1.3.6 Packet Tracer – Configure SSH (Instructor Version)
Addressing Table
| Device | Interface | IP Address | Subnet Mask |
|---|---|---|---|
| S1 | VLAN 1 | 10.10.10.2 | 255.255.255.0 |
| PC1 | NIC | 10.10.10.10 | 255.255.255.0 |
Objectives
- Part 1: Secure Passwords
- Part 2: Encrypt Communications
- Part 3: Verify SSH Implementation
Background
SSH should replace Telnet for management connections. Telnet uses insecure plain text communications. SSH provides security for remote connections by providing strong encryption of all transmitted data between devices. In this activity, you will secure a remote switch with password encryption and SSH.
Instructions
Part 1: Secure Passwords
a. Using the command prompt on PC1, Telnet to S1. The user EXEC and privileged EXEC password is cisco.
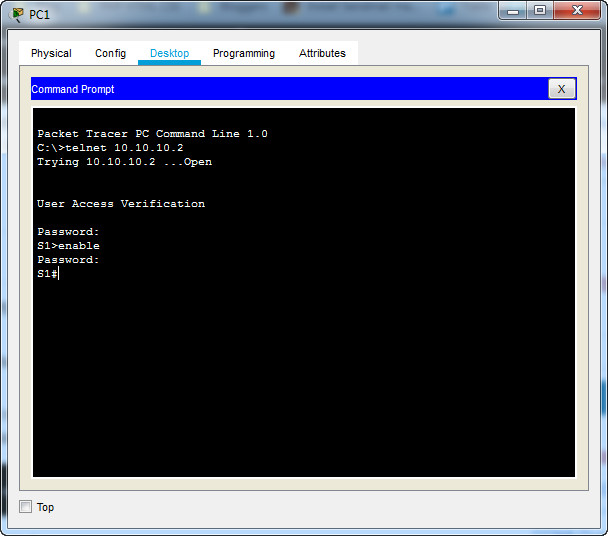
b. Save the current configuration so that any mistakes you might make can be reversed by toggling the power for S1.
S1#copy running-config startup-config Destination filename [startup-config]? Building configuration... [OK] S1#
c. Show the current configuration and note that the passwords are in plain text. Enter the command that encrypts plain text passwords:
S1#show running-config Building configuration... Current configuration : 1144 bytes ! version 12.2 no service timestamps log datetime msec no service timestamps debug datetime msec no service password-encryption ! hostname S1 ! enable password cisco !
S1(config)# service password-encryption
d. Verify that the passwords are encrypted.
S1#show running-config Building configuration... Current configuration : 1168 bytes ! version 12.2 no service timestamps log datetime msec no service timestamps debug datetime msec service password-encryption ! hostname S1 ! enable password 7 0822455D0A16 !
Part 2: Encrypt Communications
Step 1: Set the IP domain name and generate secure keys.
It is generally not safe to use Telnet, because data is transferred in plain text. Therefore, use SSH whenever it is available.
a. Configure the domain name to be netacad.pka.
S1(config)#ip domain-name netacad.pka
b. Secure keys are needed to encrypt the data. Generate the RSA keys using a 1024 key length.
S1(config)# crypto key generate rsa
The name for the keys will be: S1.netacad.pka
Choose the size of the key modulus in the range of 360 to 2048 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take
a few minutes.
How many bits in the modulus [512]: 1024
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
Step 2: Create an SSH user and reconfigure the VTY lines for SSH-only access.
a. Create an administrator user with cisco as the secret password.
S1(config)#username administrator secret cisco
b. Configure the VTY lines to check the local username database for login credentials and to only allow SSH for remote access. Remove the existing vty line password.
S1(config)#line vty 0 15 S1(config-line)#transport input ssh S1(config-line)#login local S1(config-line)#no password cisco
Step 3: Verify SSH Implementation
a. Exit the Telnet session and attempt to log back in using Telnet. The attempt should fail.
C:\>telnet 10.10.10.2 Trying 10.10.10.2 ...Open [Connection to 10.10.10.2 closed by foreign host] C:\>
b. Attempt to log in using SSH. Type ssh and press Enter without any parameters to reveal the command usage instructions. Hint: The -l option is the letter “L”, not the number 1.
C:\>ssh -l administrator 10.10.10.2 Password: S1>enable Password: S1#
c. Upon successful login, enter privileged EXEC mode and save the configuration. If you were unable to successfully access S1, toggle the power and begin again at Part 1.
S1#copy running-config startup-config Destination filename [startup-config]? Building configuration... [OK] S1#
Answer Key
config terminal service password-encryption ip domain-name netacad.pka crypto key generate rsa 1024 username administrator secret cisco line vty 0 15 login local transport input ssh no password cisco

THX broo