5.1.3.9 Lab – UPnP Vulnerabilities (Instructor Version)
Lab Topology
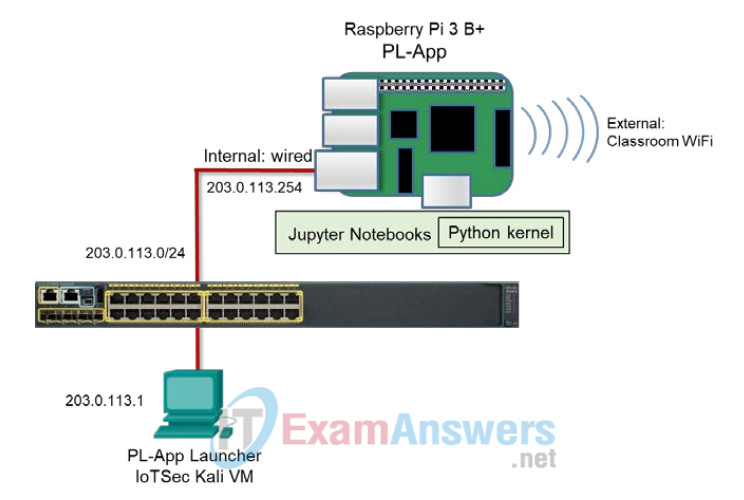
Addressing
The Pi will acquire an address from the external network, while providing addresses to the internal network.
Objectives
- Part 1: Configuring the Raspberry Pi as a wired router using a BASH script
- Part 2: Connecting a Client to the Raspberry Pi
- Part 3: Testing Ports using UPnP
Background / Scenario
Many home routers are Linux-based. To ease connectivity challenges, they offer services such as DHCP, NAT, UPnP, and more. They also offer both wired and wireless connections to the local network while protecting users from threats from the Internet. Unfortunately, these routers can be tricked to open various ports that will permit access to the internal network by threat actors from the Internet.
In this lab, you will turn a Raspberry Pi into a working router. Unlike most routers, the Raspberry Pi will connect to the network wirelessly using PL-App, and route wireless traffic into a local wired Ethernet network. A client will be added and connectivity will be tested. The client will then use Universal Plug and Play (UPnP) to open a communication port through the router without authentication.
Required Resources
- PC or laptop
- IoTSec Kali VM
- 8 GB Micro SD card (minimum required) with PL-App installed
- Raspberry Pi 3, Model B or later
- A wireless network connection
- Ethernet cables
- A switch
Predictable network interface names containing MAC addresses are becoming increasingly common. Because they may break the script used in this lab, raspi-config may be used to transition back to traditional interface names (eth0, eth1, wlan0, etc.). To learn more, read the following:
https://www.freedesktop.org/wiki/Software/systemd/PredictableNetworkInterfaceNames/
Part 1: Configuring the Raspberry Pi as a wired router using a BASH script
Step 1: Configure the PL-App image to connect to your WiFi network.
a. Connect the devices as shown in the topology diagram.
b. Start the DHCP services on the IoTSec Kali VM as necessary.
root@kali:~# lab_support_files/scripts/start_dhcp.sh [ ok ] Starting isc-dhcp-server (via systemctl): isc-dhcp-server.service.
c. Determine the IP address of the Raspberry Pi device.
d. Open a web browser in IoTSec Kali VM and navigate to the IP address of your Raspberry Pi device.
e. In the upper right-hand corner, click the Config icon (looks like a gear).
f. Enter the information for the SSID and password of your wireless network. Click OK to continue. Click Yes when prompted to continue making changes to config. The SSID and password may be provided by your instructor.
g. Open a terminal from the PL-App. Enter ifconfig to verify that the Raspberry Pi device is connected to the WiFi network.
(pl-app) root@myPi:/home/pi/notebooks# ifconfig
<output omitted>
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.11.201 netmask 255.255.255.0 broadcast 192.168.11.255
inet6 fe80::7859:df95:f2de:59f2 prefixlen 64 scopeid 0x20<link>
ether b8:27:eb:38:e8:65 txqueuelen 1000 (Ethernet)
RX packets 71 bytes 6193 (6.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 383 bytes 42370 (41.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Step 2: Run the BASH script
In this step, you will run a BASH script that prepares your Raspberry Pi to act as a router between the wired and wireless networks.
a. Navigate to the scripts directory.
(pl-app) root@myPi:/home/pi/notebooks# cd /home/pi/notebooks/Course\ Materials/4.\ IoT\ Security/scripts/
If desired, you can use the command PROMPT_DIRTRIM=1 to make the prompt shorter for the current terminal.
(pl-app) root@myPi:/home/pi/notebooks/Course Materials/4. IoT Security/scripts # PROMPT_DIRTRIM=1
b. Use ls -l to view the attributes of the script file. If it is not executable, use chmod +x to change the attributes of the file.
(pl-app) root@myPi:.../scripts# chmod +x WiFiPi.sh
c. Run the BASH script by invoking its name from the current folder.
(pl-app) root@myPi:.../scripts# ./WiFiPi.sh
d. Follow the directions and your instructor’s guidance to turn the Raspberry Pi into a wired or wireless router.
e. Wait for the Pi to reboot. You will lose network connectivity to your Raspberry Pi device.
Part 2: Connecting a Client to the Raspberry Pi
In this part of the lab, you will configure the Raspberry Pi to work as a router between the wired internal network and the wireless external network.
a. Open a web browser in IoTSec Kali VM and navigate to the Pi at 203.0.113.254. Log in to PL-App.
b. Open a new terminal on the Pi and issue the ifconfig command. You should see the following:
(pl-app) root@myPi:/home/pi/notebooks# ifconfig
eth0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 203.0.113.254 netmask 255.255.255.0 broadcast 0.0.0.0
ether b8:27:eb:61:08:42 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
<some output omitted>
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.11.201 netmask 255.255.255.0 broadcast 192.168.11.255
inet6 fe80::f377:c15:ba37:bb1 prefixlen 64 scopeid 0x20<link>
ether b8:27:eb:34:5d:17 txqueuelen 1000 (Ethernet)
RX packets 2040 bytes 397045 (387.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1815 bytes 1632892 (1.5 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Note: The address displayed above, 192.168.11.201/24, will vary depending on the configuration of your WiFi network.
Part 3: Testing Ports using UPnP
Step 1: Start the Linux Internet Gateway Device (IGD) service.
a. In the PL-App terminal that is open in the Kali VM browser, view the status of the Linux IGD service.
(pl-app) root@myPi:/home/pi/notebooks# systemctl status linux-igd
linux-igd.service - LSB: UPnP Internet Gateway Device
Loaded: loaded (/etc/init.d/linux-igd; disabled; vendor preset: enabled)
Active: inactive (dead)
Docs: man:systemd-sysv-generator(8)
b. If the Linux IDG service is not running, as shown in the output above, start the service.
(pl-app) root@myPi:/home/pi/notebooks# systemctl start linux-igd
c. If necessary, confirm the status of the Linux IDG service.
(pl-app) root@myPi:/home/pi/notebooks# systemctl status linux-igd
● linux-igd.service - LSB: UPnP Internet Gateway Device
Loaded: loaded (/etc/init.d/linux-igd; disabled; vendor preset: enabled)
Active: active (running) since Thu 2018-05-24 23:52:31 UTC; 7s ago
Docs: man:systemd-sysv-generator(8)
Process: 1059 ExecStart=/etc/init.d/linux-igd start (code=exited,
status=0/SUCCESS)
CGroup: /system.slice/linux-igd.service
└─1067 /usr/sbin/upnpd wlan0 eth0
May 24 23:52:31 pi systemd[1]: Starting LSB: UPnP Internet Gateway Device...
May 24 23:52:31 pi linux-igd[1059]: Starting Linux IGD Daemon: linux-igd.
May 24 23:52:31 pi systemd[1]: Started LSB: UPnP Internet Gateway Device.
May 24 23:52:31 pi upnpd[1067]: 0x76fd54b0 UPnP SDK Successfully Initialized.
May 24 23:52:31 pi upnpd[1067]: 0x76fd54b0 Successfully set the Web Server
Root Directory.
May 24 23:52:31 pi upnpd[1067]: 0x76fd54b0 IGD root device successfully
registered.
May 24 23:52:31 pi upnpd[1067]: 0x76fd54b0 Advertisements Sent. Listening for
requests ...
Step 2: Verify open ports and create a new mapping using Linux.
A router should isolate the Internet from the LAN behind it. Ideally devices on the Internet would not be able to open connections to devices in the LAN behind the router. UPnP allows an internal device to ask the router to open a port in its firewall, allowing devices out on the Internet to reach the internal device. While there are a few special cases where this is desirable, more often than not, allowing internal devices to use UPnP to open ports is bad practice.
In this step, we will use the iptables Linux kernel firewall utility to observe the behavior of UPnP on the Pi.
a. Use the following commands on the Raspberry Pi to determine the open ports and view the routing tables. Document the number of open ports.
(pl-app) root@myPi:/home/pi/notebooks# iptables -S -P INPUT ACCEPT -P FORWARD ACCEPT -P OUTPUT ACCEPT <some output omitted> -A FORWARD -i wlan0 -o eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT -A FORWARD -i eth0 -o wlan0 -j ACCEPT
b. Use the netstat -tuna command to list the services (and theirs ports) running on the Pi.
(pl-app) root@myPi:/home/pi/notebooks# netstat -tuna
Is there a service running on port 49152? What service often listens to that port? Perform a Google search and record your answer below.
_____________________________________________________________
Yes, a service is running on port 49152. Research on the Internet shows that Linux IGD uses port 49152 to run UPnP. In addition, research shows that the only standard port for UPnP is UPD port 1900. It is also open on the Pi.
c. Before upnpc in the Kali VM can communicate with the Raspberry Pi, you must create a default route pointing to the Pi. In the Kali VM, enter the following command:
root@kali:~# ip route add default via 203.0.113.254
Instructor Note: This default route should NOT be necessary as the Pi and Kali belong to the same network. However, because of an upnpc implementation decision, communication cannot be established without a default route.
d. In a terminal on IoTSec Kali VM, you will use upnpc to simulate an internal UPnP-ready device.
Upnpc is an UPnP client. Use the upnpc command to create a port mapping on the Raspberry Pi router. In this case, the client’s IP is 203.0.113.1 (Kali’s IP). The command requests that the router expose the client’s SSH port (port 22) to the Internet as port 1337, much as an IoT device would.
root@kali:~# upnpc -a 203.0.113.1 22 1337 tcp upnpc : miniupnpc library test client, version 2.0. (c) 2005-2017 Thomas Bernard. Go to http://miniupnp.free.fr/ or https://miniupnp.tuxfamily.org/ for more information. List of UPNP devices found on the network : desc: http://203.0.113.254:49152/gatedesc.xml st: urn:schemas-upnp-org:device:InternetGatewayDevice:1 Found a (not connected?) IGD : http://203.0.113.254:49152/upnp/control/WANIPConn1 Trying to continue anyway Local LAN ip address : 203.0.113.1 ExternalIPAddress = 192.168.11.201 InternalIP:Port = 203.0.113.1:22 external 192.168.11.201:1337 TCP is redirected to internal 203.0.113.1:22 (duration=0)
e. Return to the terminal that is open on the Raspberry Pi in PL-App. Note the change in the IP tables and ports of the Raspberry Pi router by repeating the commands from step a.
(pl-app) root@myPi:/home/pi/notebooks# iptables -S -P INPUT ACCEPT -P FORWARD ACCEPT -P OUTPUT ACCEPT <some output omitted> -A FORWARD -d 203.0.113.1/32 -p tcp -m tcp --dport 22 -j ACCEPT -A FORWARD -i wlan0 -o eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT -A FORWARD -i eth0 -o wlan0 -j ACCEPT
The UPnP service on the Kali VM has opened a port in the firewall of the Raspberry Pi gateway device. The new port mapping will now allow an attacker to communicate with a listening IoT device inside of a network. An IoT device could do much the same by using UPnP to open a port so that an Internet application could communicate with the device. A user may not be aware that the router firewall has been reconfigured in this way.
f. You can also use Miranda, a Kali tool, to discover, query, and interact with UPnP-enabled devices.
For more information about Miranda, navigate to https://tools.kali.org/information-gathering/miranda.
g. In a terminal on IoTSec Kali VM, enter miranda.
root@kali:~# miranda
h. At the upnp> prompt, enter msearch to discover UPnP-enabled devices on the network. Press Ctl+C to stop the search.
What is the IP address of UPnP device? What version UPnP is used by the UPnP-enabled device?
_____________________________________________________________The IP address of the UPnP device is 203.0.113.254 as configured in the WiFiPi script. At this time, it is using UPnP version 1.0.
i. To find out more information about the UPnP device, enter host list at the prompt.
upnp> host list
[0] 203.0.113.254:49152
j. Using the ID provided by the list in [ ], enter host get 0 to request more information in this example. Then enter host summary 0 to display the results.
upnp> host get 0 Requesting device and service info for 203.0.113.254:49152 (this could take a few seconds)... Failed to retrieve actions from service actions list for service urn:schemasdummy-com:service:Dummy:1! Host data enumeration complete! upnp> host summary 0 Host: 203.0.113.254:49152 XML File: http://203.0.113.254:49152/gatedesc.xml <output omitted>
k. Type exit to leave miranda.
Step 3: Restore to the default configurations.
a. Remove the additional default route from IoTSec Kali VM.
root@kali:~# ip route del default via 203.0.113.254
b. In the PL-App terminal, navigate to the scripts directory if necessary.
(pl-app) root@myPi:/home/pi/notebooks# cd Course\ Materials/4.\ IoT\ Security/scripts/
c. Use chmod +x to add execute attribute to the cleanup file.
(pl-app) root@myPi:.../scripts# chmod +x Cleanup_WiFiPi.sh
d. Run the BASH script by invoking its name from the current folder.
(pl-app) root@myPi:.../scripts# ./CleanUp_WiFiPi.sh
e. The Raspberry Pi device will receive an IP address from the DHCP server that is running on IoTSec Kali VM. Determine the assigned IP address.
Using a web browser on IoTSec Kali VM. Navigate to the Raspberry Pi. Verify that the dnsmasq, linux-igd and WiFiPi services are stopped.
(pl-app) root@myPi:/home/pi/notebooks# systemctl status dnsmasq (pl-app) root@myPi:/home/pi/notebooks# systemctl status linux-igd (pl-app) root@myPi:/home/pi/notebooks# systemctl status WiFiPi
Note: Make sure students disable the services after they finish the lab. Dnsmasq and linux-igd could create problems in other labs if left running.
Note: If students were unable to access the Raspberry Pi after reboot, the microSD card may need to be reimaged. The Raspberry Pi can still be accessed directly via HDMI; however, network access will need to be configured and the original /etc/dnsmasq.conf, /etc/network/interfaces and /etc/dhcpcd.config can be copied from another Raspberry Pi device and replace the affected files.
Reflection
1. What is UPnP commonly used for in home networks?
____________________________________________________________
UPnP simplifies the setup of many home network devices such as printers, media servers, IoT devices and digital assistants.
2. Consider your home network connection. Is UPnP running? What can be done to turn this service off?
____________________________________________________________Answers will vary because students’ home networks differ.
3. How can an attacker using a vulnerable IoT device take advantage of a UPnP-enabled router?
____________________________________________________________Answers will vary. The key here is that attackers can use compromised IoT devices as UPnP clients and expose internal devices to the Internet.
