1. Which three items are considered to be WAN devices? (Choose three.)
- bridges
- modems
- routers
- Layer 2 switches
- communication servers
- repeaters
2. Which layer of the hierarchical network design model is often referred to as the backbone?
- access
- distribution
- network
- core
- workgroup
- WAN
3. Drag the description on the left to the associated term on the right.
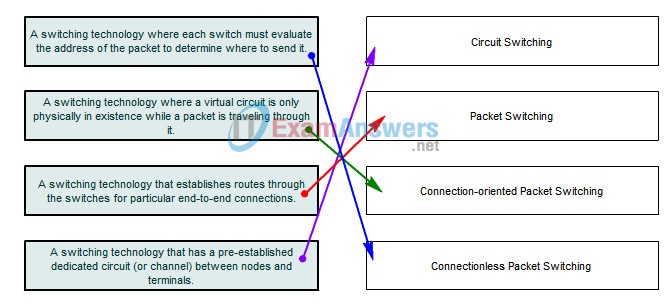
4. Drag the description of the packet-switched technology on the left to the associated term on the right.
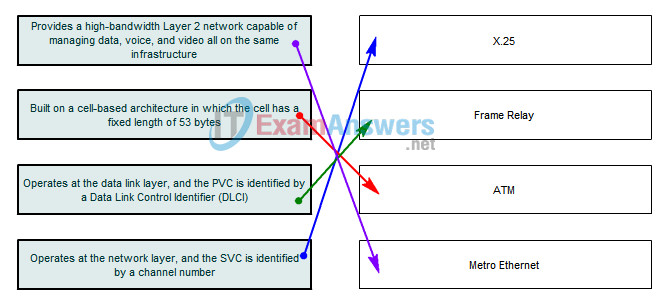
5. Which device is commonly used as Data Terminal Equipment?
- ISDN
- modem
- router
- CSU/DSU
6. Which type of WAN connection should be chosen when a dedicated point-to-point WAN communications path from the customer premises through the provider network to a remote destination is required?
- Integrated Services Digital Network (ISDN)
- analog dial-up
- Asynchronous Transfer Mode (ATM)
- Frame Relay (FR)
- leased line
7. How are Frame Relay virtual circuits identified?
- CIR
- DLCI
- VPI
- MAC
- SPID
8. What WAN technology is designed for delivering data, voice, and video simultaneously over a TDM infrastructure?
- ATM
- cable
- Frame Relay
- ISDN
9. Which architecture enables enterprises to offer important network services, such as security, new communication services, and improved application performance to every office regardless of its size or proximity to headquarters?
- Cisco Enterprise Campus Architecture
- Cisco Enterprise Data Center Architecture
- Cisco Enterprise Branch Architecture
- Cisco Enterprise Teleworker Architecture
10. At which layer of the hierarchical design model do users connect to the network?
- application
- access
- distribution
- network
- core
11. ISDN PRI is composed of how many B channels in North America?
- 2
- 16
- 23
- 30
- 64
12. The ability to connect securely to a private network over a public network is provided by which WAN technology?
- DSL
- Frame Relay
- ISDN
- PSTN
- VPN
13. Which hierarchical design model layer is responsible for containing network problems to the workgroups in which they occur?
- application
- access
- distribution
- network
- core
14. Which term describes the cabling that connects the customer site to the nearest exchange of the WAN service provider?
- CPE
- CO
- local loop
- DCE
- DTE
15. Which goal can be accomplished by the implementation of the Cisco Enterprise Teleworker Architecture?
- It allows the enterprise to add large branch sites that span large geographic areas.
- It allows the enterprise to deliver secure voice and data services to workers no matter where or when they work.
- In order to reduce remote security threats, it forces users who are located at main sites to log on to resources.
- It satisfies telephony requirements for users who are located at medium to large enterprise sites.
