1. What are three examples of personally identifiable information? (Choose three.)
- bank account number
- home water usage
- vehicle identification number
- birth date
- home thermometer value
- vehicle fuel consumption
2. Which two online activities pose high security risks? (Choose two.)
- verifying a banking site URL before entering information
- sharing information on social media
- following email links that have already been scanned by the email server
- using a VPN to access the Internet from a Wi-Fi hot spot
- creating a very complex password for a new account and storing it in a password manager service
3. Which three passwords are the least secure? (Choose three.)
- 135792468
- 34%cafe_!
- s3CurE_p@ss
- asdfghjkl
- randolph
- Ci3c0_RocK$
4. How can a virtual assistant be a security risk?
- Encryption protocols are not supported.
- Personal devices could be remotely seen.
- Sensor options could be modified.
- Personal information could be leaked.
5. What is used to identify a wireless network?
- IP address
- MAC address
- SSID
- SPI
6. Match the security best practice to the description.
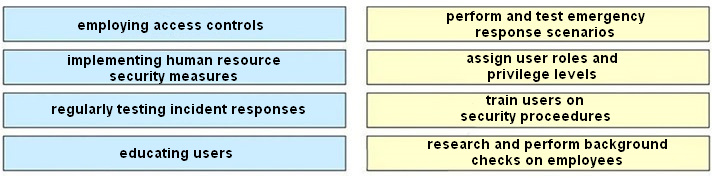
The correct answer is:
- employing access controls → assign user roles and privilege levels
- implementing human resource security measures → research and perform background checks on employees
- regularly testing incident responses → perform and test emergency response scenarios
- educating users → train users on security proceedures
7. What is a goal of performing a risk assessment?
- educating users in secure procedures
- restricting access to physical assets
- valuing assets to justify security expenditures
- outlining job duties and expectations
8. How are USB flash drives a security risk?
- They cannot be encrypted.
- They have a controller that can be infected.
- They contain wireless antennas.
- They contain a remote sensor.
9. Why would an IT person use Zabasearch?
- to research an IoT device
- to research an app
- to research a business
- to research a person
10. Which action can help reduce online risk?
- only accept unsolicited software updates when logged into a secure network
- only download programs with the most positive reviews on 3rd party websites
- only conduct transactions on websites after verifying the URL is correct
- only click embedded links in email messages from friends
11. Which three elements should be combined when creating a strong password? (Choose three.)
- dictionary words
- combinations of letters and numbers
- phrases
- personal information
- special characters
- pet names
12. What is the goal of a white hat hacker?
- modifying data
- protecting data
- validating data
- stealing data
13. What is a wireless router security best practice that limits access to only specific internal hosts?
- enabling the built-in firewall
- enabling encryption
- disabling SSID advertisements
- MAC address filtering
14. What are two recommended steps to protect and secure a wireless network? (Choose two.)
- Update firmware.
- Enable remote management.
- Locate the wireless router where it is accessible to users.
- Use WPA2-AES encryption.
- Use the default SSID.
15. An employee is using a coffee shop Wi-Fi hotspot to access corporate email. What action can the employee take to reduce the security risk of using a hotspot?
- Scan emails with antivirus software.
- Verify the name of the sender of emails before opening them.
- Only click on embedded links in email messages from trusted colleagues.
- Encrypt traffic through a VPN.
