, Serial0/1
From which router was this command executed?
- A
- B
- C
- D
28. Refer to the exhibit. Which two sets of commands are required to configure passwords for all management ports on a Catalyst 2960 switch? (Choose two.)
- ALSwitch(config)# interface vlan 1
ALSwitch(config-if)# password cisco
ALSwitch(config-if)# login - ALSwitch(config)# line vty 0 4
ALSwitch(config-line)# password cisco
ALSwitch(config-line)# login - ALSwitch(config)# line vty 0 15
ALSwitch(config-line)# password cisco
ALSwitch(config-line)# login - ALSwitch(config)# enable secret class
ALSwitch(config)# enable password cisco
ALSwitch(config)# interface fa0/1
ALSwitch(config-if)# password cisco
ALSwitch(config-if)# no shutdown - ALSwitch(config)# line cons 0
ALSwitch(config-line)# password cisco
ALSwitch(config-line)# login
29. A user reports being able to access the Internet but not being able to download e-mail from the mail server at the ISP. What should the user check on the user workstation?
- the POP3 and SMTP server settings in the e-mail application
- the patch cable connections at the back of the workstation and at the wall plate
- the DHCP settings in the operating system
- the IP address, mask, and default gateway values
- the NIC drivers
30. Refer to the graphic. Which command will configure a static route on Router A to direct traffic from LAN A that is destined for LAN C?
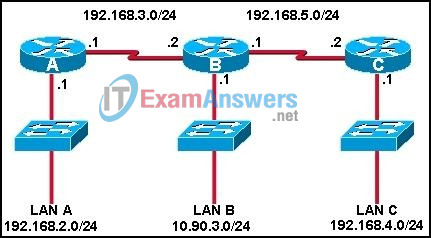
- RouterA(config)# ip route 192.168.4.0 255.255.255.0 192.168.5.2
- RouterA(config)# ip route 192.168.4.0 255.255.255.0 192.168.3.2
- RouterA(config)# ip route 192.168.5.0 255.255.255.0 192.168.3.2
- RouterA(config)# ip route 192.168.3.0 255.255.255.0 192.168.3.1
- RouterA(config)# ip route 192.168.3.2 255.255.255.0 192.168.4.0
31. Which subnet masks could be used when subnetting a Class B IP address? (Choose two.)
- 255.255.255.240
- 255.255.192.0
- 255.255.0.0
- 255.192.0.0
- 240.0.0.0
- 255.0.0.0
32. Refer to the exhibit. The network administrator has configured the RTA and RTB interfaces. In order to allow hosts that are attached to RTA to reach the server that is attached to RTB, a static route from RTA to the server LAN and a default route from RTB back to RTA need to be configured. Which two commands will the administrator use to accomplish these tasks on the two routers? (Choose two.)
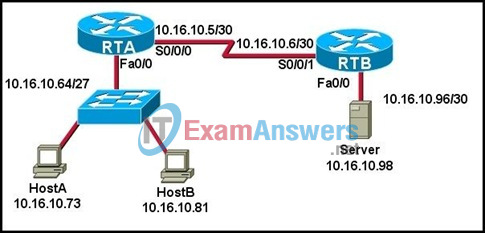
- RTA(config)# ip route 10.16.10.5 255.255.255.252 10.16.10.6
- RTA(config)# ip route 0.0.0.0 0.0.0.0 10.16.10.6
- RTA(config)# ip route 10.16.10.96 255.255.255.252 10.16.10.6
- RTB(config)# ip route 10.16.10.6 255.255.255.248 10.16.10.6
- RTB(config)# ip route 0.0.0.0 0.0.0.0 S0/0/1
- RTB(config)# ip route 0.0.0.0 0.0.0.0 10.16.10.6
33. How do port filtering and access lists help provide network security?
- They prevent specified types of traffic from reaching specified network destinations.
- They alert network administrators to various type of denial of service attacks as they occur.
- They prevent viruses, worms, and Trojans from infecting host computers and servers.
- They enable encryption and authentication of confidential data communications.
34. Refer to the exhibit. The network administrator of the building in the graphic needs to choose the type of cable best suited to add ServerB to the network. Which cable type is the best choice?
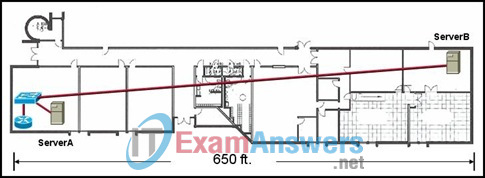
- STP
- UTP
- coaxial
- fiber optic
35. What is used by a routing protocol to determine the best path to include in the routing table?
- Convergence time
- Default distance
- Metric
- Type of router
36. Refer to the exhibit. Which IP addresses could be assigned to the hosts in the diagram? (Choose two.)
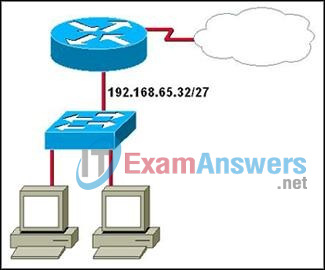
- 192.168.65.31
- 192.168.65.32
- 192.168.65.35
- 192.168.65.60
- 192.168.65.63
- 192.168.65.64
37. Given the network 192.168.25.0 shown in the graphic, which subnet mask would accommodate the number of hosts in each subnet?

- 255.255.0.0
- 255.255.224.0
- 255.255.255.0
- 255.255.255.224
- 255.255.255.240
- 255.255.255.248
38. Which two protocols allow network devices to report their status and events to a centralized network management device? (Choose two.)
- Syslog
- Telnet
- HTTP
- HTTPS
- SNMP
39. What is true regarding the differences between NAT and PAT?
- PAT uses the word “overload” at the end of the access-list statement to share a single registered address.
- Static NAT allows an unregistered address to map to multiple registered addresses.
- Dynamic NAT allows hosts to receive the same global address each time external access is required.
- PAT uses unique source port numbers to distinguish between translations.
40. Refer to the exhibit. The graphic shows the output of a command issued on router RTB. According to the output, what two statements are true of router RTB? (Choose two.)
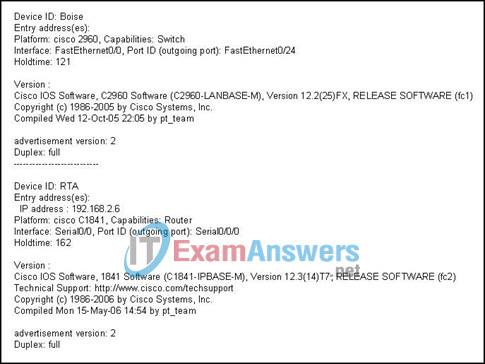
- The router is connected to a router named Boise.
- Router RTB is connected to a Cisco 1841 router.
- Router RTB is directly connected to two other routers.
- The IP address of the router interface connected to router RTB is 192.168.2.6.
- The RTB router is connected to two Cisco devices by Fast Ethernet links.
41. Refer to the exhibit. The network administrator uses the command below to configure a default route to the ISP network :
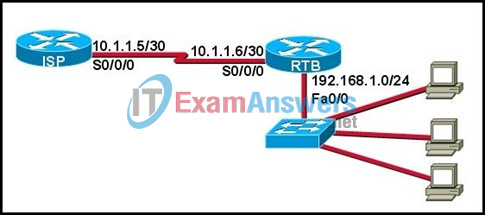
RTB(config)# ip route 0.0.0.0 0.0.0.0 10.1.1.6
A ping issued from the ISP is successful to router RTB. However, ping echo request packets arrive at a host that is attached to the Fa0/0 interface of RTB, and the replies do not make it back to the ISP router. What will fix this problem?
- The ISP must be configured to forward packets from the 192.168.1.0 network.
- The ip route command needs to be edited so that the next hop address is 10.1.1.5.
- The ip route command needs to be edited so that the 192.168.1.1 address is the next hop address.
- The ip route command should be removed from the RTB router configuration.
42. A network technician is using a network management station to gather data about the performance of devices and links within the ISP. Which application layer protocol makes this possible?
- SNMP
- FTP
- DHCP
- SMTP
43. What are two purposes of DNS? (Choose two.)
- to dynamically assign IP addressing information to network hosts
- to simplify the administration of host and default gateway addressing on client computers
- to assign TCP port numbers to hosts as part of the data transfer process
- to resolve human-readable domain names to numeric IP addresses
- to replace the static HOSTS file with a more practical dynamic system
44. A hacker attempts to reach confidential information that is stored on a server inside the corporate network. A network security solution inspects the entire packet, determines that it is a threat, and blocks the packet from entering the inside network. Which security measure protected the network?
- an IDS
- an IPS
- a host-based firewall
- Anti-X software
45. How many host addresses may be assigned on each subnetwork when using the 130.68.0.0 network address with a subnet mask of 255.255.248.0?
- 30
- 256
- 2046
- 2048
- 4094
- 4096
46. In an IPv4 environment, what information is used by the router to forward data packets from one interface of a router to another?
- destination network address
- source network address
- source MAC address
- well known port destination address
47. A small tire retailer requires a low-cost WAN connection to its headquarters in order to manage its inventory and process customer sales in real time. Which WAN connection type is best suited to its needs?
- Sonet
- T3
- dialup
- DSL
- leased line
48. The command copy tftp running-config has been entered on the router. What will this command do?
- copy the configuration in RAM to a server
- copy the configuration file from a server to RAM
- copy the configuration file in NVRAM to RAM
- copy the configuration file in NVRAM to a server
- copy the configuration file from a server to NVRAM
49. Refer to the exhibit. The network administrator needs to configure the Fa0/0 interface of RTB so that hosts from RTA can connect to the server that is attached to RTB. Which two commands will the administrator use to accomplish this task? (Choose two.)
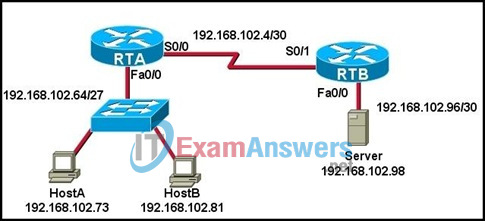
- RTB# ip address 192.168.102.98 255.255.255.248
- RTB(config-if)# ip address 192.168.102.99 255.255.255.252
- RTB(config)# ip address 192.168.102.97 255.255.255.252
- RTB(config)# no shutdown
- RTB(config-if)# no shutdown
- RTB(config-if)# ip address 192.168.102.97 255.255.255.252
50. Refer to the exhibit. A NOC technician at an ISP enters the command shown. What are two reasons to use this command? (Choose two.)

- to map the path to 192.168.1.7
- to test reachability to 192.168.1.7
- to locate connectivity problems along the route to 192.168.1.7
- to identify the ISPs that interconnect the NOC with the remote host with the address 192.168.1.7
- to measure the time that packets take to reach 192.168.1.7 and return to the technician’s workstation
51. Refer to the exhibit. A pre-sales system engineer receives a diagram of the current network WAN connectivity from a customer. EIGRP is the routing protocol used on the WAN. Based on the default operation of EIGRP, which statement is true about the routing table on router R1?
- There is a single route to the 192.168.16.0/28 LAN via the use of the T1 connection.
- There is a single route to the 192.168.16.0/28 LAN via the use of the DSL connection.
- There is a single route to the 192.168.16.0/28 LAN via the use of the Metro Ethernet connection.
- EIGRP installs all three routes to the 192.168.16.0/28 LAN and load balances the traffic.
52. A new host needs to be connected to VLAN 1. Router RA is attached to the VTP trunk and configured as shown in the output contained in the graphic. Which of the following IP addresses should be assigned to this new host?
- 192.168.1.1 /26
- 192.168.1.11 /28
- 192.168.1.22 /28
- 192.168.1.33 /28
- 192.168.1.44 /28
- 192.168.1.55 /28
53. Refer to the exhibit. A Networking Company designer is reviewing a diagram of a customer network. What two risks or issues can be identified in the topology that is shown? (Choose two.)
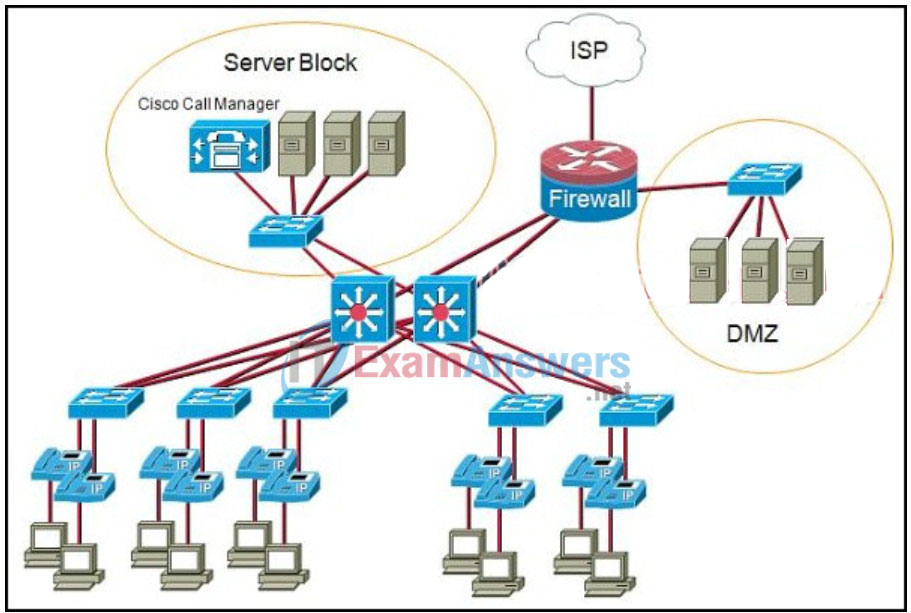
- The firewall router and ISP connection represent a single point of failure.
- A failure of the switch that connects the Cisco Call Manager to the network will cause the entire IP telephony system to fail.
- Using Layer 3 switches to interconnect the data center servers to the IP phones introduces too much delay.
- The IP phones need to be redundantly connected to the switches to prevent single points of failure at the access layer.
- If one of the Layer 3 switches fails, the Cisco Call Manager will be unreachable.
54. An engineer who is part of a sales team has been asked to select technologies and equipment capabilities to meet the network requirements of the prospective client. The engineer is also responsible for diagramming the placement and interconnection of various network devices and services. Which role is this engineer performing?
- post-sales field engineer
- account manager
- pre-sales engineer
- network designer
55. Refer to the exhibit. Two network engineers are setting up a prototype network to test a new Frame Relay network design. One of the engineers connects the cables and powers up all of the devices per the test plan. The second engineer uses a console cable to connect to the BR1 router, configures the Frame Relay connection and issues a show interfaces serial 2/0 command. What does the output of this command indicate to the engineers?
- A no shutdown command must be entered on the interface.
- The IP address has not yet been configured on the interface.
- The WAN encapsulation method is incorrect on the interface.
- The cable that connects BR1 to FR2 may not be correct or is not connected properly.
56. After an administrator installs a WIC into a two-slot router and issues the show version command, the newly installed interfaces in the WIC cannot be seen in the router output. What is a possible reason why the newly installed interfaces are not displayed in the router output?
- The interface is not configured properly.
- The WIC was put into slot 0 instead of slot 1.
- The WIC was not physically installed in the slot properly.
- The show version command cannot be used to validate the presence of installed interfaces.
57. Refer to the exhibit. What can be concluded from the output that is shown?
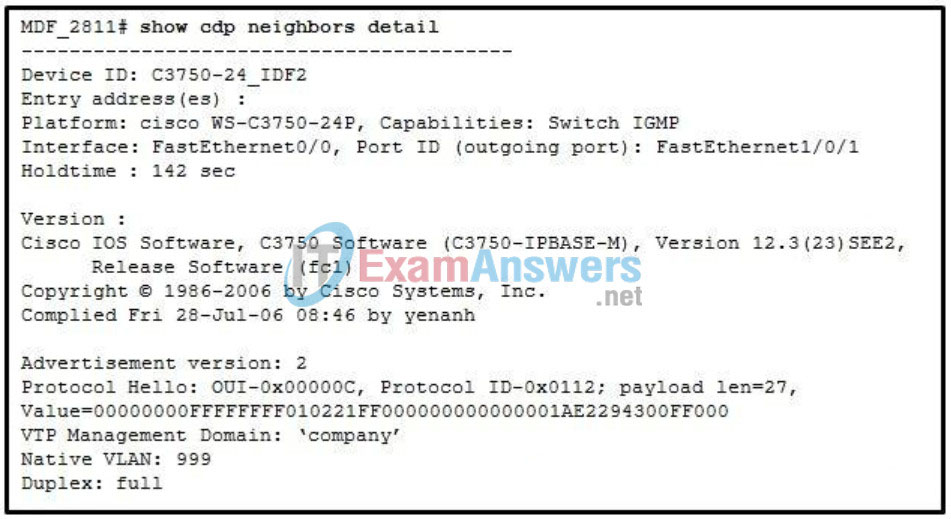
- MDF_2811 has a MAC address of 2294:300F:0000.
- A Cisco 3750 switch is connected to the FastEthernet1/0/1 port on MDF_2811.
- MDF_2811 is installed in the main distribution facility on floor 28 of building 11.
- Device 3750-24_IDF2 is running Cisco IOS Software Release 12.2(25)SEE2.
58. Refer to the exhibit. A network technician is performing an initial installation of a new switch in the east wing. The technician removes the switch from the box, connects the switch to a router that supports the 10.255.254.0/24 network, and adds the configuration that is shown. The technician notifies the network administrator that the switch has been installed. The network administrator then attempts to telnet to the switch from host 192.168.0.1 to complete the switch configuration. What are the results of this attempt to telnet?
- The switch refuses the connection.
- The connection to the switch times out.
- The network administrator is prompted to login.
- The connection is established at the user EXEC prompt.
59. A NetworkingCompany customer is interested in creating an e-commerce business, which includes a network upgrade and the addition of a new server farm. By offering their products on the web, the company expects to increase revenue and reduce wait times to process orders. The network designer proposes to implement the server farm in a new data center and to add a new T1 circuit to handle the expected traffic. What are two business goals of the NetworkingCompany customer? (Choose two.)
- install a new T1 circuit
- increase revenue
- implement a new server farm
- reduce wait times to process orders
- install a new data center
60. Refer to the exhibit. To demonstrate the importance of using contiguous IP addressing in a hierarchical network design, a network designer configures a prototype network with the use of a network simulator. Which EIGRP configuration commands should the designer enter on router R1 to correctly advertise a single summary route to router BR1 for the campus LAN?
61. What makes the Cisco EasyVPN application a useful tool for VPN implementation?
- It provides encryption algorithms unavailable in other systems.
- It ensures that remote workers actually use the VPN for connectivity.
- It simplifies the configuration tasks for the device that is used as the VPN server.
- It allows a greater variety of network devices to be used for VPN connections.
62. A local car dealership recently purchased an automobile financing company. The owner of the dealership issues a contract to NetworkingCompany to integrate the finance company network into the car dealership network. A router in the existing finance company network requires a password for both Telnet and console access, but no one remembers the passwords. What can the NetworkingCompany network technician do to obtain or change the passwords and gain access to the router?
- Use a TFTP server to download a new configuration file to the router that contains the passwords used on the car dealership network and then reload the router.
- Connect a rollover cable to the serial0/0 port of the router in order to bypass the password security, and use the show running-config command to obtain the passwords.
- Connect a console cable to the router, power cycle the router, issue a Ctrl-Break to enter ROM monitor mode, and change the configuration register to bypass the startup configuration.
- Connect the router to another Cisco router at the car dealership, use the show cdp neighbors command to obtain an IP address of the router, and use SSH to gain secure access in order to view the passwords.
63. A network administrator is troubleshooting connectivity problems on a small IPv6 network that consists of two network segments that are connected by a single router. The administrator can ping the IP addresses of local hosts on each segment from the router. Hosts on one network segment cannot successfully ping the IP addresses of hosts on the other network segment. What is the most likely cause of the connectivity problem between the segments?
- incorrect VLAN assignments on each segment
- broadcast storm that is caused by a malfunctioning NIC on a host
- incorrect DNS mappings of host names to IPv6 addresses
- IPv6 traffic forwarding not configured on the router
64. At the distribution layer of a hierarchical network, what are two advantages of using Layer 3 devices instead of Layer 2 switches? (Choose two.)
- enables the creation of large multisite VLANs
- creates fewer IP subnets to configure and manage
- reduces the number of redundant links required
- reduces the complexity of STP configurations
- enables traffic filtering based on subnet addresses
65. A NetworkingCompany engineer is on a support call resolving technical problems for a client network. After the issue is resolved, the engineer also provides a training session for the client’s network support staff. Which position on the networking company team is this engineer performing?
- post-sales field engineer
- pre-sales engineer
- network designer
- account manager
66. What is the main purpose of the access layer in a hierarchically designed network?
- perform routing and packet manipulation
- supply redundancy and failover protection
- provide a high-speed, low-latency backbone
- serves as a network connection point for end-user devices
67. A router has been removed from the network for maintenance. A new Cisco IOS software image has been successfully downloaded to a server and copied into the flash of the router. What should be done before placing the router back into service?
- Back up the new image.
- Copy the running configuration to NVRAM.
- Delete the previous version of the Cisco IOS software from flash.
- Restart the router and verify that the new image starts successfully.
68. A NetworkingCompany customer requires VPN connectivity for workers who must travel frequently. To support the VPN server, the customer router must be upgraded to a new Cisco IOS software version with the Advanced IP Services feature set. What should the field engineer do before copying the new IOS to the router?
- Set the router to load the new IOS image file directly from the TFTP server on the next reboot.
- Delete the currently installed IOS by using the erase flash: command, and reload the router
- Issue the show running-configuration command to determine the features of the currently installed IOS image file.
- Issue the show version and the show flash commands to ensure that the router has enough memory and file space to support the new IOS image.
69. The main office of a NetworkingCompany customer currently connects to three branch offices via three separate point-to-point T1 circuits. The customer network uses RIPv2 as the routing protocol within both the LAN and the WAN. The account manager proposes a change to a Frame Relay network because the costs are lower. A single local loop connection can be installed at the main office with three separate PVCs to connect the branch offices. How can the main office edge router be configured to enable the customer to continue to use RIP as the WAN routing protocol?
- Enable Inverse ARP on the serial interface in order to learn the routes to the IP addresses of the remote routers.
- To prevent the Frame Relay network from causing a routing loop, disable split horizon on the serial interface.
- Create three separate point-to-point subinterfaces on the serial interface and assign a different subnet IP address to each one.
- Configure the serial interface with a single interface DLCI number and create frame-relay map statements for each remote site address.
70. A high school uses a fractional T1 for Internet access. Wireless network access is provided in approximately 30 percent of the physical campus. Tests performed recently by the IT administrators indicate that the T1 circuit is operating at full capacity. The school district IT design team is asked to propose a network upgrade plan to address two business goals:
1. Provide wireless network connectivity for students in 90 percent of the physical campus.
2. Improve Internet access for all students and faculty.
The design team proposes to upgrade the memory of the core router that is connected to the ISP and to purchase additional wireless access points.
What can be concluded about the proposal that is presented by the design team?
- The proposal addresses only the goal to increase the wireless coverage.
- The proposal addresses only the goal to improve Internet access.
- The proposal addresses both business goals.
- The proposal addresses neither business goal.
71. Refer to the exhibit. The network administrator is configuring the port security feature on switch SWC. The administrator issued the command show port-security interface fa 0/2 to verify the configuration. What can be concluded from the output that is shown? (Choose three.)
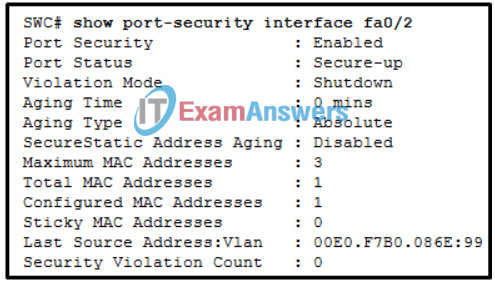
- This port is currently up.
- The port is configured as a trunk link.
- There is no device currently connected to this port.
- Three security violations have been detected on this interface.
- The switch port mode for this interface is access mode.
- Security violations will cause this port to shut down immediately.
72. What are two advantages of using a simulation tool to test an IP addressing scheme? (Choose two.)
- Address configuration errors can be addressed using out-of-band connections.
- Placement of subnets and route summarization can be verified.
- An engineer can test physical security without leaving the office or lab.
- The addressing scheme can be tested for scalability.
- The effects of combining new with existing infrastructure can be measured.
- It provides real-time monitoring of a production network.
73. Refer to the exhibit. A field engineer is called into a customer’s office to determine a problem with connectivity in the network. Based on the customer’s IP addressing scheme, what is causing the problem?
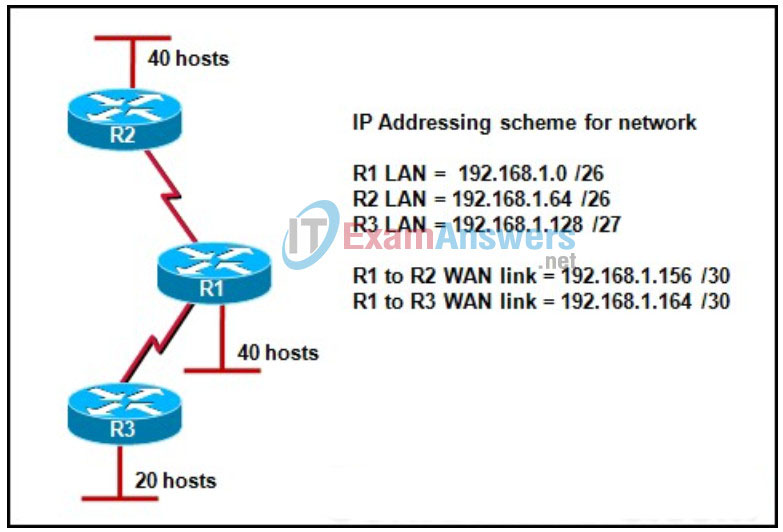
- The VLSM scheme is correct as shown.
- The WAN that connects R1 to R3 has an incorrect mask.
- The WAN that connects R1 to R2 overlaps with the R3 LAN.
- The R1 LAN is incorrect because subnet zero cannot be used with VLSM.
74. A new WIC is installed in an available router slot. At what point during the router startup process does the router test the card for hardware problems?
- after the configuration from NVRAM is loaded into RAM
- when the bootstrap program is loaded into RAM
- after the configuration from NVRAM is loaded into ROM
- during the power-on self-test (POST)
75. Refer to the exhibit. A NetworkingCompany engineer is characterizing an existing network for a new customer. The engineer issues a show run command on the branch router to gather configuration information. What is the engineer able to determine as a result of viewing the output of this command?
- The branch office router has two routes to the main office LAN in the routing table.
- The default route for the branch office traffic is the router that is located at the main office.
- A connection through ISP-A will be used to reach the main office LAN if the Frame Relay network is unavailable.
- By using both the DSL and the Frame Relay connection, the branch office router will load balance traffic that is destined for the main office LAN.
76. A configuration file needs to be loaded into the RAM of a router from a TFTP server. What should an administrator know before accomplishing this task?
- the router IP address and the operating system that is used by the TFTP server
- the TFTP server IP address and the name of the configuration file on the server
- the router IP address and the name of the router configuration file in NVRAM
- the TFTP server IP address and the router interface through which the file will be loaded
77. A network designer must select a routing protocol for the network of a customer. The currently installed network contains both Cisco and non-Cisco routers, and there is no budget to replace them. The designer plans on implementing both VLSM and route summarization in the new network design. Which two protocols can provide the necessary functionality for this LAN? (Choose two.)
- RTP
- RSTP
- RIPv1
- RIPv2
- EIGRP
- OSPF
78. Which two weaknesses in a proposed network design can be identified by setting up a prototype network and performing tests on it? (Choose two.)
- congestion and inadequate bandwidth in the provider Frame Relay network
- costs of the proposed equipment exceed the customer budget
- potential points of failure that are critical to the network
- limited scalability that can present problems if the network grows faster than anticipated
- poor documentation of existing network topology and design
79. A user in a large office calls tech support to complain that the PC no longer connects to the Internet or to any network resources, but seems otherwise normal. The help desk technician asks the caller to talk to nearby users to see if other machines are affected. After a few minutes, the caller reports that several immediate neighbors have the same problem, but those seated further away do not. Assuming that the description is accurate, what should be checked next?
- power outlet to the PC that is used by the caller
- workgroup switch in the telecommunications room
- cable between any network outlet and the telecommunications room
- cable between the PC that is used by the caller and the network outlet it connects to
- cable between the PC that is used by a neighbor and the network outlet the neighbor PC it connects to
80. Which of the following are characteristics of the core layer of the hierarchical network design model? (Choose three.)
- redundant paths
- high-level policy enforcement
- packet manipulation
- media transitions
- rapid forwarding of traffic
- no packet filtering
81. A network designer needs to perform prototype testing on a multisite network design to verify that failure domains are not larger than specified in the proposal. What would be the most efficient way to conduct this test?
- Use simulation software to check the IP addressing scheme for errors.
- Power down lab equipment and ping from one host to all other hosts.
- Disconnect links between lab equipment and ping end-to-end across the network.
- Delete devices or links in simulation software and ping from each host to all other hosts.
82. A customer has asked a network engineer to prototype the new IP addressing and summarization strategy for a large, multisite network implementation. Which tool is appropriate for testing the complete addressing scheme?
- Cisco SDM
- network simulation tool
- actual network equipment in a lab
- current network of the customer
83. During a review of the proposed bill of materials, the Networking Company account manager realizes that the systems engineer included a lower cost, less capable switch model for the access layer connectivity than was specified by the network designer. When questioned, the systems engineer responds that the switches recommended by the designer cannot be purchased within the budget limitations of the customer. Which action should the account manager take?
- Inform the customer that the project cannot be completed given the unreasonable budget constraints.
- Communicate any risks associated with the equipment substitution and obtain customer approval to proceed.
- Because the customer is probably aware that the budget limitations will require lower cost, less capable equipment, the account manager should do nothing.
- Because the customer is probably aware that the budget limitations will require lower cost, less capable equipment, the account manager should do nothing.
84. Refer to the exhibit. What is the spanning-tree role of all the enabled interfaces of SW11?
- alternate
- backup
- designated
- root
85. After performing a password recovery operation on a router, the network field engineer copies the running configuration to the startup configuration and then reloads the router. The router boots successfully but immediately enters the setup mode. The engineer manually loads the startup configuration using the copy start run command and verifies that the configuration is correct and the passwords are reset. What can cause the router to enter setup mode rather than load the correct startup configuration file?
- The field engineer configured the incorrect passwords in the startup configuration file.
- The configuration register setting was not changed back to the correct value before the router was reloaded.
- The running configuration was not successfully saved to the startup configuration before the router was reloaded.
- During the password recovery process, the engineer should have copied the startup configuration to the running configuration before reloading the router.
86. An HWIC-4ESW, four-port switch module needs to be installed in a Cisco 1841 router that currently has a WIC-2T module in slot 0. What should the network technician do first?
- Turn off power to the router before installing the new module.
- Remove the WIC-2T module so that the new module can be installed in slot 0.
- Shut down all Fast Ethernet ports on the router until the switch module installation is complete.
- Configure the router Cisco IOS software to support an internal trunk link between the switch and router module.
87. Refer to the exhibit. Based on the EIGRP configuration that is shown, what can the field engineer conclude about the EIGRP authentication between RouterA and RouterB?
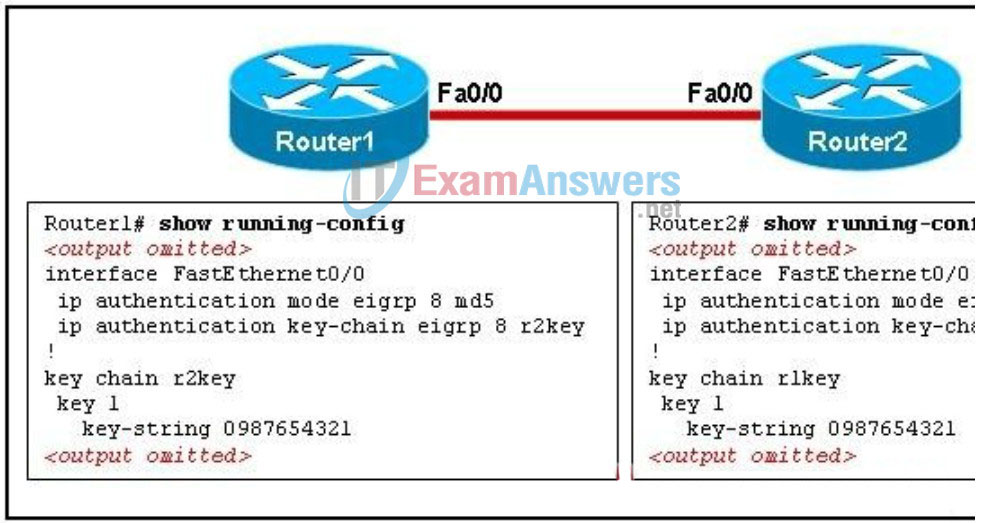
- Authentication will fail because only one key is configured.
- Authentication will fail because the key chain names do not match.
- Authentication will succeed and EIGRP updates can be exchanged.
- Authentication will fail because the key chain names must match the router names.
88. Refer to the exhibit. Following a test plan, the network systems engineer completes the configuration of an access layer switch and connects three PCs to test the configuration. The engineer attempts to ping from each PC to the other connected PCs. Which three statements describe the expected results of pinging from one host to another? (Choose three.)
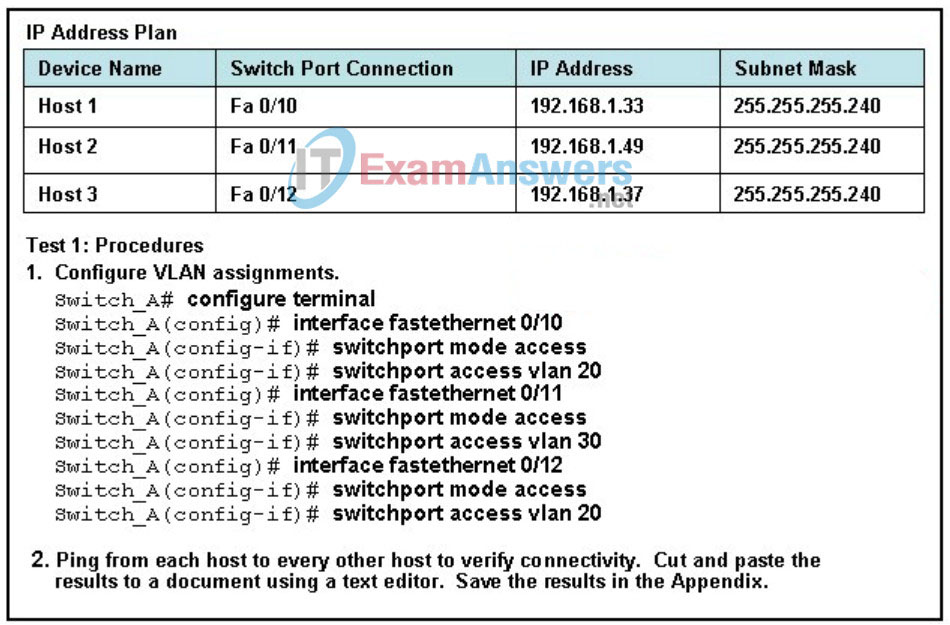
- Host1 can ping Host2.
- Host1 cannot ping Host2.
- Host1 can ping Host3.
- Host1 cannot ping Host3.
- Host2 can ping Host3.
- Host2 cannot ping Host3.
89. Refer to the exhibit. The two switches that are shown will not form a trunk. What is the most likely cause of this problem?
- The native VLANs are improperly configured.
- All the hosts are on the same VLAN and a trunk is not needed.
- Both ports are set to dynamic auto.
- The trunk should be configured using the switchport mode access command.
90. During prototype testing, the network designer performs a test to determine the ability of the network to recover from a link or device failure. Which design goal is validated if the test is a success?
- scalability
- manageability
- availability
- security
91. What are two suggested best practices to implement when securing network devices? (Choose two.)
- Configure VLAN 1 as the native VLAN.
- Disable unused ports on switches.
- Enable SSH and disable Telnet.
- Consolidate guest traffic and internal employee traffic.
- Ensure that logs are stored locally on routers.
92. Refer to the exhibit. What does the JAX router do with traffic that is destined for a web server with an IP address of 128.107.10.24?
- The traffic is sent out Serial 0/0/0.
- The router sends the traffic out all interfaces other than the one it came in on.
- A request is sent to neighboring routers for paths to the 128.107.0.0 network.
- The packets are placed into a queue until a better route is discovered via RIP.
93. When should a network designer specify that a dedicated firewall appliance be used at the perimeter of the network rather than a router with a Cisco IOS software-based firewall feature set?
- There are multiple servers in the DMZ.
- The network is large in size and network traffic can overload the device.
- Traffic filtering is needed on the internal network.
- Multiple levels of access to the network are needed.
94. Which two events occur when the command RTA(config)# frame-relay map ip 10.1.1.1 22 is issued on a router? (Choose two.)
- DLCI 22 replaces the MAC address in the ARP table for entry 10.1.1.1.
- The remote router that is connected to network 10.1.1.0 enters 22 the DLCI for host 10.1.1.1.
- Inverse-ARP is used to add an entry for 10.1.1.1 into the Frame Relay map table using DLCI 22.
- A Layer 2 address is statically mapped to a Layer 3 address.
- RTA uses DLCI 22 to forward data to 10.1.1.1.
95. Refer to the exhibit. When creating an extended ACL to deny traffic from the 192.168.30.0 network destined for the Web server 209.165.201.30, where is the best location for applying the ACL?
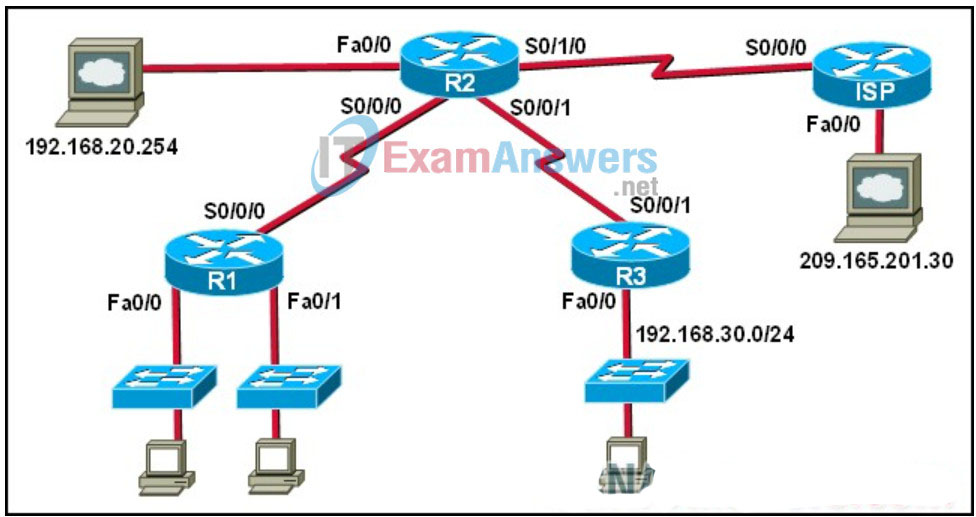
- R3 Fa0/0 inbound
- R3 S0/0/1 outbound
- R2 S0/0/1 inbound
- ISP Fa0/0 outbound
96. Why would a designer choose a flat network over a hierarchical network design?
- to make it easier to filter unwanted traffic
- to be able to implement QoS
- to keep costs low in small networks
- to reduce the size of failure domains
97. Refer to the exhibit. What does the status in the output indicate about the DLCI?
- The switch has the DLCI configured but it is not usable by this router.
- The DLCI was previously configured in the switch but is no longer there.
- It is usable but has little activity.
- The DLCI has been renamed for that PVC.
98. The network designer recommends using RSTP in the design of a new data center. There are multiple redundant Layer 2 switches and links contained in the new design. What is the benefit of using RSTP in this situation over standard STP?
- Redundant links are not blocked.
- Routing tables converge more quickly.
- Spanning Tree convergence times are reduced.
- Fewer redundant links are required to maintain connectivity.
99. A network administrator wants to load a configuration file from a TFTP server into NVRAM on a router. How should the administrator create a startup-config file in NVRAM that matches the contents of the configuration file on the TFTP server?
- Copy the configuration file from a TFTP server by using the command copy tftp startup-config.
- Copy the configuration file from a TFTP server by using the command copyfilename startup-config.
- Copy the file to RAM from a console connection by using the copy tftp running-config command. Then reload the router to use the new configuration.
- Paste the configuration file to the command line of the router while in global configuration mode. Then issue the copy startup-config running-config command.
100. What can be broadcast over the wireless network to help a guest user conveniently log in to the network and use wireless services?
- SSID
- VPN authentication
- WPA encryption
- VLAN parameters
- WEP keys
101. Which two options are true about discontiguous networks? (Choose two.)
- The routing problems of discontiguous subnetworks can be resolved easily by using the RIPv2 default configuration.
- The default configuration of all classless routing protocols can prevent problems that are caused by discontiguous networks.
- Automatic route summarization can cause problems in a network with discontiguous subnets.
- A network that runs a classful routing protocol will have problems if discontiguous subnets exist in the network.
- Automatic route summarization helps resolve problems with a network with discontiguous subnetworks.
102. Refer to the exhibit. A network associate is configuring a new router to provide routing between VLANs. The associate removes the router from the box and connects the Fa0/0 interface to a trunking port on the switch. After the configuration is applied to the router, the traffic between VLANs still fails. What is causing this to occur?
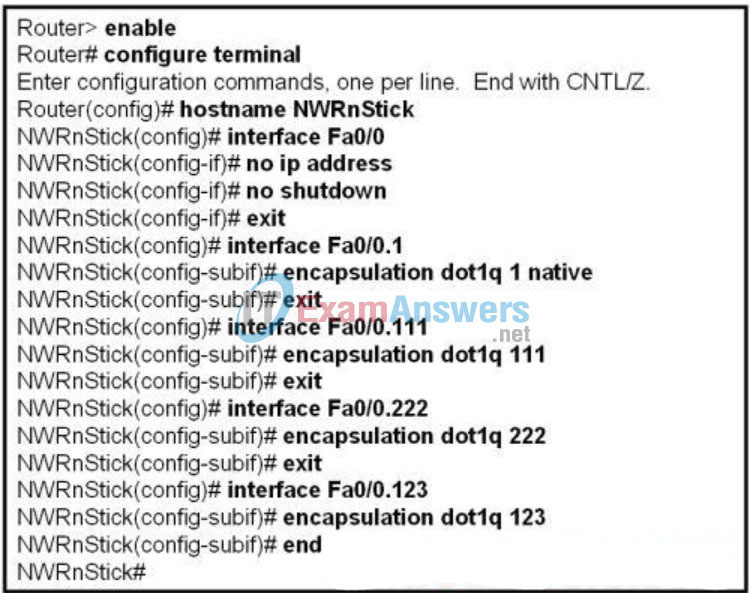
- The NWRnStick router needs a routing protocol configured.
- The NWRnStick router needs additional Fast Ethernet interfaces installed.
- The subinterfaces of the NWRnStick router should have IP addresses applied.
- All the subinterfaces of the NWRnStick router should be configured in the same VLAN.
103. A company has an IT staff that is not highly trained. What two features or technologies must the network designer identify as training needs in order for the staff to understand the basic operation of VPNs? (Choose two.)
- access control lists
- encryption algorithms
- Frame Relay configuration
- QoS operation
- tunneling protocols
- VLAN configuration
104. Which statement is true about implementing QoS in a network?
- Voice traffic automatically receives the highest priority.
- QoS guarantees enough bandwidth to every application.
- QoS increases actual bandwidth on a link to ensure voice quality.
- Voice traffic requires priority over other data traffic because it is sensitive to delays.
105. Which three enhancements does IPv6 offer over IPv4? (Choose three.)
- easier implementation and configuration
- more effective IP security
- integrated IP mobility support
- simplified header information
- fewer reserved IP addresses
- eliminates the need to implement DHCP
106. Refer to the exhibit. What happens if the network administrator issues the commands shown when an ACL called Managers already exists on the router?
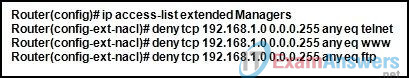
- The commands overwrite the Managers ACL that is already on the router.
- The commands are added at the end of the Managers ACL that is already on the router.
- The commands are added at the beginning of the Managers ACL that is already on the router.
- The network administrator receives an error stating that the ACL already exists.
107. A technician is configuring a router for routing using EIGRP. The technician enters the EIGRP router configuration mode command:
Router(config-router)# variance 3
What is the effect of entering this command?
- It enables unequal cost load balancing.
- It adjusts the cost of all EIGRP routes to 3.
- It restricts the number of EIGRP feasible successor routes to 3.
- It enables EIGRP equal cost load balancing over a maximum of 3 routes.
108. A small bookstore would like to offer wireless connectivity for customers with laptops. Which wireless components or devices will provide connectivity to the customers with the least possible cost to the bookstore?
- standalone access points
- wireless LAN controllers
- standalone lightweight access points
- lightweight access point and wireless LAN controller
109. A technician adds the command Router(config-router)# variance 5 to a router using EIGRP as the routing protocol. What is the result of entering this command?
- enables unequal cost load balancing
- adjusts the metric of all EIGRP routes to 5
- restricts the number of EIGRP feasible successor routes to 5
- activates the use of all K values in the composite metric calculation
- enables EIGRP equal cost load balancing over a maximum of 5 routes
110. A company is concerned with protecting internal e-commerce servers against external attacks. An application layer firewall is installed at the network edge and a host-based IDS system is installed on the internal LAN. What should be done to ensure a fast response and minimum server downtime in the event of an external attack?
- Replace the host-based IDS with an IPS.
- Place the e-commerce servers in a DMZ.
- Install a logging server to monitor all attacks.
- Replace the application layer firewall with a stateful one.
111. Which statement is true about the pairing of services and transport layer protocols for FTP and VoIP?
- FTP applications and VoIP use TCP at the transport layer.
- FTP applications and VoIP use UDP at the transport layer.
- FTP applications use TCP at the transport layer while VoIP uses UDP at the transport layer.
- FTP applications use UDP at the transport layer while VoIP uses TCP at the transport layer.
112. What type of Frame Relay subinterface must be used to connect remote sites without having to disable split horizon?
- multipoint
- multiaccess
- point-to-point
- nonbroadcast multiaccess
113. Refer to the exhibit. An administrator installs a WIC-2T module into a Cisco 1841 router. Attempts to configure the S0/0/0 interface are unsuccessful. As a first step in troubleshooting the failure, the administrator issues the show version command. What is a possible reason for the failure?
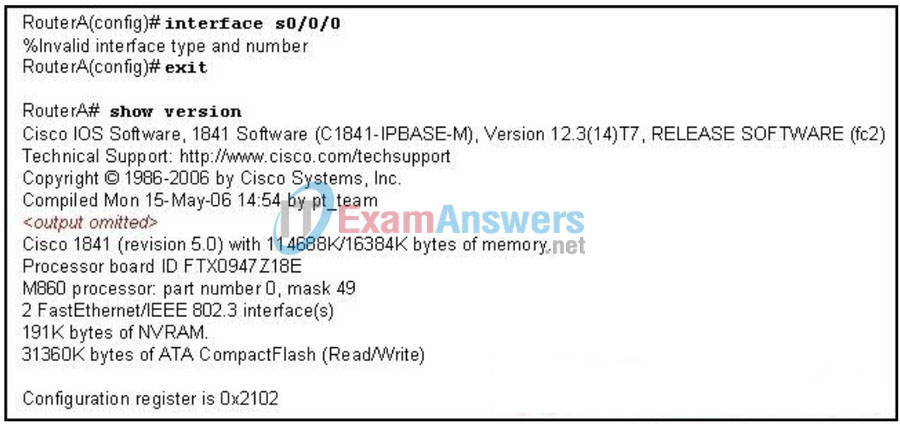
- The WIC was not physically installed properly.
- The WIC was installed into slot 1 instead of slot 0.
- The interface type and number are invalid on an 1841.
- The configuration register is the wrong value for adding new modules.
114. A company decides to deploy a virtual private network (VPN) to connect remote workers and branch offices to corporate headquarters. What is the best description of the type of connectivity the company is ready to implement?
- a VPN that uses LANs to connect remote sites or users
- a VPN that uses a public network to connect remote sites or users
- a VPN that uses a wireless LAN over the Internet to connect remote sites or users
- a VPN that uses a dedicated connections, such as leased lines, to connect remote sites or users
115. A network engineer is prototyping a new IP addressing and summarization strategy for a new network that will be integrated into the existing infrastructure. Which method is appropriate for testing the addressing scheme?
- using the production network of the customer
- using actual network equipment in a lab
- using the Cisco Network Assistant
- using a network simulation tool
116. Which technology will prioritize traffic based upon the technical requirements of IP telephony?
- PoE
- QoS
- RP
- C
- RTP
117. Refer to the exhibit. Following a test plan, the network systems engineer completes the configuration of an access layer switch and connects three PCs. The engineer attempts to ping from each PC to the other connected PCs to test the configuration. Which statement describes the result of the last step?
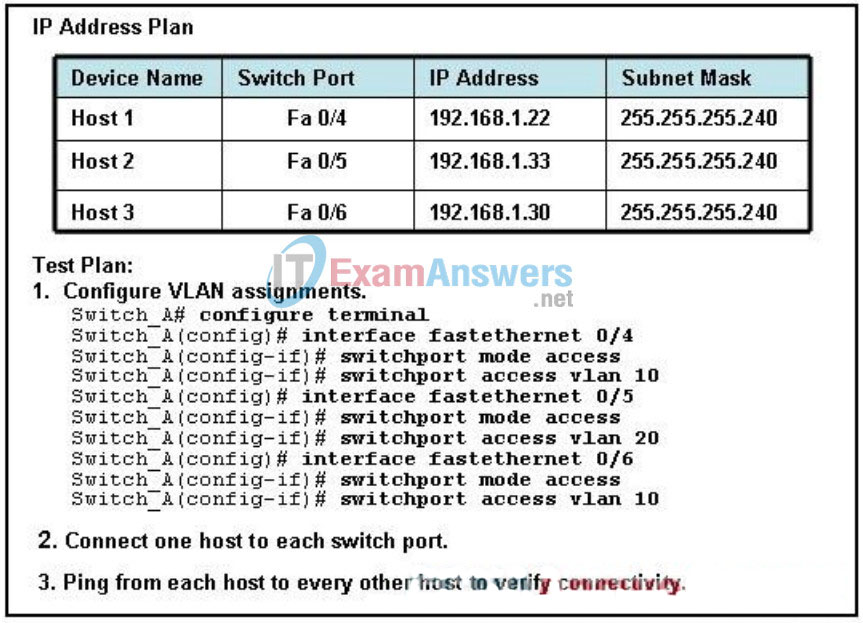
- Host 1 can ping Host 2.
- Host 1 can ping Host 3.
- Host 2 can ping Host 3.
- No hosts can ping any other host.
118. Refer to the exhibit. Access list 100 is applied inbound to interface serial 0/0/0 on the SOHO Router1. Which traffic will be denied by the configuration?
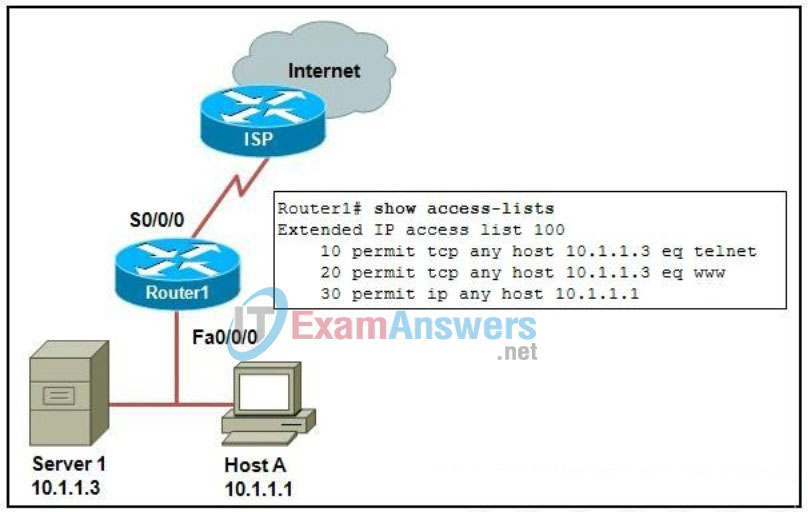
- DNS traffic from host A to the Internet
- FTP traffic from host A to the Internet
- ICMP traffic from the ISP to server 1
- traffic from the ISP to the server on port 23
119. When implementing a security policy, which two actions should be included as part of the security checklist? (Choose two.)
- Disable all logging.
- Enable Telnet on TCP port 23.
- Use HTTP for web administration.
- Set timeouts and ACLs on VTY lines.
- Shut down any unused ports and interfaces.
120. A WIC-1T module needs to be installed in a Cisco 1841 router that currently has a WIC-2T module in slot 0. What should the network technician do first?
- Install the hot-swappable option module.
- Turn off the power to the router before installing the new module.
- Remove the WIC-2T module so that the new module can be installed in slot 0.
- Shut down all Fast Ethernet ports on the router until the new WIC module installation is complete.
- Configure the Cisco IOS software to support an internal trunk link between the two WIC modules.
121. Refer to the exhibit. A networking company designer is reviewing a diagram of a customer network. What are the two problems that need to be resolved in the topology that is shown? (Choose two.)
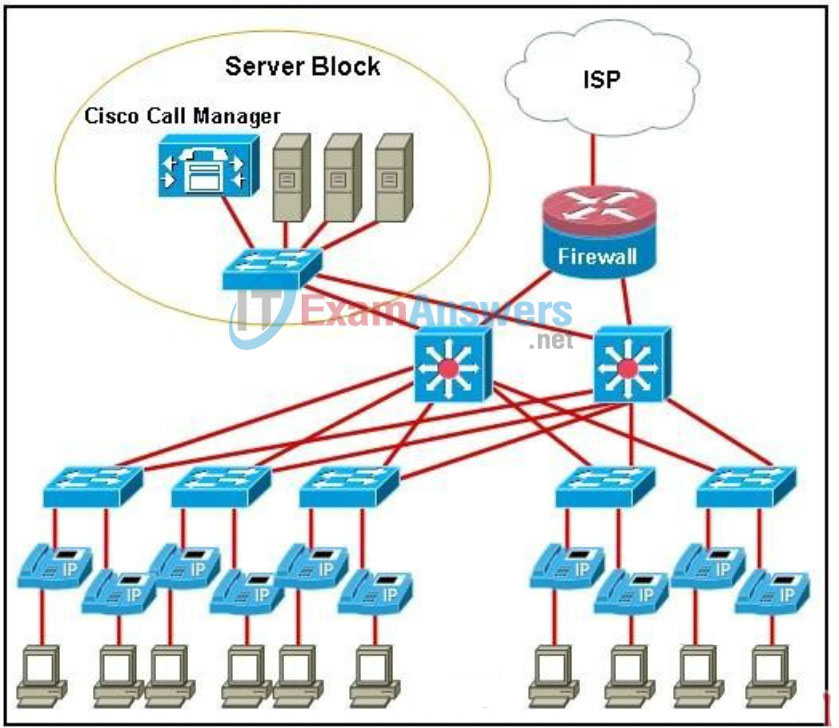
- The firewall router and ISP connection represent a single point of failure.
- If one of the Layer 3 switches fails, the Cisco Call Manager will be unreachable.
- A power supply failure of the server block switch will cause the entire IP telephony system to fail.
- Using Layer 3 switches to interconnect the server block servers to the IP phones introduces too much delay.
- The IP phones need to be redundantly connected to the switches to prevent single points of failure at the access layer.
122. Refer to the exhibit. A NetworkingCompany engineer is characterizing an existing network for a new customer. The engineer issues a show running-config command on the branch router to gather configuration information. What is the engineer able to determine as a result of viewing the output of this command?
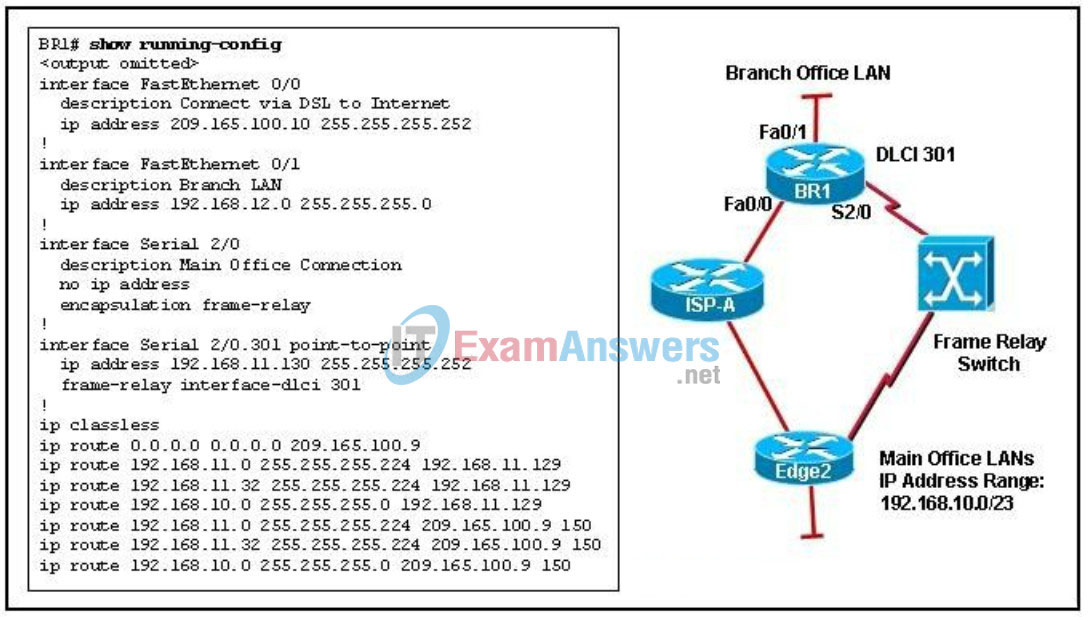
- The branch office router has two routes to the main office LANs in the routing table.
- The default route for the branch office traffic is the serial link to the Edge2 router.
- A connection through ISP-A will be used to reach the main office LANs if the Frame Relay network is unavailable.
- By using both the DSL and the Frame Relay connection, the branch office router will load balance traffic that is destined for the main office LANs.
123. What are the primary design goals for the core Layer?
- to provide centralized server farm and VoIP services
- to provide dynamic routing services, filtering, and traffic flow management
- to provide 100% uptime, maximization of throughput, and facilitation of network growth
- to provide static routing, wireless access points for the network, and security for the edge devices
124. In a converged network, which two types of traffic would be categorized as real-time traffic? (Choose two.)
- file transfer
- web browsing
- videoconferencing
- voice over IP
- video on demand
125. Refer to the exhibit. EIGRP has been configured as a routing protocol in the network. Users who are connected on LAN_1 and LAN_2 can ping their default gateways. Users on LAN_1 complain that they are unable to access the resources on the file server that is connected to LAN_2. A technician issues the show ip interface brief command on R1 to verify the status of the interfaces. What information will help the technician troubleshoot the issue?
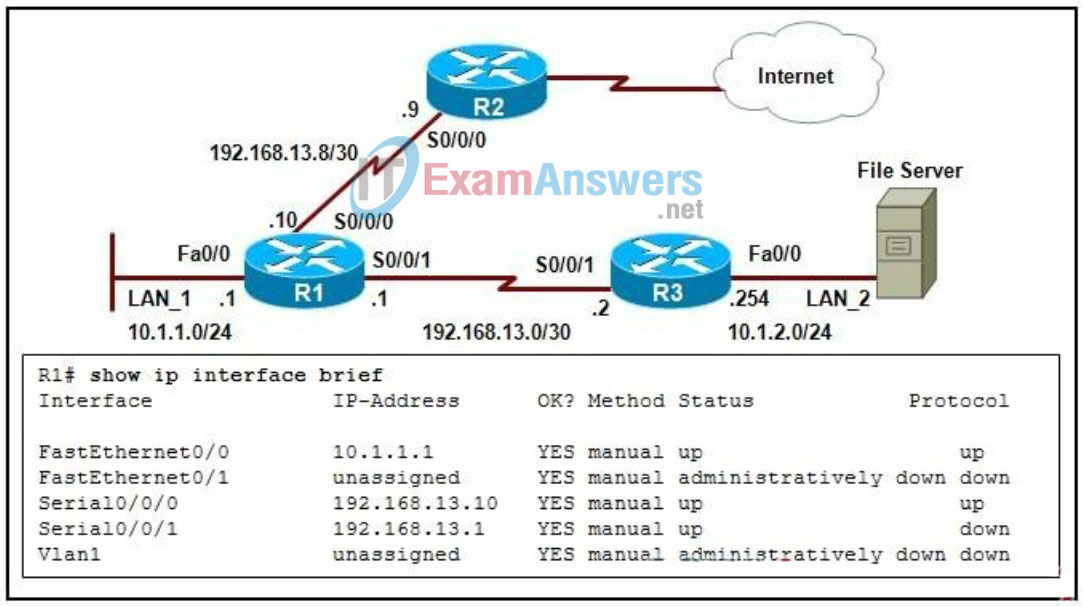
- Interface S0/0/1 line protocol is down.
- Interface Vlan1 is administratively down.
- Interface Fa0/1 is missing an IP address.
- Interface S0/0/0 is configured with an incorrect IP address.
126. Refer to the exhibit. A network engineer applies the ACL that is shown in the exhibit to interface S0/0/0 on router R1 outbound. What impact will the ACL have on traffic that moves through interface S0/0/0?
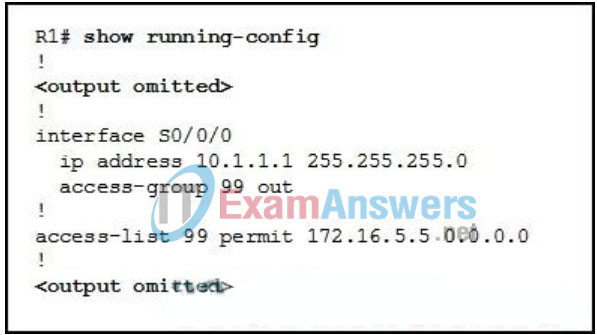
- All traffic from the 172.16.0.0/16 network will be permitted.
- All traffic from the 172.16.5.0/24 network will be permitted.
- All traffic from the host with the IP address 172.16.5.5 will be permitted.
- All traffic that is destined for the 172.16.5.0/24 network will be permitted.
- All traffic that is destined for the host with the IP address 172.16.5.5 will be permitted.
127. A network administrator is asked to upgrade the enterprise network devices and to modify the addressing scheme to support VLSM and route summarization. The current network infrastructure contains both Cisco and non-Cisco routers. The plan is to replace old routers gradually with the latest Cisco routers. Which two routing protocols can the administrator use to support both upgrading requirements? (Choose two.)
- BGP
- OSPF
- RIPv1
- RIPv2
- EIGRP
128. A network administrator is integrating IPv6 into an IPv4 network by encapsulating one protocol packet within another protocol. Which transition method is being used?
- dual stack
- tunneling
- proxying and translation
- NAT with Protocol Translator
129. What is a signaling standard that is used for managing and maintaining the connection between a CPE router and the service provider Frame Relay switch?
- ARP
- CIR
- DLCI
- Inverse ARP
- LMI
130. Which security procedure should be considered to protect a server farm against internal attacks?
- Locate the server farm on a DMZ.
- Virtualize server resources whenever possible.
- Implement load balancing and failover between servers.
- Implement a layer of firewall features and intrusion protection between the servers and the internal networks.
131. A network designer has chosen to specify the use of a dedicated firewall appliance at the perimeter of a large network. Why would the designer use a dedicated firewall rather than using the Cisco IOS firewall feature set on the existing router?
- Traffic filtering is needed on the internal LAN.
- Multiple levels of access to the network are needed.
- The DMZ requires packet filtering and port blocking.
- Heavy network traffic will be handled best by using a dedicated device.
132. Refer to the exhibit. What can be concluded from the output that is shown?

- MDF_2811 has a MAC address of 2294:300F:0000.
- Device C3750-24_IDF2 is running Cisco IOS Software Release 12.3(23)SEE2.
- A Cisco 3750 switch is connected to the FastEthernet1/0/1 port on MDF_2811.
- MDF_2811 is installed in the main distribution facility on floor 28 of building 11.
133. A network administrator has configured Frame Relay on a serial interface and issued the show interfaces serial command. The output shows that the interface is up and the line protocol is up. However, pings to the remote router across the link fail. What should the next step be to ensure that the IP address of the remote router appears in the Frame Relay map table of the local router?
- Configure the router using the no inverse-arp command.
- Ensure that the LMI type is correct for the circuit.
- Configure the router using the frame-relay map ip command.
- Verify that the remote router has Frame Relay encapsulation enabled.
134. Refer to the exhibit. The routers are configured with RIPv2 and utilize the default configuration. When attempting to communicate with other networks, hosts from 172.31.1.0/24 are experiencing connectivity issues. What could be done to resolve this issue?

- Change to a public IP address scheme.
- Ensure that automatic route summarization has been disabled on all routers in the network.
- Change the IP address for the Router3 LAN to be 192.168.7.0/24.
- Change the subnet mask on the link between Router2 and Router3 to 255.255.255.0.
135. Which statement describes the use of a network baseline?
- It creates a high level logical network diagram.
- It provides a point of reference for future network evaluations.
- It allows precise identification of the original location of network equipment.
- It should be established as soon as a problem is detected on the network.
136. Refer to the exhibit. What can be determined about the connection between R3 and R4?
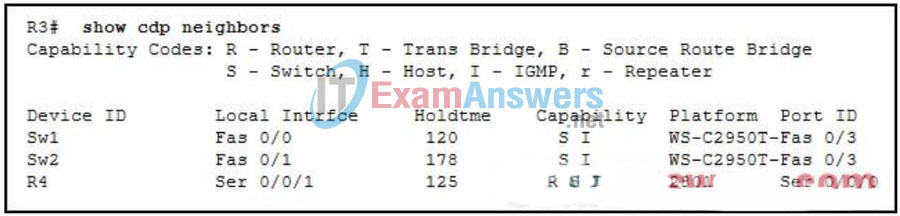
- R4 is three hops away.
- R4 is not a Cisco device.
- R3 and R4 are directly connected.
- R4 is reachable through switches Sw1 and Sw2.
137. While configuring EIGRP on a router, the technician enters this command:
Router(config-router)# variance 8
What is the effect of entering this command?
- It adjusts the cost of all EIGRP routes to 8.
- It enables unequal cost load balancing on the router.
- It restricts the number of EIGRP feasible successor routes to 8.
- It enables EIGRP equal cost load balancing over a maximum of 8 routes.
- It modifies the number of values used in the composite metric calculation.
138. What type of system connects to the PSTN and uses a PBX to route calls via analog or digital lines?
- VPN
- VoIP
- IP telephony
- traditional telephony
139. Company XYZ requires a WAN solution that provides flexible bandwidth options and supports one physical interface at the head office that would provide simultaneous connectivity to various remote sites. The distance from each site should not make the solution more expensive. Which WAN technology meets the requirements of the company?
- DSL
- cable
- Frame Relay
- T1 leased line
140. Refer to the exhibit. Which two commands allow verification of end-to-end Layer 3 connectivity from R3 to all devices? (Choose two.)
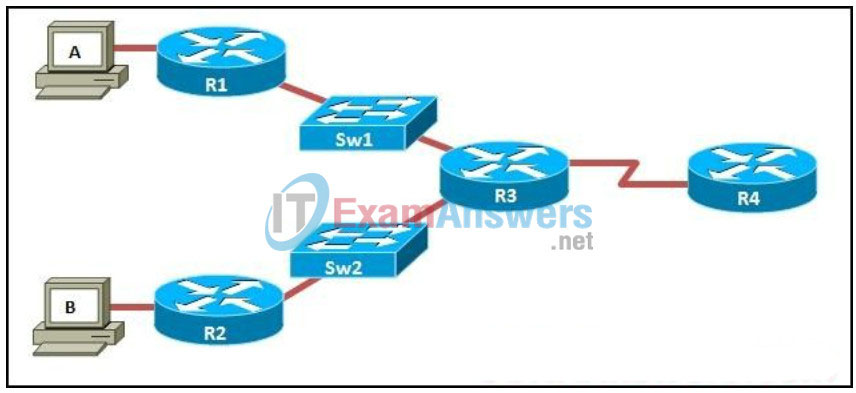
- R3> ping
- R3# traceroute
- R3# show ip arp
- R3# show ip route
- R3# show cdp neighbors
141. Why is it difficult for network designers to predict the patterns and behavior of file transfer traffic?
- The traffic is user initiated.
- File size is typically very small.
- Dedicated bandwidth is essential.
- All file transfer traffic is queued as high priority.
142. During the boot process and assuming the default sequence, what is the second location where the router will look for the IOS?
- ROM
- flash
- NVRAM
- TFTP server
143. A user in a large office calls technical support to complain that a PC has suddenly lost connectivity to the network. The technician asks the caller to talk to nearby users to see if other machines are affected. The caller reports that several immediate neighbors in the same department have a similar problem and that they cannot ping each other. Those who are seated in other departments have connectivity. What should the technician check as the first step in troubleshooting the issue?
- the power outlet to the PC that is used by the caller.
- the trunks between switches in the wiring closet.
- the status of the departmental workgroup switch in the wiring closet.
- the cable that connects the PC of the caller to the network jack.
- the cable connection between a PC and a network outlet that is used by a neighbor.
144. Which two technologies can provide data integrity in a VPN connection? (Choose two.)
- ESP
- DES
- MD5
- DH1
- SHA-1
145. What should be considered in the design of a wireless LAN on a corporate campus?
- the vendor of all employee wireless NICs
- the cables that are used for LAN connectivity
- the number of wireless NICs required on enterprise servers
- the messaging features that are used on employee cell phones
- the location of the concrete pillars and walls between the offices
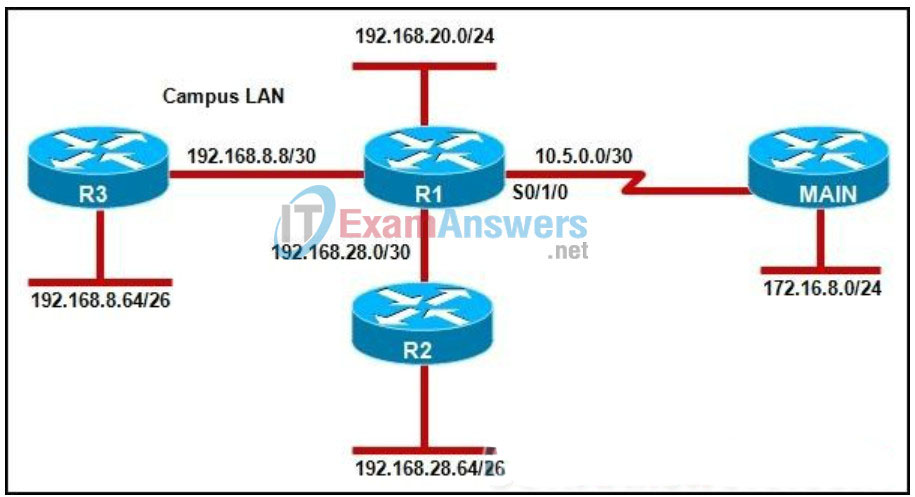
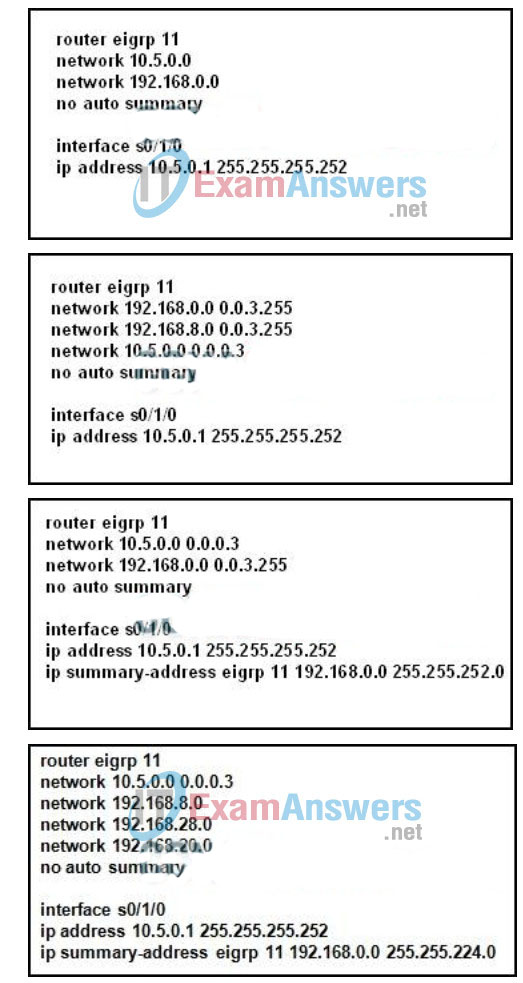
146. Refer to the exhibit. Which EIGRP configuration commands should a network administrator enter on router R1 to correctly advertise a single summary route to router MAIN for the campus LAN?
147. Refer to the exhibit. The named ACL “Managers” already exists on the router. What will happen when the network administrator issues the commands that are shown in the exhibit?
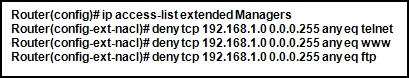
- The commands are added at the end of the existing Managers ACL.
- The commands overwrite the existing Managers ACL.
- The commands are added at the beginning of the existing Managers ACL.
- The network administrator receives an error that states that the ACL already exists.
148. Company XYZ needs a WAN connection between headquarters and branch offices that has a high level of security. The connection must provide high bandwidth to support VoIP and transactional data with as little overhead as possible. What is the best solution for WAN connectivity for company XYZ?
- DSL
- cable
- cell relay
- PPP over a leased line
149. What information does an administrator require before saving the running configuration from a router to a TFTP server?
- router IP address and the name of the configuration file in NVRAM
- TFTP server IP address and the size of the configuration file in RAM
- TFTP server IP address and the name of the configuration file that will be saved
- router IP address, size of the file and name of the configuration file on the TFTP server
- TFTP server IP address, the router IP address, and the router interface through which the file will be loaded
150. Which task would typically only require services that are located at the access layer of the hierarchical design model?
- placing a VoIP call to a business associate in another country
- connecting to the corporate web server to update sales figures
- using a VPN from home to send data to the main office server farm
- responding to an e-mail from a co-worker in another department
- printing a meeting agenda on a local departmental network printer
151. What value is an alternative representation of the IPv6 address 2001:DB80:0000:0000:0C41:3EFF:FE00:0000?
- 2001:DB8::C41:3EFF:FE:
- 2001:DB80::C41:3EFF:FE00::
- 2001:DB80::C41:3EFF:FE00:0
- 2001:DB80:0:0:0:C41:3EFF:FE::
152. A network engineer is at a customer site. After resolving technical problems in the network, the engineer provides a training session for the support staff. Which job function best fits the activities of this network engineer?
- network designer
- account manager
- pre-sales engineer
- post-sales field engineer
153. Refer to the exhibit. While planning an upgrade, a network administrator uses the Cisco NetFlow utility to analyze data flow in the current network. What generated the most packets?
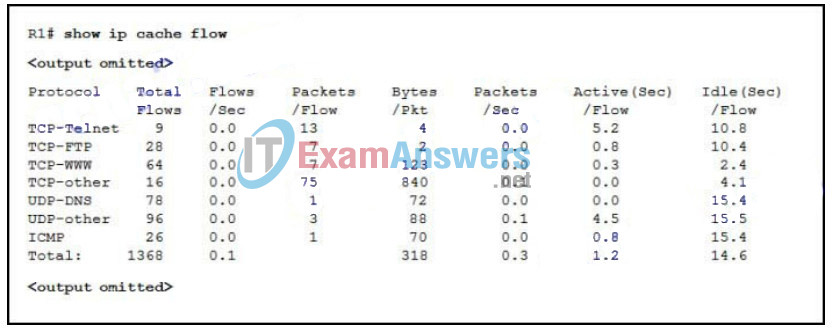
- ICMP
- TCP-Telnet
- TCP-other
- UDP-DNS
- UDP-other
154. Refer to the exhibit. After issuing the router configuration commands shown, a network administrator finds that IPv6 routing is not working on the router. What could solve the problem?
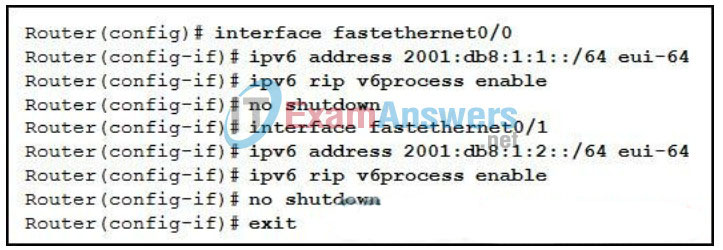
- Configure a unique IPv6 RIP process on each interface.
- Issue the ipv6 unicast-routing global configuration command.
- Issue the ipv6 router rip v6process global configuration command.
- Change the prefix length on both IPv6 addresses from 64 to 128 bits.
155. Which two processes allow a smooth transition from IPv4 to IPv6? (Choose two.)
- IPSec
- tunneling
- dual stack
- authentication
- anycast addressing
- header simplification
156. When designing a prototype network for a new server farm, a network designer chooses to use redundant links to connect to the rest of the network. Which business goal will be addressed by this choice?
- availability
- manageability
- security
- scalability
157. Which feature of network design and configuration would be considered a weakness?
- Choosing a flat network model.
- Choosing to implement an IPS instead of IDS.
- Choosing to disable Telnet and allow only SSH connections for remote access to the core routers.
- Choosing not to broadcast the SSID for wireless access points.
158. The network infrastructure at the headquarters of an organization consists of Cisco network devices that are running RIPv1. As part of an upgrade project, a portion of the company backbone will be increased to 10 Gb/s and needs to support unequal cost load balancing between routers. The IP addressing scheme is also changing and needs to support VLSM and CIDR. Which routing protocol should be selected for the network?
- BGP
- EIGRP
- OSPF
- RIPv2
159. A company would like to ensure that the failure of a single access switch does not disrupt service to the mail servers located in the data center. What can be done to ensure maximum connectivity to the mail servers?
- Enable CDP to ensure all neighboring devices are known.
- Create a separate RSTP specifically for the mail servers.
- Configure a routing protocol so that paths to all Layer 3 devices are cached.
- Install redundant access links between the servers and the access layer switches.
160. Which statement best describes the VPN feature called split tunneling?
- It creates separate pathways for different VLANs.
- It creates two tunnels, one for user traffic and one for management traffic such as CDP and SNMP.
- It allows user traffic that is destined for the corporate network to travel across the VPN tunnel, while traffic destined for the Internet travels through the local LAN of the VPN client.
- It allows separate tunnels so that high priority traffic, such as voice and video, uses the higher bandwidth tunnel, while all other user traffic travels on the lower bandwidth tunnel.
161. What is the advantage of choosing EasyVPN for a new VPN implementation?
- to provide encryption algorithms unavailable in other systems
- to ensure that remote workers actually use the VPN for connectivity
- to allow a greater variety of network devices to be used for VPN connections
- to simplify the configuration tasks for the device that is used as the VPN server
162. A network administrator of a middle-sized company is asked to upgrade the routing protocol of the network to support VLSM and route summarization. The current company network contains both Cisco and non-Cisco routers. Which routing protocol should be used for the upgrade?
- BGP
- RIPv1
- RIPv2
- EIGRP
163. Refer to the exhibit. What problem is associated with the the addressing scheme of the network?
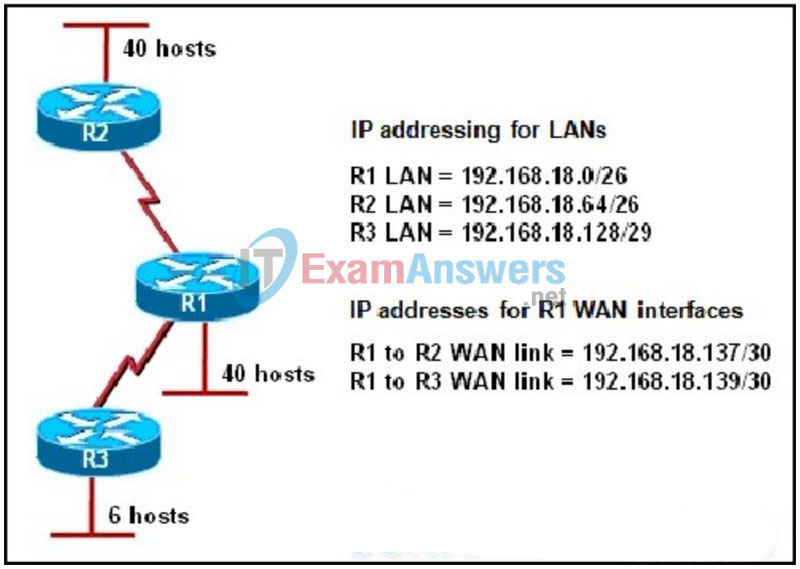
- The WAN links need IP addresses from a different major network.
- The R1 LAN is incorrect because subnet zero cannot be used with VLSM.
- The WAN link IP address that connects R1 to R3 has an incorrect mask.
- The R1 to R3 and R1 to R2 WAN links have IP addresses that overlap.
- The WAN IP address that connects R1 to R2 overlaps with the R3 LAN IP addresses.
164. Refer to the exhibit. A pre-sales system engineer receives a diagram of the current WAN from a customer. EIGRP is the routing protocol used on the WAN. Based on the default operation of EIGRP, which statement is true about the routing table on router R1?
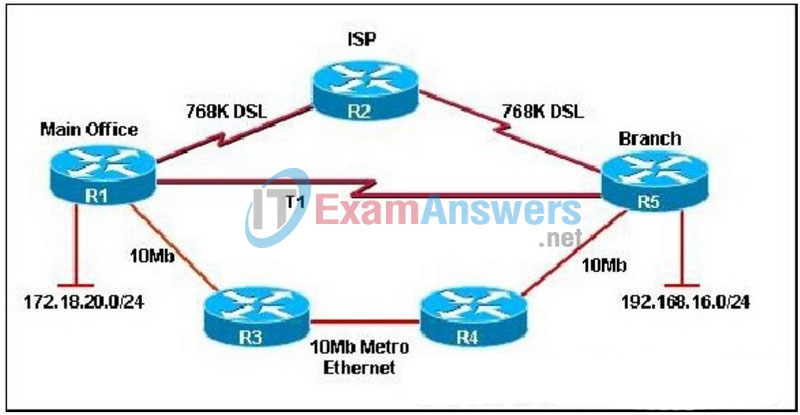
- There is a single route to the 192.168.16.0/24 LAN using the T1 connection.
- There is a single route to the 192.168.16.0/24 LAN using the DSL connection.
- There is a single route to the 192.168.16.0/24 LAN using the Metro Ethernet connection.
- EIGRP installs all three routes to the 192.168.16.0/24 LAN and load balances the traffic.
165. Which characteristic should be considered by a network designer when implementing a VoIP solution?
- VoIP traffic is generally classified as low priority.
- VoIP centrally routes calls in the same manner as a traditional PBX.
- VoIP traffic is highly reliable because of retransmission of dropped packets.
- VoIP can make use of QoS features to help reduce interruptions in communication.
166. Refer to the exhibit. What can be concluded from the output that is shown?
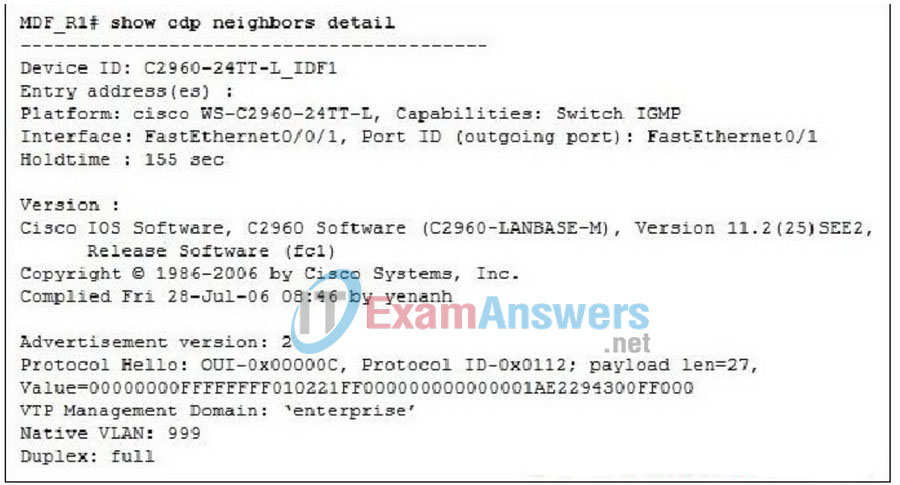
- MDF_R1 has a MAC address of 2294:300F:0000.
- MDF_R1 is connected through FastEthernet0/1 to C2960-24TT-L_IDF1.
- Device C2960-24TT-L_IDF1 is running Cisco IOS Software Release 12.2(25)SEE2.
- MDF_R1 is installed in the main distribution facility on floor 24 of building L.
167. Refer to the exhibit. Based on the output, which statement is correct?
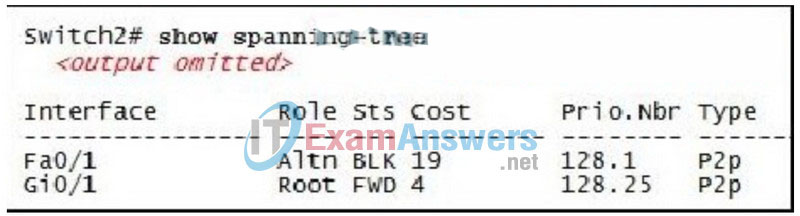
- Switch2 is the root bridge.
- Traffic will use Fa0/1 as an alternative link if Gi0/1 is busy.
- All traffic with a destination on another switch will exit via Gi0/1.
- The port cost on Gi0/1 has been changed from its default settings.
- Interface Fa0/1 on Switch2 has no role in the operation of spanning tree.
168. A company has help desk staff that is not highly trained in VPNs. What two features or technologies must the network designer identify as training needs in order for the help desk to support secure remote access for teleworkers? (Choose two.)
- QoS operation
- VLAN configuration
- tunneling protocols
- IPv6 and IPv4 dual stack
- encryption algorithms
- Frame Relay configuration
169. Which feature relies on prioritization of network traffic and is used to ensure successful delivery of real-time services?
- security
- reliability
- redundancy
- quality of service
170. A network administrator wants to configure a router that is running EIGRP so that it will advertise a route that will summarize the networks that are shown. Which network will summarize only these networks?
192.168.12.0/24
192.168.13.0/24
192.168.14.0/24
192.168.15.0/24
- 192.168.0.0/16
- 192.168.0.0/20
- 192.168.8.0/21
- 192.168.12.0/22
- 192.168.16.0/22
171. What is a function that is associated with the access layer in a hierarchically designed network?
- performs routing and packet manipulation
- supplies redundancy and failover protection
- provides a high-speed, low-latency backbone
- serves as a network connection point for IP telephony devices
172. A customer of a large multisite organization has asked a network engineer to compare a new IPv4 addressing strategy with an IPv6 strategy for their new network implementation. Which tool is appropriate for testing and comparing both addressing schemes?
- NBAR
- Cisco SDM
- Network Assistant
- network simulation tool
173. When implementing an IP telephony solution, why should VLANs be used?
- to allow the use of a single IP gateway
- to separate voice from data traffic for ease of prioritization
- to allow the PBX to use VLAN IDs to filter both voice and data traffic
- to allow connectivity between traditional phone devices and IP-based telephony devices
174. A network administrator has removed a router from the network for maintenance. A new Cisco IOS software image has been successfully downloaded to a server and copied into the flash of the router. What should the administrator do before placing the router back into service?
- Delete the previous version of the Cisco IOS software from flash.
- Copy the new IOS into NVRAM to create a backup copy.
- Restart the router and verify that the new image starts successfully.
- Verify the free space available on the router to store the new IOS image.
175. A NetworkingCompany engineer is on a support call resolving technical problems for a client network. After the issue is resolved, the engineer also provides a training session for the network support staff. What role is the engineer filling on the networking company team?
- post-sales field engineer
- pre-sales engineer
- network designer
- account manager
176. Refer to the exhibit. All router interfaces are up and RIP version 2 is configured as the routing protocol. The users in networks 172.16.8.0 /24 and 172.16.9.0/24 are not able to reach users in the 172.16.16.0/24 network. The network administrator examines the routing tables and finds that even though all directly connected networks have been entered in the RIP configuration, not all routes are present. What is the most likely cause of this problem?
- Autosummarization is enabled on all routers.
- The split-horizon rule is disabled on all routers.
- RIP version 2 does not support classless routing.
- RIP version 1 should have been used instead of version 2.
- The 10.10.4.0 networks should be replaced with 192.168.4.0 networks.
177. A network technician needs to install a four-port switch module in an operational Cisco 1841 router that has an available HWIC slot. What should the technician do first?
- Turn off the power to the router before installing the new module.
- Install the hot-swappable four-port switch module directly into slot 1 of the 1841.
- Move the existing WIC-2T module to slot 1 and install the four-port module in slot 0.
- Shut down all Fast Ethernet ports on the router until the switch module installation is complete.
178. Refer to the exhibit. What does the TOR router do with traffic that is destined for a web server with an IP address of 172.18.10.24?
- The router sends the traffic out Serial 0/0/0.
- The router sends the traffic out all interfaces other than the one it came in on.
- The router places the packets into a queue until a better route is discovered via RIP.
- The router sends a request to neighboring routers for paths to the 172.18.10.0 network.
179. Which two values represent valid IPv6 addresses? (Choose two.)
- ::::1
- FF01::1
- 0:0:0:0:0:0:0:1
- 2001:DB8::47::2A4
- 2031:0000:04AC:3400:FFE3:0
180. Which two security best practices are recommended for a router deployed as a WAN endpoint? (Choose two.)
- Turn off unnecessary services.
- Enable HTTP for web administration.
- Configure easy to remember passwords.
- Apply timeouts on VTY, AUX, and console ports.
- Enable Telnet access to allow for remote management.
181. A wireless survey has been conducted before the deployment of a wireless network. What would be the benefit of the survey?
- provides initial configuration of the access points
- determines the channel settings of the access points
- determines the security settings on the access points
- finds the optimal number and placement of access points
182. Refer to the exhibit. An extended ACL has been created to deny traffic from the 192.168.35.0/24 network to the web server with IP address 209.165.201.15. According to Cisco best practices, where should the ACL be applied?
- RTB Fa0/0 inbound
- RTC S0/0/1 inbound
- RTD Fa0/0 outbound
- RTC S0/1/0 outbound
183. Refer to the exhibit. In the Cisco IOS filename that is shown, what is signified by the underlined portion?
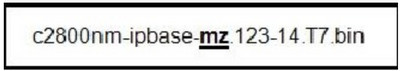
- version
- platform
- file format
- feature set
184. Refer to the exhibit. Which type of application communication model best describes this network?

- client-client
- client-server farm
- client-enterprise edge
- client-enterprise server
185. Refer to the exhibit. To provide better customer service, the network management decides to implement a new server farm, which is located in a data center. Which two technology implementations will address the requirements for strict security policies to prevent unauthorized access to the server farm? (Choose two.)
- Install firewalls and IDS capabilities on the network.
- Apply ACLs to permit only inbound TCP traffic to the servers.
- Apply filters that permit traffic only to required ports on the servers.
- Configure a flexible IP addressing structure that allocates a single subnet per VLAN.
- Configure a fast-converging routing protocol with authentication at the core layer.
- Create a management VLAN and provide access to the data center devices through Telnet.
186. If traditional phones are used when introducing VoIP to a network, what component would be required to convert the analog voice from traditional telephone signals into IP packets?
- Multipoint control unit
- Power over Ethernet switches
- a router that acts as a voice gateway
- Cisco Unified Communications Manager
