19.5.2 Module 19 – Build a Small Cisco Network Quiz Answers
1. Which connection provides a secure CLI session with encryption to a Cisco switch?
- a console connection
- an AUX connection
- a Telnet connection
- an SSH connection
2. Which interface is the default SVI on a Cisco switch?
- VLAN 1
- GigabitEthernet 0/1
- FastEthernet 0/1
- VLAN 99
3. On which switch interface would an administrator configure an IP address so that the switch can be managed remotely?
- VLAN 1
- vty 0
- console 0
- FastEthernet0/1
4. What is the effect of using the Router# copy running-config startup-config command on a router?
- The contents of NVRAM will change.
- The contents of ROM will change.
- The contents of RAM will change.
- The contents of flash will change.
5. What is one difference between using Telnet or SSH to connect to a network device for management purposes?
- Telnet supports a host GUI whereas SSH only supports a host CLI.
- Telnet does not provide authentication whereas SSH provides authentication.
- Telnet sends a username and password in plain text, whereas SSH encrypts the username and password.
- Telnet uses UDP as the transport protocol whereas SSH uses TCP.
6. Refer to the exhibit. A network technician is statically assigning an IP address to a PC. The default gateway is correct. What would be a valid IP address to assign to the host?
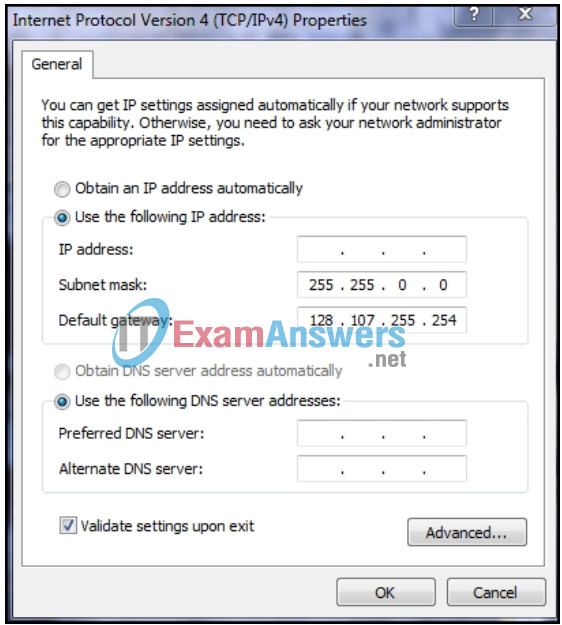
- 128.106.10.100
- 128.107.255.254
- 128.108.100.10
- 128.107.255.1
7. What happens when the transport input ssh command is entered on the switch vty lines?
- The switch requires remote connections via a proprietary client software.
- Communication between the switch and remote users is encrypted.
- The switch requires a username/password combination for remote access.
- The SSH client on the switch is enabled.
8. Company policy requires using the most secure method to safeguard access to the privileged exec and configuration mode on the routers. The privileged exec password is trustknow1. Which of the following router commands achieves the goal of providing the highest level of security?
- service password-encryption
- enable secret trustknow1
- enable password trustknow1
- secret password trustknow1
9. Which command can be used to encrypt all passwords in the configuration file?
- service password-encryption
- password
- enable secret
- enable password
10. Refer to the exhibit. From global configuration mode, an administrator is attempting to create a message-of-the-day banner by using the command banner motd Authorized access only! Violators will be prosecuted!. When users log in using Telnet, the banner does not appear correctly. What is the problem?

- The banner message is too long.
- The delimiting character appears in the banner message.
- The symbol “!” signals the end of a banner message.
- Message-of-the-day banners will only appear when a user logs in through the console port.
