Introduction to the Internet of Things ( Version 2) – Introduction to IoT: Final Exam Answers
Introduction to the Internet of Things and Digital Transformation Final Exam Answers
How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.
NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.
- It only runs in the interactive mode.
- It uses the & symbol to indicate that the interactive mode is ready to accept commands.
- The code is easy to read.
- It requires a compiler to be installed.
- It runs without conversion to machine-language.
Explanation: A compiled computer language is a computer language that compiles its programs into a set of machine-language instructions, whereas an interpreted programming language allows for an interpretation of the instructions directly without first compiling them into machine language.
2. What is the core component of Intent-Based Networking?
- artificial intelligence
- fog computing
- the internet
- the cloud
Explanation: Refer to curriculum topic: 1.2.2
Artificial intelligence will allow Intent-Based Networking to automatically configure network device across the network to fulfill network requirements based on the intent of those requirements.
3. Which statement describes global variables in programming languages?
- They can be used within any function of a program.
- They are declared within a function.
- They cannot be used within any functions in a program.
- They can only be used within the function they are declared.
Explanation: Global variables are variables that are in the scope for the time of the execution of the program, whereas local variables are within the scope of a program, function, or procedure.
4. What is the largest network in existence?
- a PAN
- a WAN
- the fog
- the internet
Explanation: The internet provides the “electronic skin” that surrounds the planet to connect electronic devices and people to data and each other.
5. How is data that has been collected through sources such as web pages, audio, or tweets categorized?
- unstructured data
- raw data
- application data
- structured data
Explanation: Collected data is categorized as either structured or unstructured data. Structured data is created by applications that use ‘fixed’ format input such as spreadsheets. Unstructured data is generated in ‘freeform’ style such tweets, audio/video files or web pages.
6. A company requires using a secure encrypted internet connection when connecting to the corporate network from outside the company. Which technology should be used when employees travel and use a laptop?
- VPN
- Siri
- Bluetooth
- Wi-Fi hotspot
Explanation: A virtual private network (VPN) should be used when connecting to a non-personal Wi-Fi network so that others that use the same network cannot eavesdrop on web traffic.
7. Which technology has the intelligence that is demonstrated by machines in a way that mimics human cognitive functions?
Explanation: Artificial intelligence (AI) allows devices to make a decision based on input data. A comma-separated values (CSV) file contains a table of data that is easily imported. Intent-based networking (IBN) uses AI and machine learning (ML) to control the function of a network to accomplish a specific purpose. Machine language is a subset of AI that allow computers to “learn” from their environment by using statistical data.
8. What is an open-source physical computing platform that can take input from a variety of switches or sensors to control physical objects?
- Beaglebone
- Arduino
- Raspberry Pi
Explanation: Arduino is an open-source physical computing platform based on a simple microcontroller board.
9. Match the term with the definition. (Not all options are used.)
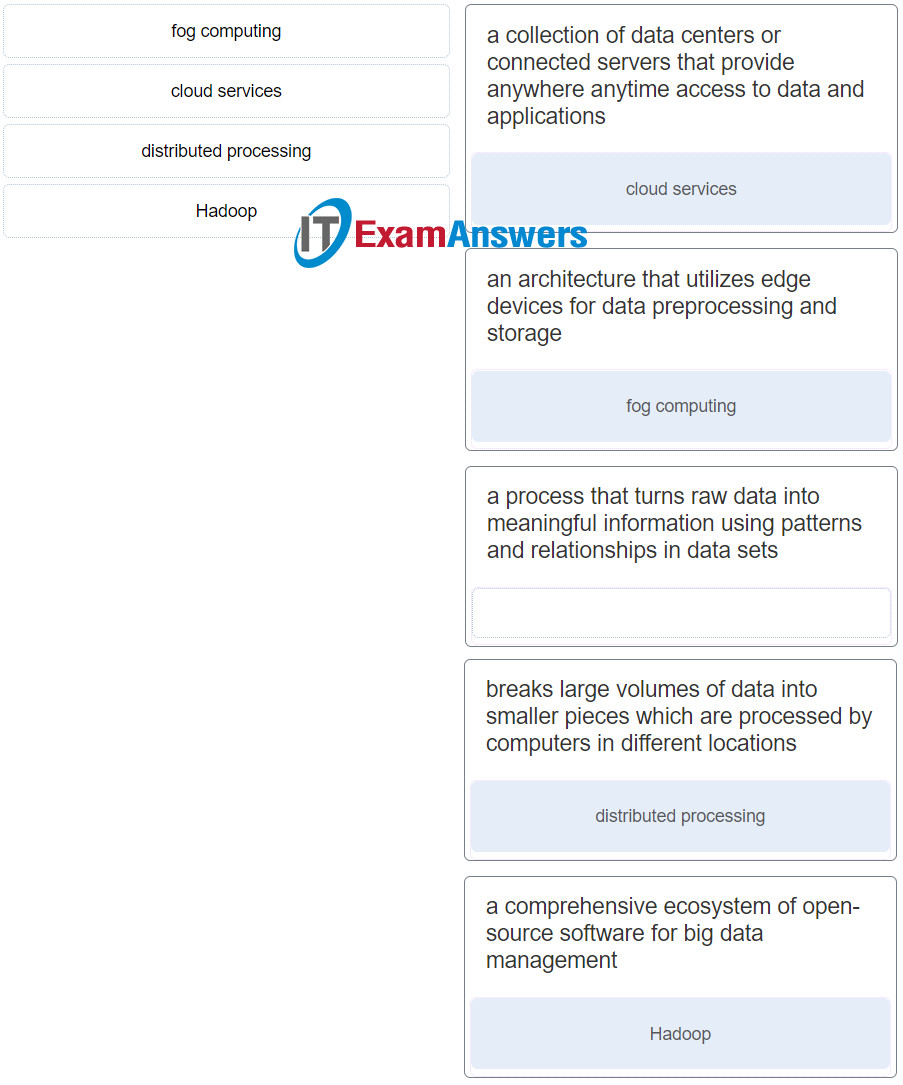
Introduction to the Internet of Things ( Version 2) – Introduction to IoT: Final Exam q9
Explanation: Options matched to the correct selection.
| a collection of data centers or connected servers that provide anywhere anytime access to data and applications |
cloud services |
| an architecture that utilizes edge devices for data preprocessing and storage |
fog computing |
| breaks large volumes of data into smaller pieces which are processed by computers in different locations |
distributed processing |
| a comprehensive ecosystem of open-source software for big data management |
Hadoop |
10. What limits the types of different objects that can become intelligent sensors on the Internet of Things?
- availability of power for consumption
- our imagination
- the size of the internet
- the government
Explanation: Only our imagination limits the different types of objects that can become intelligent devices and sensors in the IoT.
11. Which type of network is the connection between a Bluetooth headset and a vehicle?
Explanation: A Bluetooth network is an example of a PAN. Bluetooth devices are wireless devices within personal reach, such as a keyboard, mouse, headset, or speakers.
12. True or False?
Comma-separated values (CSV), JSON, and XML are all tools that can be used to manipulate structured data.
Explanation: Collected data can be categorized as structured or unstructured. Both categories of data can be collected from different file formats that may not necessarily be compatible with one another. Structured data may be manipulated using comma-separated values (CSV), whereas web scraping tools are used to extract unstructured data.
13. What is a key feature of the assurance element of the intent-based networking model?
- provisioning of intent-based policies
- end-to-end verification of network-wide behavior
- application of business intent to network configuration
- verification of configuration before devices are deployed
Explanation: There are three key elements of the intent-based networking model: assurance, translation, and activation. The assurance element is concerned with the end-to-end verification of network-wide behavior.
14. Which character is used within a search engine to gather data efficiently by placing the character before and after the name of a particular person?
- semicolon (;)
- quotation mark (“)
- question mark (?)
- colon (:)
15. What is used to provide IoT sensors with access to the network?
- fog computing
- an actuator
- a laptop
- a microcontroller
Explanation: Sensors in the IoT need to connect to the network so that data can be gathered and shared. Sensors have a wired or wireless connection to a microcontroller which provides a link to the network.
16. Which security best practice involves defining company rules, job duties, and expectations?
- maintaining patches and updates
- developing a security policy
- implementing physical security
- performing risk assessments
Explanation: A company security policy should clearly define company rules, job duties, and expectations.
17. What are three attributes of data that would indicate that it may be big data? (Choose three.)
- velocity
- volume
- visibility
- variety
- vulnerability
- versatility
Explanation: Three attributes of big data are as follows:
– Volume – the increase in data storage needs
– Velocity – the exponential growth rate of data
– Variety – the many types of data that are generated
18. Which two data types would be classified as personally identifiable information (PII)? (Choose two.)
- Facebook photographs
- hospital emergency use per region
- average number of cattle per region
- vehicle identification number
- house thermostat reading
19. Which two types of institutions do malicious web pages often look like? (Choose two.)
- technical
- bank
- commercial
- academic
- financial
Explanation: Malicious web pages often look like banks or financial institution websites. Before clicking any links, check the URL to make sure the web page is the correct one.
20. What is the purpose of data analytics?
- to ensure data security
- to compress data
- to gain new insights from data
- to optimize data storage
Explanation: The goal of many businesses is to collect and analyze the massive amounts of new product-usage data to gain valuable insights. Data analytics allows businesses to better understand the impact of their products and services, adjust their methods and goals, and provide their customers with better products faster. The ability to gain new insights from their data brings business value.
21. Change will have to occur in the corporate network in order to prepare for the Internet of Things. Which type of testing would a company do to demonstrate the benefits of networking a new “thing” that was not on the network before?

- formative
- developmental
- prototyping
- transference
Explanation: A company commonly uses prototyping or modeling to demonstrate a new or modified technology or implementation.
22. Which type of network consists of wired computers in a college classroom?
Explanation: A local-area network (LAN) is commonly contained in a small or localized area in a company or home. LANs commonly connect to wide-area networks (WANs).
23. Mined data can be visualized through the use of charts. Select two criteria that can be used to determine the best chart selection. (Choose two.)
- file size
- number of variables to be shown
- size of the chart
- items requiring comparison
- data format
Explanation: Mined data can be visualized through the use of charts. Determining the best chart to use will vary based on the following:
– Number of variables to show
– Number of data points in each variable
– Is the data representing a timeline
– Items require comparisons
24. Which technology is a subset of AI that uses statistical techniques to enable computers to “learn” from collected data?
Explanation: Many tasks have migrated from artificial intelligence (AI) to machine learning (ML) because as technology develops, many tasks that at one time required AI become routine.
25. Which two skills help with IoT prototyping? (Choose two.)
- programming
- design
- Windows operating systems
- welding
- database administration
Explanation: Prototyping in the IoT may require the following skills: design, electrical, physical/mechanical programming, and an understanding of TCP/IP.
26. Which technology is used as a visual programming tool to create a program by connecting colored blocks?
- Python
- Arduino
- JavaScript
- Blockly
Explanation: Blockly is a programming tool for beginners that can create a program that can be translated into Python or JavaScript.
27. What are the two areas of physical security within a data center?
- outside
- private
- restricted
- public
- inside
28. What is the purpose of Packet Tracer?
- to provide products and services to internet customers
- to use electromagnetic waves to carry signals over a specific geographic area
- to enable the sharing of resources such as printers, documents, pictures, and music between a few local computers
- to simulate and visualize one or more networks
29. What are three benefits of cloud computing? (Choose three.)
- It enables access to organizational data anywhere and at any time.
- It streamlines the IT operations of an organization by subscribing only to needed services.
- It uses open-source software for distributed processing of large datasets.
- It eliminates or reduces the need for onsite IT equipment, maintenance, and management.
- It utilizes end-user clients to do a substantial amount of data preprocessing and storage.
- It turns raw data into meaningful information by discovering patterns and relationships.
Explanation: There are many benefits to using cloud computing, including these:
– Access to organizational data anywhere and at any time
– Streamlined IT operations in an organization by subscribing only to needed services
– Elimination or reduction of the need for onsite IT equipment, maintenance, and management
30. What are two requirements to connect a smart device to a home wireless network? (Choose two.)
- URL
- IP addressing
- SSID
- home gateway name
- GUI
Explanation: In order for a device to communicate on a wireless network, the device must be configured with both the SSID of the wireless network and a unique
31. What are two features of automation? (Choose two.)
- a process that always uses sensors
- a process that always uses robots
- a process that is self-driven
- a process that results in 12 hour shifts
- a process that eventually eliminates the need for human intervention
Explanation: Automation is a process that is self-driven and eventually eliminates the need for human intervention.
32. Match the logic structure to the function.
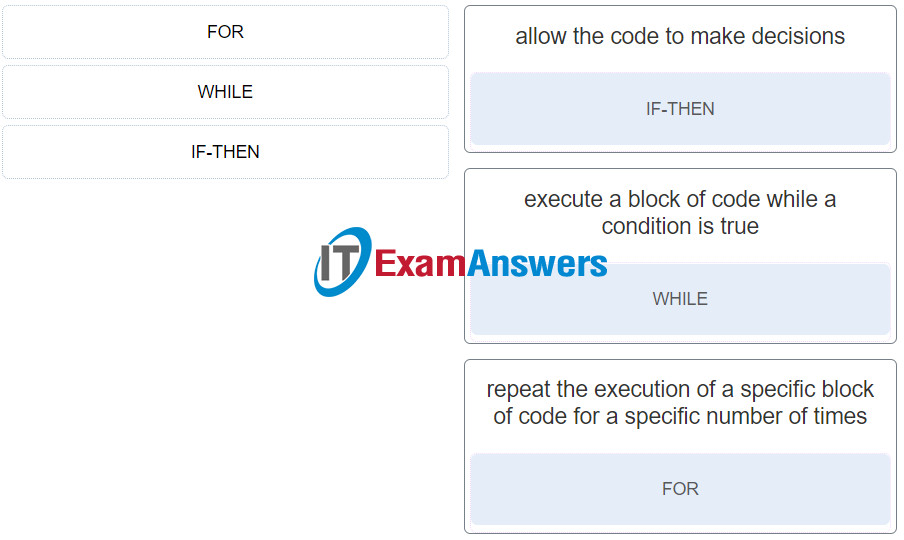
Introduction to the Internet of Things ( Version 2) – Introduction to IoT: Final Exam Q32
Explanation: Options matched to the correct selection.
| allow the code to make decisions |
IF-THEN |
| execute a block of code while a condition is true |
WHILE |
| repeat the execution of a specific block of code for a specific number of times |
FOR |
33. What are two things that all digital devices need in order to work? (Choose two.)
- computer program
- sensor
- global positioning satellite
- artificial intelligence
- data
Explanation: All digital devices need at least one computer program and data to work and be productive. Artificial intelligence is programming that allows the device to be logical when making decisions.
34. True or False?
With artificial intelligence, smart devices can modify processes and settings on the fly in response to changes on the network.
35. What device provides auto discovery services for smart devices that are connected to the network?
- laptop
- home gateway
- PC
- tablet
Explanation: The home gateway provides Internet access, wireless connectivity, and an IoT registration service for auto discovery for things in the local network.
36. What are the two areas of physical security within a data center? (Choose two.)
- outside
- inside
- restricted
- private
- public
Explanation: Data center physical security consists of outside perimeter security and inside perimeter security. Outside perimeter security includes fences, gates, and security breach alarms. Inside perimeter security includes motion detectors, security traps, and biometric access and exit sensors.



