3.2.1.4 Lab – Investigate the FCC Database (Instructor Version)
Objectives
Use the Federal Communications Commission (FCC) database to view information about various IoT devices that utilize radio frequencies for data transmission. The database has information that could benefit both the user and a potential attacker.
- Part 1: Search for Information by FCC ID
- Part 2: Search for Information using the Advanced Search
Background / Scenario
IoT devices often use wireless technologies to communicate with various equipment including other IoT devices. The FCC requires companies that develop devices that use any form of radio frequency for transmission to register those devices and provide supporting information about the particular device. Tests must be performed to make certain that the devices conform to the rules established by the FCC. The FCC requires that device manufacturers visibly display their FCC ID on the device.
Required Resources
- PC or mobile device with Internet access
Part 1: Search for Information by FCC ID
Step 1: View device information by using the search feature.
a. Use the following link to access the FCC database search function:
https://www.fcc.gov/oet/ea/fccid
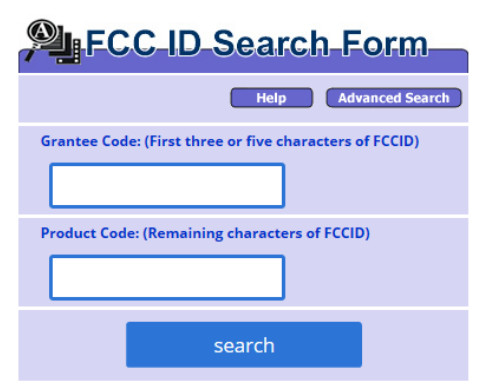
b. The search fields include a grantee code and a product code. The grantee code is either a 3 character or 5 character code stamped on the device. The example used here has the ID printed on the label as FCC ID: JNZYR0019. Because the ID provided does not specify how the number is separated attempt to put the first 3 characters in the Grantee Code text box and the remaining characters in the Product Code text box. Click the Search button. How many entries were displayed?
___________________________________________________________
There is one entry displayed at the time this lab was written.
What is the Applicant Name that is displayed?
___________________________________________________________
Logitech Far East Ltd
What other columns of information are available?
___________________________________________________________
View Form, Display Exhibits, Display Grant, Display Correspondence, Applicant Name, Address, City, State, Country, Zip Code, FCC ID, Application Purpose, Final Action Date, Lower Frequency in MHz, Upper Frequency in MHz.
c. Click the Summary link under the Display Exhibits column. Which Exhibit Types are marked as Permanent Confidential?
___________________________________________________________
Block Diagram, Operational Description, Schematics
d. Click the back button in your browser. Click the Detail link under the Display Exhibits column. A warning message displays informing you that the FCC does not guarantee the documents to be virus-free. If you have a current anti-virus application in place and have reason to trust the entity click OK to accept the warning. What Exhibit Types are available?
___________________________________________________________
Cover Letters, External Photos, ID/Location Info, Internal Photos, Test Report, Test Setup Photos, Users Manual
e. Click the Test Report attachment. Scroll down to page 6 to display the General Information. What is the Product that is displayed?
____________________________________________________________
2.4GHz Cordless Keyboard
What information is displayed about the Antenna Type?
____________________________________________________________
PCB printed antenna with 1.41dBi antenna gain
f. Scroll to the next page. How many channels are listed in the table? ______________________________
Channels 1-12
What is the frequency range? What technologies use this frequency range?
____________________________________________________________
2405-2474Mhz, Bluetooth and WiFi both use this range. This range is part of the Industrial, Scientific and Medical (ISM) radio bands.
g. Close the Test Report attachment. Click Internal Photos document. Scroll through the document, what kind of photos are displayed?
____________________________________________________________
A breakdown of the parts and components in the keyboard.
Is there a potential for an attack with this device? Please explain.
____________________________________________________________
Given the keyboard uses Bluetooth it could be possible for an attacker to capture data transmitted. It would also be possible for an attacker to modify the keyboard in some fashion to capture is being typed without the users knowledge. This could possibly be achieved by implanting some kind of recording device that makes use of the SPI_MOSI and SPI_MISO pins inside the keyboard. This keyboard could be used on many types of IoT devices.
Step 2: Search for information on a second device
a. Return to the FCC ID search screen. Enter the FCC ID: A3L-WIS09ABGN2. You may need to get creative on the entry in order to retrieve the information. Attempt to use the 3 or 5 character code. Pay attention to the message following the Product Code prompt. How many entries were returned? (Hint: Hyphen (-) is significant.)
_____________________________________________________________
There were 10 displayed at the time this lab was written.
b. Select one of the entries dated 8/20/2009. Click the Detail link. Click the link for Test Report 1. What is the equipment type? What is the model number and who is the applicant?
_____________________________________________________________
Equipment: Wireless LAN adapter, model: WIS09ABGN2, Applicant: Samsung Electronics
c. Scroll to Section 2 General Information. Based on the information in the Product Details and Table for Filed Antenna, which wireless standards are supported?
_____________________________________________________________
802.11a, 802.11b, 802.11g, 802.11n
d. Close the Test Report 1 document. Open the Internal Photos document. Scroll down to page C8 of C9. What chip is displayed? Why might this information be useful?
_____________________________________________________________
RaLink RT3572L, it could be beneficial in locating a driver.
Part 2: Search for Information using the Advanced Search
It is possible to search for devices within the FCC database without knowing the FCC ID. This part of the lab will offer some advice on narrowing the search pattern for more precise results.
Step 1: Search for a device without the FCC ID
In this search you will see what information is available for a Nest thermostat prior to purchasing one.
Return to the FCC ID search form. Click the Advanced Search button at the upper right of the dialog.
a. In the Applicant Name text box type Nest and then click Start Search near the bottom of the form. How many items were returned?
____________________________________________________________
There were 134 items at the time this lab was written.
b. With the large number of entries that were returned it would be best to provide a few more parameters. Return to the previous search screen by clicking the back button in your browser. Add the following search parameters:
1) Final Action Date Range (mm/dd/yyyy) 09/01/2016 to 04/30/2018
2) Application Purpose: Original Grant
3) Product Description: thermostat
How many items were returned?
____________________________________________________________
There were 7 items returned at the time this lab was written.
Select Details on any of the entries. How many documents are displayed for the thermostat?
____________________________________________________________
There were 12 documents returned at the time this lab was written.
Why are there multiple test reports?
____________________________________________________________
The thermostat is capable of communicating using multiple protocols. The protocols tested are WLAN (WiFi), BLE (Bluetooth Low Energy), and Zigbee.
Reflection
1. How could the information available in the FCC database be valuable when attempting to secure IoT devices?
_____________________________________________________________
Answers will vary. The primary areas to note would be the potential schematics and communication protocols.
2. How could the information available in the FCC database be valuable to an IoT attacker?
_____________________________________________________________
Answers will vary. Using the same information, we are attempting to secure areas that attackers are trying to exploit.
