4.3.1.6 Packet Tracer – Threat Modeling at the IoT Communication Layer (Instructor Version)
Topology
The topology is a home IoT system that has been prototyped in Packet Tracer. It shows a cutaway view of a home with different sensors, actuators, and connections shown.
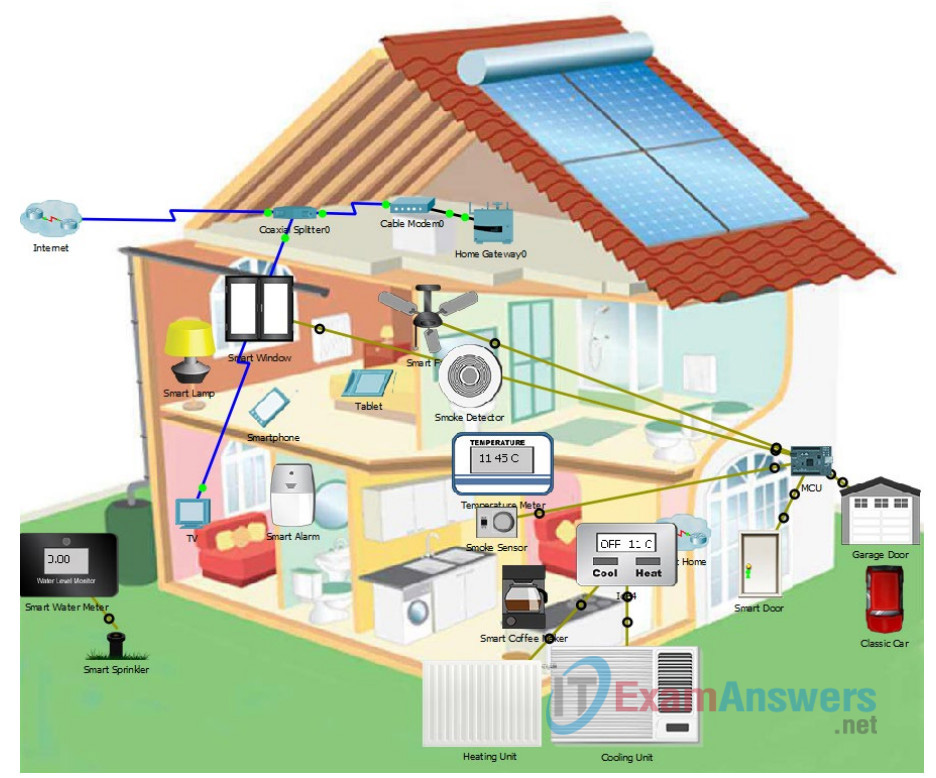
Objectives
In this Packet Tracer, you will begin the threat modeling process for the device layer of the IoT attack surface.
- Part 1: Diagraming the Communication Layer
- Part 2: Creating an Inventory of Assets of the Communication Layer Attack Surface
- Part 3: Identifying Potential Threats with the STRIDE Model
Background / Scenario
In this Packet Tracer, you will continue creating a threat model for the home automation IoT system that was started in the Chapter 3 Packet Tracer – Threat Modeling at the IoT Device Layer. You may want to review the description of the system and Packet Tracer file from that Packet Tracer.
You will be working with the communication layer of the IoT attack surface. Remember that the home automation network differs somewhat from the PT network. The home automation network that you are working with does not use Wi-Fi as the wireless protocol for the sensors and actuators. Instead, you will choose another protocol for the IoT sensor-actuator-controller network, such as Zigbee or Z-Wave. The controller handles local communication with the various wireless networks in the house and the Internet. It serves as the IP gateway for the IoT sensor-actuator network. It also functions as a router that enables communication between the local wireless LAN and the Internet.
Required Resources
- Packet Tracer 7.1 or later
Part 1: Diagraming the Communication Layer
Step 1: Choose a protocol for the sensor network.
Focus on the IoT communication layer protocols and infrastructure. Although the PT model uses Wi-Fi for communication between sensors, actuators and the IoT gateway, you will use another protocol for your analysis.
Choose a protocol that is commonly used in home automation networks for communication between sensors, actuators and the home IoT gateway. Keep security in mind.
What protocol did you choose and why did you choose it?
Zigbee is the popular choice for this one as it is efficient in power consuming and it is a two way data transfers between devices.
Step 2: Diagram the network.
Use your completed floorplan diagrams from the Threat Modeling at the IoT Device Layer Packet Tracer from Chapter 3. Additionally, you will complete the attic floorplan.
a. Complete the floorplan for the attic that is included in Appendix A of the PDF version of these Packet Tracer instructions. Add the network infrastructure devices and their connections as they are shown in the Packet Tracer network.
b. Add the network clients that are not IoT devices but are still connect to the IoT gateway.
c. Add data flows. It is not necessary to draw flows for every device, just a few representative devices is fine. In addition, when indicating connections between floors, it is fine to just write “Connected to…” at the top of a floorplan. Include several sensors and actuators, the smart phone and tablet, and the MCU.
Draw lines between the IoT devices, the IoT gateway, and the other network infrastructure components which are connected to one another. Use different colors for connections that use different protocols. Remember that some sensors and actuators may not be able to communicate directly with the IoT gateway due to power constraints. Label or color code the data flows according to the protocols in use.
What would allow any sensors and actuators that are out of range of the IoT gateway to communicate with it?
Using Zigbee the sensors and actuators can be still connected to the gateway if the Zigbee is within its range.
What other protocols are in use in the network? How could the tablet and the smart phone communicate?
Bluetooth protocols can be used, they are of low range, but it will fulfill the function
d. Add arrows to indicate the predominate direction of data flow. In some cases the flows will be mostly in one direction. In others they will be in two directions.
Which devices in the home automation network connect to the IoT Gateway?
The smart devices that is present in the home automation such as tablets, smart doors and windows and etc.
The smart devices that is present in the home automation such as tablets, smart doors and windows and etc.
Part 2: Creating an Inventory of Assets of the Communication Attack Surface
Another component of asset management is understanding the network protocols and infrastructure devices that are in use on the network. In this part of the Packet Tracer, you will compete a table for the all of the communication attack surface assets.
Step 1: List the communication networks and protocols.
Open the Packet Tracer activity and fill-in the table that is provided below. The table should include all the networks, protocols, and IP devices that are part of the home automation network system. Determine the communication relationships between assets. The network is a collection of things that uses the same protocol. It is not necessary to list every IoT device here. Instead, just refer to the wireless sensor-actuator network. This has been filled in for you.
Follow the instructions in the Packet Tracer activity to show the wireless network connections between devices if necessary. Feel free to move devices around to understand the wireless connections better. Pay attention to the color coding of the wireless connections.
| Network or Device | Protocol(s) | Communicates With |
|---|---|---|
| Part 2: Communications | ||
| Smart Solar Panel | GigaEthernet | Home Gateway |
| Smart Window | Wireless | MCU |
| TV | Coaxial | Coaxial Splitter |
| Temperatura medidor | Wireless | MCU |
| Smart Coffe Maker | Wireless | MCU |
Part 3: Identifying Potential Threats
In this part, you will identify threats using the STRIDE methodology. Try to describe as many threats as possible based on your experience in the course, the OWASP IoT vulnerabilities page, and other information sources.
Use the STRIDE model to create a list of potential threats.
Fill in the following table with threats for each category in the STRIDE threat model. Add potential threats that could occur for each STRIDE category. Include the type of threat using the OWASP terminology where possible. An extra STRIDE table is provided in Appendix B of the PDF version of these Packet Tracer instructions.
| Threat type | Network or Device | Threats |
|---|---|---|
| (S)poofing – can an attacker pretend to be someone he’s not, or falsify data? | sensor-actuator network | |
| Wireless | In a wireless network, sure, because it is in the air and any attacker could hack it. | |
| WSN | This network is the most common, therefore it would be the one that the attacker would have more success to falsify data in it. | |
| IPv6 | In this I think not since they are too small networks | |
| Wireless | Probably since this is used for small programs that only cover some functionality | |
| (T)ampering – can an attacker successfully inject falsified data into the system? | sensor-actuator network | |
| Wireless | In a wireless network, sure, because it is in the air and any attacker could hack it. | |
| IPv6 | This network is the most common, therefore it would be the one that the attacker would have more success to falsify data in it. | |
| WSN | In this I think not since they are too small networks | |
| Zolertia | Probably since this is used for small programs that only cover some functionality | |
| (R)epudiation – can a user pretend that a transaction didn’t happen? | sensor-actuator network | |
| IPv6 | Very sure yes, because IPv6 is a very common | |
| WSN | Yes, since this network specifies for actuators and sensors and can fake an action, without actually executing it | |
| Wireless | If you can manage to do that, therefore this network is not secure. | |
| Zolertia | Zolertia does not contain this type of functionalities | |
| (D)enial of Service – can the device be shut down or made unavailable maliciously? | sensor-actuator network | |
| WSN | Sure, it can hurt the actuators and damage them. | |
| Wireless | They can clearly “play” with the devices | |
| Zolertia | Yes, since it enters into the functionalities that this network has. | |
| IPv6 | It can damage the devices, to the point of short circuit. | |
| (E)scalation of Privilege – can users get access to privileged resources meant only for admins or superusers? | sensor-actuator network | |
| Wireless | Of course, this does not contain large firewalls and security services | |
| IPv6 | Does not have high security | |
| WSN | Yes, I could, but this one does not have reserved resources | |
| Domotica | Yes, because the home automation network is capable of automating a home by itself. |
Appendix A: Floor Plans
Attic:
Ground Floor Legend:
| Number | Room |
|---|---|
| 13 | attic |
Appendix B: STRIDE Table
| Threat type | Network or Device | Threats |
|---|---|---|
| (S)poofing – can an attacker pretend to be someone he’s not or falsify data | sensor-actuator network | |
| Wireless | Does not have high security | |
| IPv6 | This is low consumption which makes it easy to attack. | |
| WSN | This can be easily falsified data by accessing the firmware since this has antivirus or protection | |
| Wireless | It may become the easiest network to access. | |
| (T)ampering – can an attacker successfully inject tampered data into the system? | sensor-actuator network | |
| IPv6 | This network is the most common, therefore it would be the one that the attacker would have more success to falsify data in it. | |
| Wireless | In a wireless network, sure, because it is in the air and any attacker could hack it. | |
| WSN | In this I think not since they are too small networks | |
| Zolertia | Probably since this is used for small programs that only cover some functionality | |
| (R)epudiation – can a user pretend that a transaction didn’t happen? | sensor-actuator network | |
| IPv6 | Very sure yes, because IPv6 is a very common and without much security | |
| Wireless | Yes, since this network specifies for actuators and sensors and can fake an action, without actually executing it | |
| Zolertia | Zolertia does not contain this type of functionalities | |
| WSN | If you can manage to do that, therefore this network is not secure. | |
| (D)enial of Service – can the device be shut down or made unavailable maliciously? | sensor-actuator network | |
| Wireless | They can clearly “play” with the device | |
| Zolertia | Yes, since it enters into the functionalities that this network has. | |
| WSN | Sure, it can hurt the actuators and damage them. | |
| IPv6 | It can damage the devices, to the point of short circuit. | |
| (E)scalation of Privilege – can users get access to privileged resources meant only for admins or superusers? | sensor-actuator network | |
| Wireless | Of course, this does not contain large firewalls and security services | |
| IPv6 | It does not have high security, with which it has privileged data because it could not defend them | |
| WSN | Yes, I could, but this one does not have reserved resources | |
| Domotica | Yes, because the home automation network is capable of automating a home by itself. |
Download 4.3.1.6 Packet Tracer – Threat Modeling at the IoT Communication Layer
