Time limit: 0
Quiz-summary
0 of 25 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
Information
Good luck!
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 25 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- Answered
- Review
-
Question 1 of 25
1. Question
1 pointsAn administrator defined a local user account with a secret password on router R1 for use with SSH. Which three additional steps are required to configure R1 to accept only encrypted SSH connections? (Choose three.)Correct
Incorrect
-
Question 2 of 25
2. Question
1 pointsWhich set of commands are required to create a username of admin, hash the password using MD5, and force the router to access the internal username database when a user attempts to access the console?Correct
Incorrect
-
Question 3 of 25
3. Question
1 pointsRefer to the exhibit. Which statement about the JR-Admin account is true?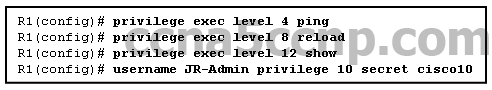 Correct
Correct
Incorrect
-
Question 4 of 25
4. Question
1 pointsWhich three areas of router security must be maintained to secure an edge router at the network perimeter? (Choose three.)Correct
Incorrect
-
Question 5 of 25
5. Question
1 pointsWhich recommended security practice prevents attackers from performing password recovery on a Cisco IOS router for the purpose of gaining access to the privileged EXEC mode?Correct
Incorrect
-
Question 6 of 25
6. Question
1 pointsRefer to the exhibit. Based on the output of the show running-config command, which type of view is SUPPORT?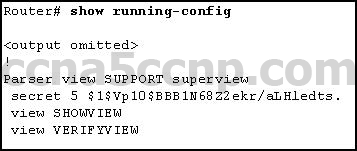 Correct
Correct
Incorrect
-
Question 7 of 25
7. Question
1 pointsWhich two characteristics apply to role-based CLI access superviews? (Choose two.)Correct
Incorrect
-
Question 8 of 25
8. Question
1 pointsWhich three types of views are available when configuring the role-based CLI access feature? (Choose three.)Correct
Incorrect
-
Question 9 of 25
9. Question
1 pointsIf AAA is already enabled, which three CLI steps are required to configure a router with a specific view? (Choose three.)Correct
Incorrect
-
Question 10 of 25
10. Question
1 pointsWhat occurs after RSA keys are generated on a Cisco router to prepare for secure device management?Correct
Incorrect
-
Question 11 of 25
11. Question
1 pointsWhich three statements describe limitations in using privilege levels for assigning command authorization? (Choose three.)Correct
Incorrect
-
Question 12 of 25
12. Question
1 pointsWhat command must be issued to enable login enhancements on a Cisco router?Correct
Incorrect
-
Question 13 of 25
13. Question
1 pointsWhat is the default privilege level of user accounts created on Cisco routers?Correct
Incorrect
-
Question 14 of 25
14. Question
1 pointsA network administrator notices that unsuccessful login attempts have caused a router to enter quiet mode. How can the administrator maintain remote access to the networks even during quiet mode?Correct
Incorrect
-
Question 15 of 25
15. Question
1 pointsWhat is a characteristic of the Cisco IOS Resilient Configuration feature?Correct
Incorrect
-
Question 16 of 25
16. Question
1 pointsWhat is a requirement to use the Secure Copy Protocol feature?Correct
Incorrect
-
Question 17 of 25
17. Question
1 pointsWhat is a characteristic of the MIB?Correct
Incorrect
-
Question 18 of 25
18. Question
1 pointsWhich three items are prompted for a user response during interactive AutoSecure setup? (Choose three.)Correct
Incorrect
-
Question 19 of 25
19. Question
1 pointsA network engineer is implementing security on all company routers. Which two commands must be issued to force authentication via the password 1A2b3C for all OSPF-enabled interfaces in the backbone area of the company network? (Choose two.)Correct
Incorrect
-
Question 20 of 25
20. Question
1 pointsWhat is the purpose of using the ip ospf message-digest-key key md5 password command and the area area-id authentication message-digest command on a router?Correct
Incorrect
-
Question 21 of 25
21. Question
1 pointsWhat are two reasons to enable OSPF routing protocol authentication on a network? (Choose two.)Correct
Incorrect
-
Question 22 of 25
22. Question
1 pointsWhich two options can be configured by Cisco AutoSecure? (Choose two.)Correct
Incorrect
-
Question 23 of 25
23. Question
1 pointsWhich three functions are provided by the syslog logging service? (Choose three.)Correct
Incorrect
-
Question 24 of 25
24. Question
1 pointsWhat is the Control Plane Policing (CoPP) feature designed to accomplish?Correct
Incorrect
-
Question 25 of 25
25. Question
1 pointsWhich three actions are produced by adding Cisco IOS login enhancements to the router login process? (Choose three.)Correct
Incorrect

Q19 should be answer 2 (level 1)