2.5.1 Packet Tracer – Basic PPP Configuration Answers
Topology
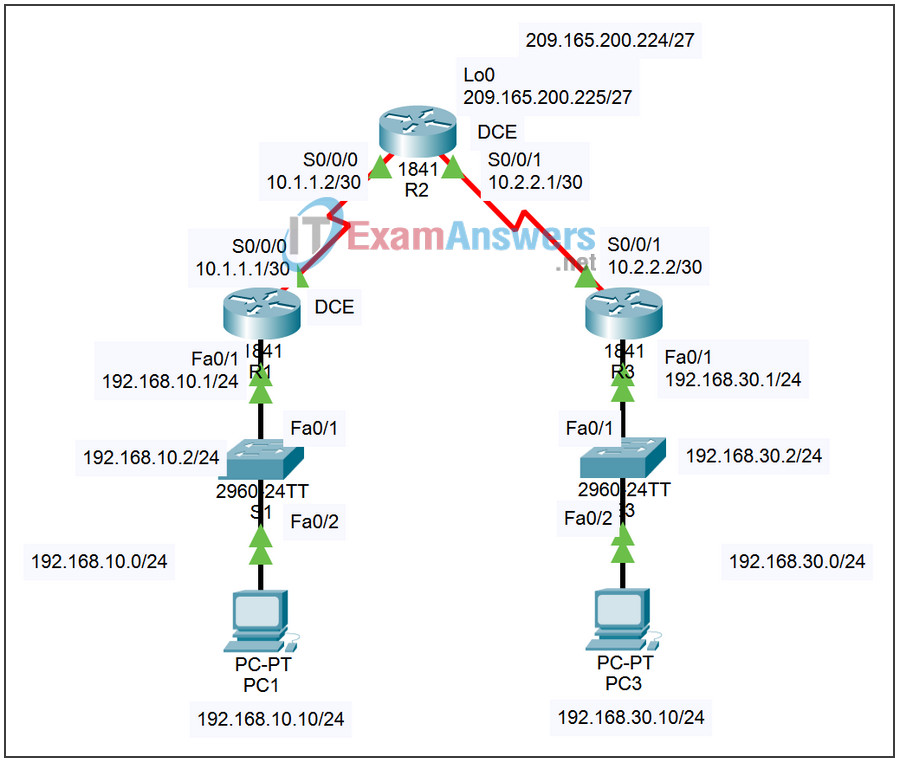
Addressing Table
| Device | Interface | IP Address | Subnet Mask | Subnet Mask |
|---|---|---|---|---|
| R1 | Fa0/1 | 192.168.10.1 | 255.255.255.0 | N/A |
| S0/0/0 | 10.1.1.1 | 255.255.255.252 | N/A | |
| R2 | Lo0 | 209.165.200.225 | 255.255.255.224 | N/A |
| S0/0/0 | 10.1.1.2 | 255.255.255.252 | N/A | |
| S0/0/1 | 10.2.2.1 | 255.255.255.252 | N/A | |
| R3 | Fa0/0 | 192.168.30.1 | 255.255.255.0 | N/A |
| S0/0/1 | 10.2.2.2 | 255.255.255.252 | N/A | |
| PC1 | NIC | 192.168.10.10 | 255.255.255.0 | 192.168.10.1 |
| PC3 | NIC | 192.168.30.10 | 255.255.255.0 | 192.168.30.1 |
Learning Objectives
- Configure OSPF routing on all routers.
- Configure PPP encapsulation on all serial interfaces.
- Intentionally break and restore PPP encapsulation.
- Configure PPP PAP and CHAP authentication.
- Intentionally break and restore PPP PAP and CHAP authentication.
Introduction
In this activity, you will learn how to configure PPP encapsulation on serial links using the network shown in the topology diagram. You will also learn how to restore serial links to their default HDLC encapsulation. Finally, you will configure PPP PAP authentication and PPP CHAP authentication.
Task 1: Configure OSPF on the Routers
Step 1. Enable OSPF routing on R1, R2, and R3.
For all three routers, use cisco for the user EXEC password and class for the privileged EXEC password. Issue the router ospf command with a process ID of 1 to enter router configuration mode. For each router, advertise all the attached networks.
R1(config)#router ospf 1 R1(config-router)#network 192.168.10.0 0.0.0.255 area 0 R1(config-router)#network 10.1.1.0 0.0.0.3 area 0 R1(config-router)# R2(config)#router ospf 1 R2(config-router)#network 10.1.1.0 0.0.0.3 area 0 R2(config-router)#network 10.2.2.0 0.0.0.3 area 0 R2(config-router)#network 209.165.200.224 0.0.0.31 area 0 R2(config-router)# R3(config)#router ospf 1 R3(config-router)#network 10.2.2.0 0.0.0.3 area 0 R3(config-router)#network 192.168.30.0 0.0.0.255 area 0 R3(config-router)#
Step 2. Verify that you have full network connectivity.
Use the show ip route and ping commands to verify connectivity.
R1# show ip route
<output omitted>
10.0.0.0/30 is subnetted, 2 subnets
C 10.1.1.0 is directly connected, Serial0/0/0
O 10.2.2.0 [110/128] via 10.1.1.2, 00:02:22, Serial0/0/0
C 192.168.10.0/24 is directly connected, FastEthernet0/1
O 192.168.30.0/24 [110/129] via 10.1.1.2, 00:00:08, Serial0/0/0
209.165.200.0/32 is subnetted, 1 subnets
O 209.165.200.225 [110/65] via 10.1.1.2, 00:02:22, Serial0/0/0
R1# ping 192.168.30.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.30.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/32/32 ms
R1#
R2# show ip route
<output omitted>
10.0.0.0/30 is subnetted, 2 subnets
C 10.1.1.0 is directly connected, Serial0/0/0
C 10.2.2.0 is directly connected, Serial0/0/1
O 192.168.10.0/24 [110/65] via 10.1.1.1, 00:02:31, Serial0/0/0
O 192.168.30.0/24 [110/65] via 10.2.2.2, 00:00:20, Serial0/0/1
209.165.200.0/27 is subnetted, 1 subnets
C 209.165.200.224 is directly connected, Loopback0
R2# ping 192.168.30.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.30.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/16/16 ms
R2# ping 192.168.10.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/16/16 ms
R2#
R3# show ip route
<output omitted>
10.0.0.0/30 is subnetted, 2 subnets
O 10.1.1.0 [110/128] via 10.2.2.1, 00:00:34, Serial0/0/1
C 10.2.2.0 is directly connected, Serial0/0/1
O 192.168.10.0/24 [110/129] via 10.2.2.1, 00:00:34, Serial0/0/1
C 192.168.30.0/24 is directly connected, FastEthernet0/1
209.165.200.0/32 is subnetted, 1 subnets
O 209.165.200.225 [110/65] via 10.2.2.1, 00:00:34, Serial0/0/1
R3# ping 209.165.200.225
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 209.165.200.225, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/16/16 ms
R3# ping 192.168.10.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/32/32 ms
R3#
Task 2: Configure PPP Encapsulation on Serial Interfaces
Step 1. Use the show interface command to check whether HDLC is the default serial encapsulation.
The default serial encapsulation on Cisco routers is HDLC. Use the show interface command on any of the serial interfaces to view the current encapsulation.
R1# show interface serial0/0/0
Serial0/0/0 is up, line protocol is up
Hardware is GT96K Serial
Internet address is 10.1.1.1/30
MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation HDLC, loopback not set
<output omitted>
If you check all the active serial interfaces, the encapsulation will be set to HDLC.
Step 2. Change the encapsulation of the serial interfaces from HDLC to PPP.
Change the encapsulation type on the link between R1 and R2, and observe the effects.
R1(config)# interface serial 0/0/0 R1(config-if)# encapsulation ppp R1(config-if)# *Aug 17 19:02:53.412: %OSPF-5-ADJCHG: Process 1, Nbr 209.165.200.225 on Serial0/0/0 from F ULL to DOWN, Neighbor Down: Interface down or detached R1(config-if)# R2(config)# interface serial 0/0/0 R2(config-if)# encapsulation ppp R2(config-if)#
What happens when one end of the serial link is encapsulated with PPP and the other end of the link is encapsulated with HDLC?
What happens when PPP encapsulation is configured on each end of the serial link?
Step 3. Change the encapsulation from HDLC to PPP on both ends of the serial link between R2 and R3.
R2(config)# interface serial0/0/1 R2(config-if)# encapsulation ppp R2(config-if)# *Aug 17 20:02:08.080: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.30.1 on Serial0/0/1 from FULL to DOWN, Neighbor Down: Interface down or detached *Aug 17 20:02:13.080: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to down *Aug 17 20:02:58.564: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to up *Aug 17 20:03:03.644: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.30.1 on Serial0/0/1 from LOAD ING to FULL, Loading Done *Aug 17 20:03:46.988: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to down R3(config)# interface serial 0/0/1 R3(config-if)# encapsulation ppp R3(config-if)# *Aug 17 20:04:27.152: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to up *Aug 17 20:04:30.952: %OSPF-5-ADJCHG: Process 1, Nbr 209.165.200.225 on Serial0/0/1 from L OADING to FULL, Loading Done
When does the line protocol on the serial link come up and the OSPF adjacency is restored?
Step 4. Verify that PPP is now the encapsulation on the serial interfaces.
R1# show interface serial0/0/0
Serial0/0/0 is up, line protocol is up
Hardware is GT96K Serial
Internet address is 10.1.1.1/30
MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, LCP Open
Open: CDPCP, IPCP, loopback not set
<output omitted>
R2# show interface serial 0/0/0
Serial0/0/0 is up, line protocol is up
Hardware is GT96K Serial
Internet address is 10.1.1.2/30
MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, LCP Open
Open: CDPCP, IPCP, loopback not set
<output omitted>
R2# show interface serial 0/0/1
Serial0/0/1 is up, line protocol is up
Hardware is GT96K Serial
Internet address is 10.2.2.1/30
MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, LCP Open
Open: CDPCP, IPCP, loopback not set
<output omitted>
R3# show interface serial 0/0/1
Serial0/0/1 is up, line protocol is up
Hardware is GT96K Serial
Internet address is 10.2.2.2/30
MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation PPP, LCP Open
Open: CDPCP, IPCP, loopback not set
<output omitted>
Task 3: Break and Restore PPP Encapsulation
Step 1. Return both serial interfaces on R2 to their default HDLC encapsulation.
R2(config)# interface serial 0/0/0 R2(config-if)# encapsulation hdlc R2(config-if)# *Aug 17 20:36:48.432: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.10.1 on Serial0/0/0 from FULL to DOWN, Neighbor Down: Interface down or detached *Aug 17 20:36:49.432: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to down R2(config-if)# *Aug 17 20:36:51.432: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up R2(config-if)# interface serial 0/0/1 *Aug 17 20:37:14.080: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to down R2(config-if)# encapsulation hdlc R2(config-if)# *Aug 17 20:37:17.368: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.30.1 on Serial0/0/1 from FULL to DOWN, Neighbor Down: Interface down or detached *Aug 17 20:37:18.368: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to down *Aug 17 20:37:20.368: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to up *Aug 17 20:37:44.080: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to down
Why is it useful to intentionally break a configuration?
Why do both serial interfaces go down, come back up, and then go back down?
Can you think of another way to change the encapsulation of a serial interface from PPP to the default HDLC encapsulation other than using the encapsulation hdlc command? (Hint: It has to do with the no command.)
Step 2. Return both serial interfaces on R2 to PPP encapsulation.
R2(config)# interface s0/0/0 R2(config-if)# encapsulation ppp *Aug 17 20:53:06.612: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up R2(config-if)# interface s0/0/1 *Aug 17 20:53:10.856: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.10.1 on Serial0/0/0 from LOAD ING to FULL, Loading Done R2(config-if)# encapsulation ppp *Aug 17 20:53:23.332: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to up *Aug 17 20:53:24.916: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.30.1 on Serial0/0/1 from LOAD ING to FULL, Loading Done R2(config-if)#
Task 4: Configure PPP Authentication
Step 1. Configure PPP PAP authentication on the serial link between R1 and R2.
R1(config)# username R2 password cisco R1(config)# int s0/0/0 R1(config-if)# ppp authentication pap R1(config-if)# *Aug 22 18:58:57.367: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to down *Aug 22 18:58:58.423: %OSPF-5-ADJCHG: Process 1, Nbr 209.165.200.225 on Serial0/0/0 from F ULL to DOWN, Neighbor Down: Interface down or detached R1(config-if)# ppp pap sent-username R1 password cisco
What happens when PPP PAP authentication is only configured on one end of the serial link?
R2(config)# username R1 password cisco R2(config)# interface Serial0/0/0 R2(config-if)# ppp authentication pap R2(config-if)# ppp pap sent-username R2 password cisco R2(config-if)# *Aug 23 16:30:33.771: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up *Aug 23 16:30:40.815: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.10.1 on Serial0/0/0 from LOAD ING to FULL, Loading Done
What happens when PPP PAP authentication is configured on both ends of the serial link?
Step 2. Configure PPP CHAP authentication on the serial link between R2 and R3.
In PAP authentication, the password is not encrypted. While this is certainly better than no authentication at all, it is still highly preferable to encrypt the password that is being sent across the link. CHAP encrypts the password.
R2(config)# username R3 password cisco R2(config)# int s0/0/1 R2(config-if)# ppp authentication chap R2(config-if)# *Aug 23 18:06:00.935: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to down R2(config-if)# *Aug 23 18:06:01.947: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.30.1 on Serial0/0/1 from FULL to DOWN, Neighbor Down: Interface down or detached R2(config-if)# R3(config)# username R2 password cisco *Aug 23 18:07:13.074: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to up R3(config)# int s0/0/1 R3(config-if)# *Aug 23 18:07:22.174: %OSPF-5-ADJCHG: Process 1, Nbr 209.165.200.225 on Serial0/0/1 from L OADING to FULL, Loading Done R3(config-if)# ppp authentication chap R3(config-if)#
Notice that the line protocol on interface serial 0/0/1 changes state to UP even before the interface is configured for CHAP authentication. Can you guess why this is the case?
Task 5: Intentionally Break and Restore PPP CHAP Authentication
Step 1. Break PPP CHAP authentication.
On the serial link between R2 and R3, change the authentication protocol on interface serial 0/0/1 to PAP.
R2# conf t Enter configuration commands, one per line. End with CNTL/Z. R2(config)# int s0/0/1 R2(config-if)# ppp authentication pap R2(config-if)# ^Z R2# *Aug 24 15:45:47.039: %SYS-5-CONFIG_I: Configured from console by console R2# copy run start Destination filename [startup-config]? Building configuration... [OK] R2# reload
Does changing the authentication protocol to PAP on interface serial 0/0/1 break authentication between R2 and R3?
Step 2. Restore PPP CHAP authentication on the serial link.
Notice that it is not necessary to reload the router for this change to take effect.
R2# conf t Enter configuration commands, one per line. End with CNTL/Z. R2(config)# int s0/0/1 R2(config-if)# ppp authentication chap R2(config-if)# *Aug 24 15:50:00.419: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to up R2(config-if)# *Aug 24 15:50:07.467: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.30.1 on Serial0/0/1 from LOAD ING to FULL, Loading Done R2(config-if)#
Step 3. Intentionally Break PPP CHAP authentication by changing the password on R3.
R3# conf t Enter configuration commands, one per line. End with CNTL/Z. R3(config)# username R2 password ciisco R3(config)# ^Z R3# *Aug 24 15:54:17.215: %SYS-5-CONFIG_I: Configured from console by console R3# copy run start Destination filename [startup-config]? Building configuration... [OK] R3# reload
After reloading, what is the status of the line protocol on serial 0/0/1?
Step 4. Restore PPP CHAP authentication by changing the password on R3.
R3# conf t Enter configuration commands, one per line. End with CNTL/Z. R3(config)# username R2 password cisco R3(config)# *Aug 24 16:11:10.679: %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/1, changed state to up R3(config)# *Aug 24 16:11:19.739: %OSPF-5-ADJCHG: Process 1, Nbr 209.165.200.225 on Serial0/0/1 from L OADING to FULL, Loading Done R3(config)#
Note that the link has come back up. Test connectivity by pinging from PC1 to PC3.
Step 5. Check results.
Your completion percentage should be 100%. If not, click Check Results to see which required components are not yet completed.
