Lab 5.5.3 – Troubleshooting Access Control Lists (Answers)
Topology Diagram
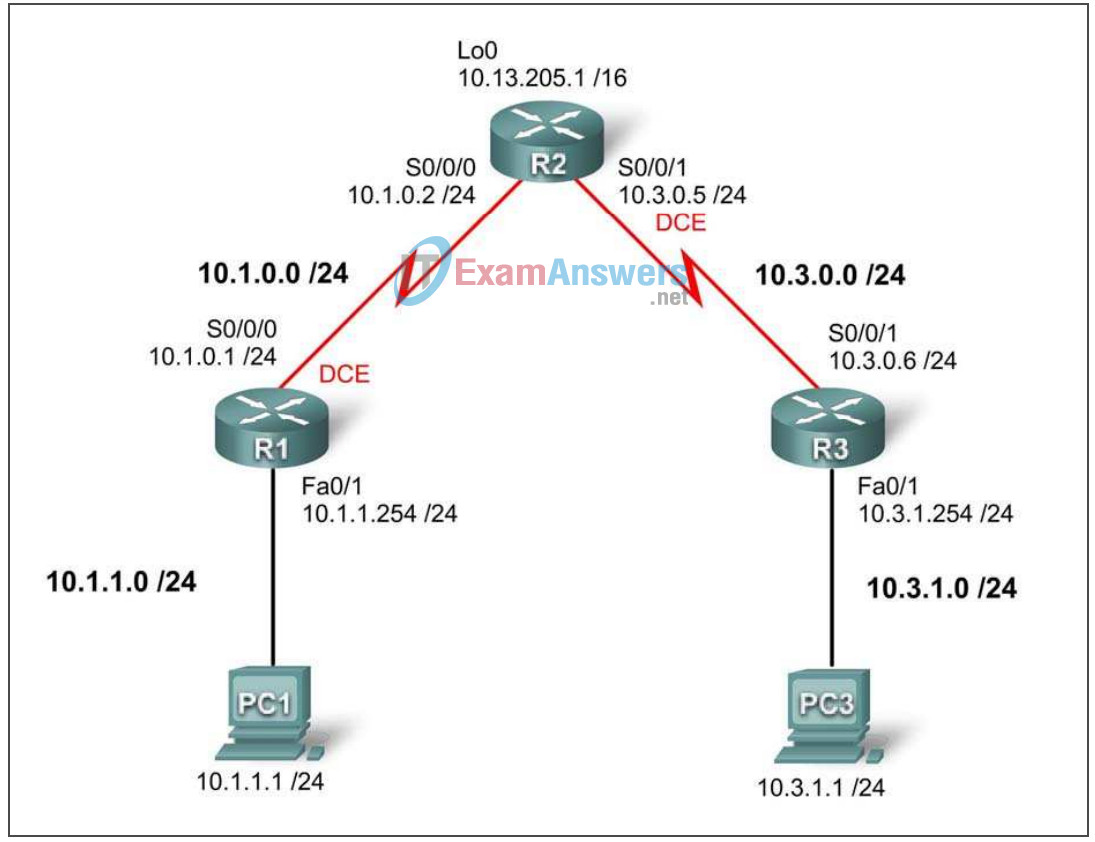
Addressing Table
| Device | Interface | IP Address | Subnet Mask | Default Gateway |
|---|---|---|---|---|
| R1 | S0/0/0 | 10.1.0.1 | 255.255.255.0 | |
| Fa0/1 | 10.1.1.254 | 255.255.255.0 | ||
| R2 | S0/0/0 | 10.1.0.2 | 255.255.255.0 | |
| S0/0/1 | 10.3.0.5 | 255.255.255.0 | ||
| Lo 0 | 10.13.205.1 | 255.255.0.0 | ||
| R3 | S0/0/1 | 10.3.0.6 | 255.255.255.0 | |
| Fa0/1 | 10.3.1.254 | 255.255.255.0 | ||
| PC1 | NIC | 10.1.1.1 | 255.255.255.0 | 10.1.1.254 |
| PC3 | NIC | 10.3.1.1 | 255.255.255.0 | 10.3.1.254 |
Learning Objectives
To complete this lab:
- Cable a network according to the topology diagram
- Erase the startup configuration and reload a router to the default state
- Load routers with scripts
- Find and correct network errors
- Document the corrected network
Scenario
You work for a regional service provider that has customers who have recently experienced several security breaches. Some security policies have been implemented that haven’t addressed the specific needs of the customers. Your department has been asked to examine the configuration, conduct tests and change the configuration as necessary to secure the customer routers.
Ensure that your final configurations implement the following security policies:
- R1 and R3 customers request that only local PCs are able to access VTY lines. Log any attempts by other devices to access the VTY lines.
- R1 and R3 directly connected networks should not be allowed to send or receive traffic to each other. All other traffic should be allowed to and from R1 and R3.
A minimum of ACL statements should be used and applied inbound on the R2 serial interfaces. OSPF is used to distribute routing information. All passwords, except the enable secret password, are set to cisco. The enable secret password is set to class.
Task 1: Load Routers with the Supplied Scripts
[Instructor note: These commands can be loaded into the router by the instructor or by the students. They are not included in the student version of the lab.]
R1
hostname R1 enable secret class no ip domain lookup ! interface FastEthernet0/1 ip address 10.1.1.254 255.255.255.0 no shutdown ! interface Serial0/0/0 ip address 10.1.0.1 255.255.255.0 clock rate 125000 no shutdown ip access-group VTY-Local out ! router ospf 1 network 10.1.0.0 0.0.0.255 area 0 network 10.1.1.0 0.0.0.255 area 0 ! ip access-list standard VTY-Local deny any log permit 10.1.1.0 0.0.0.255 ! banner motd ^Unauthorized access strictly prohibited, violators will be prosecuted to the full extent of the law.^ ! line con 0 password cisco logging synchronous login line aux 0 line vty 0 4 password cisco login
R2
hostname R2 enable secret class ! interface Loopback0 ip address 10.13.205.1 255.255.0.0 ! interface Serial0/0/0 ip address 10.1.0.2 255.255.255.0 no shutdown ip access-group block-R3 in ! interface Serial0/0/1 ip address 10.3.0.5 255.255.255.0 clock rate 125000 no shutdown ip access-group block-R1 out ! router ospf 1 network 10.1.0.0 0.0.0.255 area 0 network 10.3.0.0 0.0.0.255 area 0 network 10.13.0.0 0.0.255.255 area 0 ! ip access-list extended block-R1 deny ip 10.1.1.0 0.0.0.255 10.3.0.0 0.0.0.255 permit ip any any ! ip access-list extended block-R3 deny ip 10.3.0.0 0.0.1.255 10.1.0.0 0.0.1.255 ! banner motd ^Unauthorized access strictly prohibited, violators will be prosecuted to the full extent of the law.^ ! line con 0 password cisco logging synchronous login ! line vty 0 4 password cisco login
R3
hostname R3 enable secret class no ip domain lookup ! interface FastEthernet0/1 ip address 10.3.1.254 255.255.255.0 no shutdown ! interface Serial0/0/1 ip address 10.3.0.6 255.255.255.0 no shutdown ! router ospf 1 network 10.3.0.0 0.0.0.255 area 0 network 10.3.1.0 0.0.0.255 area 0 ! ip access-list standard VTY-Local permit 10.3.11.0 0.0.0.255 deny any log ! banner motd ^Unauthorized access strictly prohibited, violators will be prosecuted to the full extent of the law.^ ! line con 0 password cisco logging synchronous login ! line vty 0 4 access-class VTY-Local in password cisco login
Task 2: Find and Correct Network Errors
Find and correct all errors in the configuration. Document the steps you used to troubleshoot the network and note each error found.
Task 3: Document the Corrected Network
Now that you have corrected all errors and tested connectivity throughout the network, document the final configuration for each device.
R1
hostname R1 enable secret class no ip domain lookup ! interface FastEthernet0/1 ip address 10.1.1.254 255.255.255.0 ! interface Serial0/0/0 ip address 10.1.0.1 255.255.255.0 clockrate 125000 ! router ospf 1 log-adjacency-changes network 10.1.0.0 0.0.0.255 area 0 network 10.1.1.0 0.0.0.255 area 0 ! ip access-list standard VTY-Local permit 10.1.1.0 0.0.0.255 deny any log ! banner motd ^Unauthorized access strictly prohibited, violators will be prosecuted to the full extent of the law.^ ! line con 0 password cisco logging synchronous login ! line vty 0 4 access-class VTY-Local in password cisco login !
R2
hostname R2 enable secret class ! interface Loopback0 ip address 10.13.205.1 255.255.0.0 ! interface Serial0/0/0 ip address 10.1.0.2 255.255.255.0 ip access-group block-R1 in ! interface Serial0/0/1 ip address 10.3.0.6 255.255.255.0 clockrate 125000 ip access-group block-R3 in ! router ospf 1 log-adjacency-changes network 10.1.0.0 0.0.0.255 area 0 network 10.3.0.0 0.0.0.255 area 0 network 10.13.0.0 0.0.255.255 area 0 ! ip access-list extended block-R1 deny ip 10.1.0.0 0.0.1.255 10.3.0.0 0.0.1.255 permit ip any any ! ip access-list extended block-R3 deny ip 10.3.0.0 0.0.1.255 10.1.0.0 0.0.1.255 permit ip any any ! banner motd ^Unauthorized access strictly prohibited, violators will be prosecuted to the full extent of the law.^ ! line con 0 password cisco logging synchronous login ! line vty 0 4 password cisco login !
R3
hostname R3 enable secret class no ip domain lookup ! interface FastEthernet0/1 ip address 10.3.1.254 255.255.255.0 ! interface Serial0/0/1 ip address 10.3.0.5 255.255.255.0 ! router ospf 1 network 10.3.0.0 0.0.0.255 area 0 network 10.3.1.0 0.0.0.255 area 0 ! ip access-list standard VTY-Local permit 10.3.1.0 0.0.0.255 deny any log ! banner motd ^Unauthorized access strictly prohibited, violators will be prosecuted to the full extent of the law.^ ! line con 0 password cisco logging synchronous login ! line vty 0 4 access-class VTY-Local in password cisco login
Task 4: Clean Up
Erase the configurations and reload the routers. Disconnect and store the cabling. For PC hosts that are normally connected to other networks, such as the school LAN or the Internet, reconnect the appropriate cabling and restore the TCP/IP settings.
