Lab 4.6.2 – Challenge Security Configuration (Answers)
Topology Diagram
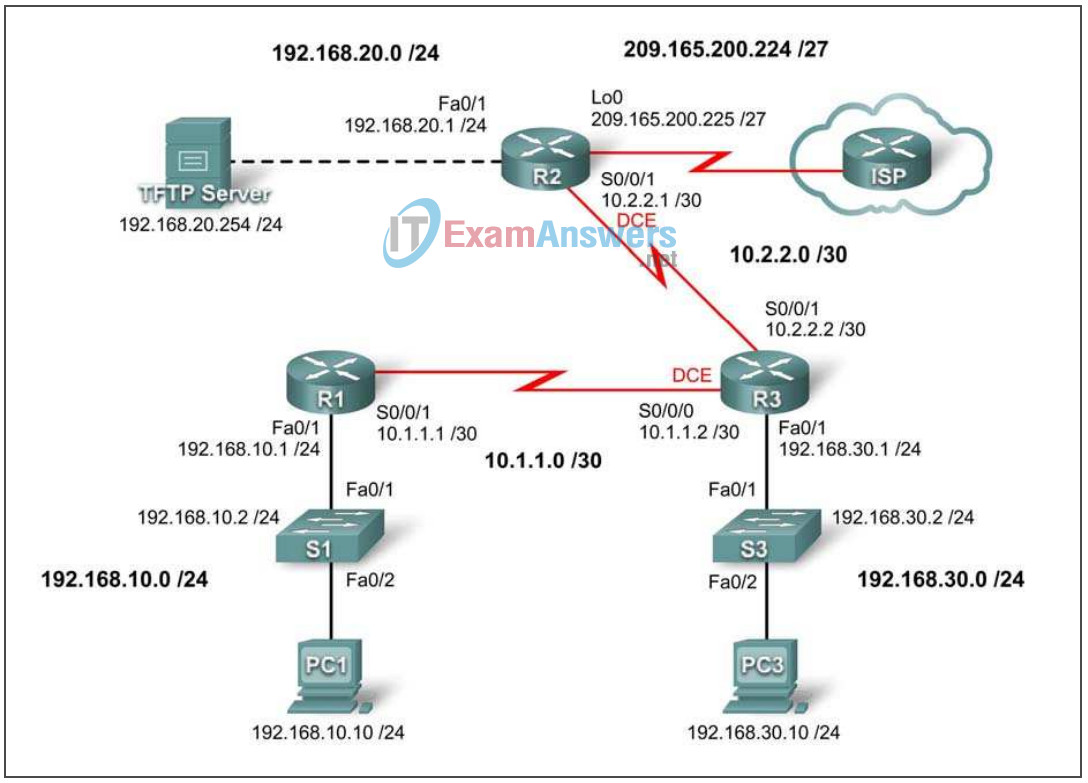
Addressing Table
| Device | Interface | IP Address | Subnet Mask | Default Gateway |
|---|---|---|---|---|
| R1 | Fa0/1 | 192.168.10.1 | 255.255.255.0 | N/A |
| S0/0/1 | 10.1.1.1 | 255.255.255.252 | N/A | |
| R2 | Fa0/1 | 192.168.20.1 | 255.255.255.0 | N/A |
| S0/0/1 | 10.2.2.1 | 255.255.255.252 | N/A | |
| Lo0 | 209.165.200.225 | 255.255.255.224 | N/A | |
| R3 | Fa0/1 | 192.168.30.1 | 255.255.255.0 | N/A |
| S0/0/1 | 10.2.2.2 | 255.255.255.252 | N/A | |
| S0/0/0 | 10.1.1.2 | 255.255.255.252 | N/A | |
| S1 | VLAN10 | 192.168.10.2 | 255.255.255.0 | N/A |
| S3 | VLAN30 | 192.168.30.2 | 255.255.255.0 | N/A |
| PC1 | NIC | 192.168.10.10 | 255.255.255.0 | 192.168.10.1 |
| PC3 | NIC | 192.168.30.10 | 255.255.255.0 | 192.168.30.1 |
| TFTP Server | NIC | 192.168.20.254 | 255.255.255.0 | 192.168.20.1 |
Learning Objectives
Upon completion of this lab, you will be able to:
- Cable a network according to the topology diagram
- Erase the startup configuration and reload a router to the default state
- Perform basic configuration tasks on a router
- Configure and activate interfaces
- Configuring basic router security
- Disable unused Cisco services and interfaces
- Protect enterprise networks from basic external and internal attacks
- Understand and manage Cisco IOS configuration files and Cisco file system
- Set up and use Cisco SDM (Security Device Manager) to configure basic router security.
Scenario
In this lab, you will configure security using the network shown in the topology diagram. If you need assistance, refer to the Basic Security lab. However, try to do as much on your own as possible. For this lab, do not use password protection or login on any console lines because they might cause accidental logout. However, you should still secure the console line using other means. Use ciscoccna for all passwords in this lab.
Task 1: Prepare the Network
Step 1: Cable a network that is similar to the one in the topology diagram.
Step 2: Clear any existing configurations on the routers.
Task 2: Perform Basic Router Configurations
Step 1: Configure routers.
Configure the R1, R2, and R3 routers according to the following guidelines:
- Configure the router hostname according to the topology diagram.
- Disable DNS lookup.
- Configure a message-of-the-day banner.
- Configure IP addresses on interfaces on R1, R2, and R3.
- Enable RIPv2 on all routers for all networks.
- Create a loopback interface on R2 to simulate the connection to the Internet.
- Create VLANs on switch S1 and S3 and configure the respective interfaces to participate in the VLANs
- Configure router R3 for SDM secure connectivity
- Install SDM on either PC3 or R3 if it is not installed already
Step 2: Configure Ethernet interfaces.
Configure the Ethernet interfaces of PC1, PC3, and TFTP Server with the IP addresses and default gateways from the addressing table at the beginning of the lab.
Step 3: Test the PC configuration by pinging the default gateway from each PC and the TFPT server.
Task 3: Secure Access to Routers
Step 1: Configure secure passwords and AAA authentication using a local database.
Create a secure password for router access. Create the username ccna to store locally on the router. Configure the router to use the local authentication database. Remember to use ciscoccna for all passwords in this lab.
service password-encryption enable secret ciscoccna username ccna password ciscoccna aaa new-model aaa authentication login local_auth local
Step 2: Secure the console the vty lines.
Configure the console and vty lines to block a user who enters an incorrect username and password five times within 2 minutes. Block additional login attempts for 2 minutes.
line con 0 exec-timeout 5 0 transport output telnet line vty 0 4 login authentication local_auth transport input telnet login block-for 300 attempt 2 within 120 security authentication failure rate 10 log
Step 3: Verify that connection attempts are denied after the failed attempt limit is reached.
R2:
R2#telnet 10.1.1.1
Trying 10.1.1.1 ... Open
Unauthorized access strictly prohibited, violators will be prosecuted
to the full extent of the law
User Access Verification
Username: cisco
Password:
% Authentication failed
User Access Verification
Username: cisco
Password:
% Authentication failed
[Connection to 10.1.1.1 closed by foreign host]
R2#telnet 10.1.1.1
Trying 10.1.1.1 ...
% Connection refused by remote host
R1:
*Sep 10 12:40:11.211: %SEC_LOGIN-5-QUIET_MODE_OFF: Quiet Mode is OFF, because block period timed out at 12:40:11 UTC Mon Sep 10 2007
Task 4: Secure Access to the Network
Step 1: Secure the RIP routing protocol.
Do not send RIP updates to non-network routers (any router not in this scenario.) Authenticate RIP updates and encrypt them.
R1:
key chain RIP_KEY key 1 key-string cisco ! int s0/0/0 ip rip authentication mode md5 ip rip authentication key-chain RIP_KEY ! router rip version 2 passive-interface default no passive-interface s0/0/0 network 10.0.0.0 network 192.168.10.0 no auto-summary
R2:
key chain RIP_KEY key 1 key-string cisco ! int s0/0/1 ip rip authentication mode md5 ip rip authentication key-chain RIP_KEY ! router rip version 2 passive-interface default no passive-interface s0/0/1 network 10.0.0.0 network 192.168.20.0 no auto-summary
R3:
key chain RIP_KEY key 1 key-string cisco ! int s0/0/1 ip rip authentication mode md5 ip rip authentication key-chain RIP_KEY ! int s0/0/0 ip rip authentication mode md5 ip rip authentication key-chain RIP_KEY ! router rip version 2 passive-interface default no passive-interface s0/0/0 no passive-interface s0/0/1 network 10.0.0.0 network 192.168.30.0 no auto-summary
Step 2: Verify that RIP routing still works.
R1:
R1#show ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is not set R 192.168.30.0/24 [120/2] via 10.1.1.2, 00:00:16, Serial0/0/1 C 192.168.10.0/24 is directly connected, FastEthernet0/1 R 192.168.20.0/24 [120/1] via 10.1.1.2, 00:00:13, Serial0/0/1 10.0.0.0/8 is variably subnetted, 2 subnets, 1 masks R 10.2.2.0/24 [120/1] via 10.1.0.2, 00:00:16, Serial0/0/1 C 10.1.1.0/24 is directly connected, Serial0/0/1
R2:
R2#show ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is not set R 192.168.30.0/24 [120/2] via 10.2.2.2, 00:00:16, Serial0/0/1 C 192.168.20.0/24 is directly connected, FastEthernet0/1 R 192.168.10.0/24 [120/1] via 10.2.2.2, 00:00:13, Serial0/0/1 10.0.0.0/8 is variably subnetted, 2 subnets, 1 masks R 10.1.1.0/24 [120/1] via 10.1.0.2, 00:00:16, Serial0/0/1 C 10.2.2.0/24 is directly connected, Serial0/0/1 C 209.165.200.224 is directly connected, Loopback0
R3:
R3#show ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is not set R 192.168.10.0/24 [120/2] via 10.1.1.1, 00:00:16, Serial0/0/1 C 192.168.30.0/24 is directly connected, FastEthernet0/1 R 192.168.20.0/24 [120/1] via 10.2.2.1, 00:00:13, Serial0/0/0 10.0.0.0/8 is variably subnetted, 2 subnets, 1 masks C 10.2.2.0/24 is directly connected, Serial0/0/0 C 10.1.1.0/24 is directly connected, Serial0/0/1
Task 5: Logging Activity with SNMP (Simple Network Management Protocol)
Step 1: Configure SNMP logging to the syslog server at 192.168.10.250 on all devices.
logging 192.168.10.250
Step 2: Log all messages with severity level 4 to the syslog server.
logging trap warnings
Task 6: Disabling Unused Cisco Network Services
Step 1: Disable unused interfaces on all devices.
R1:
interface FastEthernet0/0 no ip address shutdown ! interface Serial0/0/0 no ip address shutdown ! interface Serial0/1/0 no ip address shutdown ! interface Serial0/1/1 no ip address shutdown !
R2:
interface FastEthernet0/0 no ip address shutdown ! interface Serial0/0/0 no ip address shutdown ! interface Serial0/1/0 no ip address shutdown ! interface Serial0/1/1 no ip address shutdown !
R3:
interface FastEthernet0/0 no ip address shutdown ! interface Serial0/1/0 no ip address shutdown ! interface Serial0/1/1 no ip address shutdown !
Step 2: Disable unused global services on R1.
no service finger no service pad no service udp-small-servers no service tcp-small-servers no cdp run no ip bootp server no ip http server no ip finger no ip source-route no ip gratuitous-arps no cdp run
Step 3: Disable unused interface services on R1.
interface FastEthernet0/0 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast interface FastEthernet0/1 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast interface Serial0/0/0 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast interface Serial0/0/1 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast interface Serial0/1/0 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast interface Serial0/1/1 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast
Step 4: Use AutoSecure to secure R2.
Remember to use ciscoccna for all passwords in this lab.
R2#auto secure --- AutoSecure Configuration --- *** AutoSecure configuration enhances the security of the router, but it will not make it absolutely resistant to all security attacks *** AutoSecure will modify the configuration of your device. All configuration changes will be shown. For a detailed explanation of how the configuration changes enhance security and any possible side effects, please refer to Cisco.com for Autosecure documentation. At any prompt you may enter '?' for help. Use ctrl-c to abort this session at any prompt. Gathering information about the router for AutoSecure Is this router connected to internet? [no]: yes Enter the number of interfaces facing the internet [1]: 1 Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES manual up up FastEthernet0/1 192.168.30.1 YES unset down down Serial0/0/0 10.2.2.2 YES manual up up Serial0/0/1 10.2.2.2 YES manual up up Serial0/1/0 unassigned YES manual down down Serial0/1/1 unassigned YES unset down down Enter the interface name that is facing the internet: Serial0/1/0 Securing Management plane services... Disabling service finger Disabling service pad Disabling udp & tcp small servers Enabling service password encryption Enabling service tcp-keepalives-in Enabling service tcp-keepalives-out Disabling the cdp protocol Disabling the bootp server Disabling the http server Disabling the finger service Disabling source routing Disabling gratuitous arp Enter the new enable password: ciscoccna Confirm the enable password: ciscoccna Configuration of local user database Enter the username: ccna Enter the password: ciscoccna Confirm the password: ciscoccna Configuring AAA local authentication Configuring Console, Aux and VTY lines for local authentication, exec-timeout, and transport Securing device against Login Attacks Configure the following parameters Blocking Period when Login Attack detected: 300 Maximum Login failures with the device: 5 Maximum time period for crossing the failed login attempts: 120 Configuring interface specific AutoSecure services Disabling the following ip services on all interfaces: no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast no ip mask-reply Disabling mop on Ethernet interfaces Securing Forwarding plane services... Enabling CEF (This might impact the memory requirements for your platform) Enabling unicast rpf on all interfaces connected to internet This is the configuration generated: no service finger no service pad no service udp-small-servers no service tcp-small-servers service password-encryption service tcp-keepalives-in service tcp-keepalives-out no cdp run no ip bootp server no ip http server no ip finger no ip source-route no ip gratuitous-arps no ip identd security passwords min-length 6 security authentication failure rate 10 log enable password 7 070C285F4D061A061913 username ccna password 7 045802150C2E4F4D0718 aaa new-model aaa authentication login local_auth local line con 0 login authentication local_auth exec-timeout 5 0 transport output telnet line aux 0 login authentication local_auth exec-timeout 10 0 transport output telnet line vty 0 4 login authentication local_auth transport input telnet line tty 1 login authentication local_auth exec-timeout 15 0 line tty 192 login authentication local_auth exec-timeout 15 0 login block-for 300 attempts 5 within 120 service timestamps debug datetime msec localtime show-timezone service timestamps log datetime msec localtime show-timezone logging facility local2 logging trap debugging service sequence-numbers logging console critical logging buffered interface FastEthernet0/0 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast no ip mask-reply no mop enabled interface FastEthernet0/1 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast no ip mask-reply no mop enabled interface Serial0/0/0 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast no ip mask-reply interface Serial0/0/1 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast no ip mask-reply interface Serial0/1/0 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast no ip mask-reply interface Serial0/1/1 no ip redirects no ip proxy-arp no ip unreachables no ip directed-broadcast no ip mask-reply ip cef access-list 101 permit udp any any eq bootpc interface Serial0/0/0 ip verify unicast source reachable-via rx allow-default 101 ! end Apply this configuration to running-config? [yes]:yes
Task 7: Managing Cisco IOS and Configuration Files
Step 1: Identify where the running-config file is located in router memory.
R1#dir system: Directory of system:/ 3 dr-x 0 <no date> memory 1 -rw- 1232 <no date> running-config 2 dr-x 0 <no date> vfiles No space information available
Step 2: Transfer the running-config file from R1 to R2 using TFTP.
R1:
R1(config)#tftp-server system:running-config alias run
R2:
R2#copy tftp flash Address or name of remote host []? 10.2.2.1 Source filename []? run Destination filename [test]? run Accessing tftp://10.2.2.1/run... Loading test from 10.2.2.1 (via Serial0/0/0): ! [OK - 1192 bytes] 1192 bytes copied in 0.424 secs (2811 bytes/sec)
Step 3: Break R1 and recover it using ROMmon.
Copy and paste the following commands on R1, and then recover R1 using ROMmon.
line vty 0 4 exec-timeout 0 20 line console 0 exec-timeout 0 20 end copy run start exit rommon 1 > confreg 0x2142 rommon 2 > reset R1#copy running-config startup-config R1#configure terminal R1(config)#config-register 0x2102 R1(config)#end R2#reload
Step 4: Restore the saved configuration to R1 from R2 using TFTP.
Because R1 and R2 are not directly connected, you must set up RIP again on R1. However, R1 will not get the updates unless you set up RIP authentication.
R2:
R2(config)#tftp-server flash:run alias run
R1:
key chain RIP_KEY key 1 key-string cisco ! int s0/0/1 ip address 10.1.1.2 255.255.255.0 ip rip authentication mode md5 ip rip authentication key-chain RIP_KEY no shut ! router rip version 2 passive-interface default no passive-interface s0/0/1 network 10.0.0.0 no auto-summary R1#copy tftp nvram Address or name of remote host []? 10.2.2.1 Source filename []? run Destination filename []? nvram:startup-config Accessing tftp://10.1.1.2/run... Loading test from 10.1.1.2 (via Serial0/0/0): ! [OK - 1192 bytes] 1192 bytes copied in 0.452 secs (2637 bytes/sec)
Step 5: Erase the saved configuration from R2.
R2#delete flash:run
Task 8: Using SDM to Secure R2
Step 1: Connect to R2 using PC1.
Step 2: Navigate to the Security Audit feature.
Step 3: Perform a Security Audit.
Step 4: Choose settings to apply to the router.
Step 5: Commit the configuration to the router.
Task 9: Document the Router Configurations
On each router, issue the show run command and capture the configurations.
------------------------------------------
R1
------------------------------------------
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
no service finger
no service udp-small-server
no service tcp-small-server
!
hostname R1
!
boot-start-marker
boot-end-marker
!
security authentication failure rate 5 log
security passwords min-length 6
enable secret ciscoccna
!
aaa new-model
!
!
aaa authentication login local_auth local
!
aaa session-id common
!
resource policy
!
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
ip subnet-zero
no ip source-route
no ip gratuitous-arps
no ip finger
ip cef
!
!
no ip dhcp use vrf connected
!
!
no ip bootp server
!
!
key chain RIP_KEY
key 1
key-string cisco
username ccna password ciscoccna
!
!
!
interface FastEthernet0/0
no ip address
no ip redirects
no ip unreachables
no ip proxy-arp
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 192.168.10.1 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
duplex auto
speed auto
!
interface Serial0/0/0
no ip address
no ip redirects
no ip unreachables
no ip proxy-arp
shutdown
no fair-queue
clockrate 125000
!
interface Serial0/0/1
ip address 10.1.1.1 255.255.255.252
no ip redirects
no ip unreachables
no ip proxy-arp
ip rip authentication mode md5
ip rip authentication key-chain RIP_KEY
no fair-queue
clockrate 125000
!
!
router rip
version 2
passive-interface default
no passive-interface Serial0/0/1
network 10.0.0.0
network 192.168.10.0
no auto-summary
!
ip classless
!
no ip http server
!
login block-for 300 attempt 2 within 120
!
logging trap debugging
logging 192.168.10.150
no cdp run
!
control-plane
!
!
line con 0
exec-timeout 5 0
logging synchronous
transport output telnet
line aux 0
exec-timeout 15 0
logging synchronous
login authentication local_auth
transport output telnet
line vty 0 4
exec-timeout 15 0
logging synchronous
login authentication local_auth
transport input telnet
!
end
-------------------------------------------
R2
------------------------------------------
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
no service finger
no service udp-small-server
no service tcp-small-server
!
hostname R2
!
boot-start-marker
boot-end-marker
!
security authentication failure rate 10 log
security passwords min-length 6
enable secret ciscoccna
!
aaa new-model
!
!
aaa authentication login local_auth local
!
aaa session-id common
!
resource policy
!
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
ip subnet-zero
no ip source-route
no ip gratuitous-arps
no ip finger
ip cef
!
!
no ip dhcp use vrf connected
!
!
no ip bootp server
!
!
key chain RIP_KEY
key 1
key-string cisco
username ccna password ciscoccna
!
!
interface Loopback0
ip address 209.165.200.225 255.255.255.224
!
interface FastEthernet0/0
no ip address
no ip redirects
no ip unreachables
no ip proxy-arp
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
ip address 192.168.20.1 255.255.255.0
no ip address
no ip redirects
no ip unreachables
no ip proxy-arpshutdown
duplex auto
speed auto
no shutdown
!
interface Serial0/0/0
no ip address
no ip redirects
no ip unreachables
no ip proxy-arp
shutdown
no fair-queue
!
interface Serial0/0/1
ip address 10.2.2.1 255.255.255.252
no ip redirects
no ip unreachables
no ip proxy-arp
ip rip authentication mode md5
ip rip authentication key-chain RIP_KEY
clockrate 128000
no shutdown
!
interface Serial0/1/0
ip address 209.165.200.224 255.255.255.224
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Serial0/1/1
no ip address
no ip redirects
no ip unreachables
no ip proxy-arp
shutdown
clockrate 2000000
!
router rip
version 2
passive-interface default
no passive-interface Serial0/0/1
network 10.0.0.0
network 192.168.20.0
network 209.165.200.224
no auto-summary
!
ip classless
!
no ip http server
!
login block-for 300 attempt 2 within 120
!
logging trap debugging
logging 192.168.10.150
no cdp run
!
control-plane
!
!
line con 0
exec-timeout 5 0
logging synchronous
transport output telnet
line aux 0
exec-timeout 15 0
logging synchronous
login authentication local_auth
transport output telnet
line vty 0 4
exec-timeout 15 0
logging synchronous
login authentication local_auth
transport input telnet
!
end
!------------------------------------------
! R3
!-----------------------------------------
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
no service finger
no service udp-small-server
no service tcp-small-server
!
hostname R3
!
boot-start-marker
boot-end-marker
!
security authentication failure rate 5 log
security passwords min-length 6
enable secret ciscoccna
!
aaa new-model
!
!
aaa authentication login local_auth local
!
aaa session-id common
!
resource policy
!
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
ip subnet-zero
no ip source-route
no ip gratuitous-arps
no ip finger
ip cef
!
!
no ip dhcp use vrf connected
!
!
no ip bootp server
!
!
key chain RIP_KEY
key 1
key-string 7 01100F175804
username ccna password 7 094F471A1A0A1411050D
!
!
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface FastEthernet0/1
ip address 192.168.30.1 255.255.255.0
no shutdown
duplex auto
speed auto
!
interface Serial0/0/0
ip address 10.1.1.2 255.255.255.252
no ip redirects
no ip unreachables
no ip proxy-arp
clockrate 125000
ip rip authentication mode md5
ip rip authentication key-chain RIP_KEY
!
interface Serial0/0/1
ip address 10.2.2.2 255.255.255.252
no ip redirects
no ip unreachables
no ip proxy-arp
ip rip authentication mode md5
ip rip authentication key-chain RIP_KEY
!
router rip
version 2
passive-interface default
no passive-interface Serial0/0/0
no passive-interface Serial0/0/1
network 10.0.0.0
network 192.168.30.0
no auto-summary
!
ip classless
!
no ip http server
!
login block-for 300 attempt 2 within 120
!
logging trap debugging
logging 192.168.10.150
no cdp run
!
control-plane
!
!
line con 0
exec-timeout 5 0
logging synchronous
login authentication
transport output telnet
line aux 0
exec-timeout 15 0
logging synchronous
login authentication local_auth
transport output telnet
line vty 0 4
exec-timeout 15 0
logging synchronous
login authentication local_auth
transport input telnet
!
end
Task 10: Clean Up
Erase the configurations and reload the routers. Disconnect and store the cabling. For PC hosts that are normally connected to other networks (such as the school LAN or to the Internet), reconnect the appropriate cabling and restore the TCP/IP settings.
