Time limit: 0
Quiz-summary
0 of 57 questions completed
Questions:
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
Information
CCNA Security v2.0 Certification Practice Test Online
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading...
You must sign in or sign up to start the quiz.
You have to finish following quiz, to start this quiz:
Results
0 of 57 questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 points, (0)
| Average score |
|
| Your score |
|
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- Answered
- Review
-
Question 1 of 57
1. Question
1 pointsDuring the AAA process, when will authorization be implemented?Correct
Incorrect
-
Question 2 of 57
2. Question
1 pointsWhat is the primary function of the Diffie-Hellman algorithm?Correct
Incorrect
-
Question 3 of 57
3. Question
1 pointsWhen configuring SSH on a router to implement secure network management, a network engineer has issued the login local and transport input ssh line vty commands. What three additional configuration actions have to be performed to complete the SSH configuration? (Choose three.)Correct
Incorrect
-
Question 4 of 57
4. Question
1 pointsWhich functionality does the TACACS single-connection keyword provide to AAA services?Correct
Incorrect
-
Question 5 of 57
5. Question
1 pointsIn what situation would a network administrator most likely implement root guard?Correct
Incorrect
-
Question 6 of 57
6. Question
1 pointsWhat type of algorithms require sender and receiver to exchange a secret key that is used to ensure the confidentiality of messages?Correct
Incorrect
-
Question 7 of 57
7. Question
1 pointsA network administrator is configuring an AAA server to manage TACACS+ authentication. What are two attributes of TACACS+ authentication? (Choose two.)Correct
Incorrect
-
Question 8 of 57
8. Question
1 pointsWhat is a characteristic of a role-based CLI view of router configuration?Correct
Incorrect
-
Question 9 of 57
9. Question
1 pointsWhat service or protocol does the Secure Copy Protocol rely on to ensure that secure copy transfers are from authorized users?Correct
Incorrect
-
Question 10 of 57
10. Question
1 pointsWhich three functions are provided under Cisco NAC framework solution? (Choose three.)Correct
Incorrect
-
Question 11 of 57
11. Question
1 pointsA network administrator is configuring an AAA server to manage RADIUS authentication. Which two features are included in RADIUS authentication? (Choose two.)Correct
Incorrect
-
Question 12 of 57
12. Question
1 pointsWhat is the next step in the establishment of an IPsec VPN after IKE Phase 1 is complete?Correct
Incorrect
-
Question 13 of 57
13. Question
1 pointsA security technician uses an asymmetric algorithm to encrypt messages with a private key and then forwards that data to another technician. What key must be used to decrypt this data?Correct
Incorrect
-
Question 14 of 57
14. Question
1 pointsWhich IPS signature trigger type is based on a defined profile of normal network activity?Correct
Incorrect
-
Question 15 of 57
15. Question
1 pointsWhich condition describes a true positive IPS signature alarm?Correct
Incorrect
-
Question 16 of 57
16. Question
1 pointsIn the implementation of secure network management, what are two services or functions of the management plane of a Cisco router that should be configured? (Choose two.)Correct
Incorrect
-
Question 17 of 57
17. Question
1 pointsWhich two characteristics describe a virus? (Choose two.)Correct
Incorrect
-
Question 18 of 57
18. Question
1 pointsWhich network attack is mitigated by enabling BPDU guard?Correct
Incorrect
-
Question 19 of 57
19. Question
1 pointsWhen is a security association (SA) created if an IPsec VPN tunnel is used to connect between two sites?Correct
Incorrect
-
Question 20 of 57
20. Question
1 pointsHow is asymmetric encryption used to provide confidentiality for VPN traffic?Correct
Incorrect
-
Question 21 of 57
21. Question
1 pointsWhich AAA component can be established using token cards?Correct
Incorrect
-
Question 22 of 57
22. Question
1 pointsIn the implementation of network security, how does the deployment of a Cisco ASA firewall differ from a Cisco IOS router?Correct
Incorrect
-
Question 23 of 57
23. Question
1 pointsWhat function is performed by the class maps configuration object in the Cisco modular policy framework?Correct
Incorrect
-
Question 24 of 57
24. Question
1 pointsIn the implementation of security on multiple devices, how do ASA ACLs differ from Cisco IOS ACLs?Correct
Incorrect
-
Question 25 of 57
25. Question
1 pointsIn configuring a Cisco router to prepare for IPS and VPN features, a network administrator opens the file realm-cisco.pub.key.txt, and copies and pastes the contents to the router at the global configuration prompt. What is the result after this configuration step?Correct
Incorrect
-
Question 26 of 57
26. Question
1 pointsWhen dynamic NAT on an ASA is being configured, what two parameters must be specified by network objects? (Choose two.)Correct
Incorrect
-
Question 27 of 57
27. Question
1 pointsA system analyst is configuring and tuning a recently deployed IPS appliance. By examining the IPS alarm log, the analyst notices that the IPS does not generate alarms for a few known attack packets. Which term describes the lack of alarms by the IPS?Correct
Incorrect
-
Question 28 of 57
28. Question
1 pointsAn administrator is comparing multiple implementations of AAA. Which AAA method is server-based and considered the most secure?Correct
Incorrect
-
Question 29 of 57
29. Question
1 pointsWhat can be implemented to help mitigate the threat of a rogue switch becoming the root bridge in an STP domain?Correct
Incorrect
-
Question 30 of 57
30. Question
1 pointsConsider the following configuration on a Cisco ASA: crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac What is the purpose of this command?Correct
Incorrect
-
Question 31 of 57
31. Question
1 pointsWhat is negotiated in the establishment of an IPsec tunnel between two IPsec hosts during IKE Phase 1?Correct
Incorrect
-
Question 32 of 57
32. Question
1 pointsWhich type of IPS signature alarm occurs from normal traffic that should not have triggered an alarm?Correct
Incorrect
-
Question 33 of 57
33. Question
1 pointsWhich two options provide secure remote access to a router? (Choose two.)Correct
Incorrect
-
Question 34 of 57
34. Question
1 pointsWhat action can a network administrator take to help mitigate the threat of VLAN hopping attacks?Correct
Incorrect
-
Question 35 of 57
35. Question
1 pointsWhat type of data does the DLP feature of Cisco Email Security Appliance scan in order to prevent customer data from being leaked outside of the company?Correct
Incorrect
-
Question 36 of 57
36. Question
1 pointsA security specialist configures an IPS so that it will generate an alert when an attack is first detected. Alerts for the subsequent detection of the same attack are suppressed for a pre-defined period of time. Another alert will be generated at the end of the period indicating the number of the attack detected. Which IPS alert monitoring mechanism is configured?Correct
Incorrect
-
Question 37 of 57
37. Question
1 pointsWhich transform set provides the best protection?Correct
Incorrect
-
Question 38 of 57
38. Question
1 pointsA syslog server has received the message shown. *Mar 1 00:07:18.783: %SYS-5-CONFIG_I: Configured from console by vty0 (172.16.45.1) What can be determined from the syslog message?Correct
Incorrect
-
Question 39 of 57
39. Question
1 pointsWhat are three attributes of IPS signatures? (Choose three.)Correct
Incorrect
-
Question 40 of 57
40. Question
1 pointsWhat mitigation plan is best for thwarting a DoS attack that is creating a switch buffer overflow?Correct
Incorrect
-
Question 41 of 57
41. Question
1 pointsAn administrator assigned a level of router access to the user ADMIN using the commands below.Router(config)# privilege exec level 14 show ip route Router(config)# enable algorithm-type scrypt secret level 14 cisco-level-10 Router(config)# username ADMIN privilege 14 algorithm-type scrypt secret cisco-level-10
Which two actions are permitted to the user ADMIN? (Choose two.)Correct
Incorrect
-
Question 42 of 57
42. Question
1 pointsWhat is an effective deployment of IPS and IDS appliances in a corporate network?Correct
Incorrect
-
Question 43 of 57
43. Question
1 pointsWhich antispoofing technology is used to mitigate DoS attacks?Correct
Incorrect
-
Question 44 of 57
44. Question
1 pointsWhat mitigation method is effective against CAM table overflow attacks?Correct
Incorrect
-
Question 45 of 57
45. Question
1 pointsA network administrator notices that unsuccessful login attempts have caused a router to enter quiet mode. How can the administrator maintain remote access to the networks even during quiet mode?Correct
Incorrect
-
Question 46 of 57
46. Question
1 pointsWhich statement describes the function of the SPAN tool used in a Cisco switch?Correct
Incorrect
-
Question 47 of 57
47. Question
1 pointsWhat function is provided by the Cisco IOS Resilient Configuration feature?Correct
Incorrect
-
Question 48 of 57
48. Question
1 pointsWhat does the TACACS+ protocol provide in a AAA deployment?Correct
Incorrect
-
Question 49 of 57
49. Question
1 pointsWhich two UDP port numbers may be used for server-based AAA RADIUS authentication? (Choose two.)Correct
Incorrect
-
Question 50 of 57
50. Question
1 pointsWhich two options can limit the information discovered from port scanning? (Choose two.)Correct
Incorrect
-
Question 51 of 57
51. Question
1 pointsWhat function is provided by the RADIUS protocol?Correct
Incorrect
-
Question 52 of 57
52. Question
1 pointsWhat is the role of the Cisco NAC Agent in implementing a secure networking infrastructure?Correct
Incorrect
-
Question 53 of 57
53. Question
1 pointsWhat level of syslog is associated with Log_Alert?Correct
Incorrect
-
Question 54 of 57
54. Question
1 pointsRefer to the exhibit. Based on the security levels of the interfaces on ASA1, what traffic will be allowed on the interfaces?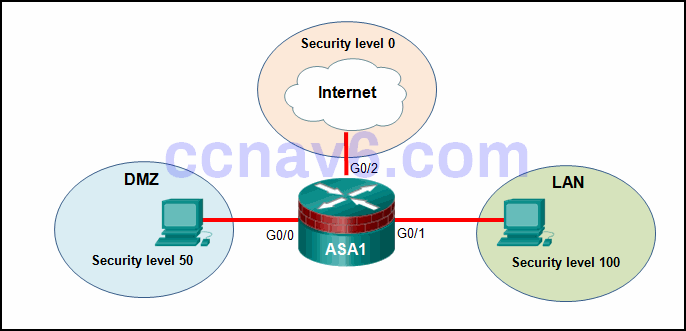 Correct
Correct
Incorrect
-
Question 55 of 57
55. Question
1 pointsRefer to the exhibit. An administrator issues these IOS login enhancement commands to increase the security for login connections. What can be concluded about them? Correct
Correct
Incorrect
-
Question 56 of 57
56. Question
1 pointsWhat are two diffrences between an ASA 5505 and an ASA 5506-X with FirePower Device? (Choose two)Correct
Incorrect
-
Question 57 of 57
57. Question
1 pointsA network analyst needs to reset an ASA 5506-X device to its defualt as-shipped state after the next reboot. What is the minimun length of time the RESET pin should be pressed to take the this effect?Correct
Incorrect
