Time limit: 0
Quiz-summary
0 of 58 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
Information
CCNA Security v2.0 Practice Final Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 58 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- Answered
- Review
-
Question 1 of 58
1. Question
1 pointsWhich three areas of router security must be maintained to secure an edge router at the network perimeter? (Choose three.)Correct
Incorrect
Hint
There are three areas of router security to maintain:- physical security
- router hardening
- operating system security
-
Question 2 of 58
2. Question
1 pointsWhat is the purpose of AAA accounting?Correct
Incorrect
Hint
AAA accounting collects and reports usage data. This data can be used for such purposes as auditing or billing. AAA authentication is the process of verifying users are who they say they are. AAA authorization is what the users can and cannot do on the network after they are authenticated. -
Question 3 of 58
3. Question
1 pointsWhat service or protocol does the Secure Copy Protocol rely on to ensure that secure copy transfers are from authorized users?Correct
Incorrect
Hint
Secure Copy Protocol (SCP) is used to securely copy IOS images and configuration files to a SCP server. To perform this, SCP will use SSH connections from users authenticated through AAA. -
Question 4 of 58
4. Question
1 pointsWhich statement accurately describes Cisco IOS Zone-Based Policy Firewall operation?Correct
Incorrect
Hint
The pass action in CCP is similar to the permit parameter in an ACL entry. Pass allows traffic only in one direction. -
Question 5 of 58
5. Question
1 pointsWhich two statements describe the use of asymmetric algorithms? (Choose two.)Correct
Incorrect
Hint
Asymmetric algorithms use two keys: a public key and a private key. Both keys are capable of the encryption process, but the complementary matched key is required for decryption. If a public key encrypts the data, the matching private key decrypts the data. The opposite is also true. If a private key encrypts the data, the corresponding public key decrypts the data. -
Question 6 of 58
6. Question
1 pointsRefer to the exhibit. Based on the output generated by the show monitor session 1 command, how will SPAN operate on the switch?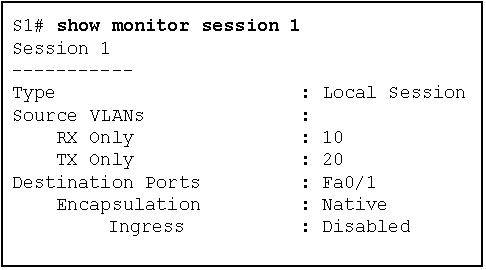 Correct
Correct
Incorrect
Hint
The show monitor session command is used to verify how SPAN is configured (what ports are involved in the traffic mirroring) -
Question 7 of 58
7. Question
1 pointsRefer to the exhibit. The ISAKMP policy for the IKE Phase 1 tunnel was configured, but the tunnel does not yet exist. Which action should be taken next before IKE Phase 1 negotiations can begin?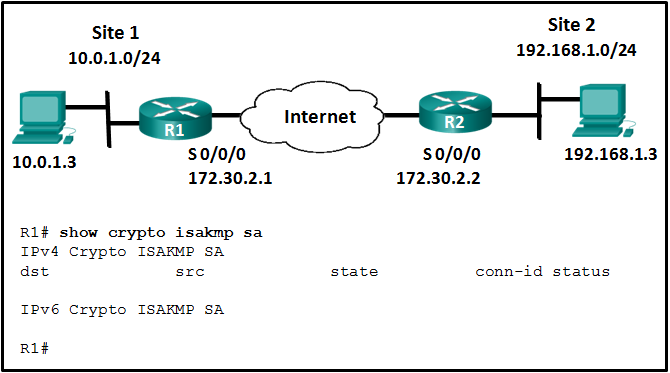 Correct
Correct
Incorrect
Hint
Although the ISAKMP policy for the IKE Phase 1 tunnel is configured, the tunnel does not yet exist as verified with the show crypto isakmp sa command. Interesting traffic must be detected before IKE Phase 1 negotiations can begin. To define interesting traffic, each router has to be configured with an ACL to permit traffic from the local LAN to the remote LAN. -
Question 8 of 58
8. Question
1 pointsWhat ports can receive forwarded traffic from an isolated port that is part of a PVLAN?Correct
Incorrect
Hint
PVLANs are used to provide Layer 2 isolation between ports within the same broadcast domain. The level of isolation can be specified with three types of PVLAN ports:- Promiscuous ports that can forward traffic to all other ports
- Isolated ports that can only forward traffic to promiscuous ports
- Community ports that can forward traffic to other community ports and promiscuous ports
-
Question 9 of 58
9. Question
1 pointsWhat is the next step in the establishment of an IPsec VPN after IKE Phase 1 is complete?Correct
Incorrect
Hint
Establishing an IPsec tunnel involves five steps:- detection of interesting traffic defined by an ACL
- IKE Phase 1 in which peers negotiate ISAKMP SA policy
- IKE Phase 2 in which peers negotiate IPsec SA policy
- Creation of the IPsec tunnel
- Termination of the IPsec tunnel
-
Question 10 of 58
10. Question
1 pointsWhat is an advantage of HIPS that is not provided by IDS?Correct
Incorrect
Hint
Network-based IDS (NIDS) sensors are typically deployed in offline mode. They do not protect individual hosts. Host-based IPS (HIPS) is software installed on a single host to monitor and analyze suspicious activity. It can monitor and protect operating system and critical system processes that are specific to that host. HIPS can be thought of as a combination of antivirus software, antimalware software, and a firewall. -
Question 11 of 58
11. Question
1 pointsWhich interface setting can be configured in ASDM through the Device Setup tab?Correct
Incorrect
Hint
In the Device Setup tab, the ASA Layer 3 interfaces can be created, edited, or deleted. Name, security level, and IP address are some of the settings that can be configured on an interface. There is no NAT, port security, or EtherChannel configuration in this tab. -
Question 12 of 58
12. Question
1 pointsA security technician uses an asymmetric algorithm to encrypt messages with a private key and then forwards that data to another technician. What key must be used to decrypt this data?Correct
Incorrect
Hint
Asymmetric algorithms use two keys. if a public key encrypts the data, the matching private key decrypts the data. The opposite is also true. If a private key encrypts the data, the corresponding public key decrypts the data. -
Question 13 of 58
13. Question
1 pointsOn what switch ports should PortFast be enabled to enhance STP stability?Correct
Incorrect
Hint
PortFast will immediately bring an interface configured as an access or trunk port to the forwarding state from a blocking state, bypassing the listening and learning states. If configured on a trunk link, immediately transitioning to the forwarding state could lead to the formation of Layer 2 loops. -
Question 14 of 58
14. Question
1 pointsWhat is the function of the Hashed Message Authentication Code (HMAC) algorithm in setting up an IPsec VPN?Correct
Incorrect
Hint
The IPsec framework uses various protocols and algorithms to provide data confidentiality, data integrity, authentication, and secure key exchange. The Hashed Message Authentication Code (HMAC) is a data integrity algorithm that uses a hash value to guarantee the integrity of a message. -
Question 15 of 58
15. Question
1 pointsWhat are three characteristics of the RADIUS protocol? (Choose three.)Correct
Incorrect
Hint
RADIUS is an open-standard AAA protocol using UDP port 1645 or 1812 for authentication and UDP port 1646 or 1813 for accounting. It combines authentication and authorization into one process; thus, a password is encrypted for transmission while the rest of the packet will be sent in plain text. RADIUS offers the expedited service and more comprehensive accounting desired by remote-access providers but provides lower security and less potential for customization than TACACS+. -
Question 16 of 58
16. Question
1 pointsA network administrator is configuring an AAA server to manage TACACS+ authentication. What are two attributes of TACACS+ authentication? (Choose two.)Correct
Incorrect
Hint
TACACS+ authentication includes the following attributes:- Separates authentication and authorization processes
- Encrypts all communication, not just passwords
- Utilizes TCP port 49
-
Question 17 of 58
17. Question
1 pointsWhat technology is used to separate physical interfaces on the ASA 5505 device into different security zones?Correct
Incorrect
Hint
For an ASA 5505, common deployments use a specific VLAN with a higher security level for an inside network and a separate VLAN with a lower security level for the outside network. -
Question 18 of 58
18. Question
1 pointsHow are Intrusion Prevention System (IPS) and Intrusion Detection System (IDS) components used conjunctively?Correct
Incorrect
Hint
IDS sensors are typically deployed in offline mode. Although they do not stop the triggered packets immediately, they have no impact on network performance and hence can be configured to identify a broader scope of activities. IPS sensors can be configured to perform a packet drop to stop the trigger packet. However, because they are deployed inline, inspection of heavy traffic flow could have a negative impact on network performance. IDS and IPS technologies can complement each other. For example, an IDS can be implemented to validate IPS operation because the IDS can be configured for deeper packet inspection offline. This allows the IPS to focus on fewer but more critical traffic patterns inline. -
Question 19 of 58
19. Question
1 pointsWhat is the result of a DHCP starvation attack?Correct
Incorrect
Hint
DCHP starvation attacks are launched by an attacker with the intent to create a DoS for DHCP clients. To accomplish this goal, the attacker uses a tool that sends many DHCPDISCOVER messages to lease the entire pool of available IP addresses, thus denying them to legitimate hosts. -
Question 20 of 58
20. Question
1 pointsWhich router component determines the number of signatures and engines that can be supported in an IPS implementation?Correct
Incorrect
Hint
The number of signatures and engines that can be adequately supported depends on the amount of available memory . -
Question 21 of 58
21. Question
1 pointsWhat algorithm is used with IPsec to provide data confidentiality?Correct
Incorrect
Hint
The IPsec framework uses various protocols and algorithms to provide data confidentiality, data integrity, authentication, and secure key exchange. Two popular algorithms that are used to ensure that data is not intercepted and modified (data integrity) are MD5 and SHA. AES is an encryption protocol and provides data confidentiality. DH (Diffie-Hellman) is an algorithm that is used for key exchange. RSA is an algorithm that is used for authentication. -
Question 22 of 58
22. Question
1 pointsWhen configuring SSH on a router to implement secure network management, a network engineer has issued the login local and transport input ssh line vty commands. What three additional configuration actions have to be performed to complete the SSH configuration? (Choose three.)Correct
Incorrect
Hint
SSH is automatically enabled after the RSA keys are generated. Setting user privilege levels and configuring role-based CLI access are good security practices but are not a requirement of implementing SSH. -
Question 23 of 58
23. Question
1 pointsWhat can be used as an alternative to HMAC?Correct
Incorrect
Hint
Both HMAC and digital signatures are used to guarantee that messages are authentic. MD5 and SHA are considered legacy algorithms that should be avoided because they have security flaws. Encryption algorithms ensure data confidentiality rather than authentication. -
Question 24 of 58
24. Question
1 pointsHow can DHCP spoofing attacks be mitigated?Correct
Incorrect
Hint
One of the procedures to prevent a VLAN hopping attack is to disable DTP (auto trunking) negotiations on nontrunking ports. DHCP spoofing attacks can be mitigated by using DHCP snooping on trusted ports. The ip verify source interface configuration command is used to enable IP Source Guard on untrusted ports to protect against MAC and IP address spoofing. -
Question 25 of 58
25. Question
1 pointsA network administrator is configuring an AAA server to manage RADIUS authentication. Which two features are included in RADIUS authentication? (Choose two.)Correct
Incorrect
Hint
RADIUS authentication supports the following features:- RADIUS authentication and authorization as one process
- Encrypts only the password
- Utilizes UDP
- Supports remote-access technologies, 802.1X, and Session Initiation Protocol (SIP)
-
Question 26 of 58
26. Question
1 pointsA syslog server has received the message shown.*Mar 1 00:07:18.783: %SYS-5-CONFIG_I: Configured from console by vty0 (172.16.45.1)
What can be determined from the syslog message?Correct
Incorrect
Hint
The message shown is a level 5 Log_Notice and displays that a user with an IP address of 172.16.45.1 has configured this device remotely. -
Question 27 of 58
27. Question
1 pointsWhat is the default preconfigured security level for the outside network interface on a Cisco ASA 5505?Correct
Incorrect
Hint
By default the Cisco ASA ships with two interfaces preconfigured: interface VLAN 1 for the inside network with a security level of 100 and VLAN 2 for outside network with a security level of 0. -
Question 28 of 58
28. Question
1 pointsWhat term describes a set of rules used by an IDS or IPS to detect typical intrusion activity?Correct
Incorrect
Hint
A signature is a set of rules that an IDS and an IPS use to detect typical intrusion activity, such as DoS attacks. These signatures uniquely identify specific worms, viruses, protocol anomalies, and malicious traffic. -
Question 29 of 58
29. Question
1 pointsWhich type of VLAN-hopping attack may be prevented by designating an unused VLAN as the native VLAN?Correct
Incorrect
Hint
Spoofing DTP messages forces a switch into trunking mode as part of a VLAN-hopping attack, but VLAN double tagging works even if trunk ports are disabled. Changing the native VLAN from the default to an unused VLAN reduces the possibility of this type of attack. DHCP spoofing and DHCP starvation exploit vulnerabilities in the DHCP message exchange. -
Question 30 of 58
30. Question
1 pointsWhich statement describes the Cisco Cloud Web Security?Correct
Incorrect
Hint
The Cisco Cloud Web Security (CWS) is a cloud-based security service that uses web proxies in the Cisco cloud environment to scan traffic for malware and policy enforcement. It is not a firewall or web server solution. The Cisco Web Security Appliance (WSA) combines multiple security solutions to provide an all-in-one solution on a single platform to address the challenges of securing and controlling web traffic. -
Question 31 of 58
31. Question
1 pointsWhy is Diffie-Hellman algorithm typically avoided for encrypting data?Correct
Incorrect
-
Question 32 of 58
32. Question
1 pointsWhat information does the SIEM network security management tool provide to network administrators?Correct
Incorrect
-
Question 33 of 58
33. Question
1 pointsWhat can be configured as part of a network object?Correct
Incorrect
-
Question 34 of 58
34. Question
1 pointsA user complains about not being able to gain access to the network. What command would be used by the network administrator to determine which AAA method list is being used for this particular user as the user logs on?Correct
Incorrect
-
Question 35 of 58
35. Question
1 pointsWhat is a limitation to using OOB management on a large enterprise network?Correct
Incorrect
-
Question 36 of 58
36. Question
1 pointsA company deploys a network-based IPS. Which statement describes a false negative alarm that is issued by the IPS sensor?Correct
Incorrect
-
Question 37 of 58
37. Question
1 pointsWhat type of ACL offers greater flexibility and control over network access?Correct
Incorrect
-
Question 38 of 58
38. Question
1 pointsWhich security document includes implementation details, usually with step-by-step instructions and graphics?Correct
Incorrect
-
Question 39 of 58
39. Question
1 pointsWhat is a characteristic of a DMZ zone?Correct
Incorrect
-
Question 40 of 58
40. Question
1 pointsWhich type of ASDM connection would provide secure remote access for remote users into corporate networks?Correct
Incorrect
-
Question 41 of 58
41. Question
1 pointsWhich three forwarding plane services and functions are enabled by the Cisco AutoSecure feature? (Choose three.)Correct
Incorrect
-
Question 42 of 58
42. Question
1 pointsWhich feature of the Cisco Network Foundation Protection framework prevents a route processor from being overwhelmed by unnecessary traffic?Correct
Incorrect
-
Question 43 of 58
43. Question
1 pointsWhat three tasks can a network administrator accomplish with the Nmap and Zenmap security testing tools? (Choose three.)Correct
Incorrect
-
Question 44 of 58
44. Question
1 pointsWhich two end points can be on the other side of an ASA site-to-site VPN configured using ASDM? (Choose two.)Correct
Incorrect
-
Question 45 of 58
45. Question
1 pointsA company deploys a hub-and-spoke VPN topology where the security appliance is the hub and the remote VPN networks are the spokes. Which VPN method should be used in order for one spoke to communicate with another spoke through the single public interface of the security appliance?Correct
Incorrect
-
Question 46 of 58
46. Question
1 pointsWhich two types of hackers are typically classified as grey hat hackers? (Choose two.)Correct
Incorrect
-
Question 47 of 58
47. Question
1 pointsWhich security implementation will provide management plane protection for a network device?Correct
Incorrect
-
Question 48 of 58
48. Question
1 pointsA security technician is evaluating a new operations security proposal designed to limit access to all servers. What is an advantage of using network security testing to evaluate the new proposal?Correct
Incorrect
-
Question 49 of 58
49. Question
1 pointsWhich feature is specific to the Security Plus upgrade license of an ASA 5505 and provides increased availability?Correct
Incorrect
-
Question 50 of 58
50. Question
1 pointsWhat is a characteristic of an ASA site-to-site VPN?Correct
Incorrect
-
Question 51 of 58
51. Question
1 pointsWhat is a result of enabling the Cisco IOS image resilience feature?Correct
Incorrect
-
Question 52 of 58
52. Question
1 pointsWhat does the keyword default specify when used with the aaa authentication login command?Correct
Incorrect
-
Question 53 of 58
53. Question
1 pointsWhat are two protocols that are used by AAA to authenticate users against a central database of usernames and password? (Choose two.)Correct
Incorrect
-
Question 54 of 58
54. Question
1 pointsWhich service should be disabled on a router to prevent a malicious host from falsely responding to ARP requests with the intent to redirect the Ethernet frames?Correct
Incorrect
-
Question 55 of 58
55. Question
1 pointsWhat is a characteristic of asymmetric algorithms?Correct
Incorrect
-
Question 56 of 58
56. Question
1 pointsWhat are two drawbacks in assigning user privilege levels on a Cisco router? (Choose two.)Correct
Incorrect
-
Question 57 of 58
57. Question
1 pointsWhich service is added to the Cisco ASA 5500 by the ASA 5500-X?Correct
Incorrect
-
Question 58 of 58
58. Question
1 pointsA network analyst inserts a USB drive into an ASA 5506-X device. How is the external storage treated by the IOS?Correct
Incorrect
