Time limit: 0
Quiz-summary
0 of 99 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
Information
Good Luck For You!
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 99 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- Answered
- Review
-
Question 1 of 99
1. Question
1 pointsWhich security implementation will provide control plane protection for a network device?Correct
Incorrect
-
Question 2 of 99
2. Question
1 pointsWhat is the one major difference between local AAA authentication and using the login local command when configuring device access authentication?Correct
Incorrect
-
Question 3 of 99
3. Question
1 pointsRefer to the exhibit.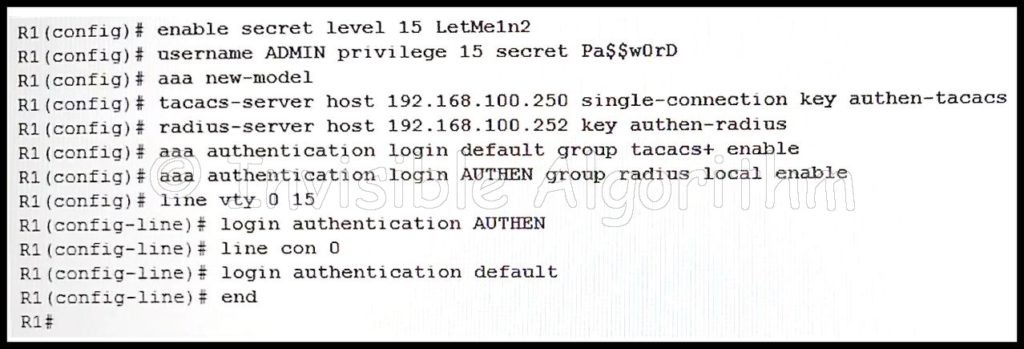 A network administrator configures AAA authentication on R1. The administrator then tests the configuration by telneting to R1. The ACS servers are configured and running. What will happen if the authentication fails? Correct
A network administrator configures AAA authentication on R1. The administrator then tests the configuration by telneting to R1. The ACS servers are configured and running. What will happen if the authentication fails? Correct
Incorrect
-
Question 4 of 99
4. Question
1 pointsWhat are two tasks that can be accomplished with the Nmap and Zenmap network tools? (Choose two.)Correct
Incorrect
-
Question 5 of 99
5. Question
1 pointsWhich Cisco IOS subcommand is used to compile an IPS signature into memory?Correct
Incorrect
-
Question 6 of 99
6. Question
1 pointsWhy are DES keys considered weak keys?Correct
Incorrect
-
Question 7 of 99
7. Question
1 pointsWhat is a benefit of using a next-generation firewall rather than a stateful firewall?Correct
Incorrect
-
Question 8 of 99
8. Question
1 pointsWhat is a result of securing the Cisco IOS image using the Cisco IOS Resilient Configuration feature?Correct
Incorrect
-
Question 9 of 99
9. Question
1 pointsThe corporate security policy dictates that the traffic from the remote-access VPN clients must be separated between trusted traffic that is destined for the corporate subnets and untrusted traffic destined for the public Internet. Which VPN solution should be implemented to ensure compliance with the corporate policy?Correct
Incorrect
-
Question 10 of 99
10. Question
1 pointsWhich two conditions must be met in order for a network administrator to be able to remotely manage multiple ASAs with Cisco ASDM? (Choose two.)Correct
Incorrect
-
Question 11 of 99
11. Question
1 pointsWhat is negotiated in the establishment of an IPsec tunnel between two IPsec hosts during IKE Phase 1?Correct
Incorrect
-
Question 12 of 99
12. Question
1 pointsWhat are two benefits of using a ZPF rather than a Classic Firewall? (Choose two.)Correct
Incorrect
-
Question 13 of 99
13. Question
1 pointsWhich security policy characteristic defines the purpose of standards?Correct
Incorrect
-
Question 14 of 99
14. Question
1 pointsWhat algorithm is used to provide data integrity of a message through the use of a calculated hash value?Correct
Incorrect
-
Question 15 of 99
15. Question
1 pointsOn which port should Dynamic ARP Inspection (DAI) be configured on a switch?Correct
Incorrect
-
Question 16 of 99
16. Question
1 pointsWhat is a feature of a Cisco IOS Zone-Based Policy Firewall?Correct
Incorrect
-
Question 17 of 99
17. Question
1 pointsRefer to the exhibit. The administrator can ping the S0/0/1 interface of RouterB but is unable to gain Telnet access to the router by using the password cisco123. What is a possible cause of the problem?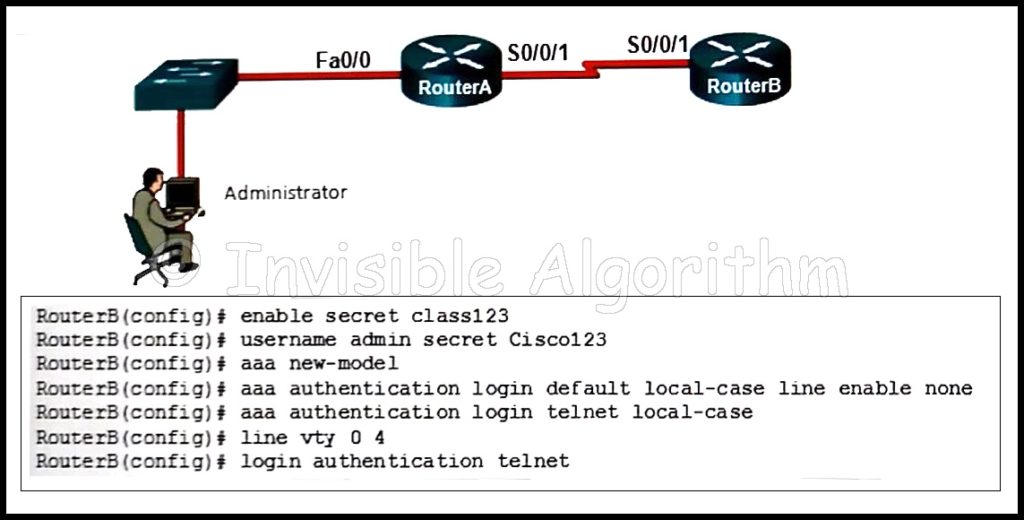 Correct
Correct
Incorrect
-
Question 18 of 99
18. Question
1 pointsRefer to the exhibit. The ip verify source command is applied on untrusted interfaces. Which type of attack is mitigated by using this configuration? Correct
Correct
Incorrect
-
Question 19 of 99
19. Question
1 pointsRefer to the exhibit.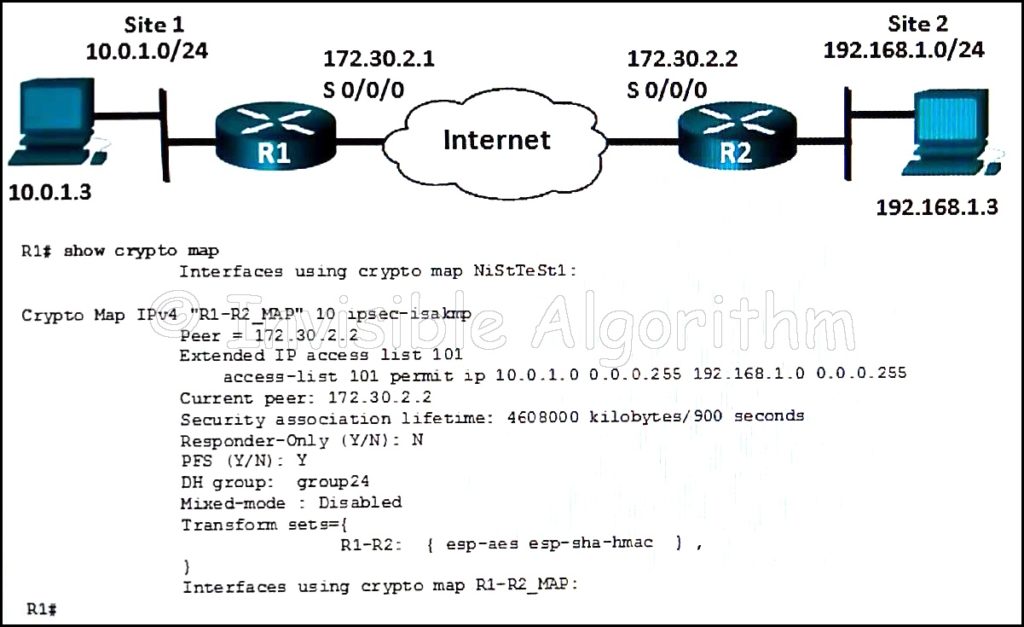 Which conclusion can be made from the show crypto map command output that is shown on R1? Correct
Which conclusion can be made from the show crypto map command output that is shown on R1? Correct
Incorrect
-
Question 20 of 99
20. Question
1 pointsWhat type of algorithms require sender and receiver to exchange a secret key that is used to ensure the confidentiality of messages?Correct
Incorrect
-
Question 21 of 99
21. Question
1 pointsWhat is an advantage in using a packet filtering firewall versus a high-end firewall appliance?Correct
Incorrect
-
Question 22 of 99
22. Question
1 pointsRefer to the exhibit.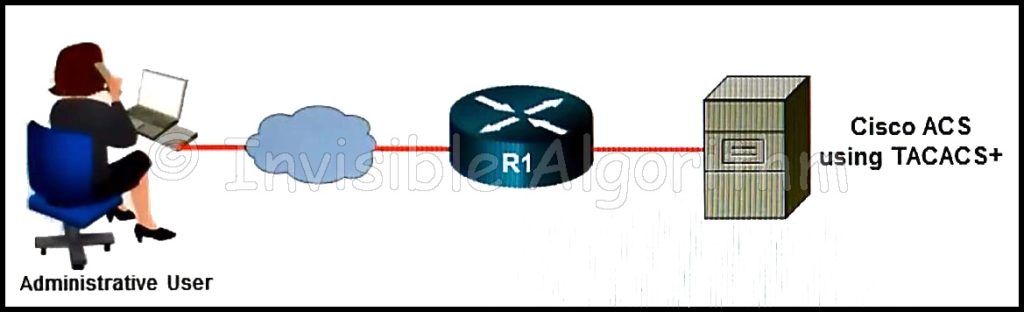 In the network that is shown, which AAA command logs the use of EXEC session commands? Correct
In the network that is shown, which AAA command logs the use of EXEC session commands? Correct
Incorrect
-
Question 23 of 99
23. Question
1 pointsA network administrator enters the single-connection command. What effect does this command have on AAA operation?Correct
Incorrect
-
Question 24 of 99
24. Question
1 pointsWhich two practices are associated with securing the features and performance of router operating systems? (Choose two.)Correct
Incorrect
-
Question 25 of 99
25. Question
1 pointsWhich statement describes a characteristic of the IKE protocol?Correct
Incorrect
-
Question 26 of 99
26. Question
1 pointsRefer to the exhibit.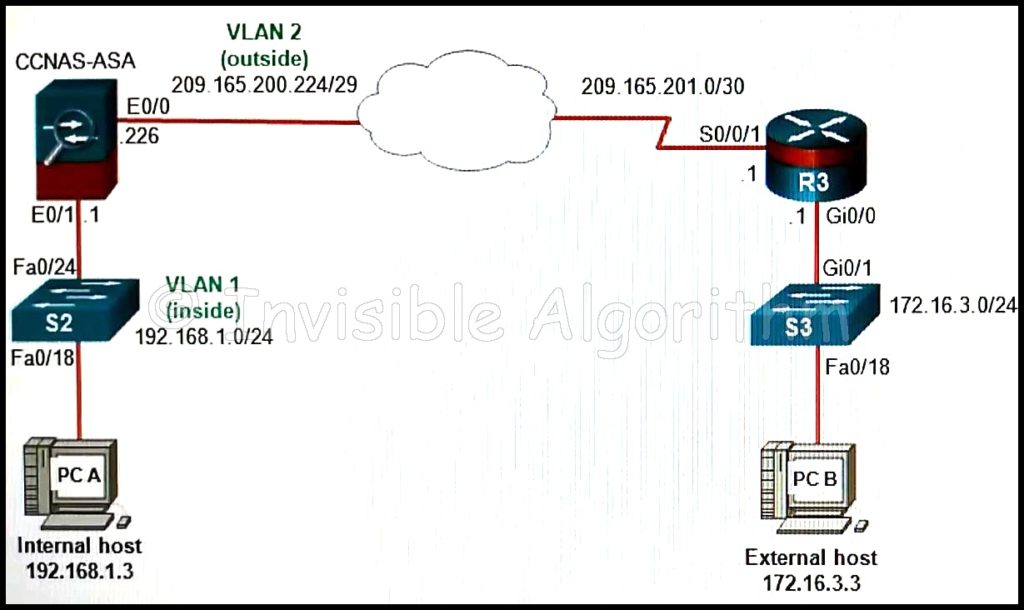 If a network administrator is using ASDM to configure a site-to-site VPN between the CCNAS-ASA and R3, which IP address would the administrator use for the peer IP address textbox on the ASA if data traffic is to be encrypted between the two remote LANs?
Correct
If a network administrator is using ASDM to configure a site-to-site VPN between the CCNAS-ASA and R3, which IP address would the administrator use for the peer IP address textbox on the ASA if data traffic is to be encrypted between the two remote LANs?
Correct
Incorrect
-
Question 27 of 99
27. Question
1 pointsRefer to the exhibit.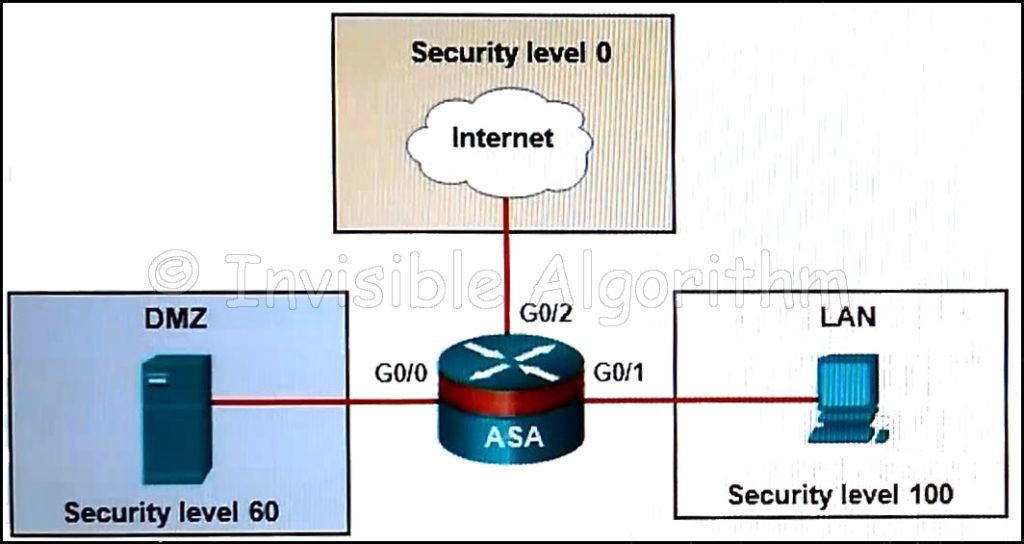 Based on the security levels of the interfaces on the ASA, what statement correctly describes the flow of traffic allowed on the interfaces?
Correct
Based on the security levels of the interfaces on the ASA, what statement correctly describes the flow of traffic allowed on the interfaces?
Correct
Incorrect
-
Question 28 of 99
28. Question
1 pointsWhat two assurances does digital signing provide about code that is downloaded from the Internet? (Choose two.)Correct
Incorrect
-
Question 29 of 99
29. Question
1 pointsWhich interface option could be set through ASDM for a Cisco ASA?Correct
Incorrect
-
Question 30 of 99
30. Question
1 pointsWhat are two characteristics of a stateful firewall? (Choose two.)Correct
Incorrect
-
Question 31 of 99
31. Question
1 pointsWhat are three characteristics of SIEM? (Choose three.)Correct
Incorrect
-
Question 32 of 99
32. Question
1 pointsWhich type of traffic is subject to filtering on an ASA 5505 device?Correct
Incorrect
-
Question 33 of 99
33. Question
1 pointsWhich IDS/IPS signature alarm will look for packets that are destined to or from a particular port?Correct
Incorrect
-
Question 34 of 99
34. Question
1 pointsWhich three actions can the Cisco IOS Firewall IPS feature be configured to take when an intrusion activity is detected? (Choose three.)Correct
Incorrect
-
Question 35 of 99
35. Question
1 pointsWhich two protocols can be selected using the Cisco AnyConnect VPN Wizard to protect the traffic inside a VPN tunnel? (Choose two.)Correct
Incorrect
-
Question 36 of 99
36. Question
1 pointsWhat is a characteristic of a role-based CLI view of router configuration?Correct
Incorrect
-
Question 37 of 99
37. Question
1 pointsMatch the network security testing technique with how it is used to test network security. (Not all options are used)?Correct
Incorrect
-
Question 38 of 99
38. Question
1 pointsWhich statement describes the use of certificate classes in the PKI?Correct
Incorrect
-
Question 39 of 99
39. Question
1 pointsRefer to the exhibit. An administrator issues these IOS login enhancement commands to increase the security for login connections. What can be concluded about them? Correct
Correct
Incorrect
-
Question 40 of 99
40. Question
1 pointsA company deploys a Cisco ASA with the Cisco CWS connector enabled as the firewall on the border of corporate network. An employee on the internal network is accessing a public website. What should the employee do in order to make sure the web traffic is protected by the Cisco CWS?Correct
Incorrect
-
Question 41 of 99
41. Question
1 pointsRefer to the exhibit. A network administrator configures AAA authentication on router R1. The ACS servers are configured and running. The administrator tests the configuration by telneting to R1. What will happen if the administrator attempts to authenticate through the RADIUS server using incorrect credentials?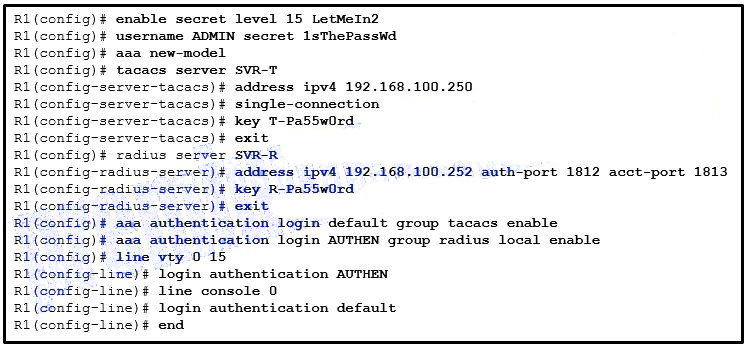 Correct
Correct
Incorrect
-
Question 42 of 99
42. Question
1 pointsWhat mechanism is used by an ASA 5505 device to allow inspected outbound traffic to return to the originating sender who is on an inside network?Correct
Incorrect
-
Question 43 of 99
43. Question
1 pointsWhich two end points can be on the other side of an ASA site-to-site VPN configured using ASDM? (Choose two.)Correct
Incorrect
-
Question 44 of 99
44. Question
1 pointsWhat Layer 2 attack is mitigated by disabling Dynamic Trunking Protocol?Correct
Incorrect
-
Question 45 of 99
45. Question
1 pointsIn an AAA-enabled network, a user issues the configure terminal command from the privileged executive mode of operation. What AAA function is at work if this command is rejected?Correct
Incorrect
-
Question 46 of 99
46. Question
1 pointsAn organization has configured an IPS solution to use atomic alerts. What type of response will occur when a signature is detected?Correct
Incorrect
-
Question 47 of 99
47. Question
1 pointsWhat two algorithms can be part of an IPsec policy to provide encryption and hashing to protect interesting traffic? (Choose two.)Correct
Incorrect
-
Question 48 of 99
48. Question
1 pointsFill in the blank.?- A stateful signature is also known as a (Composite?) signature.
Correct
Incorrect
-
Question 49 of 99
49. Question
1 pointsWhy is hashing cryptographically stronger compared to a cyclical redundancy check (CRC)?Correct
Incorrect
-
Question 50 of 99
50. Question
1 pointsA network analyst wants to monitor the activity of all new interns. Which type of security testing would track when the interns sign on and sign off the network?Correct
Incorrect
-
Question 51 of 99
51. Question
1 pointsRefer to the exhibit. What two pieces of information can be gathered from the generated message? (Choose two.) Correct
Correct
Incorrect
-
Question 52 of 99
52. Question
1 pointsWhat is required for auto detection and negotiation of NAT when establishing a VPN link?Correct
Incorrect
-
Question 53 of 99
53. Question
1 pointsRefer to the exhibit. The network administrator is configuring the port security feature on switch SWC. The administrator issued the command show port-security interface fa 0/2 to verify the configuration. What can be concluded from the output that is shown? (Choose three.)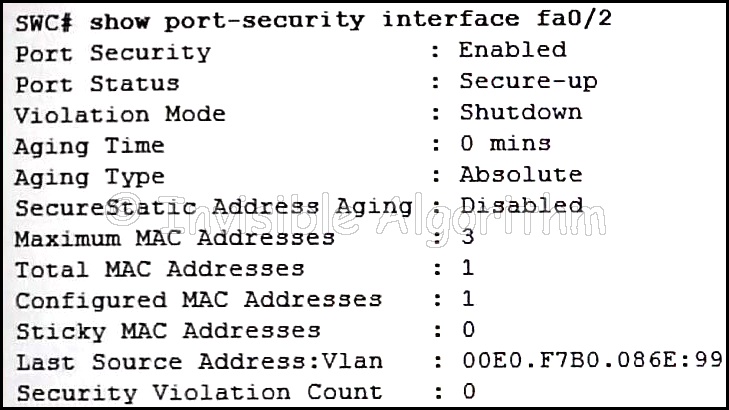 Correct
Correct
Incorrect
-
Question 54 of 99
54. Question
1 pointsIn which two instances will traffic be denied as it crosses the ASA 5505 device? (Choose two.)Correct
Incorrect
-
Question 55 of 99
55. Question
1 pointsRefer to the exhibit. Based on the configuration that is shown, which statement is true about the IPS signature category?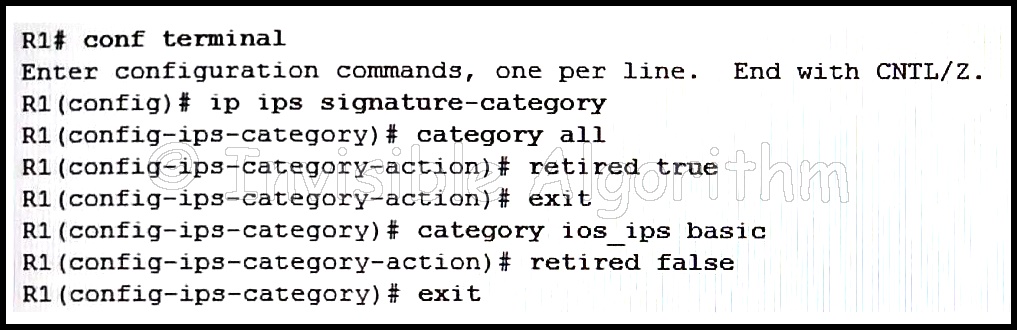 Correct
Correct
Incorrect
-
Question 56 of 99
56. Question
1 pointsWhich two ports can send and receive Layer 2 traffic from a community port on a PVLAN? (Choose two.)Correct
Incorrect
-
Question 57 of 99
57. Question
1 pointsWhat is a feature of the TACACS+ protocol?Correct
Incorrect
-
Question 58 of 99
58. Question
1 pointsWhich security measure is best used to limit the success of a reconnaissance attack from within a campus area network?Correct
Incorrect
-
Question 59 of 99
59. Question
1 pointsWhat is the benefit of the network-based IPS (NIPS) over host-based IPS (HIPS) deployment models?Correct
Incorrect
-
Question 60 of 99
60. Question
1 pointsWhat represents a best practice concerning discovery protocols such as CDP and LLDP on network devices?Correct
Incorrect
-
Question 61 of 99
61. Question
1 pointsWhat function is provided by the Tripwire network security tool?Correct
Incorrect
-
Question 62 of 99
62. Question
1 pointsWhat is the function of a policy map configuration when an ASA firewall is being configured?Correct
Incorrect
-
Question 63 of 99
63. Question
1 pointsIf a network administrator wants to track the usage of FTP services, which keyword or keywords should be added to the aaa accounting command?Correct
Incorrect
-
Question 64 of 99
64. Question
1 pointsWhat is indicated by the use of the local-case keyword in a local AAA authentication configuration command sequence?Correct
Incorrect
-
Question 65 of 99
65. Question
1 pointsWhat is the purpose of a local username database if multiple ACS servers are configured to provide authentication services?Correct
Incorrect
-
Question 66 of 99
66. Question
1 pointsRefer to the exhibit. Based on the security levels of the interfaces on ASA1, what traffic will be allowed on the interfaces?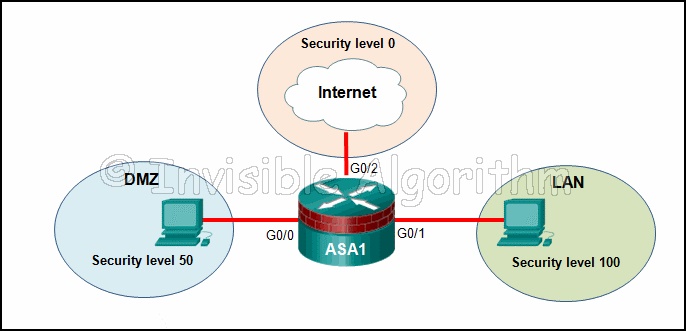 Correct
Correct
Incorrect
-
Question 67 of 99
67. Question
1 pointsWhat are two reasons to enable OSPF routing protocol authentication on a network? (Choose two.)Correct
Incorrect
-
Question 68 of 99
68. Question
1 pointsA security awareness session is best suited for which topic?Correct
Incorrect
-
Question 69 of 99
69. Question
1 pointsWhat provides both secure segmentation and threat defense in a Secure Data Center solution?Correct
Incorrect
-
Question 70 of 99
70. Question
1 pointsWhich two features should be configured on end-user ports in order to prevent STP manipulation attacks( Choose two.)?Correct
Incorrect
-
Question 71 of 99
71. Question
1 pointsWhat is a characteristic of most modern viruses?Correct
Incorrect
-
Question 72 of 99
72. Question
1 pointsWhich statement describes a characteristic of the Security Device Event Exchange (SDEE) feature supported by the Cisco IOS IPS?Correct
Incorrect
-
Question 73 of 99
73. Question
1 pointsWhich network security tool allows an administrator to test and detect weak passwords?Correct
Incorrect
-
Question 74 of 99
74. Question
1 pointsWhat is an advantage of logging packets that are seen by an IPS device?Correct
Incorrect
-
Question 75 of 99
75. Question
1 pointsWhich procedure is recommended to mitigate the chances of ARP spoofing?Correct
Incorrect
-
Question 76 of 99
76. Question
1 pointsIn a server-based AAA implementation, which protocol will allow the router to successfully communicate with the AAA server?Correct
Incorrect
-
Question 77 of 99
77. Question
1 pointsA network technician is attempting to resolve problems with the NAT configuration on anASA. The technician generates a ping from an inside host to an outside host. Whichcommand verifies that addresses are being translated on the ASA?Correct
Incorrect
-
Question 78 of 99
78. Question
1 pointsWhat are three components of a technical security policy? (Choose three.)Correct
Incorrect
-
Question 79 of 99
79. Question
1 pointsWhich security policy outlines the overall security goals for managers and technical personnel within an organization and includes the consequences of noncompliance with the policy?Correct
Incorrect
-
Question 80 of 99
80. Question
1 pointsWhat is a secure configuration option for remote access to a network device?Correct
Incorrect
-
Question 81 of 99
81. Question
1 pointsOn what switch ports should BPDU guard be enabled to enhance STP stability?Correct
Incorrect
-
Question 82 of 99
82. Question
1 pointsWhich feature is specific to the Security Plus upgrade license of an ASA 5505 and provides increased availability?Correct
Incorrect
-
Question 83 of 99
83. Question
1 pointsA company deploys a hub-and-spoke VPN topology where the security appliance is the hub and the remote VPN networks are the spokes. Which VPN method should be used in order for one spoke to communicate with another spoke through the single public interface of the security appliance?Correct
Incorrect
-
Question 84 of 99
84. Question
1 pointsWhat are two drawbacks in assigning user privilege levels on a Cisco router? (Choose two.)Correct
Incorrect
-
Question 85 of 99
85. Question
1 pointsWhich two types of hackers are typically classified as grey hat hackers? (Choose two.)Correct
Incorrect
-
Question 86 of 99
86. Question
1 pointsWhat is the default preconfigured interface for the outside network on a Cisco ASA 5505?Correct
Incorrect
-
Question 87 of 99
87. Question
1 pointsA user successfully logs in to a corporate network via a VPN connection. Which part of the AAA process records that a certain user performed a specific operation at a particular date and time?Correct
Incorrect
-
Question 88 of 99
88. Question
1 pointsWhat determines which switch becomes the STP root bridge for a given VLAN?Correct
Incorrect
-
Question 89 of 99
89. Question
1 pointsWhat is a function of the GRE protocol?Correct
Incorrect
-
Question 90 of 99
90. Question
1 pointsWhat is used to determine the root bridge when the priority of the switches are the same?Correct
Incorrect
-
Question 91 of 99
91. Question
1 pointsWhat is algorithm-type to protect the data in transit?Correct
Incorrect
-
Question 92 of 99
92. Question
1 pointsWhat type of ACL is designed for use in the configuration of an ASA to support filtering for clientless SSL VPN’s?Correct
Incorrect
-
Question 93 of 99
93. Question
1 pointsThe following authentication configuration is applied to a router. aaa authentication login default tacacs+ local enable none Several days later the TACACS+ server goes off-line. Which method will be used to authenticate users?Correct
Incorrect
-
Question 94 of 99
94. Question
1 pointsA security technician is evaluating a new operations security proposal designed to limit access to all servers. What is an advantage of using network security testing to evaluate the new proposal?Correct
Incorrect
-
Question 95 of 99
95. Question
1 pointsWhich security implementation will provide management plane protection for a network device?Correct
Incorrect
-
Question 96 of 99
96. Question
1 pointsWhat two new features are offered by Cisco ASA 5500-X with FirePOWER service when compared with the original ASA 5500 series? (Choose two.)Correct
Incorrect
-
Question 97 of 99
97. Question
1 pointsWhich two statements describe the 8 Ethernet ports in the backplane of a Cisco ASA 5506-X device? (Choose two.)Correct
Incorrect
-
Question 98 of 99
98. Question
1 pointsAn administrator assigned a level of router access to the user ADMIN using the commands below.Router(config)# privilege exec level 14 show ip route Router(config)# enable algorithm-type scrypt secret level 14 cisco-level-10 Router(config)# username ADMIN privilege 14 algorithm-type scrypt secret cisco-level-10
Which two actions are permitted to the user ADMIN? (Choose two.)Correct
Incorrect
-
Question 99 of 99
99. Question
1 pointsRefer to the exhibit. The administrator wants to enable port security on an interface on switch S1, but the command was rejected. Which conclusion can be drawn?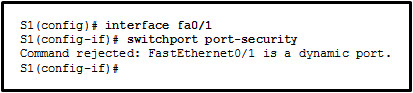 Correct
Correct
Incorrect

Are these question all in the final exam
No they are only training questions
Hey, the start quiz button not working
Fixed, please reload page
What is the benefit of the network-based IPS (NIPS) over host-based IPS (HIPS) deployment models? >> correct answer: NIPS monitors network segments ?
“The network administrator is configuring the port security feature on switch SWC. The administrator issued the command show port-security interface fa 0/2 to verify the configuration. What can be concluded from the output that is shown? ” >>> isn’t one of the three answers: “The switch port mode for this interface is access mode “?