1. Match a security category to each security weakness (answers may be used more than once):
Operating system weaknesses
Unsecured user accounts
Network equipment weaknesses
Unsecured default settings
Lack of consistency and continuity
TCP/IP and ICMP weaknesses
Lack of a disaster recovery plan
A. Technological weakness
B. Configuration weakness
C. Security policy weakness
| Operating system weaknesses |
Technological weakness |
| Unsecured user accounts |
Configuration weakness |
| Network equipment weaknesses |
Technological weakness |
| Unsecured default settings |
Configuration weakness |
| Lack of consistency and continuity |
Security policy weakness |
| TCP/IP and ICMP weaknesses |
Technological weakness |
| Lack of a disaster recovery plan |
Security policy weakness |
2. Which pieces of information can you determine from opening a router’s Cisco SDM home page? (Choose two.)
- Routing table
- CDP neighbors
- Snapshot of the router configuration
- A listing of available configuration wizards
- Features supported by the Cisco IOS software
3. A technician has been asked to perform a Cisco SDM one-step lockdown test. Which mode and SDM page should be used to initiate the test?
- The Firewall page in Diagnostic mode
- The Security Audit page in Configure mode
- The Security Audit page in Test mode
- The Firewall page in Test mode
4. Match each attack type with its description:
Reconnaissance attack
Password attack
Port redirection
Worm, virus, Trojan horse
DoS attack
A. Dictionary-cracking and brute-force attack
B. Uses a compromised host to pass traffic through a firewall that would otherwise be dropped
C. Uses ping sweeps, port scans, and packet sniffers to gain information about a network
D. Floods a network device with traffic in an attempt to render it unusable for legitimate traffic
E. Malicious software designed to damage a system, replicate itself, or deny services or access to networks, systems, or services
| Reconnaissance attack |
Uses ping sweeps, port scans, and packet sniffers to gain information about a network |
| Password attack |
Dictionary-cracking and brute-force attack |
| Port redirection |
Uses a compromised host to pass traffic through a firewall that would otherwise be dropped |
| Worm, virus, Trojan horse |
Malicious software designed to damage a system, replicate itself, or deny services or access to networks, systems, or services |
| DoS attack |
Floods a network device with traffic in an attempt to render it unusable for legitimate traffic |
5. What is a major advantage of HIPS over HIDS?
- HIPS does not require host-based client software.
- HIPS consumes fewer system resources.
- HIPS can prevent intrusions.
- With HIPS, you don’t need to update signature files as often.
Explanation: A host-based intrusion detection system (HIDS) typically is implemented as inline or passive technology and sends logs to a management console only after the attack has occurred and the damage is done. A host-based intrusion prevention system (HIPS) typically is implemented inline and actually stops the attack, prevents damage, and blocks the propagation of worms and viruses. Active detection can be set to shut down the network connection or to stop impacted services automatically. Corrective action can be taken immediately. Cisco provides HIPS using the Cisco Security Agent software.
6. What is the core or “hub” component of the Security Wheel?
- Secure
- Monitor
- Improve
- Test
- Security policy
Explanation: The security policy is the hub upon which the four steps of the Security Wheel (secure, monitor, test, and improve) are based. It drives the application of security measures:
- It identifies the organization’s security objectives.
- It documents the resources to be protected.
- It identifies the network infrastructure with current maps and inventories.
- It identifies the critical resources that need to be protected, such as research and development, finance, and human resources. This is called a risk analysis.
7. As part of a network security plan, where does Cisco recommend that administrators send events captured by syslog?
- Flash
- NVRAM
- Designated log hosts
- Designated TFTP clients
- Designated SNMP clients
Explanation: A syslog server provides a better solution because all network devices can forward their logs to one central station, where an administrator can review them. Multiple syslog hosts can be configured to provide fault tolerance. An example of a syslog server application is Kiwi Syslog Daemon.
8. Which protocol should be used when strong privacy and session integrity are needed for remote administration?
- HTTP
- SNMP
- SSH
- Telnet
- TFTP
Explanation: Secure Shell (SSH) provides the same functionality and authentication as Telnet but establishes an encrypted connection.
9. Match each network policy with its description:
Account access request policy
Remote-access policy
Risk assessment policy
Audit policy
Acceptable user policy
A. Defines the standards for connecting to the internal network from outside the organization.
B. Specifies procedures to investigate incidents, ensure conformance to security policies, and monitor user and system activity.
C. Defines how network resources may and may not be employed.
D. Formalizes the process of how users request access to systems.
E. Defines the requirements and provides the authority for the information security team to identify, assess, and remediate risks to the information infrastructure associated with conducting business.
| Account access request policy |
Formalizes the process of how users request access to systems. |
| Remote-access policy |
Defines the standards for connecting to the internal network from outside the organization. |
| Risk assessment policy |
Defines the requirements and provides the authority for the information security team to identify, assess, and remediate risks to the information infrastructure associated with conducting business. |
| Audit policy |
Specifies procedures to investigate incidents, ensure conformance to security policies, and monitor user and system activity. |
| Acceptable user policy |
Defines how network resources may and may not be employed. |
10. What are the three required steps to configure SDM?
- Use the auto secure command to configure router security.
- Enable the HTTP and HTTPS servers on the router.
- Create a user account defined with privilege level 15.
- Create a user account defined with privilege level 0.
- Create an ACL to allow HTTP traffic into the router, and apply it to the VTYs.
- Configure SSH and Telnet for local login and privilege level 15.
- Configure SSH and Telnet for local login and privilege level 0.
Explanation: Step 1: Create a user account defined with privilege level 15.
Step 2: Enable the HTTP and HTTPS servers on the router.
Step 3: Configure SSH and Telnet for local login and privilege level 15.
11. Which services should be disabled if they aren’t required on a router to prevent security vulnerabilities? (Choose three.)
- Network Time Protocol (NTP)
- Domain Name System (DNS)
- Secure Socket Layer (SSL)
- Cisco Express Forwarding (CEF)
- Simple Network Management Protocol (SNMP)
- Secure Shell (SSH)
12. Which feature provides a straightforward “one-touch” device lockdown for configuring the security posture of routers?
13. Match the network management service with its description:
Network Time Protocol (NTP)
Domain Name System (DNS)
Simple Network Management Protocol (SNMP)
A. An application layer protocol that provides a facility for retrieving and posting data for monitoring and managing devices in a network using TCP port 161
B. A protocol designed to synchronize the time on a network of machines and that runs over UDP using port 123
C. A distributed database that maps hostnames to IP addresses using services on a designated server
| Network Time Protocol (NTP) |
A protocol designed to synchronize the time on a network of machines and that runs over UDP using port 123 |
| Domain Name System (DNS) |
A distributed database that maps hostnames to IP addresses using services on a designated server |
| Simple Network Management Protocol (SNMP) |
An application layer protocol that provides a facility for retrieving and posting data for monitoring and managing devices in a network using TCP port 161 |
14. Which feature is a web-based device-management tool for Cisco IOS software-based routers?
15. Which SDM wizards are available to configure a router? (Choose three.)
- Security audit
- Firewall and ACL
- DHCP
- QoS
- Routing
- Access list
16. List the four types of reconnaissance attacks, and provide an example of a tool that can be used to carry out each type of attack.
Internet information queries:
Ping sweeps:
Port scans:
Packet sniffers:
17. List four types of access attacks.
- Password attack
- Trust exploitation attack
- Port redirection attack
- Man-in-the-middle attack
18. List three types of DoS attacks and three types of DDoS attacks.
DoS attacks:
- Ping of death attack
- SYN flood attack
- Packet fragmentation and reassembly attack
- E-mail bomb attack
- CPU hogging attack
- Malicious applet attack
DDoS attacks:
- Smurf attack
- Tribe Flood Network (TFN)
- Stacheldraht
- MyDoom
19. List and explain the anatomy of a worm attack and the four steps to mitigate it.
The anatomy of a worm attack is as follows:
- The enabling vulnerability: A worm installs itself by exploiting known vulnerabilities in systems, such as naive end users who open unverified executable e-mail attachments.
- Propagation mechanism: After gaining access to a host, a worm copies itself to that host and then selects new targets.
- Payload: After a host is infected with a worm, the attacker has access to the host, often as a privileged user. Attackers can use a local exploit to escalate their privilege level to administrator.
The following are the recommended steps for worm attack mitigation:
- Step 1, Containment: Contain the spread of the worm into your network and within your network. Compartmentalize uninfected parts of your network.
- Step 2, Inoculation: Start patching all systems and, if possible, scanning for vulnerable systems.
- Step 3, Quarantine: Track down each infected machine in your network. Disconnect, remove, or block infected machines from the network.
- Step 4, Treatment: Clean and patch each infected system. Some worms may require complete core system reinstallations to clean the system.
20. Refer to the exhibit.
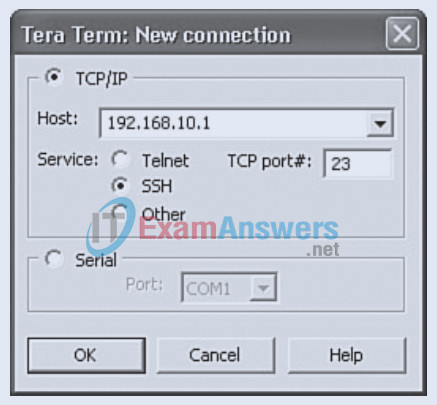
The following has been configured on router R1:
hostname R1
username Student secret cisco123
line vty 0 4
no transport input
transport input telnet
To increase administrative access security, you have applied the following configuration. However, you are unable to establish an SSH connection to router R1. Assume that you could telnet to the router before, and that the hostname, IP domain name, and crypto key have been correctly configured. Which changes would correct this problem?
On router R1:
- The transport input command should be transport input ssh.
- The login local command is missing from the line vty 0 4 configuration mode.
- The SSH port number in the Tera Term window should reference TCP port 22.
21. List five vulnerable Cisco IOS network services, and provide the best practices associated with them. For example, unused interfaces should be disabled.
- Small services such as echo, discard, and chargen should be disabled.
- BOOTP should be disabled.
- Finger should be disabled.
- Hypertext Transfer Protocol (HTTP) should be disabled, and secure HTTPS should be configured (if required).
- Simple Network Management Protocol (SNMP) versions 1 and 2 should be disabled, and SNMPv3 should be configured.
- Cisco Discovery Protocol (CDP) should be disabled unless required.
- Remote configuration should be disabled.
- Source routing should be disabled.
- Classless routing should be disabled.
- no ip directed-broadcast should be configured to stop Smurf attacks.
- no ip proxy-arp should be configured to stop ad hoc routing attacks.
22. List the steps to enable the lockdown feature of SDM.
1. Choose Configure.
2. Choose Security Audit.
3. Click the One-step lockdown button.
4. In the Cisco SDM Warning dialog box, click Yes.
5. Deliver commands to the router.
23. List the three steps required to update a router with a new Cisco IOS image file located on a TFTP server.
1. Ping the TFTP server to make sure you have access to it.
2. Use the show flash: command to verify that the router has enough room in flash to accommodate the size of the Cisco IOS image file.
3. Copy the new Cisco IOS image from the TFTP server using the copy tftp flash: command in privileged EXEC mode. Answer the required prompts.

