Cybersecurity Essentials 1.1 Chapter 4 Quiz Answers Full Questions
Chapter 4: The Art of Protecting Secrets
1.Which asymmetric algorithm provides an electronic key exchange method to share the secret key?
- RSA
- Diffie-Hellman
- WEP
- DES
- hashing
2.What encryption algorithm uses one key to encrypt data and a different key to decrypt data?
- transposition
- symmetric
- asymmetric
- one-time pad
3. What type of cipher encrypts plaintext one byte or one bit at a time?
- block
- stream
- hash
- enigma
- elliptical
4. What cryptographic algorithm is used by the NSA and includes the use of elliptical curves for digital signature generation and key exchange?
- ECC
- RSA
- AES
- El-Gamal
- IDEA
5.What is the term used to describe the science of making and breaking secret codes?
- factorization
- cryptology
- impersonation
- spoofing
- jamming
6.Which three processes are examples of logical access controls? (Choose three.)
- intrusion detection system (IDS) to watch for suspicious network activity
- firewalls to monitor traffic
- guards to monitor security screens
- fences to protect the perimeter of a building
- swipe cards to allow access to a restricted area
- biometrics to validate physical characteristics
7.What term is used to describe concealing data in another file such as a graphic, audio, or other text file?
- masking
- hiding
- obfuscation
- steganography
8.What are three examples of administrative access controls? (Choose three.)
- policies and procedures
- encryption
- background checks
- hiring practices
- intrusion detection system (IDS)
- guard dogs
9.Which three protocols use asymmetric key algorithms? (Choose three.)
- Secure File Transfer Protocol (SFTP)
- Telnet
- Pretty Good Privacy (PGP)
- Secure Shell (SSH)
- Advanced Encryption Standard (AES)
- Secure Sockets Layer (SSL)
10.A warning banner that lists the negative outcomes of breaking company policy is displayed each time a computer user logs in to the machine. What type of access control is implemented?
- masking
- deterrent
- detective
- preventive
11. Which term describes the technology that protects software from unauthorized access or modification?
- copyright
- watermarking
- access control
- trademark
12. What encryption algorithm uses the same pre-shared key to encrypt and decrypt data?
- hash
- asymmetric
- one-time pad
- symmetric
13.Which two terms are used to describe cipher keys? (Choose two.)
- key space
- key randomness
- keylogging
- key length
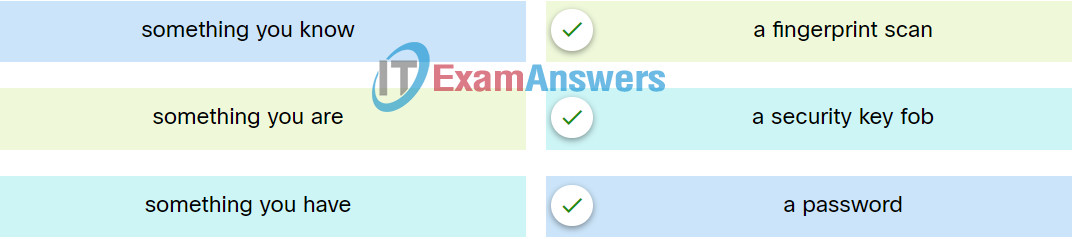
14.Match the type of multifactor authentication with the description.
15. What is the name of the method in which letters are rearranged to create the ciphertext?
- substitution
- transposition
- one-time pad
- enigma
16. Which 128-bit block cipher encryption algorithm does the US government use to protect classified information?
- Vignere
- AES
- Caesar
- 3DES
- Skipjack
17.Match the description with the correct term. (Not all targets are used.)
- steganography —> hiding data within an audio file
- steganalysis —> discovering that hidden information exists within a graphic file
- social steganography —> creating a message that says one thing but means something else to a specific audience
- obfuscation —> making a message confusing so it is harder to understand
- Other Incorrect Match Options:
- replacing sensitive information in a file with nonsensitive information
18. What term is used to describe the technology that replaces sensitive information with a nonsensitive version?
- blanking
- whiteout
- masking
- retracting
- hiding
19. Which type of cipher is able to encrypt a fixed-length block of plaintext into a 128-bit block of ciphertext at any one time?
- transform
- stream
- hash
- symmetric
- block
20. Which three devices represent examples of physical access controls? (Choose three.)
- locks
- routers
- swipe cards
- firewalls
- servers
- video cameras

Refer to curriculum topic: 4.2.4
Multi-factor authentication uses a minimum of two methods of verification and can include the following:
The correct answer is: a password → something you know, a fingerprint scan → something you are, a security key fob → something you have
Match the type of multifactor authentication with the description.
a security fob ———> something you have
a fingerprint scan ———-> something you are
a password ———-> something you know
Multi-factor authentication uses a minimum of two methods of verification and can include the following:
The correct answer is: a security key fob → something you have, a fingerprint scan → something you are, a password → something you know
Correct this on your website.
Thank You